SEC Consult SA-20260218-0 :: Multiple Critical Vulnerabilities in NesterSoft WorkTime (on-prem/cloud)
嗯,用户让我帮忙总结一下这篇文章的内容,控制在一百个字以内,而且不需要用“文章内容总结”或者“这篇文章”这样的开头。直接写文章描述即可。 首先,我需要快速浏览一下这篇文章。看起来这是一份安全公告,来自SEC Consult Vulnerability Lab。他们发现了NesterSoft WorkTime软件中的多个严重漏洞。这个软件用于员工监控,所以安全问题可能很严重。 文章里提到了五个CVE编号,分别是CVE-2025-15563、CVE-2025-15562、CVE-2025-15561、CVE-2025-15560和CVE-2025-15559。每个漏洞都有不同的影响,比如操作系统命令注入、SQL注入、本地权限提升、反射型跨站脚本(XSS)以及由于访问控制不当导致的拒绝服务。 接下来,文章指出这些漏洞影响了WorkTime的所有版本,直到11.8.8,并且目前还没有补丁可用,因为厂商没有回应。这可能意味着用户需要自己采取措施来缓解风险。 然后,我需要把这些信息浓缩到一百个字以内。重点包括:发现的漏洞数量、软件名称、漏洞类型、影响版本以及厂商未响应的情况。 最后,确保语言简洁明了,直接描述内容,不使用任何开头的模板。 </think> SEC Consult披露NesterSoft WorkTime存在多个严重漏洞(CVE-2025-15563至15559),包括未认证OS命令注入、SQL注入、本地权限提升等,影响版本<=11.8.8。厂商未回应修复请求。 2026-2-22 18:3:29 Author: seclists.org(查看原文) 阅读量:1 收藏
嗯,用户让我帮忙总结一下这篇文章的内容,控制在一百个字以内,而且不需要用“文章内容总结”或者“这篇文章”这样的开头。直接写文章描述即可。 首先,我需要快速浏览一下这篇文章。看起来这是一份安全公告,来自SEC Consult Vulnerability Lab。他们发现了NesterSoft WorkTime软件中的多个严重漏洞。这个软件用于员工监控,所以安全问题可能很严重。 文章里提到了五个CVE编号,分别是CVE-2025-15563、CVE-2025-15562、CVE-2025-15561、CVE-2025-15560和CVE-2025-15559。每个漏洞都有不同的影响,比如操作系统命令注入、SQL注入、本地权限提升、反射型跨站脚本(XSS)以及由于访问控制不当导致的拒绝服务。 接下来,文章指出这些漏洞影响了WorkTime的所有版本,直到11.8.8,并且目前还没有补丁可用,因为厂商没有回应。这可能意味着用户需要自己采取措施来缓解风险。 然后,我需要把这些信息浓缩到一百个字以内。重点包括:发现的漏洞数量、软件名称、漏洞类型、影响版本以及厂商未响应的情况。 最后,确保语言简洁明了,直接描述内容,不使用任何开头的模板。 </think> SEC Consult披露NesterSoft WorkTime存在多个严重漏洞(CVE-2025-15563至15559),包括未认证OS命令注入、SQL注入、本地权限提升等,影响版本<=11.8.8。厂商未回应修复请求。 2026-2-22 18:3:29 Author: seclists.org(查看原文) 阅读量:1 收藏

Full Disclosure mailing list archives
From: SEC Consult Vulnerability Lab via Fulldisclosure <fulldisclosure () seclists org>
Date: Wed, 18 Feb 2026 11:52:03 +0000
SEC Consult Vulnerability Lab Security Advisory < 20260218-0 >
=======================================================================
title: Multiple Critical Vulnerabilities
product: NesterSoft WorkTime (on-prem/cloud)
vulnerable version: <= 11.8.8
fixed version: No patch available, vendor unresponsive.
CVE number: CVE-2025-15563, CVE-2025-15562, CVE-2025-15561
CVE-2025-15560, CVE-2025-15559
impact: Critical
homepage:https://www.worktime.com/
found: 2025-05-22
by: Tobias Niemann (Office Bochum)
Daniel Hirschberger
Thorger Jansen (Office Bochum)
Marius Renner (Office Berlin)
SEC Consult Vulnerability Lab
An integrated part of SEC Consult, an Atos business
Europe | Asia
https://www.sec-consult.com
=======================================================================
Vendor description:
-------------------
"WorkTime is a green employee monitoring software with a primary focus on
monitoring employees' productivity. It is a non-invasive, transparent, safe,
and socially responsible technology. WorkTime offers a safe replacement for
every invasive function."
Source:https://www.worktime.com/employee-monitoring
Business recommendation:
------------------------
The vendor did not respond to our communication attempts anymore. It is currently
unclear, whether a patch is available. Please contact the vendor to request a
patch for the identified critical security issues.
SEC Consult highly recommends to perform a thorough security review of the
product conducted by security professionals to identify and resolve potential
further security issues.
Vulnerability overview/description:
-----------------------------------
1) Unauthenticated OS Command Injection (CVE-2025-15559)
An unauthenticated attacker can inject OS commands when calling a server API
endpoint. This allows an attacker to execute arbitrary commands on the
WorkTime server as NT Authority\SYSTEM with the highest privileges. Attackers
are able to access or manipulate sensitive data and take over the whole
server.
2) SQL Injection (MSSQL/Firebird Backend) (CVE-2025-15560)
An authenticated attacker with minimal permissions can exploit a SQL injection
in a WorkTime server API endpoint to inject SQL queries. If the Firebird
backend is used, attackers are able to retrieve all data from the database backend.
If the MSSQL backend is used the attacker can execute arbitrary SQL statements
on the database backend and gain access to sensitive data.
3) Local Privilege Escalation (CVE-2025-15561)
An attacker can exploit the update behavior of the WorkTime monitoring daemon
to elevate privileges on the local system to NT Authority\SYSTEM.
4) Reflected Cross-Site Scripting (XSS) (CVE-2025-15562)
A server API endpoint reflects received data into the HTML response without
applying proper encoding or filtering. This allows an attacker to execute
arbitrary JavaScript in the victim's browser if the victim opens a URL prepared
by the attacker.
5) Broken Access Control results in Denial of Service (CVE-2025-15563)
Any unauthenticated user can reset the WorkTime on-prem database configuration
by sending a specific HTTP request to the WorkTime server. No authorization check is
applied here.
Proof of concept:
-----------------
1) Unauthenticated OS Command Injection (CVE-2025-15559)
The server API call to generate and download the WorkTime client from the
WorkTime server is vulnerable against OS command injection in the "guid"
parameter. For this proof of concept the following OS command is injected:
--------------------------------------------------------------------------------
whoami > C:\secwashere
--------------------------------------------------------------------------------
The HTTP request is shown below:
--------------------------------------------------------------------------------
< PoC removed >
--------------------------------------------------------------------------------
The injected command is executed on the server as NT Authority\SYSTEM:
<command_injection.png>
2) SQL Injection (MSSQL/Firebird Backend) (CVE-2025-15560)
The following authenticated "widget" API endpoint is vulnerable. Minimal
permissions are required to access the server endpoint.
--------------------------------------------------------------------------------
POST /api/widget HTTP/1.1
Host: <server_hostname>:8080
Content-Type: multipart/form-data; boundary=---------------------------295635091325610060643320064167
Content-Length: [...]
-----------------------------295635091325610060643320064167
< removed >
-----------------------------295635091325610060643320064167--
--------------------------------------------------------------------------------
Note that the request requires a token value in the request body.
Any user that has access to the WorkTime server in any role has access to a
valid token. The three parameters employee, computer and department are injectable.
If the Firebird database backend is configured, the injection can be exploited
using the following sqlmap command:
--------------------------------------------------------------------------------
< PoC removed >
--------------------------------------------------------------------------------
If the MSSQL backend is used the following sqlmap command can be used
with the request from above:
--------------------------------------------------------------------------------
< PoC removed >
--------------------------------------------------------------------------------
Depending on the used MSSQL database user and the database configuration
the injection can also be exploited to execute OS commands on the server.
3) Local Privilege Escalation (CVE-2025-15561)
To exploit the vulnerability, the attacker must first create an executable that
should be executed with elevated privileges. For this proof of concept the
following C code was used.
--------------------------------------------------------------------------------
< PoC removed >
--------------------------------------------------------------------------------
It is required to add versioning information during the linking process.
Otherwise WorkTime will not execute the created binary. Any resource file can be
used:
--------------------------------------------------------------------------------
1 VERSIONINFO
FILEVERSION 1,0,0,0
PRODUCTVERSION 1,0,0,0
FILEFLAGSMASK 0x3f
FILEFLAGS 0x0
FILEOS 0x40004
FILETYPE 0x1
FILESUBTYPE 0x0
BEGIN
BLOCK "StringFileInfo"
BEGIN
BLOCK "040904b0" // Language and code page
BEGIN
VALUE "CompanyName", "Your Company"
VALUE "FileDescription", "Your Application Description"
VALUE "FileVersion", "1.0.0.0"
VALUE "InternalName", "YourApp"
VALUE "OriginalFilename", "YourApp.exe"
VALUE "ProductName", "Your Product"
VALUE "ProductVersion", "1.0.0.0"
END
END
BLOCK "VarFileInfo"
BEGIN
VALUE "Translation", 0x409, 1200
END
--------------------------------------------------------------------------------
Compile the PoC code:
--------------------------------------------------------------------------------
$ x86_64-w64-mingw32-windres resource.rc -o resource.o
$ x86_64-w64-mingw32-gcc exec.c resource.o
--------------------------------------------------------------------------------
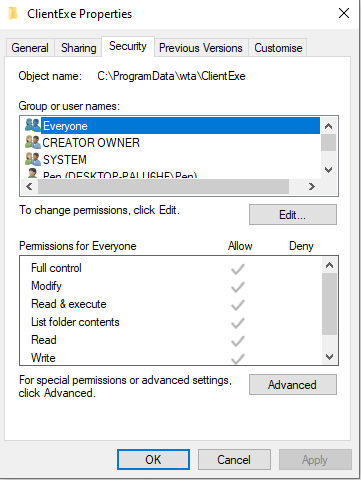
The resulting executable must now be renamed to WTWatch.exe and be dropped
in C:\ProgramData\wta\ClientExe.
The folder is writable by Everyone:
<folder_permissions.png>
After dropping the executable, it is executed by the WorkTime monitoring daemon
as NT Authority\SYSTEM:
<priv_esc.png>
4) Reflected Cross-Site Scripting (XSS) (CVE-2025-15562)
As a proof of concept the following JavaScript payload was used:
--------------------------------------------------------------------------------
alert(document.location)
--------------------------------------------------------------------------------
The type parameter in the POST body is reflected back into the HTML response:
--------------------------------------------------------------------------------
POST /report/internet/urls HTTP/1.1
Host: <server_hostname>:8079
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Cookie: PHPSESSID=[...]; aup_accept=accept
type="><script>alert(document.cookie)</script>
--------------------------------------------------------------------------------
The injected payload is reflected back into the HTTP response without proper
encoding or filtering and the payload is executed:
<xss.png>
5) Broken Access Control results in Denial of Service (CVE-2025-15563)
An unauthenticated attacker can access the following URL to reset the
server's configured database.
< PoC URL removed >
If the attacker presses the displayed button the browser sends the following
unauthenticated HTTP request which resets the database configuration:
--------------------------------------------------------------------------------
< Poc removed >
--------------------------------------------------------------------------------
Vulnerable / tested versions:
-----------------------------
The following version has been tested which was the latest version available
at the time of the test:
* WorkTime v11.8.8
Vendor contact timeline:
------------------------
2025-07-09: Initial mail to the vendor (info () worktime com)
2025-07-23: First vendor response, requesting unencrypted advisory.
2025-07-29: Sending the advisory via email.
2025-09-29: Asking for a status update regarding any fixes or roadmap, asking
whether we should reserve CVE numbers or the vendor.
2025-09-30: Customer support answers that "Firebird for On-Premises" (CVE-2025-24975)
is fixed. They ask us which other CVEs we have identified.
2025-10-02: Replying to vendor that we submitted the advisory including all details
on 29th July and that CVE-2025-24975 has nothing to do with our advisory.
No response.
2025-11-03: Asking the vendor for a status update, informing them about our disclosure
deadline again and setting preliminary release date to 19th November.
2025-11-03: Vendor support responds to check with the technical team.
2025-11-17: Vendor responds they are actively working on it this week to analyze
the issues and report back to us within a week.
2026-02-04: No response from the vendor so far. Reserved CVE numbers, asking for
status update / fixed version numbers, informing vendor about planned
public release on 18th February.
2026-02-18: Still no response, public release of advisory.
Solution:
---------
The vendor did not respond to our communication attempts anymore. It is currently
unclear, whether a patch is available. Please contact the vendor to request a
patch for the identified critical security issues.
Workaround:
-----------
None
Advisory URL:
-------------
https://sec-consult.com/vulnerability-lab/
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
SEC Consult Vulnerability Lab
An integrated part of SEC Consult, an Atos business
Europe | Asia
About SEC Consult Vulnerability Lab
The SEC Consult Vulnerability Lab is an integrated part of SEC Consult, an
Atos business. It ensures the continued knowledge gain of SEC Consult in the
field of network and application security to stay ahead of the attacker. The
SEC Consult Vulnerability Lab supports high-quality penetration testing and
the evaluation of new offensive and defensive technologies for our customers.
Hence our customers obtain the most current information about vulnerabilities
and valid recommendation about the risk profile of new technologies.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Interested to work with the experts of SEC Consult?
Send us your applicationhttps://sec-consult.com/career/
Interested in improving your cyber security with the experts of SEC Consult?
Contact our local officeshttps://sec-consult.com/contact/
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Mail: security-research at sec-consult dot com
Web:https://www.sec-consult.com
Blog:https://blog.sec-consult.com
X:https://x.com/sec_consult
EOF Tobias Niemann, Daniel Hirschberger, Thorger Jansen, Marius Renner / @2026
Attachment:
smime.p7s
Description: S/MIME Cryptographic Signature
_______________________________________________ Sent through the Full Disclosure mailing list https://nmap.org/mailman/listinfo/fulldisclosure Web Archives & RSS: https://seclists.org/fulldisclosure/
Current thread:
- SEC Consult SA-20260218-0 :: Multiple Critical Vulnerabilities in NesterSoft WorkTime (on-prem/cloud) SEC Consult Vulnerability Lab via Fulldisclosure (Feb 22)
文章来源: https://seclists.org/fulldisclosure/2026/Feb/31
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh



