
嗯,用户让我用中文总结一下这篇文章的内容,控制在一百个字以内,而且不需要用“文章内容总结”或者“这篇文章”这样的开头,直接写描述就行。首先,我需要通读整篇文章,抓住主要信息。 文章主要讲的是2025年的网络威胁情况,特别是勒索软件和供应链攻击的增加。勒索软件攻击数量上升了52%,供应链攻击更是几乎翻倍。主要的勒索软件集团Qilin在这一年占据主导地位。同时,供应链攻击影响了各个行业,尤其是IT和技术部门。 接下来,文章还提到了一些具体的案例和趋势,比如利用OAuth漏洞、国家支持的APT组织攻击云服务提供商等。最后,文章给出了一些应对建议,如加强身份验证、加密数据、进行定期安全测试等。 现在我要把这些信息浓缩到100字以内。首先点明年份和主要威胁类型:勒索软件和供应链攻击显著增加。然后提到数据增长情况:勒索软件增长52%,供应链攻击增长93%。接着说明影响范围:覆盖多个行业和地区。最后简要提及应对措施:强化网络安全措施。 这样组织起来应该符合用户的要求。 </think> 2025年网络威胁显著增加,勒索软件攻击增长52%,供应链攻击激增93%,影响多个行业和地区,需强化网络安全措施应对风险。 2026-1-16 08:31:12 Author: cyble.com(查看原文) 阅读量:1 收藏
The threat landscape shifted significantly in 2025. Here are the threats and trends to watch as we enter 2026.
Overview
Ransomware and supply chain attacks soared in 2025, and persistently elevated attack levels suggest that the global threat landscape will remain perilous heading into 2026.
Cyble recorded 6,604 ransomware attacks in 2025, up 52% from the 4,346 attacks claimed by ransomware groups in 2024. The year ended with a near-record 731 ransomware attacks in December, second only to February 2025’s record totals (chart below).
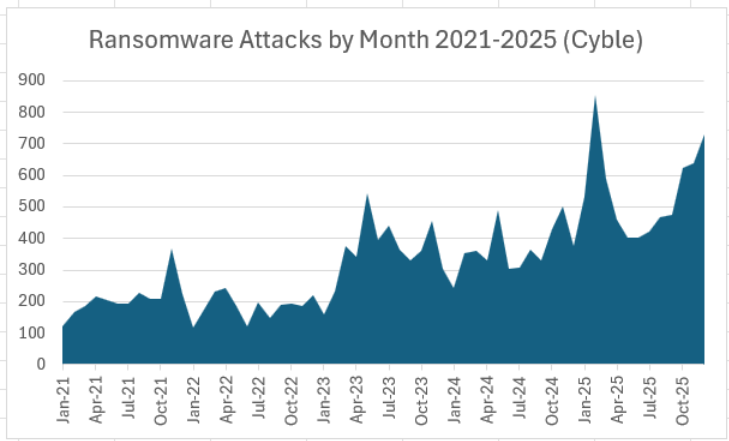
Supply chain attacks nearly doubled in 2025, as Cyble dark web researchers recorded 297 supply chain attacks claimed by threat groups in 2025, up 93% from 154 such events in 2024 (chart below). As ransomware groups are consistently behind more than half of supply chain attacks, the two attack types have become increasingly linked.
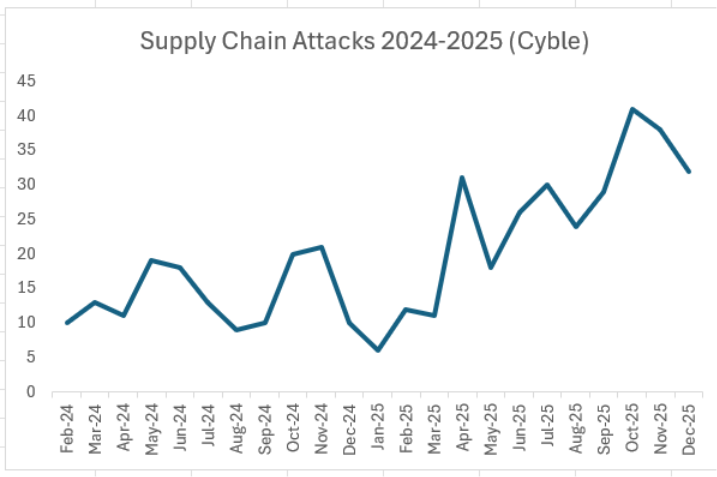
While supply chain attacks have declined in the two months since October’s record, they remain above even the elevated trend that began in April 2025.
We’ll take a deeper look at ransomware and supply chain attack data, including targeted sectors and regions, attack trends, and leading threat actors. Some of the data and insights come from Cyble’s new Annual Threat Landscape Report covering cybercrime, ransomware, vulnerabilities, and other 2025-2026 cyber threat trends.
Qilin Dominated After RansomHub Declined
Qilin emerged as the leading ransomware group in April after RansomHub went offline amid possible sabotage by rival Dragonforce. Qilin has remained on top in every month but one since, and was once again the top ransomware group in December with 190 claimed victims (December chart below).

December was also noteworthy for the long-awaited resurgence of Lockbit and the continued emergence of Sinobi.
For full-year 2025, Qilin dominated, claiming 17% of all ransomware victims (full-year chart below). Of the top five ransomware groups in 2025, only Akira and Play also made the top five in 2024, as RansomHub, Lockbit and Hunters all fell from the top five. Lockbit was hampered by repeated law enforcement actions, while Hunters announced it was shutting down in mid-2025.

Cyble documented 57 new ransomware groups and 27 new extortion groups in 2025, including emerging leaders like Sinobi and The Gentlemen. Over 350 new ransomware strains were discovered in 2025, largely based on the MedusaLocker, Chaos, and Makop ransomware families.
Among newly emerged ransomware groups, Cyble observed heightened attacks on critical infrastructure industries (CII), especially in Government & LEA and Energy & Utilities, by groups such as Devman, Sinobi, Warlock, and Gunra. Several newly emerged groups targeted the software supply chain, among them RALord/Nova, Warlock, Sinobi, The Gentlemen, and BlackNevas, with a particular focus on the IT & ITES, Technology, and Transportation & Logistics sectors.
Cl0p’s Oracle E-Business Suite vulnerability exploitation campaign led to a supply-chain impact on more than 118 entities globally, including those in the IT & ITES sector. Among these, six entities from the critical infrastructure industries (CII) were observed to have fallen victim to this exploitation campaign. The Fog ransomware group also leaked multiple GitLab source codes from several IT companies.
The U.S. remains by far the most frequent target of ransomware groups, accounting for 55% of ransomware attacks in 2025 (chart below). Canada, Germany, the UK, Italy, and France were also consistent targets for ransomware groups.

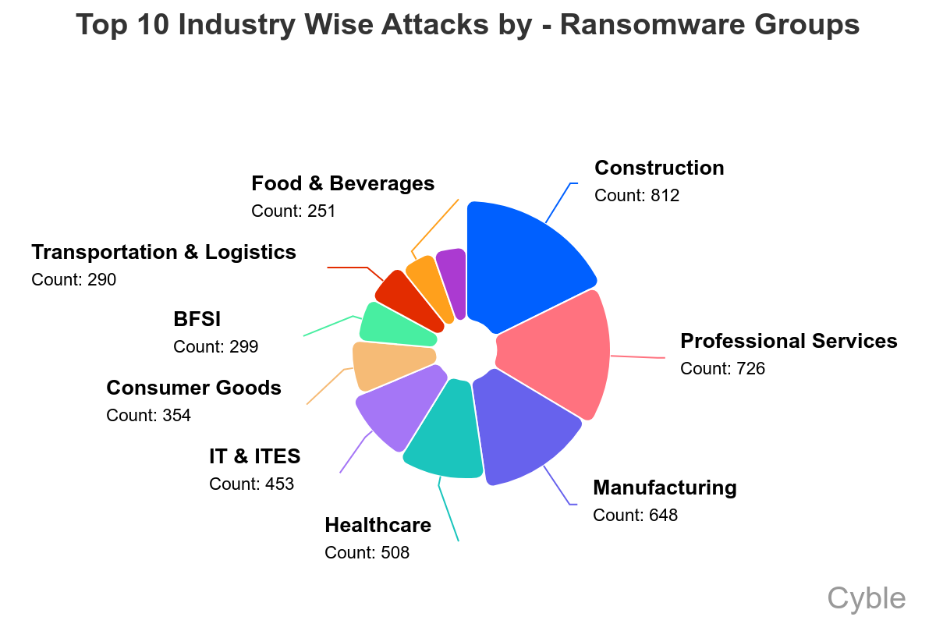
Construction, professional services, and manufacturing were consistently the sectors most targeted by ransomware groups, with healthcare and IT rounding out the top five (chart below).
Supply Chain Attacks Hit Every Industry and Sector in 2025
Every sector tracked by Cyble was hit by a software supply chain attack in 2025 (chart below), but because of the rich target they represent and their significant downstream customer base, the IT and Technology sectors were by far the most frequently targeted, accounting for more than a third of supply chain attacks.

Supply chain intrusions in 2025 expanded far beyond traditional package poisoning, targeting cloud integrations, SaaS trust relationships, and vendor distribution pipelines.
Adversaries are increasingly abusing upstream services—such as identity providers, package registries, and software delivery channels—to compromise downstream environments on a large scale.
A few examples highlighting the evolving third-party risk landscape include:
Attacks targeting Salesforce data via third-party integrations did not modify code; instead, they weaponized trust between SaaS platforms, illustrating how OAuth-based integrations can become high-impact supply chain vulnerabilities when third-party tokens have been compromised.
The nation-state group Silk Typhoon intensified operations against IT and cloud service providers, exploiting VPN zero-days, password-spraying attacks, and misconfigured privileged access systems. After breaching upstream vendors such as MSPs, remote-management platforms, or PAM service providers, the group pivoted into customer environments via inherited admin credentials, compromised service principals, and high-privilege cloud API permissions.
A China-aligned APT group, PlushDaemon, compromised the distribution channel of a South Korean VPN vendor, replacing legitimate installers with a trojanized version bundling the SlowStepper backdoor. The malicious installer, delivered directly from the vendor’s website, installed both the VPN client and a modular surveillance framework supporting credential theft, keylogging, remote execution, and multimedia capture. By infiltrating trusted security software, the attackers gained persistent access to organizations relying on the VPN for secure remote connectivity, turning a defensive tool into an espionage vector.
Conclusion
The significant supply chain and ransomware threats facing security teams as we enter 2026 require a renewed focus on cybersecurity best practices that can help protect against a wide range of cyber threats. These practices include:
- Prioritizing vulnerabilities based on risk.
- Protecting web-facing assets.
- Segmenting networks and critical assets.
- Hardening endpoints and infrastructure.
- Strong access controls, allowing no more access than is required, with frequent verification.
- A strong source of user identity and authentication, including multi-factor authentication and biometrics, as well as machine authentication with device compliance and health checks.
- Encryption of data at rest and in transit.
- Ransomware-resistant backups that are immutable, air-gapped, and isolated as much as possible.
- Honeypots that lure attackers to fake assets for early breach detection.
- Proper configuration of APIs and cloud service connections.
- Monitoring for unusual and anomalous activity with SIEM, Active Directory monitoring, endpoint security, and data loss prevention (DLP) tools.
- Routinely assessing and confirming controls through audits, vulnerability scanning, and penetration tests.
Cyble’s comprehensive attack surface management solutions can help by scanning network and cloud assets for exposures and prioritizing fixes, in addition to monitoring for leaked credentials and other early warning signs of major cyberattacks. Additionally, Cyble’s third-party risk intelligence can help organizations carefully vet partners and suppliers, providing an early warning of potential risks.
如有侵权请联系:admin#unsafe.sh
