
嗯,用户让我帮忙总结一篇文章的内容,控制在一百个字以内,而且不需要特定的开头。首先,我需要理解文章的主要内容。 文章讲的是SmarterMail软件存在一个认证绕过漏洞,允许攻击者重置管理员密码并获得完全权限。这个漏洞存在于force-reset-password API端点,没有身份验证机制。研究人员报告后,SmarterTools发布了补丁,但不久后发现漏洞被利用。攻击者可能逆向工程补丁找到了利用方法。这个漏洞影响管理员账户,可能导致远程代码执行。 接下来,我需要将这些信息浓缩到100字以内。要突出关键点:漏洞名称、影响、攻击方式、后果以及修复情况。 可能的结构是:SmarterMail存在认证绕过漏洞,允许重置管理员密码并获取权限。攻击者利用API端点绕过身份验证,可能导致远程代码执行。补丁发布后不久就被利用。建议升级到最新版本。 检查字数是否在限制内,并确保信息准确无误。 </think> SmarterMail 存在认证绕过漏洞,允许攻击者重置管理员密码并获取系统权限。该漏洞源于未认证的 force-reset-password API 端点,攻击者可借此绕过安全控制并执行远程代码。尽管 SmarterTools 已发布修复补丁(Build 9511),但漏洞已被活跃利用。建议用户立即升级以缓解风险。 2026-1-22 18:45:17 Author: www.bleepingcomputer.com(查看原文) 阅读量:0 收藏

Hackers began exploiting an authentication bypass vulnerability in SmarterTools' SmarterMail email server and collaboration tool that allows resetting admin passwords.
An authentication bypass vulnerability in SmarterTools SmarterMail, which allows unauthenticated attackers to reset the system administrator password and obtain full privileges, is now actively exploited in the wild.
The issue resides in the force-reset-password API endpoint, which is intentionally exposed without authentication.
Researchers at cybersecurity company watchTowr reported the issue on January 8, and SmarterMail released a fix on January 15 without an identifier being assigned.
After the issue was addressed, the researchers found evidence that threat actors started to exploit it just two days later. This suggests that hackers reverse-engineered the patch and found a way to leverage the flaw.
SmarterMail is a self-hosted Windows email server and collaboration platform developed by SmarterTools that provides SMTP/IMAP/POP email, webmail, calendars, contacts, and basic groupware features.
It is typically used by managed service providers (MSPs), small and medium-sized businesses, and hosting providers offering email services. SmarterTools claims that its products have 15 million users in 120 countries.
The CVE-less flaw arises from the API endpoint ‘force-reset-password’ accepting attacker-controlled JSON input, including a 'IsSysAdmin' bool type property, which, if set to ‘true,’ forces the backend to execute the system administrator password reset logic.
However, the mechanism does not perform any security controls or verify the old password, despite the 'OldPassword' field being present in the request, watchTowr researchers found.
As a result, anyone who knows or guesses an admin username could set a new password and hijack the account.
The researchers note that the flaw affects only admin-level accounts, not regular users.
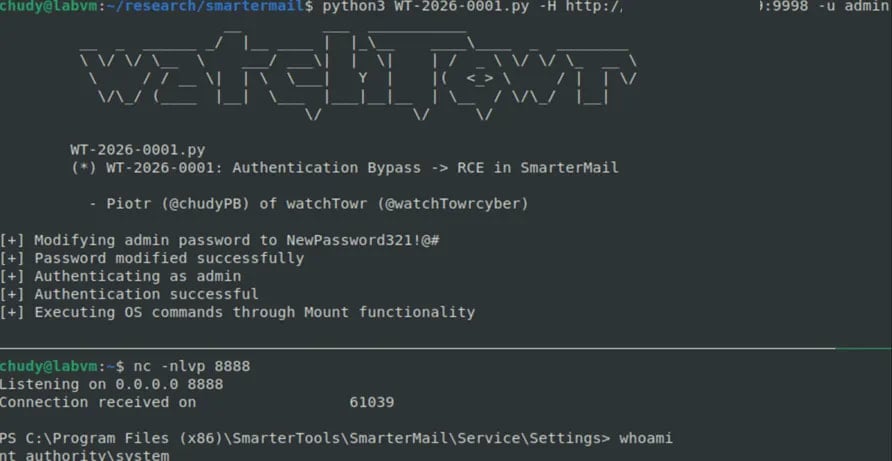
With admin-level access, attackers can run OS commands, thus getting full remote code execution on the host.
watchTowr researchers have created a proof-of-concept exploit that demonstrates SYSTEM-level shell access.
Source: watchTowr
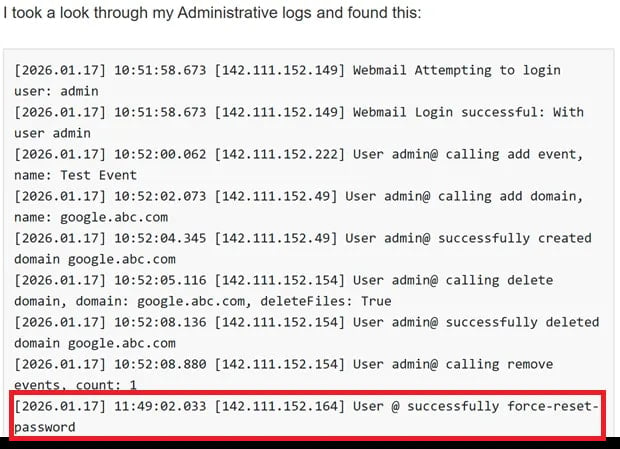
The researchers learned that the vulnerability was being exploited in the wild from an anonymous user, who stated that somebody was resetting administrator passwords.
To back their claims, the tipster pointed watchTowr researchers to a forum post describing a similar situation.
Examining the shared logs revealed that these attacks targeted the ‘force-reset-password’ endpoint, supporting the conclusion that the issue is currently under active exploitation.
Source: watchTowr
Two weeks earlier, watchTowr discovered a critical pre-auth RCE flaw in SmarterMail, tracked as CVE-2025-52691, which led to the discovery of the latest issue.
Users of SmarterMail are recommended to upgrade to the latest version of the software, Build 9511, released on January 15, that addresses both issues.
Secrets Security Cheat Sheet: From Sprawl to Control
Whether you're cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.
如有侵权请联系:admin#unsafe.sh

