Day 3 of Pwn2Own Automotive 2026 is here - the final push. The world’s top security researchers return for their last shots at the latest automotive targets. After two days, $955,750 awarded for 66 unique 0-day vulnerabilities, and the Master of Pwn leaderboard has a clear frontrunner as the competition heads into its final stretch.
Bold attempts, decisive moments, and a dramatic finish lie ahead. Follow the final updates on Twitter, Mastodon, LinkedIn, and Bluesky, and join the conversation using #Pwn2OwnAutomotive and #P2OAuto.
SUCCESS / COLLISON - Tobias Scharnowski (@ScepticCtf), Felix Buchmann (@diff_fusion), and Kristian Covic (@SeTcbPrivilege) of Fuzzware.io targeted the Alpine iLX-F511, demonstrating one vulnerability previously used by another contestant, earning $2,500 USD and 1 Master of Pwn point. #Pwn2Own #P2OAuto
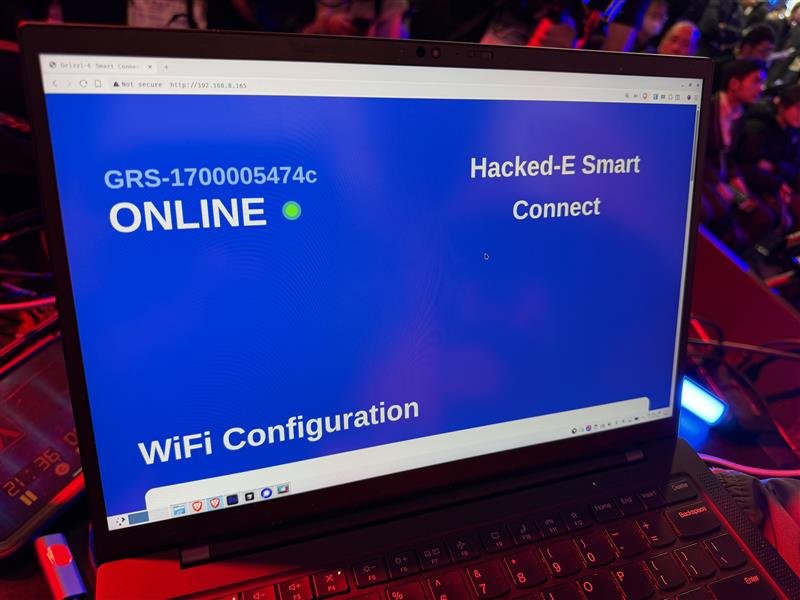
SUCCESS / COLLISON - Slow Horses of Qrious Secure (@qriousec) targeted the Grizzl-E Smart 40A but encountered two bug collisions, still earning $5,000 USD and 2 Master of Pwn points.