
好的,我现在需要帮用户总结一篇文章,控制在100字以内。用户的要求是直接写文章描述,不需要特定的开头。 首先,我得快速浏览文章内容。文章讲的是一个网络安全公司Cyber Centaurs发现INC勒索软件团伙的数据泄露。他们通过深入分析攻击残留物,发现了存储在多个受害者数据中的攻击者基础设施。最终成功恢复了12家美国组织的数据。 接下来,我需要提取关键信息:网络安全公司、INC团伙、数据泄露、恢复12家组织的数据。然后把这些信息浓缩成简洁的句子。 要注意字数限制,所以每个要点都要简明扼要。比如“深入分析”可以表达为“通过分析攻击残留物”。同时,确保句子通顺,没有语法错误。 最后检查一下是否符合用户的要求:中文、100字以内、直接描述内容。确认无误后就可以给出总结了。 </think> 一家网络安全公司通过分析INC勒索软件攻击残留物,发现其存储在多个受害者数据中的基础设施,并成功恢复了12家美国组织的被盗数据。 2026-1-22 16:30:35 Author: www.bleepingcomputer.com(查看原文) 阅读量:2 收藏

An operational security failure allowed researchers to recover data that the INC ransomware gang stole from a dozen U.S. organizations.
A deep forensic examination of the artifacts left behind uncovered tooling that had not been used in the investigated attack, but exposed attacker infrastructure that stored data exfiltrated from multiple victims.
The operation was conducted by Cyber Centaurs, a digital forensics and incident response company that disclosed its success last November and now shared the full details with BleepingComputer.
The Cyber Centaurs investigation began after a client U.S. organization detected ransomware encryption activity on a production SQL Server.
The payload, a RainINC ransomware variant, was executed from the PerfLogs directory, which is typically created by Windows. However, ransomware actors have begun to use it more frequently for staging.
The researchers also noticed the presence of artifacts from the legitimate backup tool Restic, although data exfiltration had occurred during the lateral movement stage and the threat actor had not used the utility in this attack.
This caused a shift in the researchers' investigation "from incident response to infrastructure analysis."
The traces that INC ransomware left behind included renamed binaries (like ‘winupdate.exe’), PowerShell scripts to execute Restic, hardcoded repository configuration variables, and backup commands.
Restic-related remnants indicated that the threat actor was using the backup tool selectively as part of its operational toolkit.
One of the discovered PowerShell scripts, 'new.ps1', contained Base64-encoded commands for Restic and included hardcoded environment variables used to run the tool (access keys, repository paths, and S3 passwords for encrypted repositories).
"If INC routinely reused Restic-based infrastructure across campaigns, then the storage repositories referenced in attacker scripts were unlikely to be dismantled once a ransom event concluded," the researchers theorized.
"Instead, those repositories would likely persist as long-lived attacker-controlled assets, quietly retaining encrypted victim data well after negotiations ended or payments were made."
If this were the case, data stolen from other organizations could still be available in an encrypted form and could potentially be recovered from the backup server.
To validate this hypothesis, the team developed a controlled, non-destructive enumeration process that confirmed the presence of encrypted data stolen from 12 unrelated organizations in the healthcare, manufacturing, technology, and service sectors in the United States.
None of the organizations were Cyber Centaurs clients, and the incidents were unrelated, distinct ransomware events.
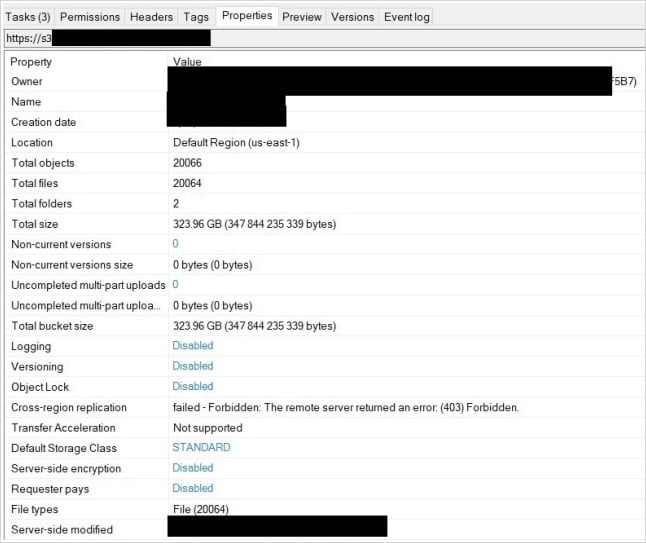
Source: Cyber Centaurs
The researchers then decrypted the backups and preserved the copies while contacting law enforcement to help validate ownership and guide them through the proper procedure.
The Cyber Centaurs report lists multiple tools used in INC ransomware attacks, which include, among others, cleanup tools, remote access software, and network scanners.
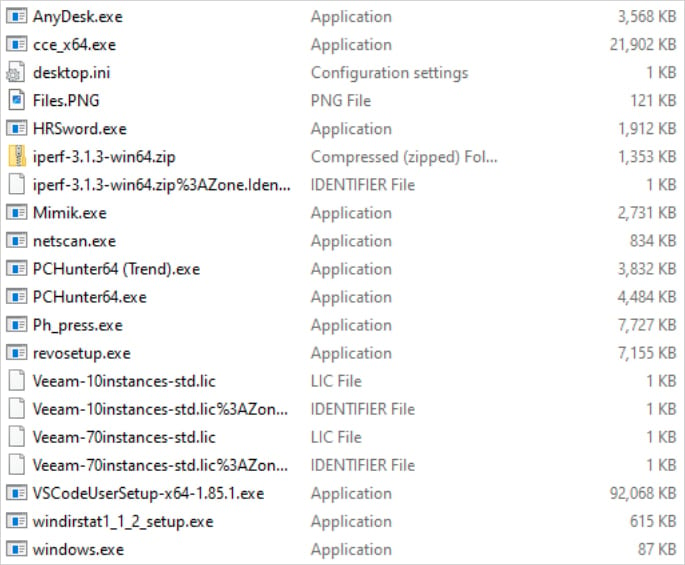
Source: Cyber Centaurs
The researchers also created YARA and Sigma rules to help defenders detect the Restic backup tool or its renamed binaries in the environment or running from suspicious locations, which could signal a ransomware attack in development.
INC ransomware is a ransomware-as-a-service (RaaS) operation that emerged in mid-2023.
The threat actor claimed several high-profile victims over the years, including Yamaha Motor, Xerox Business Solution, Scotland's NHS, McLaren Health Care, the Texas State Bar, Ahold Delhaize, the Panama Ministry of Economy, the Pennsylvania AG Office, and Crisis24.
7 Security Best Practices for MCP
As MCP (Model Context Protocol) becomes the standard for connecting LLMs to tools and data, security teams are moving fast to keep these new services safe.
This free cheat sheet outlines 7 best practices you can start using today.
如有侵权请联系:admin#unsafe.sh

