嗯,用户让我帮忙总结一篇文章,控制在100字以内,而且不需要用“文章内容总结”之类的开头。首先,我需要仔细阅读文章内容,抓住主要信息。 文章讲的是西班牙的电子产品零售商PcComponentes否认了数据泄露影响1600万客户的说法,但承认遭受了凭据填充攻击。他们没有发现未经授权的访问证据,但确实有攻击者试图用其他泄露的数据来登录他们的账户。泄露的数据包括订单详情、地址、姓名、电话号码、IP地址等。公司采取了措施,比如启用双重认证和Captcha。 接下来,我需要把这些要点浓缩到100字以内。要确保涵盖否认数据泄露、承认凭据填充攻击、泄露的数据类型以及公司的应对措施。 可能会这样组织:PcComponentes否认数据泄露影响1600万客户,但承认凭据填充攻击。泄露数据包括订单详情、地址等。公司已采取措施如双重认证和Captcha。 检查一下字数是否在限制内,并且表达清晰。确保没有遗漏关键点,比如攻击者的行为和公司的应对措施。 </think> 西班牙电子产品零售商PcComponentes否认数据泄露影响1600万客户,但承认遭受凭据填充攻击。攻击者声称窃取1630万条记录并泄露50万条数据,包括订单详情、地址等。公司未发现非法访问证据,并已采取双重认证和Captcha等措施应对。 2026-1-21 21:0:35 Author: www.bleepingcomputer.com(查看原文) 阅读量:0 收藏

PcComponentes, a major technology retailer in Spain, has denied claims of a data breach on its systems impacting 16 million customers, but confirmed it suffered a credential stuffing attack.
The Spanish e-commerce company specializes in the sale of computers, laptops, peripherals, and hardware, and has an estimated 75 million unique marketplace visitors per year.
Yesterday, a threat actor named ‘daghetiaw’ published what they claimed to be a customer database stolen from PcComponentes, containing 16.3 million records. The threat actor leaked 500,000 records and offered to sell the rest to the highest bidder.
The leaked data contains order details, physical addresses, full names, phone numbers, IP addresses, product wish-lists, and customer support messages exchanged with the firm via Zendesk.
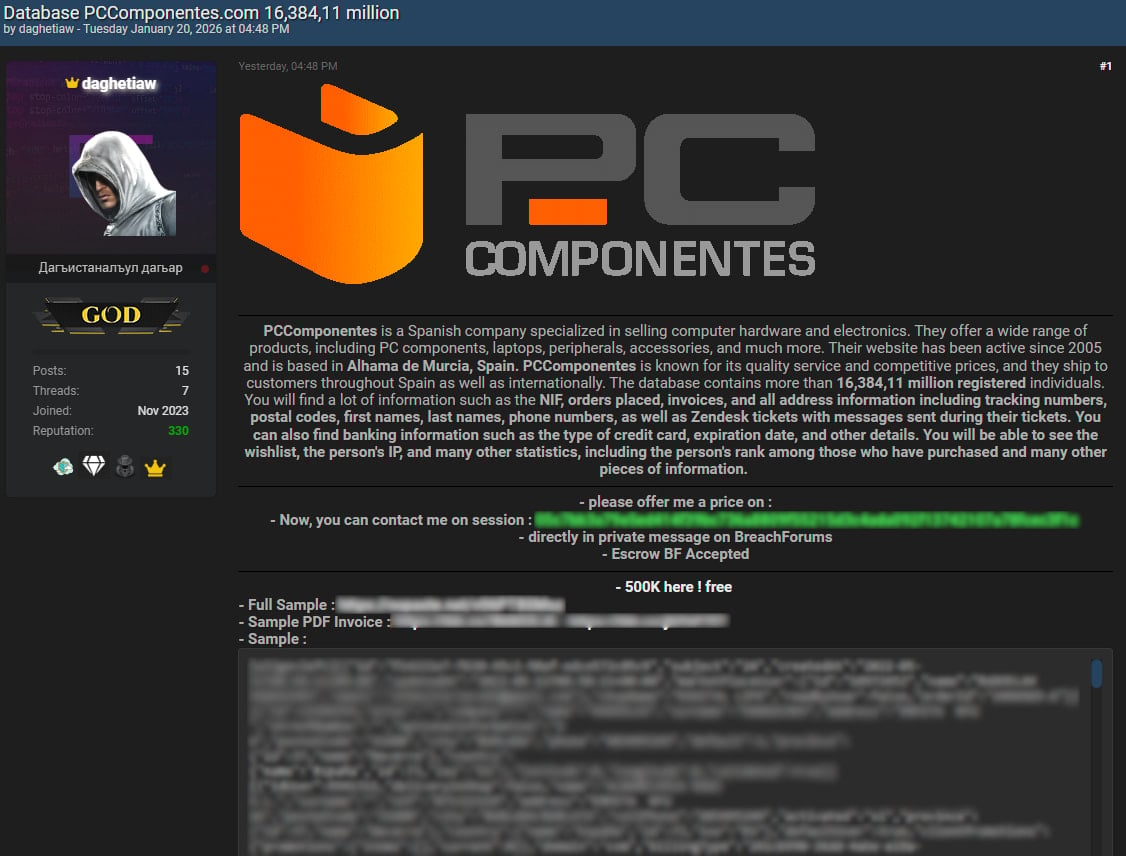
Source: BleepingComputer
In an announcement today, PcComponents says that it investigated a possible breach of its systems, but its security experts found no evidence of unauthorized access.
"There has been no illegitimate access to our databases or internal systems," the company assures, adding that "the figure of 16 million supposedly affected customers is false, as the number of active PcComponentes accounts is significantly lower."
The company also underlined that no financial details or customer passwords are stored on its systems.
However, PcComponentes admitted that its investigation discovered evidence of a credential stuffing attack on its platform. This means that a threat actor tried email addresses and passwords from other security breaches or leaked databases to find PcComponentes accounts.
Credential stuffing attacks are typically automated and rely on large volumes of reused login credentials from other services.
An investigation from threat intelligence company Hudson Rock discovered that the attackers likely collected the login data from computers infected with info-stealing malware.
"Every single email we checked from the threat actor’s sample was found in existing infostealer logs," Hudson Rock says in a post today, adding that some of the logins were as old as 2020.
A screenshot that Hudson Rock published shows a set of six email addresses that were verified and all of them were marked as previously compromised in infostealer infections.
According to PcComponentes’ announcement, the following data was exposed for a small number of compromised accounts:
- First and last names
- National ID number
- Physical addresses
- IP addresses
- Email addresses
- Phone numbers
In response to the incident, PcComponentes has implemented a set of defenses that include CAPTCHA on the login pages, mandatory activation of two-factor authentication (2FA) for all accounts, and invalidation of all active sessions.
As a result, customers will be automatically logged out, and accounts without two-factor authentication (2FA) will be required to enable it before regaining access.
PcComponentes also recommends that customers use strong, unique passwords for each account, store their passwords in a password manager, and stay vigilant for potential phishing messages.
BleepingComputer has contacted PcComponentes to ask how many customers have been impacted precisely, but a statement wasn’t immediately available.
7 Security Best Practices for MCP
As MCP (Model Context Protocol) becomes the standard for connecting LLMs to tools and data, security teams are moving fast to keep these new services safe.
This free cheat sheet outlines 7 best practices you can start using today.
如有侵权请联系:admin#unsafe.sh

