…
This short write-up is about a vulnerability in Facebook Lite that allowed anyone to be invincible to blocking for Facebook Lite Users.
…
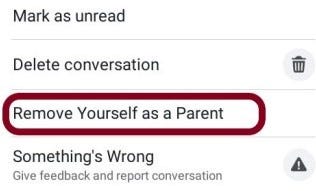
Using Messenger Kids; users can create a messaging account of their children. Users can also choose to add any of their Facebook friends as a parent/guardian of the kid. After this, they are automatically added as one of the kid’s guardians without their consent or without any sort of invitation. However, they can remove themselves from the guardian role if they want; using the Facebook web or the Facebook app. But, there was no such feature in Facebook lite to remove oneself from the role when added as a guardian of a kid.
> Why was this thing a problem?
Because there’s a policy in Facebook that a parent account cannot block the messages of its own kid’s account.
Now, Using these two main points, an attacker could simply create an attack scenario where he could victimize any user with whom s/he is a friend. Simply, he could make a Messenger Kid Account and add the victim in the parent role of the Kid. This will allow him/her to message the victim unlimitedly using the kid account without ever being blocked.
Even if the victim blocks the attacker’s real account, there was no way for the victim to block the messages of the Kid Account using Facebook Lite.
REPRODUCTION STEPS
==
1. Attacker goes to the messenger kids control section (using web or app).
2. Attacker then adds Victim as a guardian of the kid’s account.
3. Victim gets the notification (User A has added you as a guardian of the ….).
4. Victim finds no way to remove himself from the role.
5. Attacker then opens the kid’s account using Messenger Kids and messages the Victim.
6. Victim tries to block the kid’s messages, but cannot.
7. Victim then blocks Attacker from messaging as well as from Facebook.
8. Attacker can still message Victim using the kid’s account forever without ever being blocked or without the fear of being blocked.
Or, you can see the POC Video HERE.
…
Timeline of the report thread
Reported — Friday, 20 November 2020
Pre-Triaged — Wednesday, 25 November 2020
Triaged — Thursday, 26 November 2020
Shared additional info — Thursday, 17 December 2020
Asked for an update — Friday, 1 January 2021
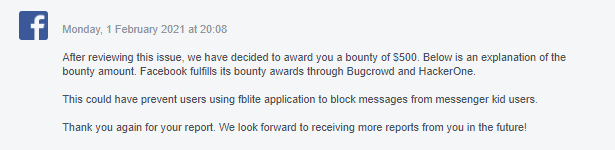
Bounty Awarded —Monday, 1 February 2021
Fixed — Wednesday, 17 February 2021
Fixed confirmed — Tuesday, 23 February 2021
Bypass sent [producable in mbasic.facebook.com & m.facebook.com] — — Tuesday, 23 February 2021
Bypass not accepted [Reason: Not high impact for those sites] & report finally closed — Monday, 1 March 2021
…
Thank you for reading this write-up about a simple vulnerability. If you have any suggestions/queries, I’m available on Facebook/ Instagram.
…
如有侵权请联系:admin#unsafe.sh