嗯,用户让我帮忙总结一篇文章,控制在100字以内,而且不需要特定的开头。首先,我得仔细阅读文章内容,抓住主要信息。 文章讲的是Pwn2Own Automotive 2026比赛已经结束,安全研究人员通过利用76个零日漏洞赚取了1,047,000美元。比赛地点在东京,时间是1月21日至23日。参赛者攻击了车载信息娱乐系统、电动汽车充电器和汽车操作系统。团队Fuzzware.io赢得了最高奖金,其次是Team DDOS和Synactiv。比赛还涉及漏洞披露和修复的时间安排。 接下来,我需要将这些信息浓缩到100字以内。要突出比赛结果、奖金数额、参赛团队以及主要攻击目标。同时,确保语言简洁明了。 可能会遗漏一些细节,比如具体的漏洞数量或修复时间,但关键点必须保留。最后检查一下字数是否符合要求。 </think> Pwn2Own Automotive 2026比赛结束,安全研究人员通过利用76个零日漏洞赚取了1,047,000美元。比赛在东京举行,参赛者攻击了车载信息娱乐系统、电动汽车充电器和汽车操作系统。团队Fuzzware.io赢得最高奖金,其次是Team DDOS和Synactiv。 2026-1-23 13:0:23 Author: www.bleepingcomputer.com(查看原文) 阅读量:2 收藏

Pwn2Own Automotive 2026 has ended with security researchers earning $1,047,000 after exploiting 76 zero-day vulnerabilities between January 21 and January 23.
The Pwn2Own Automotive hacking competition focuses on automotive technologies and took place this week in Tokyo, Japan, during the Automotive World auto conference.
Throughout the contest, the hackers targeted fully patched in-vehicle infotainment (IVI) systems, electric vehicle (EV) chargers, and car operating systems (e.g., Automotive Grade Linux).
Before TrendMicro's Zero Day Initiative publicly discloses them, vendors have 90 days to develop and release security fixes for zero-days that were exploited and reported during the Pwn2Own contest.
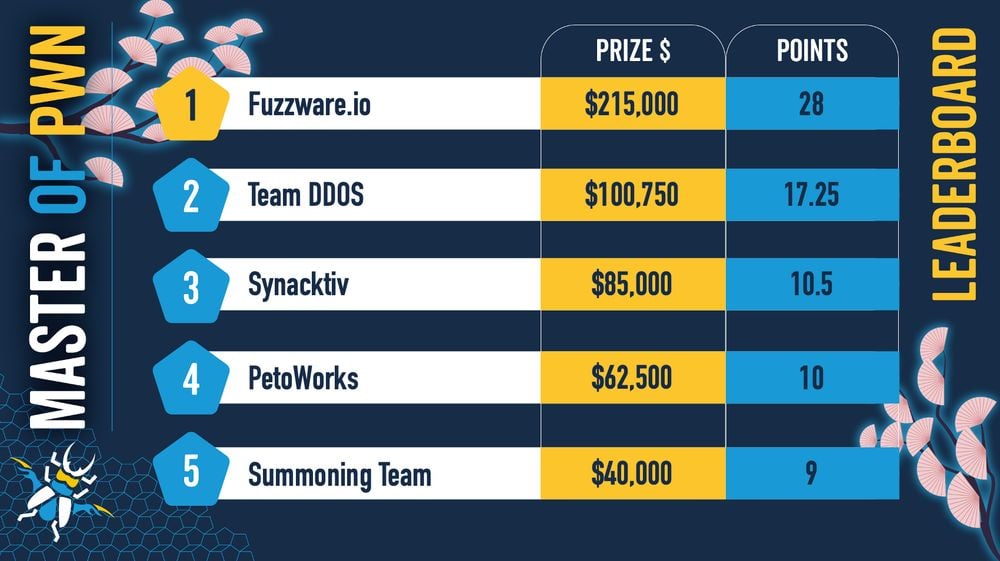
Team Fuzzware.io won the Pwn2Own Automotive 2026 contest after taking home $215,000 in cash, followed by Team DDOS with $100,750 and Synactiv with $85,000.
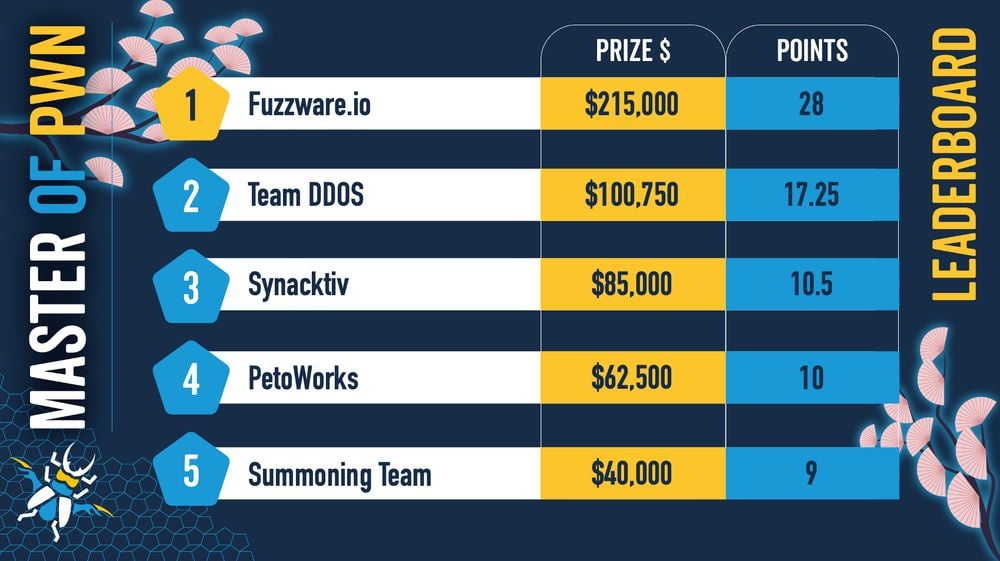
In total, Fuzzware.io earned $118,00 after hacking an Alpitronic HYC50 Charging Station, an Autel charger, and a Kenwood DNR1007XR navigation receiver on the first day.
They were also awarded another $95,000 for demonstrating multiple zero-days in the Phoenix Contact CHARX SEC-3150 charging controller, the ChargePoint Home Flex EV charger, and the Grizzl-E Smart 40A EV charging station on the second day, and an additional $2,500 after a bug collision while attempting to root an Alpine iLX-F511 multimedia receiver on the last day of the contest.
Synacktiv Team also collected $35,000 after chaining an out‑of‑bounds write flaw and an information leak to hack the Tesla Infotainment System via a USB-based attack on the first day of Pwn2Own.
The full schedule for the third day and the results for each challenge are available here, while the complete schedule for Pwn2Own Automotive 2026 is available here.
During the Pwn2Own Automotive 2024 contest, hackers collected another $1,323,750 after demoing 49 zero-day bugs and hacking a Tesla car twice. Last year, security researchers earned another $886,250 after exploiting 49 zero-days at Pwn2Own Automotive 2025.
7 Security Best Practices for MCP
As MCP (Model Context Protocol) becomes the standard for connecting LLMs to tools and data, security teams are moving fast to keep these new services safe.
This free cheat sheet outlines 7 best practices you can start using today.
如有侵权请联系:admin#unsafe.sh

