好的,用户希望我用中文总结这篇文章的内容,控制在100字以内,而且不需要以“文章内容总结”或“这篇文章”这样的开头。直接写文章描述即可。 首先,我需要通读整篇文章,理解其主要观点。文章主要讨论了身份威胁检测与响应(ITDR)的重要性,特别是在当前网络安全威胁日益增加的情况下。攻击者不再通过入侵系统,而是通过合法登录来获取访问权限。因此,组织需要深入洞察IT事件,以防御账户被入侵和内部威胁。 文章还提到了常见的身份攻击方式,如钓鱼邮件、泄露密码和社会工程学等。这些攻击手段容易自动化和大规模实施,对用户造成持续的压力。即使只有一个攻击突破防线,也可能给组织带来灾难性后果。 为了应对这些威胁,文章建议采取多层次的防御措施,包括邮件过滤、多因素认证、访问控制等。然而,这些预防措施并非万无一失,因此检测和响应能力至关重要。ITDR提供了深入的可见性,帮助组织识别可疑活动并迅速采取行动。 此外,文章介绍了Tenfold软件的解决方案tenfold,它结合了身份治理和安全功能,提供全面的事件审计和日志管理功能,并且以用户友好的方式呈现。 综上所述,文章强调了在当前威胁环境下身份安全的重要性,并介绍了Tenfold提供的解决方案来帮助组织提升防御能力。 </think> 文章强调了身份安全在现代网络安全中的重要性,并介绍了Tenfold软件的解决方案tenfold如何通过整合身份治理与安全功能来帮助组织提升防御能力。 2026-1-20 15:15:21 Author: www.bleepingcomputer.com(查看原文) 阅读量:0 收藏

Attackers no longer break in, they log in. To defend against compromised accounts and insider threats, organizations need in-depth visibility into IT events. Identity Threat Detection helps you spot suspicious activity and stop attackers in their tracks.
Defend against your #1 threat
From phishing mails to leaked passwords and social engineering, identity-based attacks are the most common form of attack businesses face today. Low-effort approaches such as malicious emails and password spraying are easy to automate and run at scale, resulting in a constant barrage that can wear down even the most vigilant users.
If just one attack among thousands of attempts makes it past your defenses, it can spell disaster for your organization.
Once an attacker has access to a single account on your network, they move fast, spreading to other systems, covering their tracks and lying in wait until they are ready to cause as much damage as possible.
Go from risk mitigation to proactive defense
There are many steps organizations can take to minimize the risk of a successful attack. Email filters can stop phishing attempts from hitting your users’ inboxes. MFA and conditional access help prevent unauthorized logins.
Effective access control designed around the Principle of Least Privilege (PoLP) limits the amount of damage a single compromised account can cause. These are all good ideas that you should include in your security strategy.
The problem is that no form of prevention is 100% effective. Which leaves security teams with a burning question: How can you tell if you have suffered a breach? Would you even know if an attacker was lurking in your environment right now? Or would you be left unaware until they make themselves known? Once it’s too late, your data is gone and every device has been encrypted?
With identities becoming the frontline of today’s threat landscape, organizations that want to mount an effective defense need to make Identity Security a centerpiece of their strategy. It is no longer enough to reduce risk and hope for the best.
Identity Threat Detection & Response (ITDR) gives you the in-depth visibility you need to see what is happening in your environment and act when it matters most.
tenfold: Your all-in-one solution for Identity Governance & Security
From role-based access to lifecycle automation and access reviews for shared content, tenfold gives you full control over user accounts and IT privileges. With a growing set of logging and event auditing features, our platform now combines Identity Governance and Identity Security in a single solution. The best part? All new features are included in your subscription at no additional cost.
Book your personal tenfold demo to see it in action!
Know your enemy, know your user
By logging and analyzing events across all systems, ITDR gives you up-to-the-minute information on exactly what is going on in your IT environment: What your users are up to, when new accounts are added or security groups are changed.
From there, filters, alerts and behavioral analytics allow you to spot suspicious activity and respond to threats quickly.
The better you understand your users’ normal behavior, the easier it becomes to identify malicious activity.
For example, most employees are only active at specific times and stick to a small number of apps, folders and resources (whatever is relevant to their current project). By contrast, some IT events are clear red flags that your security team will want to investigate right away:
- A sudden spike in (unsuccessful) logon events
- Unexpected logins to privileged accounts
- New accounts being created outside of onboarding workflows
- Changes to group policy or security settings
- Users accessing a lot of directories in a short time (outside their normal job role)
Even if there is a innocent explanation for an unusual pattern in IT activity, being aware of these events allows your IT team to investigate what is going on and rule out an account breach or insider threat. When it comes to suspicious behavior, you should always follow the approach “better safe than sorry.”
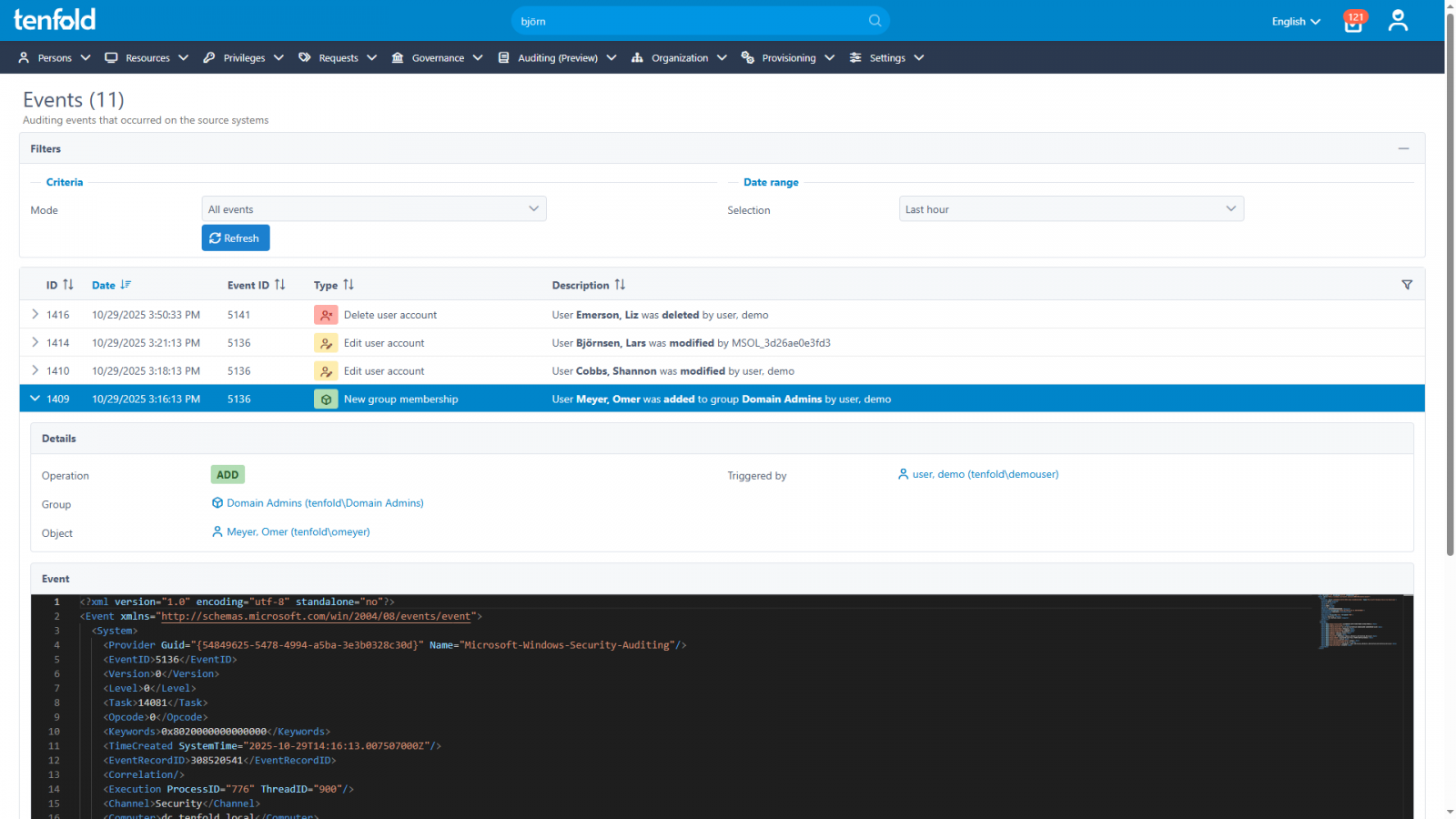
tenfold: Governance & Event Auditing in one platform
Are you tired of flying blind and want to boost your Identity Security strategy in 2026? Are you looking for a powerful Identity solution that won’t nickel and dime you with per-feature pricing?
With tenfold, you get Identity Governance, Data Access Governance and Event Auditing – all in the same platform. That means with just a single subscription, you can:
- Automate on- and offboarding with user lifecycles & role-based access
- Get a detailed breakdown of user permissions down to folders and objects
- Implement access reviews across local and cloud systems
- Investigate IT events from a centralized log with powerful filters
- Identify suspicious activity and respond to attacks quickly
Take your first steps towards Identity Threat Detection with our user-friendly, no-code platform – built from the ground up to be deployed quickly and easy to operate. It’s time to close the loop and govern with confidence, from streamlined onboarding to event auditing.
Learn more about tenfold by booking a personalized walkthrough of our solution today.
Sponsored and written by Tenfold Software.
如有侵权请联系:admin#unsafe.sh