嗯,用户让我总结一篇关于Dormakaba安全漏洞的文章,控制在100字以内,而且不需要特定的开头。首先,我需要快速浏览文章内容,抓住关键点。 文章提到研究人员发现了超过20个漏洞,这些漏洞可能让攻击者远程解锁大型组织的门禁系统。Dormakaba的系统被广泛用于欧洲的能源、物流和机场等高安全环境。漏洞包括硬编码凭证、弱密码和缺少认证等,可能导致门禁被控制或敏感数据被盗。 接下来,我需要把这些信息浓缩到100字以内。重点包括:研究人员发现20多个漏洞、影响大型组织、漏洞类型、潜在影响以及修复情况。同时,要避免使用“这篇文章”这样的开头。 可能会这样组织:研究人员发现Dormakaba系统有20多个漏洞,允许攻击者远程解锁门禁,影响能源、物流和机场等高安全环境。漏洞包括硬编码凭证和弱密码,可能导致门被打开或数据泄露。虽然尚未有攻击报告,但厂商已修复。 检查一下字数是否在限制内,并确保信息准确无误。 </think> 研究人员发现Dormakaba门禁系统存在20多个安全漏洞,可能使攻击者远程解锁大型组织的门禁。这些系统广泛应用于欧洲能源、物流和机场等高安全环境。漏洞包括硬编码凭证和弱密码,可能导致门被打开或敏感数据泄露。尽管尚未报告实际攻击,但厂商已修复相关问题。 2026-1-27 06:14:5 Author: securityaffairs.com(查看原文) 阅读量:3 收藏
Dormakaba flaws allow to access major organizations’ doors

Researchers found over 20 flaws in Dormakaba access systems that could let attackers remotely unlock doors at major organizations.
Researchers from SEC Consult discovered and fixed more than 20 security flaws in Dormakaba physical access control systems.
The experts uncovered multiple critical vulnerabilities in Dormakaba physical access control systems based on exos 9300. These enterprise systems are widely used by large European organizations, including energy firms, logistics companies, and airports, to manage access with key cards or fingerprint readers. Dormakaba said several thousand customers were affected, including some operating in high-security environments.
“These flaws let an attacker open arbitrary doors in numerous ways, reconfigure connected controllers and peripherals without prior authentication, and much more.” reads the report published by the researchers.
Researchers identified multiple flaws in a Dormakaba access control product, including hardcoded credentials, weak passwords, missing authentication, and command injection.
The researchers examined Dormakaba’s exos 9300 physical access control ecosystem, including central management software, access managers, and door-side registration units. Exos 9300 runs on Windows Server, uses an MSSQL database, and manages access devices through networked controllers. The access managers (9200 series) run either Windows CE or Linux and expose multiple services, including web interfaces and a SOAP API used to control locks. They store sensitive data locally, such as credentials, PINs, and configurations.
SEC Consult found flaws that could let attackers unlock doors, steal access PINs, or launch further attacks. Dormakaba pointed out that exploitation would require prior access to the customer’s internal network or hardware. Dormakaba confirmed that a few thousand customers were potentially affected, including some high-security environments. Over 20 vulnerabilities were reported, and the vendor has spent the past 18 months releasing patches, hardening guidance, and working with major customers.
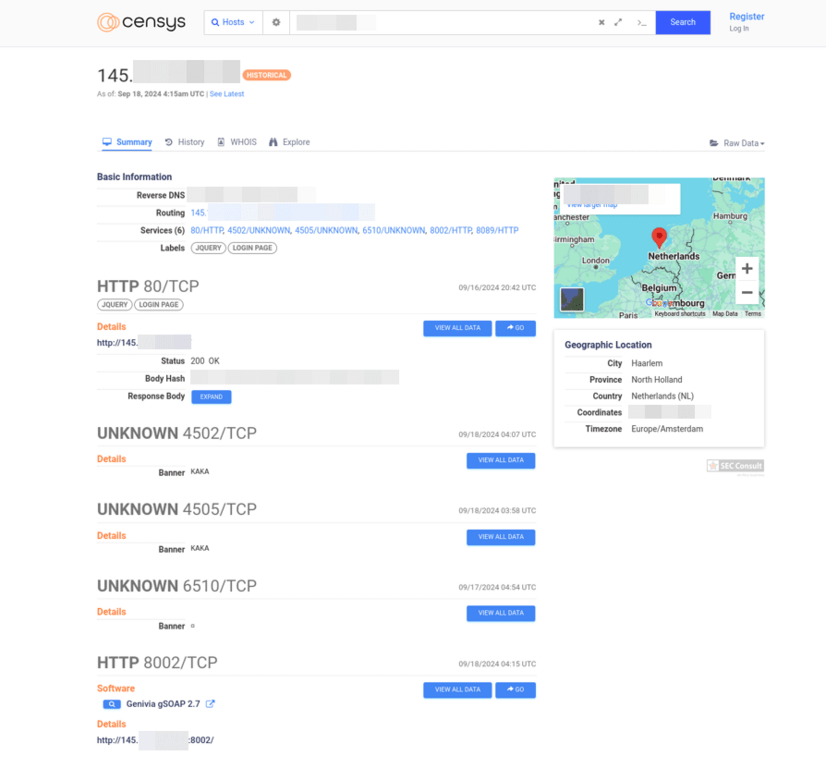
Researchers found some access managers directly exposed to the internet, mainly clustered in countries such as Spain, the Netherlands, and Switzerland. Many had web login pages and the SOAP API on port 8002 publicly accessible, allowing direct control of door relays. If exploited, the identified vulnerabilities could let attackers remotely open doors over the internet.
“Using those fingerprints, we were able to identify some access managers directly available via the internet. It was quite suspicious that they popped up in clusters and mostly in specific countries like Spain and the Netherlands, sometimes Switzerland. Most of the identified access managers on the internet had their web service including the login exposed as well as the SOAP service (Port 8002) to directly control the connected relays and doors.” reads the report. “It would be possible to exploit the vulnerabilities detailed in this blogpost to open doors via the internet.”

The researchers published a PoC video of an attack that opens doors using specially crafted requests.
At the time of this writing, Dormakaba is not aware of any attacks exploiting one of these vulnerabilities in the wild.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Dormakaba)
如有侵权请联系:admin#unsafe.sh