
2021-12-22 14:32:9 Author: infosecwriteups.com(查看原文) 阅读量:22 收藏

Hey there,
Yash Here, I’m noob BB Hunter & Security researcher from India.
In this section, I will explain you, how i was able to bypass the Covid-19 portal of Chandrapur ( Maharashtra ) Government & from which it leads to full admin access control of Dashboard. There was Confidential Information of thousands of Covid-19 patients such as their Name, Address, Mobile number, Dr Name who’s treating, Hospital where the patient is allocated & many more.

What is SQL injection (SQLi)?
SQL injection is a web security vulnerability that allows an attacker to interfere with the queries that an application makes to its database. It generally allows an attacker to view data that they are not normally able to retrieve. This might include data belonging to other users, or any other data that the application itself is able to access. In many cases, an attacker can modify or delete this data, causing persistent changes to the application’s content or behavior.
In some situations, an attacker can escalate an SQL injection attack to compromise the underlying server or other back-end infrastructure, or perform a denial-of-service attack.

While doing my recon. I found some endpoints but one took my all attention towards it. I found the admin panel of Covid-19 Portal.
Detailed Steps :-
- Open admin login page using the following URL: https://dmchanda.in/admin/admin-login.php
- Now put Payload admin’ or ‘1’=’1-- in the Username field and any random password & enter the verification code and then click on login button.
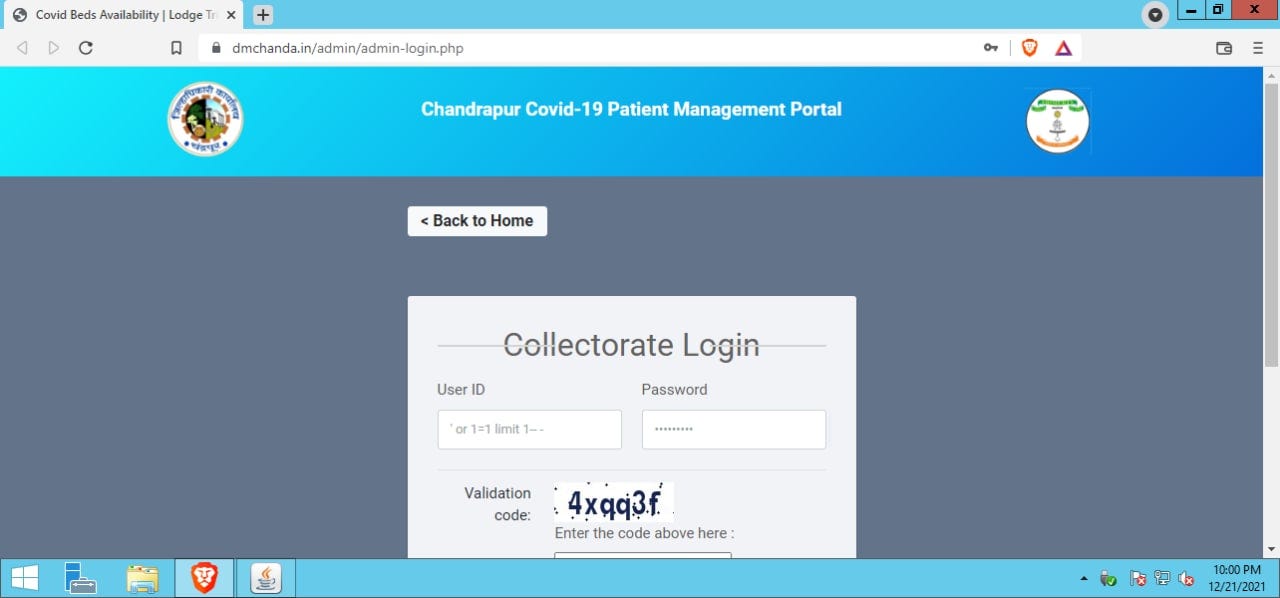
Boom !!!
3. Server accepted the payload and I was successfully able to bypass the panel without any credentials. And also I was able to see information of thousands of Covid-19 Patients such as their Name, Address, Mobile Number, Dr Name who’s treating, Hospital where the patient is allocated & many more info.


I instantly recorded the poc and reported to NCIIPC.
TimeLine:
Nov 17, 2021, 9:43pm: Reported.
Nov 18, 2021, 9:13am: A ticket was assigned.
Nov 18, 2021: Acknowledged by NCIIPC.
Nov 26, 2021: The issue was resolved (retested).

Thanks for reading.
Stay Safe.
如有侵权请联系:admin#unsafe.sh