The Good
“Stalkerware” is a term that refers to commercial software used to monitor the digital activities of others, typically without their consent. Although there are legitimate uses for location tracking (think fleet vehicles) and activity monitoring (parental monitoring, say) some companies market software that stretches these boundaries and is intended to appeal to an audience of abusive partners, unscrupulous employers, cyber stalkers, and others who seek to control the behavior of their victims through covert surveillance. In the security industry, we often end up referring to these as PUPs or PUAs (Potentially Unwanted Programs/Applications) to alert users to their presence when detected.
However, in the case of “SpyFone”, they went beyond even the usual boundaries of commercial spyware, with a catalog of misbehavior that has now been called out by the FTC. The company and CEO have been found to have committed several misdeeds including illegally harvesting private information from SpyFone users and failing to secure that information from other hackers and identity thieves. They also failed to comply with a previous FTC order to fully investigate a hack of the company’s servers back in 2018.
The FTC has now banned both company and CEO from any further trading in surveillance software, not just in the US, but worldwide. In addition, the FTC has ordered the company behind SpyFone (Support King) and the CEO to “delete any information illegally collected from their stalkerware apps”, as well as “notify owners of devices on which SpyFone’s apps were installed that their devices might have been monitored and the device may not be secure”. Hopefully, this will serve as an example to other ne’er-do-wells thinking of dipping their feet into the murky world of Stalkerware apps: the FTC is watching you.
The Bad
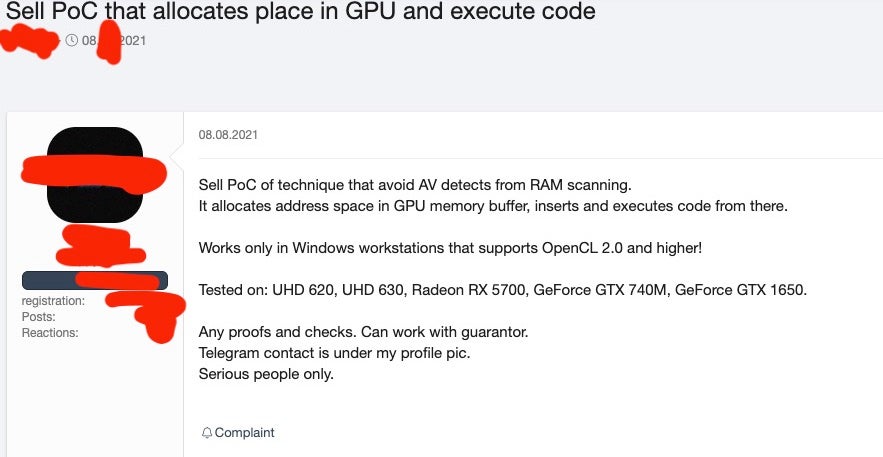
This week, news broke of a particular seller on one underground forum selling a new evasion method with the hope of appealing to cybercriminals looking for an edge. The seller offered a Proof-of-Concept to execute code in GPUs made by Intel, AMD and Nvidia. Executing code directly from the GPU is attractive for malicious purposes as it may provide an avenue to bypass certain types of endpoint security controls.
The seller states that the tool “allocates address space in GPU memory buffer, inserts and executes code from there”. They go on further to indicate that the technique can be used against Windows systems running OpenCL 2x and above. The original advertisement went up for sale in early August 2021. On the 25th of August, the same seller updated the thread simply stating “Sold”.
There have been other methodologies published in the past for executing code out of GPU, and other participants in the same forum were quick to point this out to the seller.
While the novelty of this seller’s product may be up for debate, the threat of such a tactic should be taken seriously. Attempting to execute code via various side channels has always been advantageous to enterprising attackers. There is plenty of academic research out there documenting similar tactics as well as in-the-wild examples. Whether the apparent buyer of this PoC will turn up on our radar remains to be seen, but we suspect that if the developer’s code has genuine utility, we’ll see that ‘Sold’ message revert to ‘For Sale’ again before too long.
The Ugly
An article published this week by NPR raised some fresh, and worrying, concerns related to the recent rash of MS Exchange server hacks committed by Chinese APT actor Hafnium. The article suggests that those attacks and others over recent years may have been committed specifically for the purpose of feeding and training a Chinese-built AI system with data on US citizens.

The article notes that four years ago, China was producing more research related to AI than any other country, and that it currently has over 1,000 AI firms. Combine this with the fact that it’s been an open secret among Western intelligence agencies that China is on a campaign to steal massive amounts of data and what might seem like random, untargeted attacks on small and medium-sized businesses running on-premises Exchange servers starts to take on a different complexion.
Former director of the NCSC (National Counterintelligence and Security Center) William Evanina recently testified in front of the Senate Committee on Intelligence claiming that a catalog of hacks in recent years had hovered up the PII (personally identifiable information) of more than 80% of all Americans.
“The Chinese have more data than we have on ourselves…So you have the OPM data breach…you have an entire security clearance file for someone, you have Anthem records, you have his Marriott point record, credit cards, Equifax, his loans, his mortgages, his credit score. They know everything about you…”
To what end? The South China Morning Post claims the country has a vision to be a world leader in AI by 2030 with a focus on “social governance, national defence construction, and industrial value chain”. According to Evanina, the name of the game is manipulation, at home and abroad. Whether it’s coercing individuals or stealing IP or curbing criticism, we all know that data means power, and China appears to be grabbing all the data it can get its hands on. Not for nothing has President Biden declared that cyber security is a matter of national and economic security, but it’s not just the government that needs to up its game. We are all targets now. We owe it to ourselves and each other to take our own cybersecurity posture more seriously.
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.
Read more about Cyber Security
- Hive Attacks | Analysis of the Human-Operated Ransomware Targeting Healthcare
- Feature Spotlight: Ease Deployment and Minimize Risk With Ranger Pro™
- 5 Traits of a Great Endpoint Security System
- 6 Reasons Why Ransomware Is Not Going To Be Stopped
- What Is A Malware File Signature (And How Does It Work)?
- HiveNightmare | Protecting Windows 10 Security Account Manager Against CVE-2021-36934
- MeteorExpress | Mysterious Wiper Paralyzes Iranian Trains with Epic Troll
- Detecting XLoader | A macOS ‘Malware-as-a-Service’ Info Stealer and Keylogger
- PrintNightmare | Latest Patch Almost Puts Microsoft Vulnerability to Bed
