

Before we go deep into the ACTUAL bypasses section, It’s really important to understand what is a WAF(Web application firewall) and it’s types.
Hi guys, welcome to this new blog and here, we are talking about WAFs which is considered as one of the biggest enemies of hackers. Well, it is also important to keep in mind WAF is not same as usual firewalls(Network firewalls). So here is a brief difference: A Web Application Firewall is a network security firewall solution that protects web applications from HTTP/S and web application-based security vulnerabilities where Network Firewall is a device which controls access to a secured LAN network to protect it from unauthorized access.
So, in common terms, A WAF sits between external users and web applications to analyze all HTTP communication. It then detects and blocks malicious requests before they reach users or web applications. As a result, WAFs secure business-critical web applications and web servers from zero-day threats and other application-layer attacks. This is increasingly important as businesses expand into new digital initiatives, which can leave new web applications and application programming interfaces (APIs) vulnerable to attacks. If you want to read further about it, click here:) Also, you can go through this image for a general idea:
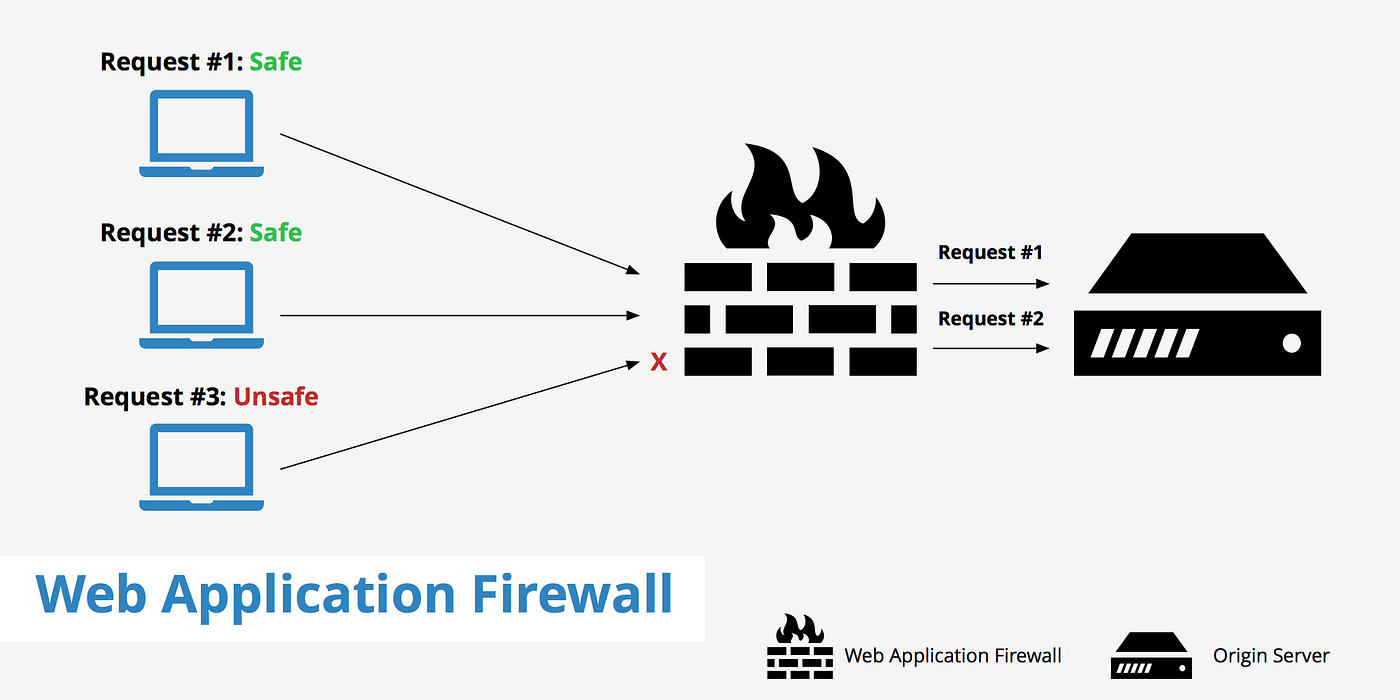
Now, there are different types of WAF and so are the providers. Basically there are three types of WAFs:
- Network based WAFs
- Host-based WAFs
- Cloud based WAFs
First one, Network basesd WAFs are hardware based and provide latency reduction benefits due to the local installation. This means NWAF is installed close to the application server and is easy to access.
Host-based web application firewalls exist as modules for a web server. It is a significantly cheaper solution compared to hardware-based WAFs, which are meant for small web applications. Most of the software WAFs are made to be easily integrated with popular web servers.
Cloud-based web application firewalls provide similar benefits as other software-based WAF solutions, such as low cost and the lack of on-premises resources that you must manage. Cloud-based solutions are an excellent choice when you don’t want to limit yourself with performance capabilities or are aiming to avoid a system that requires maintenance. Cloud service providers can offer unlimited hardware pool with competent setup and support.
Enough talk, let’s see some points as an attacker view. The most common attacks which needs a WAF bypass are XSS and SQLi. Or you can also say a few types of injection attacks need bypasses. So we will see how actually a bypass work and why it works when WAF is built to secure attacks:) Here we are taking an example of Cloudflare since we see it a lot in real life scenarios. However there are other CDNs which are being used for eg.:
- Akamai.
- Sucuri.
- Amazon CloudFront.
- Stackpath.
- Fastly.
Suppose(just suppose), You got a search field and tried a simple payload like <script>alert(1)</script>. It didn’t work:( Now you tried another one, this time “><img src=x onerror=alert(1)>. This didn’t work either. Now, when you check, website blocked you and you need to go back now. Something like this:

Here, you should assume there is a firewall behind this which is preventing you from entering any filtered character. That’s why it was implemented right! Okay, so this is the place where BYPASSES come in play. Bypasses are simply the techeniques to evasing the filters. So, put your hacker mind and try something out of the box here. We will take a normal payload to understand how it bypasses the WAF. Let’s look at this payload:
%22%3E%3Cimg%20src%3Dx%20onerror%3Dalert(1)%3E
This is same as “><img src=x onerror=alert(1)> but sometimes encoding it might work. Now the question is why did WAF accept this payload where this is also going with “alert”. Simply understand like this: WAFs have some defined rules which they follow upon kind of a checklist containing filtered characters and words. So here a simple encoding will work if it is not filtered in that checklist. However, these days WAFs are quite advanced and they even filter base-64 encoding. Anyways, this is the basic idea why our payloads bypass the WAFs.
There are multiple ways to bypass a WAF for XSS. You can always check it with Google and you should get a lot of payloads and cheat-sheets but I am including some of them:
- OWASP Filter evasion cheat-sheet
- Cheat sheet from citybasebrooks
- Payloads by HackTricks
When we try to exploit SQL injections, WAFs restricts us a lot of times and it don’t let us go ahead with our payload. For eg.:if /?id=1+union+select+1,2,3/* is being blocked by firewall, we can try it in this way:
/?id=1+un/**/ion+sel/**/ect+1,2,3 —
And, if the application is vulnerable to SQLi, the 2nd one will bypass it. Here, what we did is we sent our payload to server in a way that it took it as it is but we know it will get executed as the first one. Since it was blocking union, we breaked it and sent it with /**/. WAF didn’t block it since it was not filtered or organised to be blocked. Similarly, if union select 1,2,3,4,5#”] is being blocked, we can split “select” into something like se”,”lect 1,2,3,4,5 and it should go well. Following are some lists for SQLi filter evasions:
Well, there are few more things to mention. Before you go to bypass it, some things are there which will help you to identify the backstage story. Until you know which firewall you are coming across, you can’t try blindly. So there are few studd to figure that out:
The second link which I have mentioned is I think one of the best things for WAFs. It works same like LiveOverflow’s can I take over XYZ. You can check the different CDNs and WAFs details for eg.:
Cloudflare
- Detectability: Easy
- Detection Methodology:
- Response headers might have
cf-rayfield value. Serverheader field has valuecloudflare.Set-Cookieresponse headers have__cfuid=cookie field.- Page content might have
Attention Required!orCloudflare Ray ID:. - Page content may contain
DDoS protection by Cloudflareas text. - You may encounter
CLOUDFLARE_ERROR_500S_BOXupon hitting invalid URLs.
I highly recommend checking that and it should help you a lot.
WAFs have been always challanging to be bypassed but there is some serious learning as well. And yeah! you can get quite good amount if you can escalate it to SQLi somehow. So it’s always a win-win. There are advance techniques as well and the more you dig deeper, the more ideas you gain.
Well, that would be everything for this blog and I hope you liked it. If you did, go ahead and share it in community:) You can follow me on twitter for any other related stuff and I highly appreciate your inputs whether it is suggestions or additions I need to do:)
Take care, happy hacking!
Adios ❤
Twitter:- @manasH4rsh
如有侵权请联系:admin#unsafe.sh