嗯,用户让我帮忙总结一下这篇文章的内容,控制在一百个字以内,而且不需要特定的开头。首先,我需要仔细阅读文章,了解主要内容。 文章分为三个部分:The Good, The Bad, 和 The Ugly。The Good部分讲的是执法机构打击网络犯罪,比如乌克兰和德国捣毁了Black Basta勒索软件团伙,逮捕了他们的头目和其他成员。美国也起诉了一个入侵政府系统的黑客。此外,欧盟还提出了新的网络安全法规来加强保护。 The Bad部分提到朝鲜相关的威胁行为者利用Visual Studio Code来传播后门程序,攻击目标主要是软件工程师,特别是加密货币和金融科技领域的。这种方法利用了VS Code的功能来执行恶意代码。 The Ugly部分则讲述了攻击者利用配置错误的训练应用(如DVWA和OWASP Juice Shop)来入侵大型公司的云环境。这些应用通常暴露在公网,并且权限设置过于宽松,导致攻击者可以部署挖矿软件和webshell,获取云存储的访问权限。 接下来,我需要将这些内容浓缩到100字以内。要涵盖执法行动、网络犯罪手段、以及云安全问题。同时保持语言简洁明了。 可能的结构是:执法机构打击犯罪,包括逮捕勒索软件头目、起诉入侵者,并加强欧盟法规;同时网络攻击手段多样化,包括利用VS Code传播后门和利用配置错误的应用入侵云环境。 最后检查字数是否在限制内,并确保没有遗漏关键点。 </think> 执法机构打击网络犯罪活动,包括捣毁Black Basta勒索团伙、起诉入侵政府系统的黑客,并加强欧盟网络安全法规;同时网络攻击手段多样化,包括利用Visual Studio Code传播后门及通过配置错误的应用程序入侵云环境。 2026-1-23 17:21:24 Author: www.sentinelone.com(查看原文) 阅读量:1 收藏
The Good | Authorities Expose RaaS Leaders, Prosecute Identity Hackers & Tighten EU Cybersecurity Rules
Law enforcement in Ukraine and Germany have moved to dismantle Black Basta ransomware gang, confirming its leader and placing him on Europol and Interpol wanted lists. Identified as Oleg Evgenievich Nefedov, the Russian national is also known online as kurva, Washington, and S.Jimmi.
Police have also arrested two alleged Black Basta affiliates accused of breaching networks, cracking credentials, escalating privileges, and preparing ransomware attacks.
Investigators link Nefedov in a secondary role associated with the now-defunct Conti syndicate, confirming Black Basta’s evolution into a major ransomware-as-a-service (RaaS) operation responsible for hundreds of extortion incidents since 2022.

In the United States, Nicholas Moore, has pleaded guilty to breaching electronic filing systems tied to the Supreme Court of the United States, AmeriCorps, and the Department of Veterans Affairs. Prosecutors note that he repeatedly accessed the Supreme Court’s restricted system in 2023 using stolen credentials. He also breached AmeriCorps and veterans’ accounts, stealing and leaking sensitive personal and health data. Moore took to Instagram under the account @ihackedthegovernment to post screenshots of his victims’ information. He has since confessed to one count of computer fraud, punishable by one year in prison and a $100,000 fine.
New cybersecurity legislation proposed by the European Commission mandates the removal of high-risk suppliers from telecom networks and shoring up defenses against state-backed and criminal cyber threats targeting critical infrastructure. The plan builds on shortcomings in the EU’s voluntary 5G Security Toolbox, originally designed to limit member’s reliance on high-risk vendors. It also grants the Commission authority to coordinate EU-wide risk assessments across 18 critical sectors, strengthens ICT supply chain security, and streamlines voluntary certification schemes to improve resilience and technological sovereignty.
The Bad | Contagious Interview Attackers Leverage Visual Studio Code to Deploy Backdoors
DPRK-linked threat actors behind the ongoing Contagious Interview campaign are evolving their tactics by using malicious Microsoft Visual Studio Code projects to deliver backdoors.
In new research, the attackers are seen masquerading as recruiters conducting job assessments, instructing targets to clone repositories from platforms like GitHub and open them in VS Code. Once opened, specially crafted task configuration files automatically execute, fetching obfuscated JavaScript payloads hosted on Vercel domains and deploying multi-stage malware.
This novel technique, first seen last month, leverages VS Code’s runOn: folderOpen feature to trigger execution whenever a project is accessed. Earlier variants delivered the BeaverTail and InvisibleFerret implants, while newer versions disguise droppers as benign spell-check dictionaries to achieve remote code execution.
As part of the final payload, the backdoor logic establishes a continuous execution loop to harvest basic host information and fingerprints systems before executing attacker-supplied code. In some cases, additional scripts are downloaded minutes later to beacon frequently to a remote server, run further commands, and erase traces of activity. Researchers note that parts of the malware may be AI-assisted due to its code structure and inline comments.
Targets are typically software engineers, especially those working in the cryptocurrency, blockchain, and fintech sectors, where access to source code, credentials, and digital assets is valuable. Parallel research shows similar abuse of VS Code tasks to deploy backdoors, cryptominers, and credential-stealing modules via multiple fallback methods.
DPRK-based threat actors are rapidly experimenting with various delivery methods to increase the success of their attacks. Developers can counter the threat by continuing to scrutinize third-party repositories, carefully review task configurations, and install only trusted dependencies.
The Ugly | Attackers Target Misconfigured Training Apps to Access Cloud Environments
Threat actors are targeting misconfigured web applications like DVWA and OWASP Juice Shop to infiltrate cloud environments of Fortune 500 companies and their security vendors.
These intentionally vulnerable apps, designed for security training and internal testing, are exposed publicly and tied to privileged cloud accounts, creating a perfect storm of risks advantageous to attackers. Researchers have found nearly 2000 live, exposed apps, many linked to overly permissive identity access management (IAM) roles on AWS, GCP, and Azure, often using default credentials.
Attackers are leveraging the apps to deploy crypto miners, webshells, and persistence mechanisms. About 20% of found DVMA instances contain malicious artifacts, including XMRig cryptocurrency miners and a self-restoring watchdog.sh script that downloads additional AES-256-encrypted tools and removes competing miners.
PHP webshells like filemanager.php are also being deployed, allowing file operations and command execution, sometimes with indicators hinting at the operators’ origin.
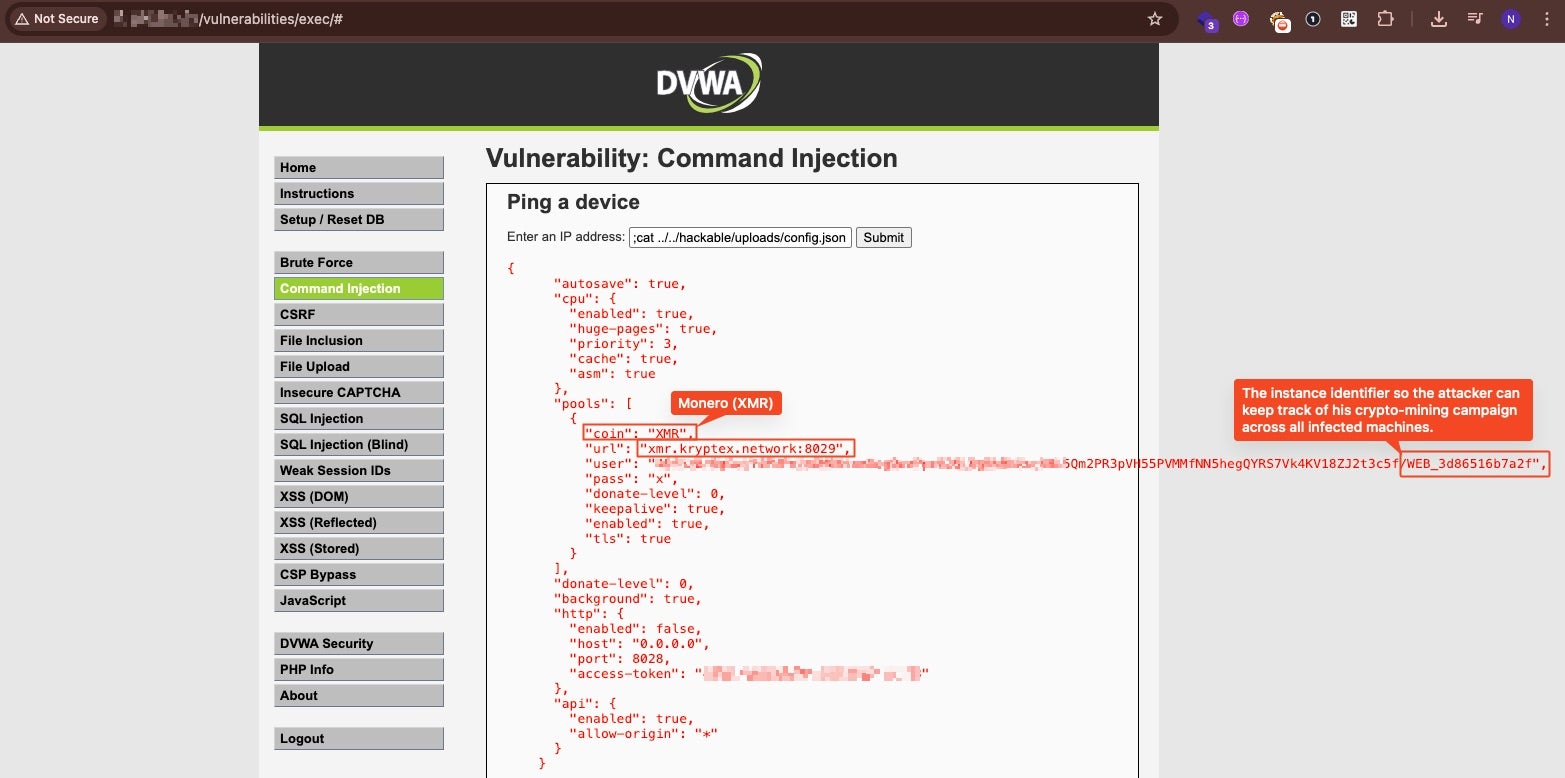
These exposed credentials could provide attackers full access to S3 buckets, GCS, and Azure Blob Storage, meaning attackers have read and write permissions to Secrets Manager, can interact with container registries, and obtain admin cloud privileges.
With these attacks active in the wild, organizations are urged to take steps to minimize their risk profile. Key defenses include maintaining a resource inventory, isolating test environments, and enforcing least-privilege IAM roles. By also replacing default credentials and automating resource expiration, organizations can eliminate systemic blind spots in non-production systems.
如有侵权请联系:admin#unsafe.sh