好的,我现在需要帮用户总结这篇文章的内容,控制在100字以内。首先,我得通读整篇文章,理解其主要观点。 文章主要讨论了Red Teaming在现代网络安全中的重要性。它指出,尽管许多组织投入大量资源进行漏洞扫描和渗透测试,但攻击者仍能找到未被模拟的路径入侵系统。Red Teaming通过模拟真实攻击场景,帮助组织检测、响应和阻止入侵。 接下来,文章列出了企业领导者在考虑Red Teaming时的十个关键问题,包括是否需要Red Teaming、何时进行、如何选择供应商、成本、投资回报率等。每个问题都提供了简明扼要的答案,帮助决策者理解Red Teaming的价值和实施方法。 总结时,我需要涵盖Red Teaming的目的、与渗透测试的区别、实施的好处以及关键考虑因素。同时,要保持简洁,不超过100字。 可能的结构是:首先介绍Red Teaming的作用,然后提到与渗透测试的不同之处,接着说明其好处和适用场景。最后强调其对企业安全的重要性。 现在组织语言:Red Teaming模拟真实攻击路径,评估企业检测和响应能力。它不同于渗透测试,专注于多方面漏洞链式利用。适用于高风险环境的企业领导者需考虑成本、频率及供应商选择等问题。 这样大概控制在100字左右。 </think> 文章介绍了红队(Red Teaming)作为现代网络安全中的重要实践,通过模拟真实攻击路径来验证组织能否检测、响应并阻止入侵。与渗透测试不同,红队侧重于多维度漏洞链式利用和业务影响评估。企业领导者需考虑成本、频率及供应商选择等问题,在高风险环境中提升安全成熟度。 2026-1-23 11:32:13 Author: securityboulevard.com(查看原文) 阅读量:1 收藏
Red Teaming has become one of the most discussed and misunderstood practices in modern cybersecurity. Many organizations invest heavily in vulnerability scanners and penetration tests, yet breaches continue to happen through paths those tools never simulate. Enterprise leaders now ask a deeper question: “Does our security testing completely reflect how attackers will break in?”
This is where Red Teaming comes in.
The exercise simulates real-world attack scenarios across people, processes, and technology to validate whether an organization can truly detect, respond to, and stop a breach. Below are the ten most important questions enterprise leaders ask about Red Teaming.
10 Questions Every Enterprise Leader Should Ask On Red Teaming
Here are the answers that matter when making the most important decision given the threat level we are bound to defend:
1. Do I need Red Teaming if I already do penetration testing?
Short answer: Yes, penetration testing and Red Teaming serve different purposes.
Penetration testing identifies technical vulnerabilities in specific systems. In case of black box testing, each and every vulnerability is taken into consideration and listed. On the other hand, in a red team exercise only those vulnerabilities that can grant unauthorized access to an organization’s internal system and sensitive data are prioritized. In short, Red Teaming tests whether an attacker can actually achieve a real business impact by chaining multiple weaknesses across the environment.
Pen tests answer “What is vulnerable?”
Red Teams answer “Can an attacker actually get access to our internal system and get access to sensitive data?”
Organizations that rely only on pentesting often miss attack paths that involve identity abuse, lateral movement, social engineering, and poor detection controls.
2. When should a company run a Red Team exercise?
A company should run a Red Team exercise when it has reached basic security maturity and wants to validate real breach readiness.
Typical triggers include:
- After deploying EDR, SIEM, SOC, or zero-trust controls
- Before or after regulatory audits
- Following mergers, cloud migrations, or major infrastructure changes
- When leadership wants to test incident response readiness
This exercise is most valuable once baseline security controls are already in place.
3. How do I choose the right Red Team vendor?
The right Red Team vendor should simulate real attackers not just run scripted tests.
Key criteria to evaluate:
- Proven experience in your industry (banking, healthcare, regulated sectors)
- Ability to test across network, cloud, identity, and social engineering
- Clear attack path reporting with business impact mapping
- Integration with detection and response teams (Purple Team capability)
- Compliance alignment with NIST, ISO 27001, SOC 2, or sector regulations
Avoid vendors that only deliver vulnerability lists instead of breach scenarios.
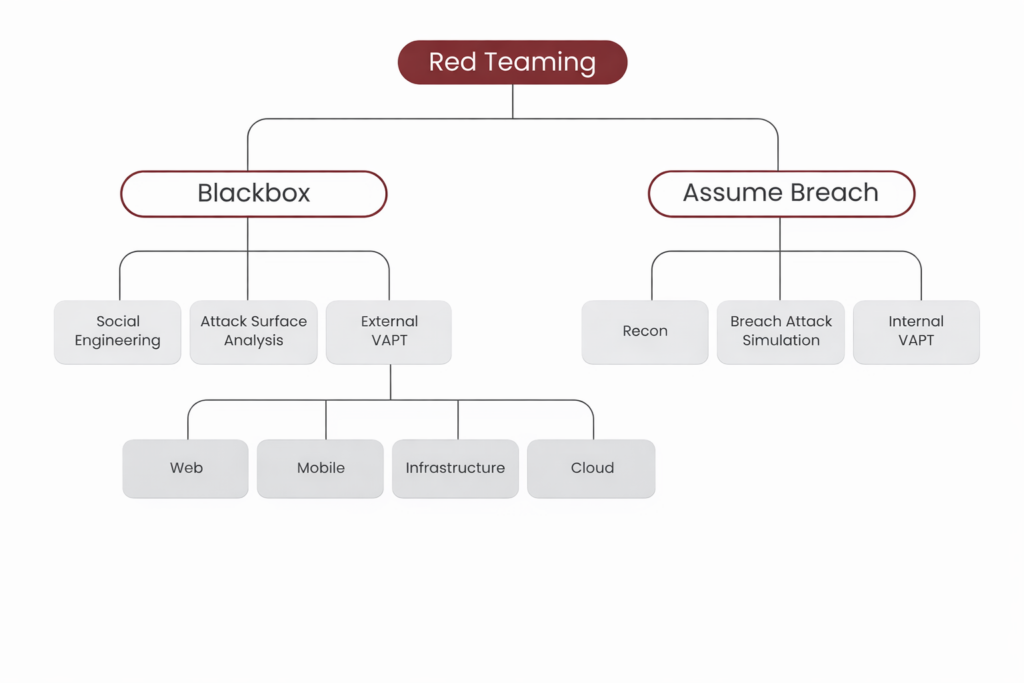
The image below showcases Kratikal’s coverage within red team assessment.
4. How much does a Red Team exercise cost?
Red Team exercise typically costs more than penetration testing because it involves multi-week, multi-vector attack simulations.
Pricing usually depends on:
- Scope (network, cloud, identity, physical, social engineering)
- Duration
- Level of stealth and realism
- Reporting depth and executive briefings
The real question is not cost but whether the exercise prevents a breach that could cost millions.
5. Is Red Teaming worth the investment?
Yes, when used correctly, Red Teaming delivers one of the highest ROI security validations.
Red Teaming helps organizations:
- Identify undetected attack paths
- Validate SOC and detection effectiveness
- Improve incident response readiness
- Reduce dwell time and breach impact
- Strengthen audit and regulatory posture
Most large breaches occur through chains of small failures. Red Teaming exposes those chains before attackers exploit them.
6. What is the difference between Red Teaming and penetration testing?
Penetration testing focuses on finding vulnerabilities. Red Teaming focuses on simulating a real attacker achieving a real objective.
Key differences:
- Pen tests are scoped and time-boxed; Red Teams are goal-driven and stealthy
- Pen tests test systems; Red Teams test people, processes, and detection
- Pen tests stop after exploitation; Red Teams test lateral movement and persistence
In mature security programs, Red Teaming complements and does not replace penetration testing.
7. How often should an organization conduct Red Team exercises?
Most enterprises run Red Team exercises once every 12 to 24 months, or after major infrastructure or security changes. High-risk sectors such as banking, financial services, healthcare, and critical infrastructure often run them annually. Red Teaming should be treated as a strategic validation exercise, not a one-time activity.
8. What should we expect as outcomes from a Red Team exercise?
A proper Red Team engagement should deliver more than a technical report.
Expected outcomes include:
- Documented attack paths and breach scenarios
- Detection gaps in SOC, SIEM, and EDR controls
- Time-to-detect and time-to-respond metrics
- Business impact mapping (data, systems, revenue risk)
- Clear remediation and improvement roadmap
The goal is operational improvement along with compliance documentation.
9. Does Red Teaming help with regulatory compliance?
Yes. Red Teaming strongly supports compliance requirements across multiple frameworks.
It aligns directly with:
- ISO 27001 continuous risk validation
- NIST CSF detection and response maturity
- SOC 2 security testing controls
- Banking and financial regulator cyber resilience guidelines
Many regulators now expect advanced security testing beyond basic vulnerability scanning.
10. Should we build an in-house Red Team or outsource it?
Most organizations should outsource Red Teaming. Building an in-house Red Team requires:
- Highly specialized offensive talent
- Ongoing training and tooling
- Separation from detection teams to maintain realism
Outsourced Red Teams bring fresh attacker perspectives, proven methodologies, and regulatory credibility. Large global enterprises sometimes combine both internal Purple Teams with periodic external Red Team validation.
Red Teaming A Must for Breach-Ready Enterprises
Red Teaming is not an advanced penetration test. It is a strategic breach-readiness validation exercise. For enterprises operating in regulated, high-risk, or cloud-first environments, Red Teaming answers the only question that truly matters:
“Can we detect and stop a real attacker before business damage occurs?”
Organizations that rely only on scanners and checklist audits often discover the truth too late during a breach. Red Teaming replaces assumptions with evidence. And in modern cybersecurity, evidence is the only thing that protects the business.
The post 10 Questions Enterprise Leaders Should Ask Before Running a Red Teaming Exercise appeared first on Kratikal Blogs.
*** This is a Security Bloggers Network syndicated blog from Kratikal Blogs authored by Puja Saikia. Read the original post at: https://kratikal.com/blog/10-questions-enterprise-leaders-should-ask-before-running-a-red-teaming-exercise/
如有侵权请联系:admin#unsafe.sh