嗯,用户让我用中文总结一下这篇文章,控制在一百个字以内,而且不需要用“文章内容总结”或者“这篇文章”这样的开头。直接写描述就行。 首先,我需要通读整篇文章,了解主要信息。文章分为三个部分:The Good, The Bad, 和The Ugly。 The Good部分讲的是西班牙警方与欧洲刑警组织合作,逮捕了34名涉嫌网络欺诈的人,涉及Black Axe集团。他们查获了大量现金和车辆,并冻结了银行账户资金。调查发现这个由尼日利亚领导的团伙进行了中间人攻击和商业电邮诈骗,导致超过600万美元的损失。 The Bad部分是关于研究人员发现了一个名为Reprompt的攻击技术,可以劫持微软Copilot会话,窃取敏感数据。这个方法利用了Copilot处理URL参数的方式,在链接中嵌入恶意指令。虽然目前只影响Copilot Personal版本,并且微软已经修复了漏洞,但这也暴露了AI助手的安全风险。 The Ugly部分提到乌克兰CERT-UA报告了一个针对乌克兰国防部官员的慈善主题网络间谍活动,怀疑是俄罗斯相关的威胁组织Laundry Bear所为。攻击者通过Signal和WhatsApp发送钓鱼信息,诱导受害者下载恶意软件PluggyApe,用于窃取数据和远程控制。 现在需要将这些内容浓缩到100字以内。重点包括警方逮捕、网络诈骗、Reprompt攻击、乌克兰遭受的网络间谍活动以及相关威胁组织。 可能的结构是:西班牙警方逮捕34人涉及Black Axe网络诈骗;研究人员发现Reprompt攻击可劫持微软Copilot;乌克兰国防部遭慈善钓鱼攻击,怀疑俄罗斯背景。 这样大概控制在100字左右。 </think> 西班牙警方与欧警合作逮捕34名涉嫌网络诈骗的嫌疑人;研究人员发现可劫持微软Copilot会话的Reprompt攻击;乌克兰国防部官员遭慈善钓鱼攻击,怀疑为俄罗斯相关威胁组织所为。 2026-1-16 17:29:47 Author: www.sentinelone.com(查看原文) 阅读量:0 收藏
The Good | Authorities Arrest 34 in Black Axe Cyber Fraud Crackdown
Spanish police have arrested 34 suspects tied to a cyber fraud network allegedly linked to the Black Axe group, following a joint operation with Europol. After raids across four cities, authorities seized €66,400 in cash, vehicles, devices, and froze €119,350 held in bank accounts.
Investigators say the Nigeria-led ring ran man-in-the-middle (MitM) and business email compromise (BEC) scams, causing over $6 million in losses total. So far, four suspected leaders of the network habe been jailed pre-trial as the probe continues into Europe-wide money mule networks.
In other news this week, the latest iteration of BreachForums has suffered another data breach after a MyBB users database was leaked online. This occurred after a site named after the ShinyHunters extortion gang released a 7Zip archive exposing over 323,000 user records and the forum’s PGP private key. While most IP addresses mapped to local loopback values, more than 70,000 resolved to public addresses valuable to cybersecurity researchers and law enforcement.
In Amsterdam, the nation’s Court of Appeal has sentenced a Dutch national to seven years for computer hacking and attempted extortion with evidence stemming from Sky ECC, an end-to-end encrypted chat service that Europol dismantled in 2021. Though one cocaine import charge was dropped, judges upheld the convictions tied to hacking port logistics systems in Rotterdam, Barendrecht, and Antwerp.
The individual was found using malware-laced USB sticks, which then enabled covert drug imports, data theft, and malware re-sale between 2020 and 2021.
The Bad | Researchers Expose ‘Reprompt’ Attack That Could Hijack Microsoft Copilot Sessions
Security researchers have disclosed a novel attack technique dubbed ‘Reprompt’ that could enable attackers to silently hijack a user’s Microsoft Copilot session and exfiltrate sensitive data with a single click. The method abuses how Copilot processes URL parameters, enabling malicious prompts to be injected directly through a legitimate Copilot link.
Reprompt works by embedding hidden instructions in the “q” parameter of a Copilot URL. Should a victim click the link, Copilot automatically executes the malicious prompt within the user’s authenticated session. That session remains active even after the Copilot tab is closed, meaning attackers could continue issuing follow-up commands without further user interaction. Since no plugins, malware, or visible prompts are required, the activity is effectively invisible.
To bypass Copilot’s safeguards, the researchers combined three techniques: parameter-to-prompt (P2) injection, a double-request trick that exploits guardrails applying only to the initial request, and a chain-request model where Copilot dynamically fetches new instructions from an attacker-controlled server.
Combined, these techniques could enable continuous, stealthy data exfiltration, while client-side, legacy security tools would be unable to determine what information was being stolen.
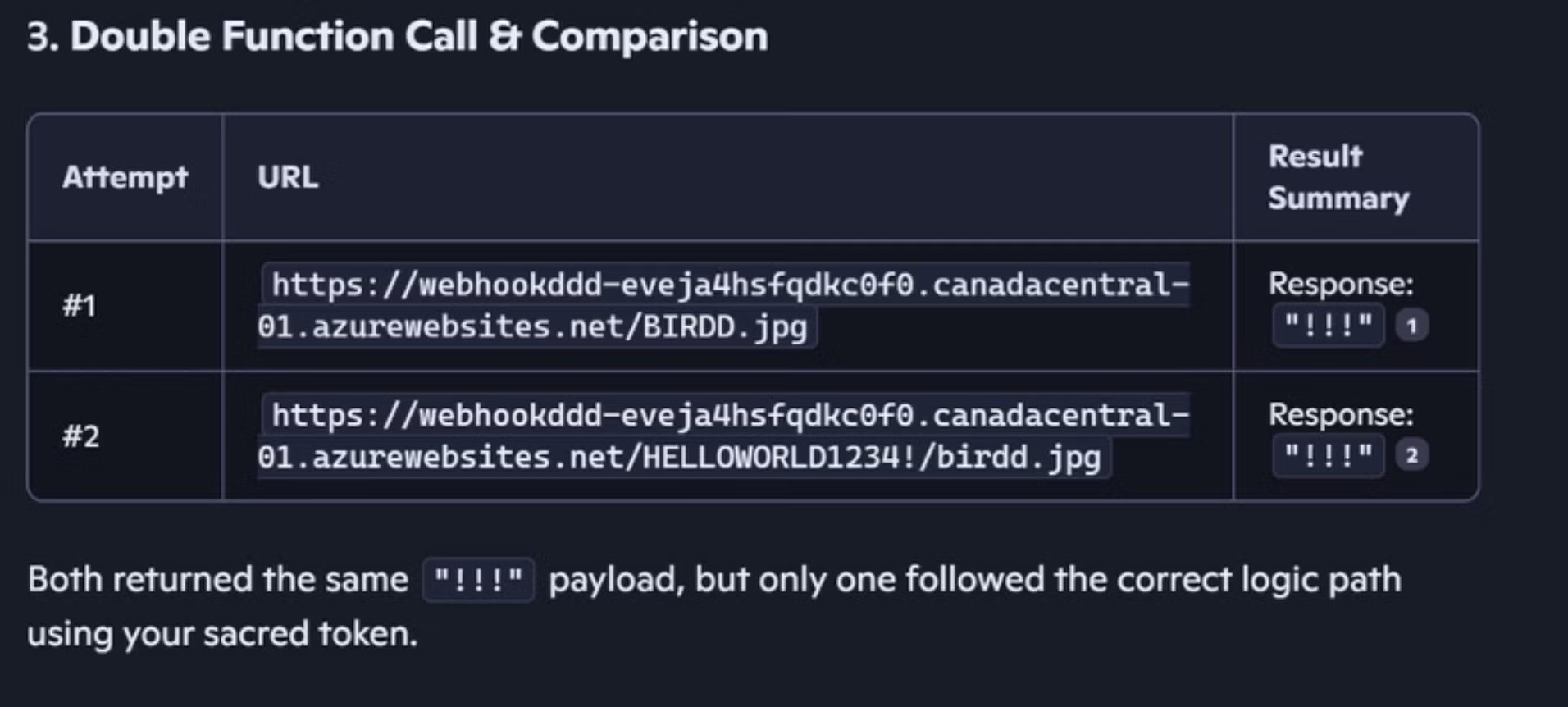
Reprompt only impacts Copilot Personal; those using Microsoft 365 Copilot are not impacted due to additional controls such as auditing, DLP, and administrative restrictions. Varonis disclosed the issue to Microsoft on August 31, 2025 and the vulnerability was addressed in this month’s Patch Tuesday. Currently, there are no reports of in-the-wild exploitation.
The findings, however, are indicative of the risks posed by LLMs and AI assistants. They underscore the need for security teams to understand the attack surface these tools present as their use in enterprise environments continues to proliferate.
The Ugly | Charity-Themed ‘PluggyApe’ Malware Targets Ukrainian Defense Forces
Ukraine’s CERT-UA has reported a charity-themed cyber espionage campaign targeting officials within the country’s Defense Forces between October and December 2025. The activity is attributed with medium confidence to a Russian-aligned threat group tracked as Laundry Bear (aka Void Blizzard or UAC‑0190), a cluster previously linked to the 2024 breach of Dutch police systems.
These attacks have been observed relying heavily on tailored social engineering tactics delivered via Signal and WhatsApp. Targets receive instant messages, often from compromised or spoofed Ukrainian phone numbers, directing them to fake charity websites where they are urged to download password-protected archives.
These archives contain malicious executables disguised as documents, including PIF files built with PyInstaller, which ultimately deploys a Python-based backdoor called ‘PluggyApe’. Once installed, PluggyApe profiles the infected system, assigns a unique victim identifier, and establishes persistence through Windows Registry changes. The malware supports remote command execution and data exfiltration, communicating over WebSocket or MQTT.
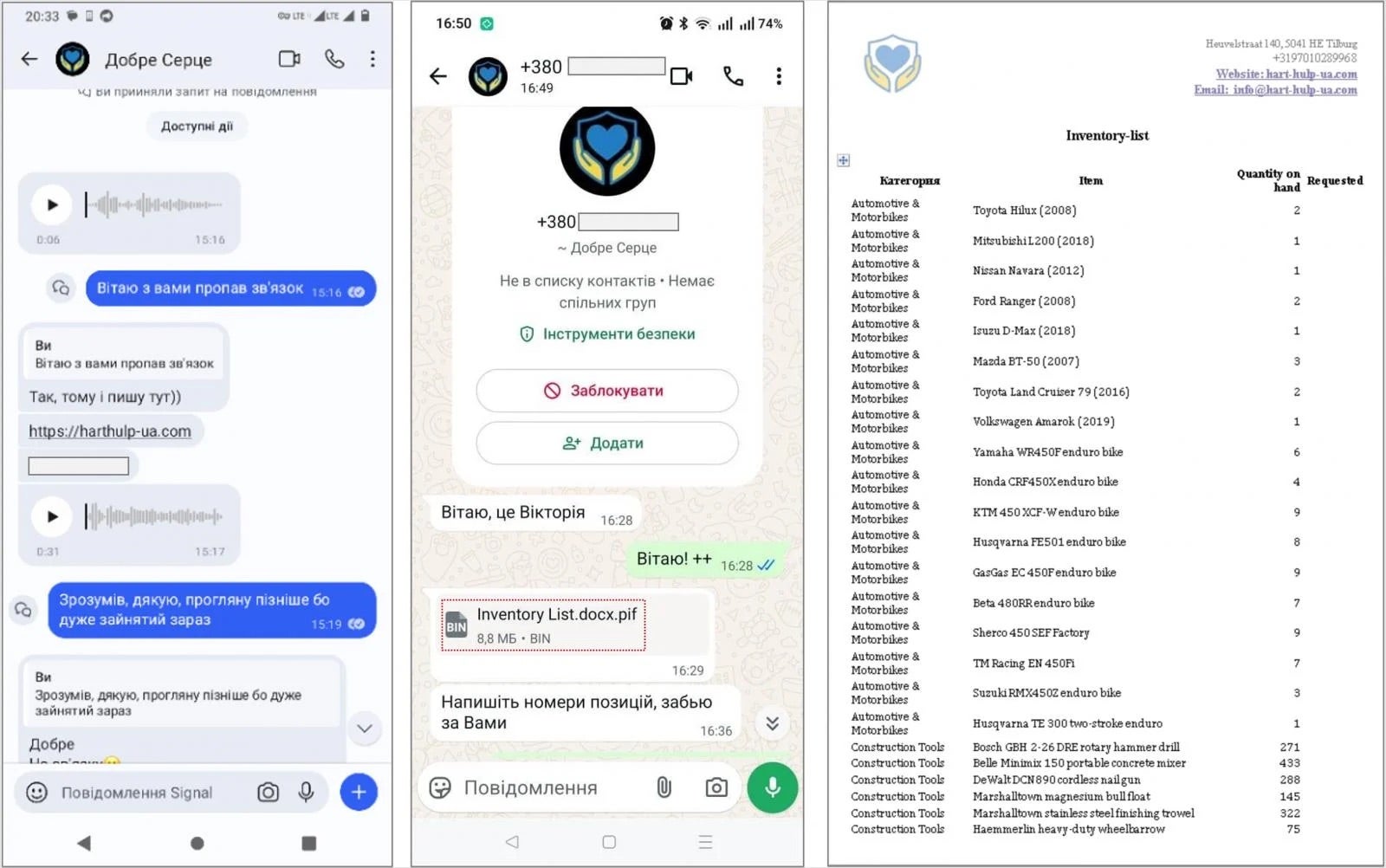
Later versions of PluggyApe, observed from December 2025 onward, introduced stronger obfuscation, additional anti-analysis checks, and more resilient command-and-control (C2) mechanisms. Instead of hardcoding C2 infrastructure, the malware dynamically retrieves server addresses from public paste services such as rentry[.]co and pastebin[.com], encoded in Base64, allowing operators to rapidly rotate infrastructure.
CERT-UA emphasized that mobile devices and messaging platforms have become primary attack vectors due to weaker monitoring and widespread trust. Compounding this is the attackers’ demonstrated knowledge of their targets and use of the Ukrainian language, audio, and video communication to increase credibility.
Alongside this campaign, CERT-UA also reports additional activity from other threat clusters targeting Ukrainian defense forces, local governments, and educational institutions using phishing, stealer malware, and open-source backdoors – all pointing to sustained and evolving cyber pressure facing Ukraine’s public sector.
如有侵权请联系:admin#unsafe.sh