嗯,用户让我帮忙总结一篇文章的内容,控制在一百个字以内,而且不需要特定的开头。首先,我需要仔细阅读这篇文章,理解其主要内容。 文章讲的是美国网络安全和基础设施安全局(CISA)要求政府机构修补一个高危漏洞CVE-2025-8110。这个漏洞存在于Gogs软件中,Gogs是一个类似于GitLab或GitHub Enterprise的代码托管平台,用Go语言编写。这个漏洞允许经过身份验证的攻击者通过路径遍历绕过之前修补的漏洞,进而执行远程代码。 漏洞被利用的情况是攻击者创建包含符号链接的仓库,指向敏感系统文件,然后通过PutContents API写入数据,覆盖仓库外的目标文件。这可能导致攻击者强制目标系统执行任意命令。 Wiz Research在7月发现这个漏洞,并在10月30日向Gogs维护者报告。补丁在上周发布,增加了符号链接感知的路径验证。CISA确认了这一报告,并要求联邦机构在三周内修补漏洞。 用户的需求是用中文总结内容,控制在100字以内。所以我要提取关键信息:CISA下令修补Gogs高危漏洞CVE-2025-8110,该漏洞允许远程代码执行,影响政府机构。 接下来需要确保语言简洁明了,不使用复杂的术语,并且符合用户的要求。 </think> 美国网络安全机构CISA下令政府机构修复Gogs软件中的高危漏洞CVE-2025-8110,该漏洞可被用于远程代码执行攻击。 2026-1-12 20:15:26 Author: www.bleepingcomputer.com(查看原文) 阅读量:0 收藏

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has ordered government agencies to secure their systems against a high-severity Gogs vulnerability that was exploited in zero-day attacks.
Designed as an alternative to GitLab or GitHub Enterprise and written in Go, Gogs is often exposed online for remote collaboration.
Tracked as CVE-2025-8110, this remote code execution (RCE) security flaw stems from a path traversal weakness in the PutContents API and allows authenticated attackers to bypass protections implemented for a previously patched RCE bug (CVE-2024-55947) by overwriting files outside the repository via symbolic links.
Attackers can abuse this flaw by creating repos containing symbolic links pointing to sensitive system files, and then writing data through the symlink using the PutContents API, overwriting targets outside the repository. By overwriting Git configuration files, specifically the sshCommand setting, threat actors can force target systems to execute arbitrary commands.
Wiz Research discovered the vulnerability while investigating a malware infection affecting a customer's Internet-facing Gogs server in July and reported the flaw to Gogs maintainers on July 17. They acknowledged Wiz's report three months later, on October 30, and released patches for CVE-2025-8110 last week that add symlink-aware path validation at all file-write entry points.
According to a disclosure timeline shared by Wiz Research, a second wave of attacks targeting this vulnerability as a zero-day was observed on November 1.
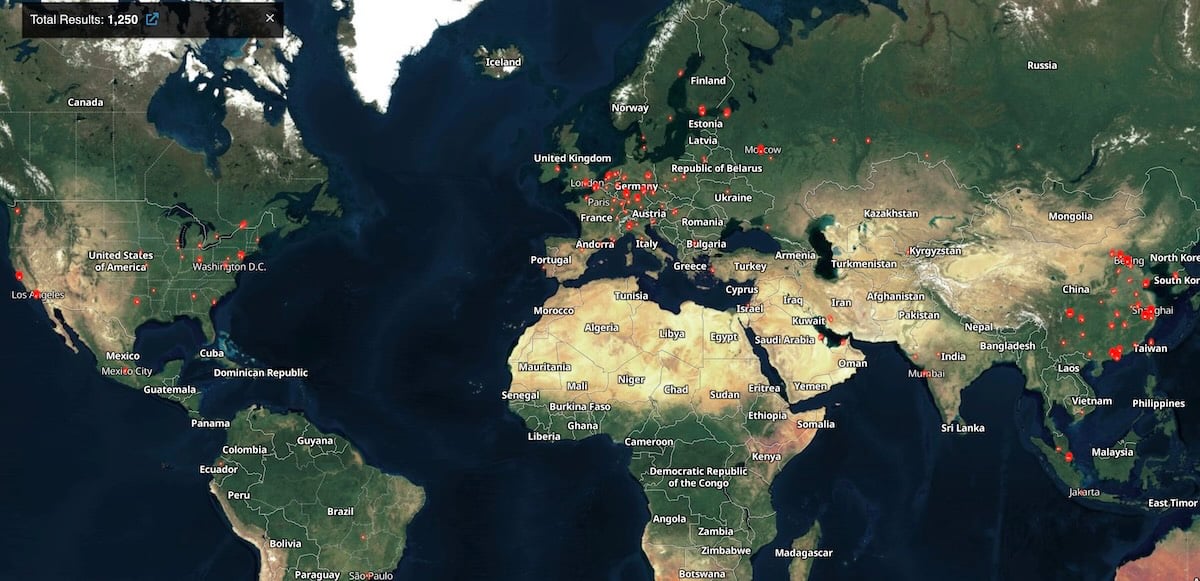
While investigating these campaigns, Wiz researchers found over 1,400 Gogs servers exposed online (1,250 of which remain exposed) and more than 700 instances showing signs of compromise.
CISA has now confirmed Wiz's report and added the security flaw to its list of vulnerabilities exploited in the wild, ordering Federal Civilian Executive Branch (FCEB) agencies to patch within three weeks, by February 2, 2026.
FCEB agencies are non-military U.S. executive branch agencies, such as the Department of Energy, the Department of Justice, the Department of Homeland Security, and the Department of State.
"This type of vulnerability is a frequent attack vector for malicious cyber actors and poses significant risks to the federal enterprise," CISA warned. "Apply mitigations per vendor instructions, follow applicable BOD 22-01 guidance for cloud services, or discontinue use of the product if mitigations are unavailable."
To further reduce the attack surface, Gogs users are advised to disable the default open-registration setting immediately and limit server access using a VPN or an allow list.
Additionally, admins who want to check for signs of compromise on their Gogs instance should look for suspicious use of the PutContents API and for repositories with random eight-character names created during the two attack waves.
Secrets Security Cheat Sheet: From Sprawl to Control
Whether you're cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.
如有侵权请联系:admin#unsafe.sh

