好的,我现在需要帮用户总结这篇文章的内容,控制在100字以内。首先,我得通读整篇文章,抓住主要信息。 文章讲的是WinRAR的一个漏洞CVE-2025-8088被多个威胁行为者利用。包括国家支持的APT和犯罪团伙,他们通过钓鱼攻击传播恶意软件。这个漏洞已经被修复,但即使补丁发布后,攻击者仍然在利用它。 接下来,我需要将这些信息浓缩到100字以内。重点包括:漏洞名称、影响范围、攻击者类型、攻击方式以及漏洞的影响。 要注意避免使用“文章内容总结”这样的开头,直接描述即可。同时要确保语言简洁明了。 最后检查字数,确保不超过限制。这样用户就能快速了解文章的核心内容了。 </think> 国家支持的威胁行为者和犯罪团伙利用WinRAR漏洞CVE-2025-8088进行初始访问和恶意软件传播。该漏洞允许通过恶意压缩文件执行任意代码,并被用于钓鱼攻击和传播恶意软件。尽管已修复,但多个威胁行为者仍在利用该漏洞针对政府、军事和技术部门以及企业等目标。 2026-1-29 10:53:15 Author: securityaffairs.com(查看原文) 阅读量:0 收藏
Nation-state and criminal actors leverage WinRAR flaw in attacks

Multiple threat actors exploited a now-patched critical WinRAR flaw to gain initial access and deliver various malicious payloads.
Google Threat Intelligence Group (GTIG) revealed that multiple threat actors, including APTs and financially motivated groups, are exploiting the CVE-2025-8088 flaw in RARLAB WinRAR to establish initial access and deploy a diverse array of payloads.
The WinRAR flaw CVE-2025-8088 is a directory traversal bug fixed in version 7.13 that was exploited as a zero-day in phishing attacks to deliver RomCom malware. The vulnerability is a path traversal issue affecting the Windows version of WinRAR. Attackers can exploit the vulnerability to execute arbitrary code by crafting malicious archive files. Researchers Anton Cherepanov, Peter Košinár, and Peter Strýček from ESET disclosed the flaw. Attackers can craft archives that place executables in Windows Startup folders, causing them to run at login and enabling remote code execution. ESET researchers told Bleeping Computer that threat actors actively exploited the vulnerability in spear-phishing attacks to deliver RomCom backdoors.
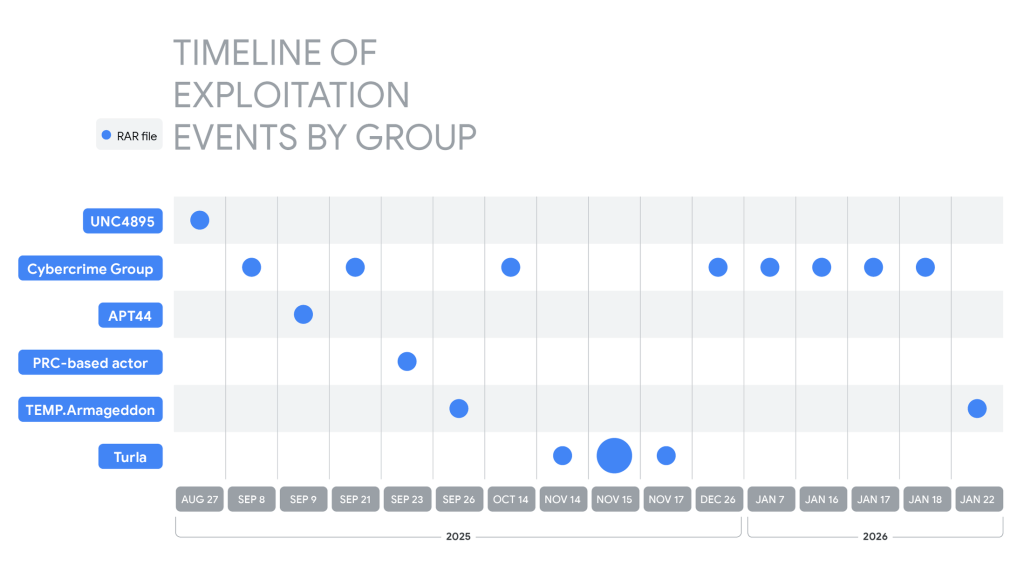
“The Google Threat Intelligence Group (GTIG) has identified widespread, active exploitation of the critical vulnerability CVE-2025-8088 in WinRAR, a popular file archiver tool for Windows, to establish initial access and deliver diverse payloads.” reads the report published by Google. “Discovered and patched in July 2025, government-backed threat actors linked to Russia and China as well as financially motivated threat actors continue to exploit this n-day across disparate operations. “
Multiple threat actors actively exploit CVE-2025-8088 in WinRAR, even after a patch became available, confirming how effective n-day vulnerabilities remain. Nation-state actors mainly target military, government, and tech sectors, echoing the large-scale abuse of the 2023 WinRAR flaw. Russian-linked actors focus heavily on Ukraine, using tailored lures to deliver malware such as NESTPACKER, STOCKSTAY, and multi-stage downloaders via malicious RAR archives. Chinese actors also abuse the flaw to deploy POISONIVY.

Cybercriminal groups quickly adopted the exploit as well, spreading commodity RATs, stealers, and phishing tools against businesses, hospitality firms, banks, and regional users across LATAM and Asia. Activity continued into early 2026.
This fast and broad adoption ties to the underground exploit market. Sellers like “zeroplayer” sell ready-made exploits, making attacks easier for both state and criminal groups and turning cyber attacks into an off-the-shelf commodity.
The actor promotes a range of high-value exploits for sale, targeting widely used software and security controls:
- In November 2025, zeroplayer claimed to have a sandbox escape RCE zero-day exploit for Microsoft Office advertising it for $300,000.
- In late September 2025, zeroplayer advertised a RCE zero-day exploit for a popular, unnamed corporate VPN provider; the price for the exploit was not specified.
- Starting in mid-October 2025, zeroplayer advertised a zero-day Local Privilege Escalation (LPE) exploit for Windows listing its price as$100,000.
- In early September 2025, zeroplayer advertised a zero-day exploit for a vulnerability that exists in an unspecified drive that would allow an attacker to disable antivirus (AV) and endpoint detection and response (EDR) software; this exploit was advertised for $80,000.
“The widespread and opportunistic exploitation of CVE-2025-8088 by a wide range of threat actors underscores its proven reliability as a commodity initial access vector. It also serves as a stark reminder of the enduring danger posed by n-day vulnerabilities.” concludes the report. “When a reliable proof of concept for a critical flaw enters the cyber criminal and espionage marketplace, adoption is instantaneous, blurring the line between sophisticated government-backed operations and financially motivated campaigns.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, WinRAR)
如有侵权请联系:admin#unsafe.sh