好的,我现在需要帮用户总结这篇文章的内容,控制在100字以内。首先,我得通读整篇文章,抓住关键点。 文章主要讲的是WordPress插件ACF Extended的一个严重漏洞,编号是CVE-2025-14533。这个漏洞允许未认证的攻击者远程获取管理员权限。插件目前在10万个网站上使用,影响范围挺大的。 漏洞出现在Insert User/Update User表单中,开发者没有限制角色设置,所以攻击者可以随意设置用户角色,甚至设为管理员。这个漏洞已经在版本0.9.2.2中修复了,但仍有大约5万个网站可能还在使用旧版本。 另外,文章还提到安全公司GreyNoise监测到针对WordPress插件的大规模枚举活动,可能在寻找漏洞利用的机会。特别是Post SMTP和LiteSpeed Cache这两个插件已经被积极利用。 总结的时候,我需要把这些关键点浓缩进去:漏洞名称、影响范围、攻击方式、修复情况以及潜在威胁。同时要控制在100字以内,所以要简洁明了。 可能会这样组织句子:ACF Extended插件存在严重漏洞(CVE-2025-14533),允许未认证攻击者获取管理员权限。该插件被10万网站使用,在旧版本中存在此问题,已修复但仍有部分网站受影响。此外,大规模WordPress插件枚举活动增加风险。 检查一下字数是否符合要求,并确保信息准确无误。 </think> WordPress插件ACF Extended存在严重漏洞(CVE-2025-14533),允许未认证攻击者通过滥用表单操作获取管理员权限。该插件被10万网站使用,在旧版本中存在此问题,已修复但仍有部分网站受影响。此外,大规模WordPress插件枚举活动增加风险。 2026-1-20 22:15:15 Author: www.bleepingcomputer.com(查看原文) 阅读量:0 收藏

A critical-severity vulnerability in the Advanced Custom Fields: Extended (ACF Extended) plugin for WordPress can be exploited remotely by unauthenticated attackers to obtain administrative permissions.
ACF Extended, currently active on 100,000 websites, is a specialized plugin that extends the capabilities of the Advanced Custom Fields (ACF) plugin with features for developers and advanced site builders.
The vulnerability, tracked as CVE-2025-14533, can be leveraged for admin privileges by abusing the plugin’s ‘Insert User / Update User’ form action, in versions of ACF Extended 0.9.2.1 and earlier.
The flaw arises from the lack of enforcement of role restrictions during form-based user creation or updates, and exploitation works even when role limitations are appropriately configured in the field settings.
"In the vulnerable version [of the plugin], there are no restrictions for form fields, so the user's role can be set arbitrarily, even to 'administrator', regardless of the field settings, if there is a role field added to the form," Wordfence explains.
"As with any privilege escalation vulnerability, this can be used for complete site compromise," the researchers warn.
Although the outcome from exploiting the flaw is severe, Wordfence notes that the issue is only exploitable on sites that explicitly use a ‘Create User’ or ‘Update User’ form with a role field mapped.
CVE-2025-14533 was discovered by security researcher Andrea Bocchetti, who, on December 10, 2025, submitted a report to Wordfence to validate the issue and escalate it to the vendor.
Four days later, the vendor addressed the problem and released it in ACF Extended version 0.9.2.2.
Based on download stats from wordpress.org, roughly 50,000 users have downloaded the plugin since then. Assuming all downloads were for the latest version, that leaves roughly an equal number of sites exposed to attacks.
WordPress plugin enumeration activity
Although no attacks targeting CVE-2025-14533 have been observed yet, a report from threat monitoring firm GreyNoise presents large-scale WordPress plugin reconnaissance activity aimed at enumerating potentially vulnerable sites.
According to GreyNoise, from late October 2025 to mid-January 2026, nearly 1,000 IPs across 145 ASNs targeted 706 distinct WordPress plugins in over 40,000 unique enumeration events.
The most targeted plugins are Post SMTP, Loginizer, LiteSpeed Cache, SEO by Rank Math, Elementor, and Duplicator.
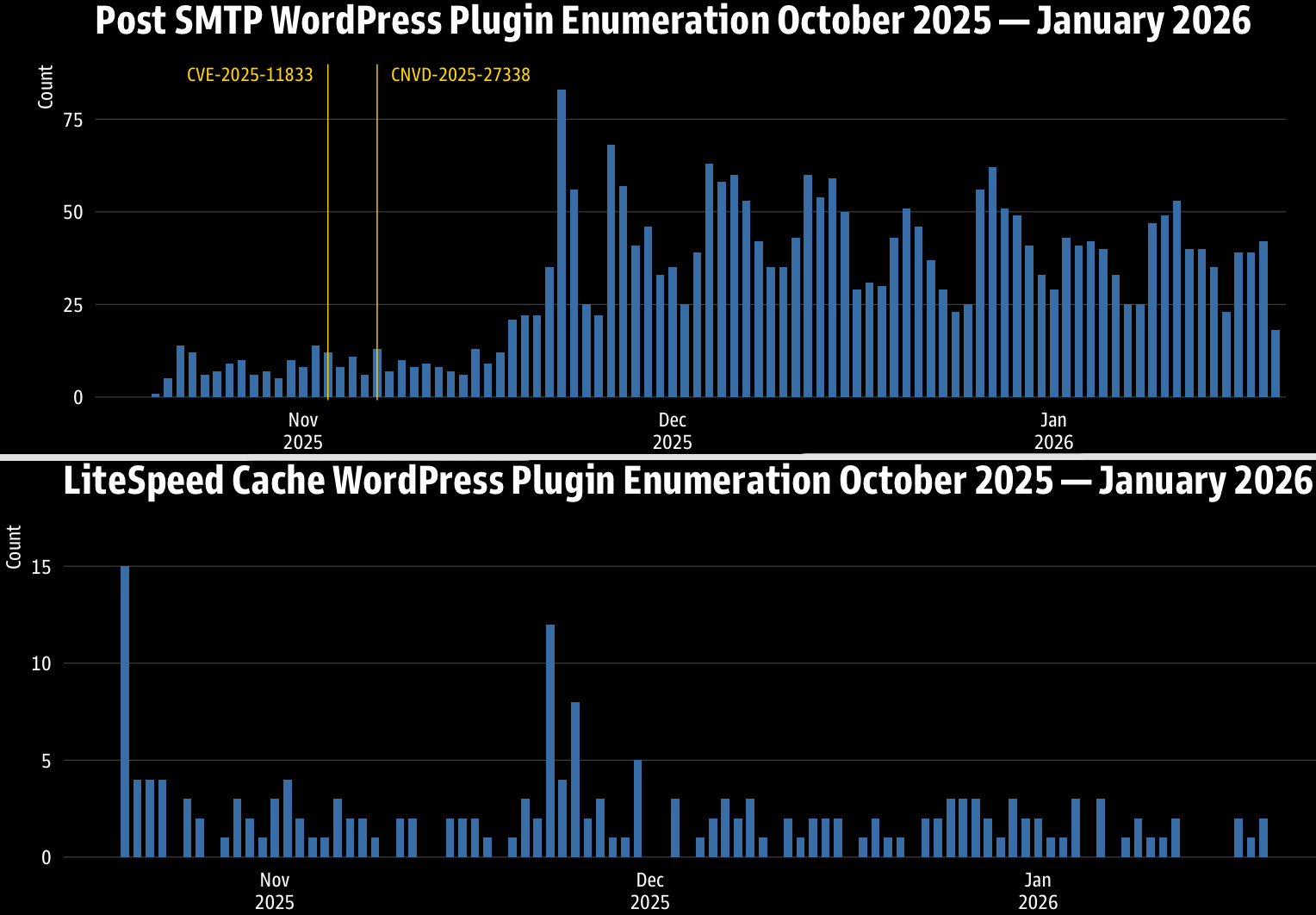
Source: GreyNoise
Active exploitation of the Post SMTP flaw CVE-2025-11833 was reported in early November 2025 by Wordfence, and GreyNoise’s records indicate a focused effort targeting this flaw involving 91 IPs.
Another flaw GreyNoise urged admins to patch is CVE-2024-28000, which impacts LiteSpeed Cache and was marked as actively exploited by Wordfence in August 2024.
7 Security Best Practices for MCP
As MCP (Model Context Protocol) becomes the standard for connecting LLMs to tools and data, security teams are moving fast to keep these new services safe.
This free cheat sheet outlines 7 best practices you can start using today.
如有侵权请联系:admin#unsafe.sh

