嗯,用户让我帮忙总结一下这篇文章的内容,控制在一百个字以内,而且不需要用“文章内容总结”这样的开头。首先,我需要仔细阅读文章,理解其主要内容。 文章主要讲的是微软报告的一个针对能源行业的多阶段网络钓鱼和商业电子邮件诈骗(BEC)活动。攻击者利用SharePoint链接和收件箱规则来窃取凭证。攻击过程分为七个阶段,包括初始访问、恶意链接点击、凭证窃取、创建收件箱规则、传播钓鱼邮件、BEC活动以及进一步的账户扩展。 接下来,我需要将这些信息浓缩到一百个字以内。要抓住关键点:目标行业是能源部门,攻击手段包括多阶段钓鱼、利用SharePoint和收件箱规则,最终导致凭证窃取和BEC活动。 然后,我需要用简洁的语言表达出来,确保不遗漏重要信息。同时,避免使用复杂的术语,让总结更易理解。 最后,检查字数是否在限制范围内,并确保内容准确无误。 </think> 微软报告称,针对能源行业的多阶段网络钓鱼和商业电子邮件诈骗活动利用SharePoint链接和收件箱规则窃取凭证,并通过恶意活动隐藏痕迹。攻击者通过初始访问、恶意链接点击、凭证窃取等步骤逐步扩大影响范围。 2026-1-26 12:38:42 Author: securityaffairs.com(查看原文) 阅读量:9 收藏
Energy sector targeted in multi-stage phishing and BEC campaign using SharePoint

Microsoft warns of a multi-stage phishing and BEC campaign hitting energy firms, abusing SharePoint links and inbox rules to steal credentials.
Microsoft reports an active multi-stage phishing campaign targeting energy sector organizations.
The campaign misused SharePoint file-sharing to deliver phishing links and created inbox rules to hide malicious activity and maintain persistence. After the initial compromise, attackers launched AiTM attacks that led to business email compromise across multiple organizations. They then abused trusted internal accounts to spread phishing internally and externally, expanding the attack’s reach. The activity highlights the complexity of AiTM campaigns and shows that effective remediation requires revoking active sessions and removing malicious inbox rules, not just resetting passwords.
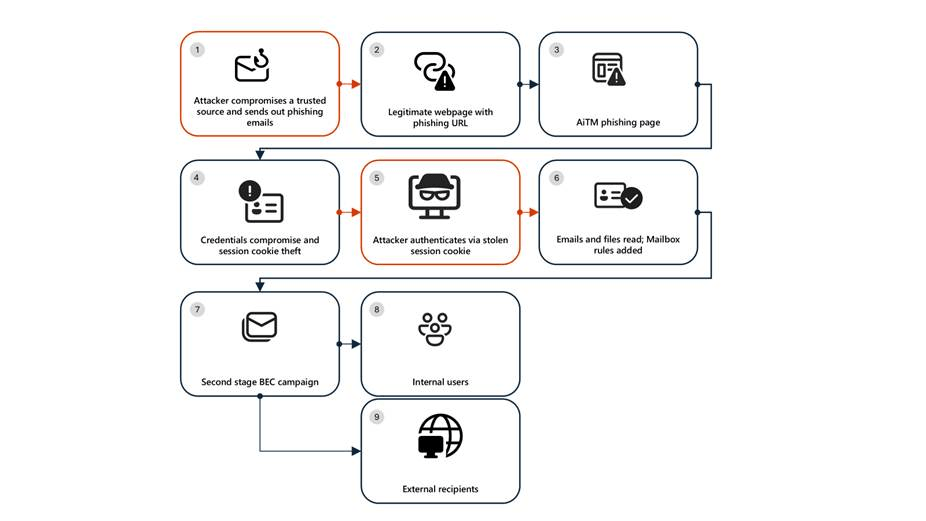
Below is the attack chain observed by Microsoft in the AiTM phishing campaign:
- Stage 1 – Initial access (trusted sender)
Attackers sent a phishing email from a compromised trusted organization. The message used a SharePoint link and realistic document-sharing subjects to appear legitimate. - Stage 2 – Malicious link click
Victims clicked the SharePoint URL. Attackers abused trusted cloud services like SharePoint to bypass email defenses. - Stage 3 – AiTM credential theft
The link redirected users to a fake sign-in page designed to steal credentials and session data. - Stage 4 – Inbox rule creation
Attackers logged in and created inbox rules to delete incoming emails and mark messages as read, hiding their activity. - Stage 5 – Phishing spread
Using the compromised account, attackers sent over 600 phishing emails to internal and external contacts and distribution lists. - Stage 6 – BEC activity
Attackers monitored replies, removed warning emails, and responded to questions to make the phishing appear legitimate. - Stage 7 – Account compromise expansion
Additional users who clicked the link were compromised through the same AiTM technique, allowing the attack to spread further.

“The recipients of the phishing emails from within the organization who clicked on the malicious URL were also targeted by another AiTM attack. Microsoft Defender Experts identified all compromised users based on the landing IP and the sign-in IP patterns.” states the report published by Microsoft.
Microsoft Defender XDR detects AiTM phishing by spotting suspicious sign-ins across multiple accounts and malicious inbox rules on compromised mailboxes. Defender Experts rapidly contained the attack by disrupting AiTM activity, auto-purging phishing emails, and helping customers recover affected identities. The researchers pointed out that effective remediation went beyond password resets and included revoking session cookies, undoing attacker-made MFA changes, and removing malicious inbox rules. Because AiTM steals active sessions, password resets alone are not enough. Microsoft stresses the continued importance of MFA, combined with conditional access policies, continuous access evaluation, advanced anti-phishing tools, and ongoing monitoring of risky sign-ins to reduce exposure and limit attacker persistence.
Microsoft provided recommendations and mitigations to reduce the impact of this threat.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, phishing)
如有侵权请联系:admin#unsafe.sh