嗯,用户让我总结一篇文章,控制在一百个字以内,而且不需要用“文章内容总结”这样的开头。我得先仔细阅读这篇文章,抓住关键点。 文章主要讲的是SmarterMail软件的一个漏洞,编号WT-2026-0001。这个漏洞允许攻击者绕过认证,重置管理员密码,进而获得系统级访问权限。漏洞是在1月15日发布的补丁Build 9511中修复的,但补丁发布后不久就被积极利用了,目前还没有CVE编号。 我需要把这些信息浓缩到一百字以内。首先说明漏洞名称和影响:攻击者可以重置密码并获得系统权限。然后提到补丁发布的时间和漏洞被利用的情况,最后说明没有CVE编号。 这样组织起来应该可以满足用户的要求。确保语言简洁明了,不使用任何复杂的术语。 </think> SmarterMail软件存在认证绕过漏洞(WT-2026-0001),攻击者可利用该漏洞重置管理员密码并获得系统级访问权限。该漏洞于2026年1月15日通过补丁修复,但已被积极利用,尚未分配CVE编号。 2026-1-22 15:12:41 Author: securityaffairs.com(查看原文) 阅读量:1 收藏
Critical SmarterMail vulnerability under attack, no CVE yet

A SmarterMail flaw (WT-2026-0001) is under active attack just days after its January 15 patch, with no CVE assigned yet.
A newly disclosed flaw in SmarterTools SmarterMail is being actively exploited just two days after a patch was released. The issue, tracked as WT-2026-0001 and lacking a CVE, was fixed on January 15, 2026, with Build 9511 after responsible disclosure by watchTowr Labs.
SmarterTools SmarterMail is a commercial email server software designed for businesses and service providers. It provides enterprise-level email, calendar, contacts, tasks, and collaboration features.
The flaw is an authentication bypass that lets attackers reset the SmarterMail administrator password via a specially crafted request to the force-reset-password API endpoint.
The vulnerabilities lies in SmarterMail’s APT unauthenticated ForceResetPassword, which trusts an IsSysAdmin flag.
“You may notice that this API endpoint accepts the ForceResetPasswordInputs object, which can be deserialized from the JSON.” reads the report published by Watchtowr.”It has several interesting properties that can be controlled by the user:
IsSysAdminUsernameOldPasswordNewPasswordConfirmPassword
That combination is immediately unusual. Password reset flows typically rely on a second factor or out-of-band proof of control – for example, a secret token delivered via email.”
By setting it to true, an attacker can reset an administrator’s password via a crafted HTTP request, gaining admin access.

This bypass can then be escalated to remote code execution by abusing built‑in admin features to run arbitrary OS commands, leading to SYSTEM‑level access.
“There are no security controls here. No authentication. No authorization. No verification of OldPassword. Despite the API requiring an OldPassword field in the request, it is never checked when resetting a system administrator’s password.” continues the report.
“Ironically, the regular user password reset flow does validate the existing password. The privileged path does not.”
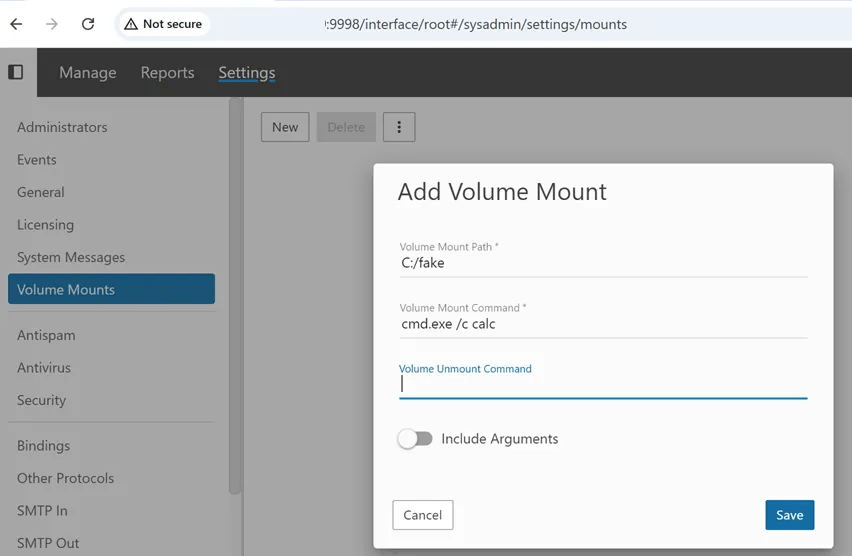
The researchers pointed out that although classified as an authentication bypass, the SmarterMail flaw enables full remote code execution. After gaining system admin access, attackers can use the Volume Mounts feature to run arbitrary OS commands, achieving SYSTEM-level control.

The researchers created a proof of concept that allows achieving a SYSTEM-level shell on the target host.
The issue was patched in version 9511 on January 15, 2026, and is actively exploited. On patched systems, exploit attempts fail due to added password validation checks. No CVE has been assigned yet.
“Once again, this demonstrates that attackers actively monitor release notes and perform patch diffing on high-value targets. Together, friends, we have learned this the hard way today with WT-2026-0001.” concludes the report.
“Given that this vulnerability is already under active exploitation, upgrading is not optional.”
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, SmarterTools SmarterMail)
如有侵权请联系:admin#unsafe.sh