嗯,用户让我用中文总结这篇文章,控制在一百个字以内,而且不需要特定的开头。首先,我需要通读整篇文章,抓住主要内容。 文章讲的是Notepad++的托管服务器被黑,导致更新流量被重定向到恶意服务器。攻击者是来自中国的莲花 Blossom APT 组织。他们没有利用Notepad++本身的漏洞,而是通过托管提供商的基础设施进行的。攻击持续了大约半年,使用了自定义后门Chrysalis和一些加载器来隐藏恶意代码。 接下来,我需要把这些信息浓缩到100字以内。重点包括:Notepad++托管被黑、恶意更新、莲花 Blossom APT 组织、基础设施攻击、后门Chrysalis和加载器。 然后,确保语言简洁明了,不使用复杂的术语。可能的结构是:Notepad++托管被黑导致恶意更新,与莲花 Blossom APT 组织有关,利用基础设施攻击部署后门Chrysalis和加载器。 最后检查字数是否在限制内,并且信息准确无误。 </think> Notepad++托管服务器遭网络攻击,导致用户更新流量被重定向至恶意服务器。此次攻击与疑似中国背景的莲花 Blossom APT 组织相关,利用基础设施层级的漏洞实施定向攻击,并部署了自定义后门 Chrysalis 和加载器以隐藏恶意代码执行。 2026-2-3 09:35:23 Author: securityaffairs.com(查看原文) 阅读量:2 收藏
Notepad++ infrastructure hack likely tied to China-nexus APT Lotus Blossom
Pierluigi Paganini
February 03, 2026

Rapid7 researchers say the Notepad++ hosting breach is likely linked to the China-nexus Lotus Blossom APT group.
Recently, the Notepad++ maintainer revealed that nation-state hackers compromised the hosting provider’s infrastructure, redirecting update traffic to malicious servers. The attack did not exploit flaws in Notepad++ code but intercepted updates before they reached users.
“According to the analysis provided by the security experts, the attack involved infrastructure-level compromise that allowed malicious actors to intercept and redirect update traffic destined for notepad-plus-plus.org.” reads the advisory published by the software maintainers. “The exact technical mechanism remains under investigation, though the compromise occured at the hosting provider level rather than through vulnerabilities in Notepad++ code itself. Traffic from certain targeted users was selectively redirected to attacker-controlled served malicious update manifests.”
The incident began in June 2025 and was linked by multiple researchers to a likely Chinese state-sponsored group, based on its highly selective targeting. Attackers compromised a shared hosting server until September 2, 2025, and later used stolen internal credentials to redirect Notepad++ update traffic to malicious servers until December 2.
The hosting provider moved all affected customers to a new server, fixed the vulnerabilities that were abused, and rotated all credentials that may have been exposed.
After completing these actions, the provider reviewed system logs and confirmed there was no evidence of continued attacker access or malicious activity.
The security expert found the attack ended on November 10, 2025, while the hosting provider reported possible attacker access until December 2. Combining both assessments, the compromise likely lasted from June to December 2, 2025.
Rapid7 Labs and its MDR team uncovered a sophisticated campaign tied to the China-linked APT Lotus Blossom. Active since 2009, the group runs targeted espionage against government, telecom, aviation, critical infrastructure, and media organizations, mainly in Southeast Asia and Central America. The investigation traced a compromise of Notepad++ hosting infrastructure used to deploy a new custom backdoor, dubbed Chrysalis, along with stealthy loaders that abuse Microsoft Warbird to conceal malicious code execution.
“Our investigation identified a security incident stemming from a sophisticated compromise of the infrastructure hosting Notepad++, which was subsequently used to deliver a previously undocumented custom backdoor, which we have dubbed Chrysalis.” reads the report published by Rapid7.
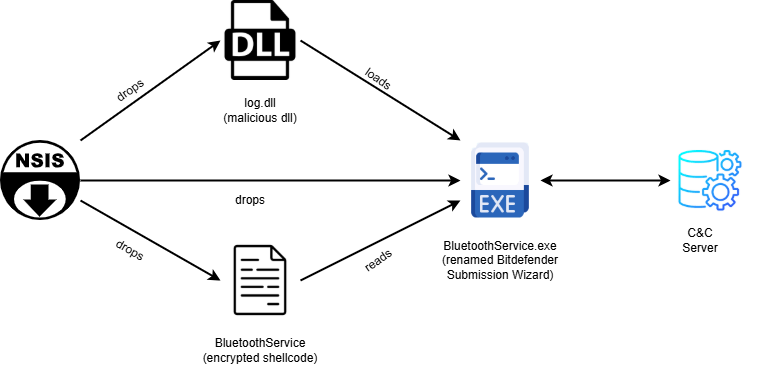
Rapid7’s MDR team traced the initial access to abuse of Notepad++ distribution infrastructure. Investigators saw notepad++.exe and GUP.exe run first, followed by a suspicious update.exe downloaded from an external IP. That file turned out to be an NSIS installer, a delivery method often used by Chinese APT groups. It dropped files into a hidden AppData folder and abused DLL sideloading through a renamed Bitdefender binary to decrypt and launch a custom backdoor called Chrysalis.
“Shortly after the execution of BluetoothService.exe, which is actually a renamed legitimate Bitdefender Submission Wizard abused for DLL sideloading, a malicious log.dll was placed alongside the executable, causing it to be loaded instead of the legitimate library.” continues the report. “Two exported functions from log.dll are called by Bitdefender Submission Wizard: LogInit and LogWrite.”
The malware relied on multiple layers of obfuscation to conceal its code and make analysis harder. It used custom API hashing to avoid calling Windows functions directly and encrypted its configuration to hide key settings. After running, it set up persistence to survive reboots, collected detailed information about the infected system, and connected to a remote command-and-control server. Through this connection, attackers could run commands, move files, and take full control of compromised machines.
Chrysalis supports full remote control, including command execution, file transfer, and interactive shells. Investigators also uncovered related loaders abusing Metasploit shellcode, Cobalt Strike beacons, and even Microsoft Warbird protections, showing long-term development and a complex, multi-stage attack chain.
Researchers attribute the campaign to Lotus Blossom based on strong overlaps with prior Symantec research, including a renamed Bitdefender tool used to sideload log.dll, similar loader chains, and shared Cobalt Strike public keys across multiple samples.
“The discovery of the Chrysalis backdoor and the Warbird loader highlights an evolution in Billbug’s capabilities. While the group continues to rely on proven techniques like DLL sideloading and service persistence, their multi-layered shellcode loader and integration of undocumented system calls (NtQuerySystemInformation) mark a clear shift toward more resilient and stealth tradecraft.” concludes the report. “What stands out is the mix of tools: the deployment of custom malware (Chrysalis) alongside commodity frameworks like Metasploit and Cobalt Strike, together with the rapid adaptation of public research (specifically the abuse of Microsoft Warbird).”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Notepad++)
如有侵权请联系:admin#unsafe.sh
