嗯,用户让我帮忙总结一篇文章的内容,控制在100字以内,而且不需要特定的开头。首先,我需要通读整篇文章,抓住主要信息。 文章讲的是发现了17个恶意扩展程序,和GhostPoster活动有关,这些扩展在Chrome、Firefox和Edge商店里,总安装量有84万次。这些扩展隐藏了恶意的JavaScript代码在logo里,监控浏览器活动,植入后门。代码从外部资源获取混淆的payload,用来追踪用户浏览、劫持 affiliate链接,注入iframe进行广告和点击欺诈。 LayerX报告指出活动还在继续,尽管被曝光了。这些扩展在2020年就已经存在了,说明长期成功运营。其中有一个新的变种,在InstagramDownloader中使用了更复杂的机制来隐藏恶意代码。 最后提到这些扩展已经被移除,但已经安装的用户可能仍有风险。 总结的时候要涵盖:恶意扩展数量、涉及浏览器、安装量、隐藏代码的方式、功能以及活动仍在继续的事实。控制在100字以内。 </think> 研究人员发现17款恶意浏览器扩展程序与GhostPoster活动相关联,在Chrome、Firefox和Edge商店中累计安装量达84万次。这些扩展隐藏恶意JavaScript代码于logo中,监控浏览器活动并植入后门。代码从外部资源获取混淆的payload,用于追踪用户浏览、劫持电商平台 affiliate链接,并注入隐形iframe以实施广告和点击欺诈。该活动自2020年起持续至今。 2026-1-18 02:0:47 Author: www.bleepingcomputer.com(查看原文) 阅读量:0 收藏

Another set of 17 malicious extensions linked to the GhostPoster campaign has been discovered in Chrome, Firefox, and Edge stores, where they accumulated a total of 840,000 installations.
The GhostPoster campaign was first reported by Koi Security researchers in December. They found 17 extensions that were hiding malicious JavaScript code in their logo images, which monitored browser activity and planted a backdoor.
The code fetches a heavily obfuscated payload from an external resource, which tracks the victim’s browsing activity, hijacks affiliate links on major e-commerce platforms, and injects invisible iframes for ad fraud and click fraud.
A new report from browser security platform LayerX indicates that the campaign is still ongoing despite being exposed, and the following 17 extensions are part of it:
- Google Translate in Right Click – 522,398 installs
- Translate Selected Text with Google - 159,645 installs
- Ads Block Ultimate – 48,078 installs
- Floating Player – PiP Mode – 40,824 installs
- Convert Everything – 17,171 installs
- Youtube Download – 11,458 installs
- One Key Translate – 10,785 installs
- AdBlocker – 10,155 installs
- Save Image to Pinterest on Right Click – 6,517 installs
- Instagram Downloader – 3,807 installs
- RSS Feed – 2,781 installs
- Cool Cursor – 2,254 installs
- Full Page Screenshot – 2,000 installs
- Amazon Price History – 1,197 installs
- Color Enhancer – 712 installs
- Translate Selected Text with Right Click – 283 installs
- Page Screenshot Clipper – 86 installs
According to the researchers, the campaign originated on Microsoft Edge and then expanded to Firefox and Chrome.
LayerX found that some of the above extensions have been present in browser add-on stores since 2020, indicating a successful long-term operation.

Source: LayerX
Although evasion and post-activation capabilities remain mostly the same as previously documented by Koi, LayerX has identified a more advanced variant in the ‘Instagram Downloader’ extension.
The difference consists of moving the malicious staging logic into the extension’s background script and using a bundled image file as a covert payload container rather than only an icon.
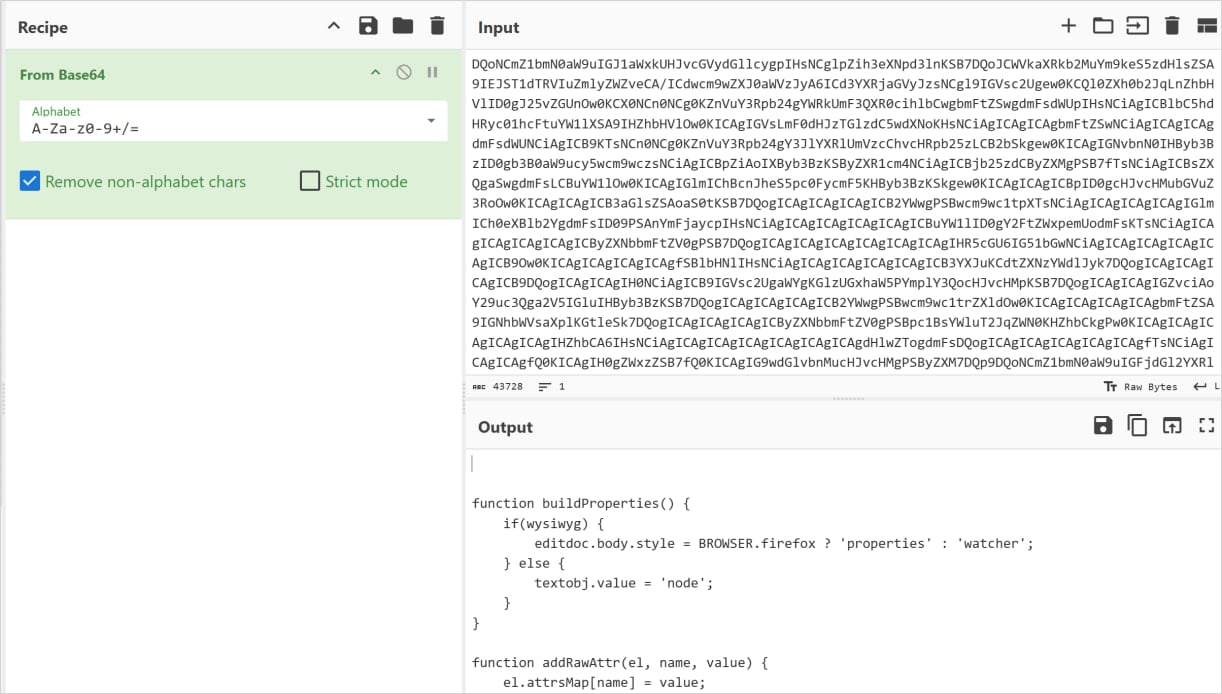
Source: LayerX
At runtime, the background script scans the image’s raw bytes for a specific delimiter (>>>>), extracts and stores the hidden data in local extension storage, then later Base64-decodes and executes it as JavaScript.
“This staged execution flow demonstrates a clear evolution toward longer dormancy, modularity, and resilience against both static and behavioral detection mechanisms,” comments LayerX about the newest GhostPoster variant.
The researchers said that the newly identified extensions are no longer present in Mozilla's and Microsoft's add-on stores. However, users who installed them in their browsers may still be at risk.
BleepingComputer has contacted Google about the extensions being present in the Chrome Web Store, and a spokesperson confirmed that all of them have been removed.
The 2026 CISO Budget Benchmark
It's budget season! Over 300 CISOs and security leaders have shared how they're planning, spending, and prioritizing for the year ahead. This report compiles their insights, allowing readers to benchmark strategies, identify emerging trends, and compare their priorities as they head into 2026.
Learn how top leaders are turning investment into measurable impact.
如有侵权请联系:admin#unsafe.sh

