2021-12-13 19:07:34 Author: infosecwriteups.com(查看原文) 阅读量:18 收藏
As-Salaam-Alaikum (Peace be unto you)
Hello, Amazing hackers My name is Rizwan Siddiqui I am a Bug Hunter. This is my First Write-up hope You guys will enjoy it and learn something new from it. Let’s get started on how I found this API misconfiguration.

scenario: The web application is some car or bus selling web application and there are also jobs related stuff there. I try file upload XSS but nothing works then I Go To id.target.com there is some profile type function where I can upload my file and there is my login log my IP address who login in to my account through which IP. I try some XSS again file upload vulnerability but nothing works
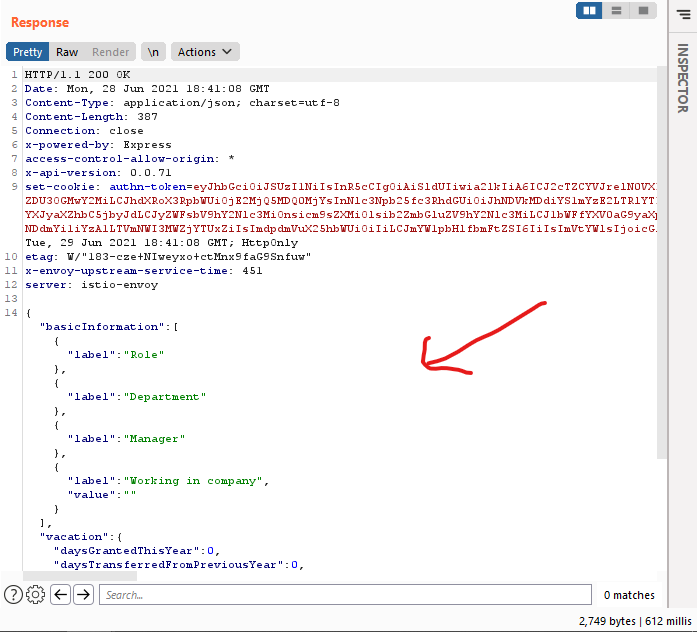
After that i thought i should give up and change my target but in id.target.com there is api endpoint that is fetching my personal details like my ip address and name stuff. That time i thought i should fuzz here i try fuzzing after that i notice that this is authenticated endpoint i should fuzz with my cookie so i can find something juice info and i start fuzz like this ffuf -u https://id.target.com/api/FUZZ -w wordlist -c COOKIE_HERE after some time it give me https://id.target.com/api/work and guess what there is some misconfiguration in api endpoint which is leaking company employee data like there position in company jobs Descriptions profile pic that time i thought this is just some basic or someone person info but i am wrong when i send it to repeater tab and i send that request, again and again, they give me new employee data every time.

Step To reproduce:
- Go to id.target.com login with your credential.
- open burp suite forward requests until u see the request like this :
GET /api/personal HTTP 1.1
HOST: id.target.com
Cookie : JWT TOKEN
Accept: application/json3. Just remove “personal” and add “work” then see the magic.
Takeaway:
Always Fuzz with your cookies if there is an API endpoint. And never lose hope.
如有侵权请联系:admin#unsafe.sh