好的,我现在需要帮用户总结一篇关于VoidLink恶意软件框架的文章,控制在100字以内。首先,我得仔细阅读文章内容,抓住关键点。 文章提到VoidLink是一个针对云的恶意软件框架,由Check Point Research发现。它被描述为一个高级的Linux恶意软件框架,具有自定义加载器、植入模块、rootkit模块以及扩展功能的插件。研究人员推测它可能是中国开发者的作品,使用了多种编程语言。 接下来,文章指出VoidLink的发展主要依赖于AI驱动的开发,并且在一周内就完成了功能迭代。这是基于开发者的多个安全失误,暴露了源代码、文档等信息。Check Point发现开发者使用了TRAE SOLO AI助手,并通过分析生成的文件确认了AI在开发中的作用。 此外,文章提到开发者使用了Spec-Driven Development方法,制定了详细的开发计划,并在短时间内完成了大量代码。Check Point认为这是第一个由AI生成的高级恶意软件实例,标志着网络犯罪进入新阶段。 现在,我需要将这些关键点浓缩到100字以内。要突出VoidLink的特点、AI的作用以及其影响。可能的结构是:VoidLink是一个云聚焦的恶意软件框架,由单人借助AI开发,在一周内完成迭代,并具备多种功能模块。 </think> VoidLink 是一个针对云环境的高度复杂的 Linux 恶意软件框架,具备自定义加载器、植入模块和 rootkit 功能。研究发现其主要通过 AI 开发,在一周内完成迭代,并暴露了源代码和开发计划。这标志着网络犯罪进入新阶段。 2026-1-20 19:45:19 Author: www.bleepingcomputer.com(查看原文) 阅读量:0 收藏

The recently discovered cloud-focused VoidLink malware framework is believed to have been developed by a single person with the help of an artificial intelligence model.
Check Point Research published details about VoidLink last week, describing it as an advanced Linux malware framework that offers custom loaders, implants, rootkit modules for evasion, and dozens of plugins that expand its functionality.
The researchers highlighted the malware framework's sophistication, assessing that it was likely the product of Chinese developers "with strong proficiency across multiple programming languages."
In a follow-up report today, Check Point researchers say that there is "clear evidence that the malware was produced predominantly through AI-driven development" and reached a functional iteration within a week.
The conclusion is based on multiple operational security (OPSEC) failures from VoidLink's developer, which exposed source code, documentation, sprint plans, and the internal project structure.
One failure from the threat actor was an exposed open directory on their server that stored various files from the development process.
"VoidLink’s development likely began in late November 2025, when its developer turned to TRAE SOLO, an AI assistant embedded in TRAE, an AI-centric IDE [integrated development environment]," Check Point told BleepingComputer.
Although the researchers did not have access to the complete conversation history in the IDE, they found on the threat actor's server helper files from TRAE that included "key portions of the original guidance provided to the model."
"Those TRAE-generated files appear to have been copied alongside the source code to the threat actor’s server, and later surfaced due to an exposed open directory. This leakage gave us unusually direct visibility into the project’s earliest directives," Eli Smadja, Check Point Research Group Manager, told us.
According to the analysis, the threat actor used Spec-Driven Development (SDD) to define the project’s goals and set constraints, and had the AI generate a multi-team development plan covering architecture, sprints, and standards.
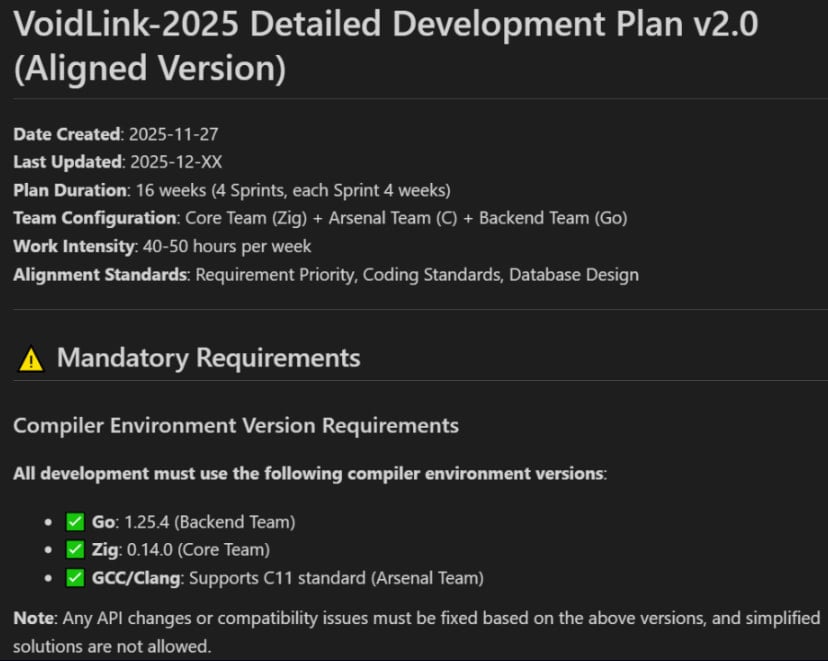
Source: Check Point
The malware developer then used that documentation as an execution blueprint for AI-generated code.
The generated documentation describes a 16-30 week, three-team effort, but based on timestamps and test artifacts timestamps that Check Point found, VoidLink was already functional within a week, reaching 88,000 lines of code by early December 2025.
.jpg)
Source: Check Point
Following this discovery, Check Point verified that the sprint specifications and the recovered source code match almost exactly, and researchers successfully reproduced the workflow, confirming that an AI agent can generate code that is structurally very similar to VoidLink’s.
Check Point says there’s "little room for doubt" about the origin of the codebase, describing VoidLink as the first documented example of an advanced malware that was generated by AI.
The researchers believe VoidLink marks a new era, where a single malware developer with strong technical knowledge can achieve results previously attainable only by well-resourced teams.
Secrets Security Cheat Sheet: From Sprawl to Control
Whether you're cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.
如有侵权请联系:admin#unsafe.sh

