
2021-10-15 13:37:08 Author: infosecwriteups.com(查看原文) 阅读量:25 收藏

Hey hackers ✋✋,
I’m back again with another portion of our enterprise, the binary exploitation series. In case you’re perusing my article 1st time ?? I unassumingly request you to spend a little time on my previous parts of the series before proceeding. You can find here →PART-1: 0x000001 | PART-2: 0x000002
NOTE:-
This time I’m not specifically into exploitation. Instead, I wanna share my information with my readers around Integer Overflow, Its occurrence & consequences. In coming write-ups, I’ll perfectly cover each exploitation technique & strategy. I’m not prepared to skip any topics, so I have written this 3rd portion about “Integer Overflow”.
Skip the “lines” only if you’re confident merely as of now that you know the stuff. You’re not squandering a single piece of your time whereas perusing something you never know. Learn and upgrade yourself before it’s too late. Without any delay, let’s begin.
What is Arithmetic Overflow?
It occurs when there are insufficient bits to depict the result of an arithmetic operation. ie, the result of a calculation that surpasses the memory space designated to hold it. Technically, when an adder/subtractor circuit is utilizing signed(+/-) arithmetic &, if there’s arithmetic overflow, the most significant magnitude bit into the sign bit will be overflowed. It will happen for the case when a 4-bit arithmetic result is required & when two 3-bit numbers are added together and the fourth bit within the circuit has been assigned for demonstrating the sign(+/-) of the answer. The consequences of the flood when it happens:
1. The addition of two positive numbers gives a negative answer
2. The addition of two negative numbers gives a positive answer
I’ll show an example,
considering 7FFFFFFF & 6FFFFFFF, let’s add these 2 & see what comes about.


The result is: EFFFFFFE
The amount that a calculated value is greater than a given register or storage location can store. So, we’d added 2 +ve to induce the -ve result.

I hope the concept is clear for you.
But why does it matter? How this be a severe issue within the genuine world??
Just think about it, Within the Internet era, we run on the digital world (miserable truth). For illustration, amid budgetary calculations or something related, results inside the recipient ends can be controlled in unintended ways. Art of exploitation opens boundless entryways without any rules. I don’t wanna share the “Fiendish things”. So I’m letting you discover why it’s an issue or not.
But what if an arithmetic operation endeavors to make a numeric value that’s exterior of the range that can be represented with a given number of digits ??

An Integer Overflow is a sort of arithmetic flood that happens when an integer value is increased to a value that’s as well huge to store within the related representation. When this happens, the value may wrap to ended up a little or negative number. It can have security consequences in case the wrap is unforeseen. Typically especially the case if the numbers flood can be activated utilizing user-supplied inputs. This gets to be a critical security issue. This weakness can sometimes trigger buffer overflows which can be utilized to execute arbitrary code. This will generally lead to undefined behaviour and thus crashes. Within the case of floods involving loop file factors, the probability of unbounded loops is additionally high. In case the value in address is critical to information (as restricted to streaming), simple data corruption will occurs. Too, on the off chance that the wrap-around comes about in other conditions such as buffer flood, encourage memory debasement may happen.
It is exceptionally difficult to find and anticipate. There’s no error, there’s no warning, you essentially get an off-base result of the operation. The as were way to find them is to look at the operands before the operation or look at the result after the addition of 2 two positive numbers. Depending on the language, you’ll be able to come over libraries or mechanisms that assist you to avoid and find integer overflows.
Code analysis | Sample
Be beyond any doubt, it’s fairly made by myself as a case, this would likely never appear up in genuine life.
#include<stdio.h>
#include<string.h>
#include<stdlib.h>int main(int argc, char *argv[])
{char buffer[100];
if(argc < 3)
int Integer_value;
unsigned short sixteen_bits;
{
printf("No input provided...!");
return -1;
}Integer_value = atoi(argv[1]);
sixteen_bits = Integer_value;if(sixteen_bits >= 100)
{
printf("******* Oops!! *******\n");
return -1;
}printf("sixteen_bits = %d\n", sixteen_bits);
return 0;
memcpy(buffer, argv[2], Integer_value);
buffer[Integer_value] = '\0';
printf("%s\n", buffer);
}
I’ll show the different kinda outputs:

Case 1: *** When no I/P provided. ***
if(argc < 3)
{
printf("No input provided...!");
return -1;
}Case 2: *** O/P ***
printf("sixteen_bits = %d\n", sixteen_bits);
memcpy(buffer, argv[2], Integer_value);
buffer[Integer_value] = '\0';
printf("%s\n", buffer);return 0;
Case 3: *** “>= 100” ***
if(sixteen_bits >= 100)
{
printf("******* Oops!! *******\n");
return -1;
}Presently, where’s the issue exists within the above piece of code??

Subsequently, it’s affirmed that the code is vulnerable. The length argument is taken from the command line and held within the integer variable When this value is exchanged into the unsigned short integer, it is truncated in case the value is as well incredible to fit into.
Integer_value = atoi(argv[1]);
sixteen_bits = Integer_value;
unsigned short int data type denotes a 16 — bit integer and does not use a bit to store the sign. Hence, it can hold only positive values between 0 and 65535. So, the value is exchanged into the unsigned short integer, it’ll overflow.
65535 in binary is 1111111111111111 (length= 16)
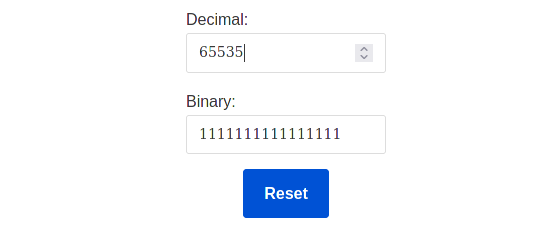
65536 in binary is 10000000000000000 (length= 17)

It works on the intended way until the input stays under 65535. If the input exceeds, the value between 65536 to 65635 it’ll be a segmentation fault.

Because of this, it is conceivable to bypass the bounds check and flood the buffer. After this, standard stack smashing strategies can be utilized to exploit the process.
I’m dropping off the case, letting you discover yourself a way to exploit it.

NOTE:
1) Not every segfault is exploitable. but it’s still a bug, and if you have no clue about exploitation, still better to assume it’s exploitable, and fix it.
2) Additionally, storing a value lesser than the least supported value is called integer underflow.
3) Integer overflow on its own doesn’t lead to arbitrary code execution, but an integer overflow “might lead” to stack overflow or heap overflow which might result in subjective code execution.
The above case appears a stack-related issue, now let’s check an outline on Heap.
/** Vulnerable piece of code that I found online. **/int myfunction(int *array, int len){
int *myarray, i;myarray = malloc(len * sizeof(int));
if(myarray == NULL)
{
return -1;
}for(i = 0; i < len; i++)
{
myarray[i] = array[i];
}
return myarray;
}
This code is vulnerable to an Integer-Overflow, which can cause the size of the buffer allocated to be much smaller than is required. If the “len” parameter is larger than intended, eg: 0x100000004 is as well enormous to store as a 32-bit numbers (max- 0x7FFFFFFF), so this implies that malloc( ) will allocate as it were a 4-byte buffer, and the loop to copy data into the newly allocated array will write way past the end of this allocated buffer. This results in a heap overflow.
In coming write-ups, I’ll be back with aggressive exploitation strategies. But now, I wanna wrap up it off pleasantly. I wanna instruct you a lot of stuff approximately stack & Stack-based Buffer flood vulnerabilities and bypassing the security mitigations, etc. After completing all those stuff let’s investigate the world of the heap !! Stay inquisitive..! 😎😎
Feel free to connect on Twitter @7h3h4ckv157

如有侵权请联系:admin#unsafe.sh