
好的,我现在需要帮用户总结这篇文章的内容,控制在100字以内。首先,我得仔细阅读文章,理解其主要内容。 文章主要讲的是Intellexa公司的Predator间谍软件如何隐藏iOS设备的录音指示器。它通过劫持系统指示器,而不是利用iOS漏洞,来实现这一点。苹果在iOS 14中引入了这些指示器,用来提醒用户摄像头或麦克风被使用的情况。 接下来,文章详细描述了Predator的工作机制。研究人员Jamf分析了样本,发现Predator通过在SpringBoard中使用一个钩子函数(HiddenDot::setupHook()),每当传感器活动变化时调用该方法。这样就能拦截传感器状态更新,阻止它们到达UI层,从而隐藏绿点或红点。 此外,文章还提到Predator在处理VoIP录音时依赖同样的隐藏机制,并且通过ARM64指令模式匹配和PAC重定向来绕过摄像头权限检查。虽然苹果没有回应评论请求,但Jamf指出了一些恶意进程的技术迹象。 现在,我需要将这些信息浓缩到100字以内。重点包括:Predator间谍软件、隐藏iOS录音指示器、劫持系统指示器、不利用漏洞、苹果的录音指示器功能、技术机制(钩子函数、传感器拦截)、以及苹果未回应的情况。 确保语言简洁明了,避免使用复杂的术语。同时,开头不需要“这篇文章总结了...”之类的句子,直接描述内容即可。 </think> Intellexa的Predator间谍软件可隐藏iOS设备的录音指示器,在不触发系统漏洞的情况下通过劫持传感器活动更新来实现隐蔽操作。苹果在iOS 14中引入了绿色或橙色点作为录音提示功能以提高用户隐私保护意识。 2026-2-21 16:30:21 Author: www.bleepingcomputer.com(查看原文) 阅读量:3 收藏

Intellexa’s Predator spyware can hide iOS recording indicators while secretly streaming camera and microphone feeds to its operators.
The malware does not exploit any iOS vulnerability but leverages previously obtained kernel-level access to hijack system indicators that would otherwise expose its surveillance operation.
Apple introduced recording indicators on the status bar in iOS 14 to alert users when the camera or microphone is in use, displaying a green or an orange dot, respectively.
US-sanctioned surveillance firm Intellexa developed the Predator commercial spyware and delivered it in attacks that exploited Apple and Chrome zero-day flaws and through 0-click infection mechanisms.
While its ability to suppress camera and microphone activity indicators is well known, it was unclear how the mechanism worked.

Source: Jamf
How Predator hides recording
Researchers at mobile device management company Jamf analyzed Predator samples and documented the process of hiding the privacy-related indicators.
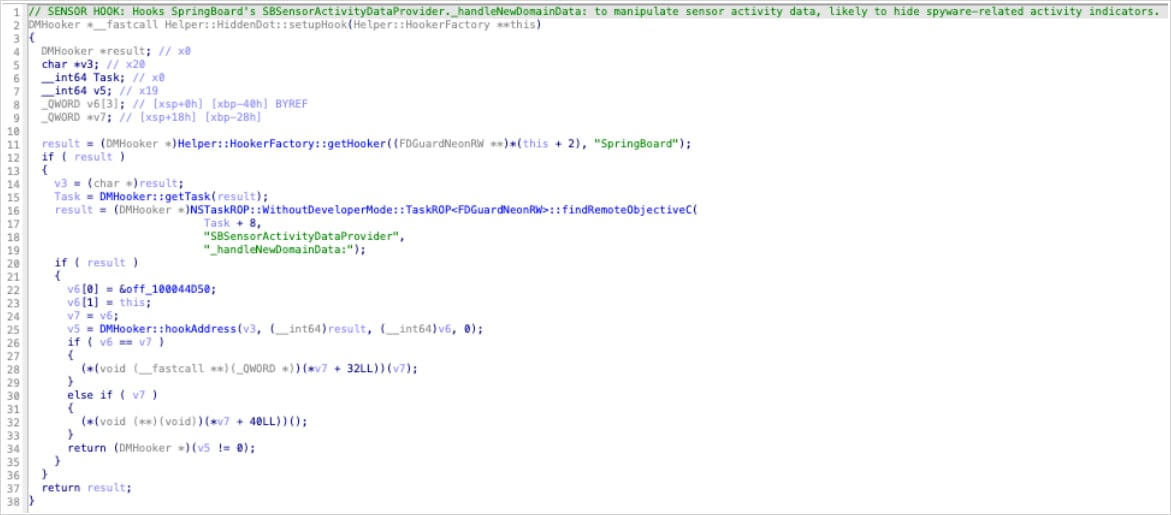
According to Jamf, Predator hides all recording indicators on iOS 14 by using a single hook function (‘HiddenDot::setupHook()’) inside SpringBoard, invoking the method whenever sensor activity changes (upon camera or microphone activation).
By intercepting it, Predator prevents sensor activity updates from ever reaching the UI layer, so the green or red dot never lights up.
“The target method _handleNewDomainData: is called by iOS whenever sensor activity changes - camera turns on, microphone activates, etc.,” Jamf researchers explain.
“By hooking this single method, Predator intercepts ALL sensor status updates before they reach the indicator display system.”
Source: Jamf
The hook works by nullifying the object responsible for sensor updates (SBSensorActivityDataProvider in SpringBoard). In Objective-C, calls to a null object are silently ignored, so SpringBoard never processes the camera or microphone activation, and no indicator appears.
Because SBSensorActivityDataProvider aggregates all sensor activity, this single hook disables both the camera and the microphone indicators.
The researchers also found “dead code” that attempted to hook ‘SBRecordingIndicatorManager’ directly. However, it doesn’t execute, and is likely an earlier development path that was abandoned in favor of the better approach that intercepts sensor data upstream.
In the case of VoIP recordings, which Predator also supports, the module responsible lacks an indicator-suppression mechanism, so it relies on the HiddenDot function for stealth.
Jamf further explains that camera access is enabled through a separate module that locates internal camera functions using ARM64 instruction pattern matching and Pointer Authentication Code (PAC) redirection to bypass camera permission checks.
Without indicators lighting up on the status bar, the spyware activity remains completely hidden to the regular user.
Jamf notes that technical analysis reveals the signs of the malicious processes, such as unexpected memory mappings or exception ports in SpringBoard and mediaserverd, breakpoint-based hooks, and audio files written by mediaserverd to unusual paths.
BleepingComputer has contacted Apple with a request for a comment on Jamf’s findings, but the company never responded.
The future of IT infrastructure is here
Modern IT infrastructure moves faster than manual workflows can handle.
In this new Tines guide, learn how your team can reduce hidden manual delays, improve reliability through automated response, and build and scale intelligent workflows on top of tools you already use.
如有侵权请联系:admin#unsafe.sh

