嗯,用户让我总结这篇文章的内容,控制在一百个字以内。首先,我需要快速浏览文章,抓住关键点。 文章标题提到SmarterTools SmarterMail存在远程代码执行漏洞,CVE编号是2025-52691。这是一个未认证的任意文件上传漏洞,可能导致远程代码执行。影响版本是Build 9406及之前,修复版本是Build 9413。 接下来,用户要求总结在一百字以内,不需要特定开头。我需要涵盖漏洞名称、影响、攻击方式、修复措施和严重性评分。 可能的结构:漏洞名称+攻击方式+影响版本+修复版本+CVSS评分。 这样就能在简洁的句子中包含所有重要信息。 </think> SmarterTools SmarterMail 存在未认证任意文件上传漏洞(CVE-2025-52691),允许攻击者上传文件并可能实现远程代码执行。受影响版本为 Build 9406 及以下,建议升级至 Build 9413 或更高版本以修复问题。该漏洞 CVSS 3.1 评分为 10.0,属于最高危级别。 2026-1-12 21:21:39 Author: horizon3.ai(查看原文) 阅读量:2 收藏
SmarterTools SmarterMail Remote Code Execution via Unauthenticated Arbitrary File Upload | Critical
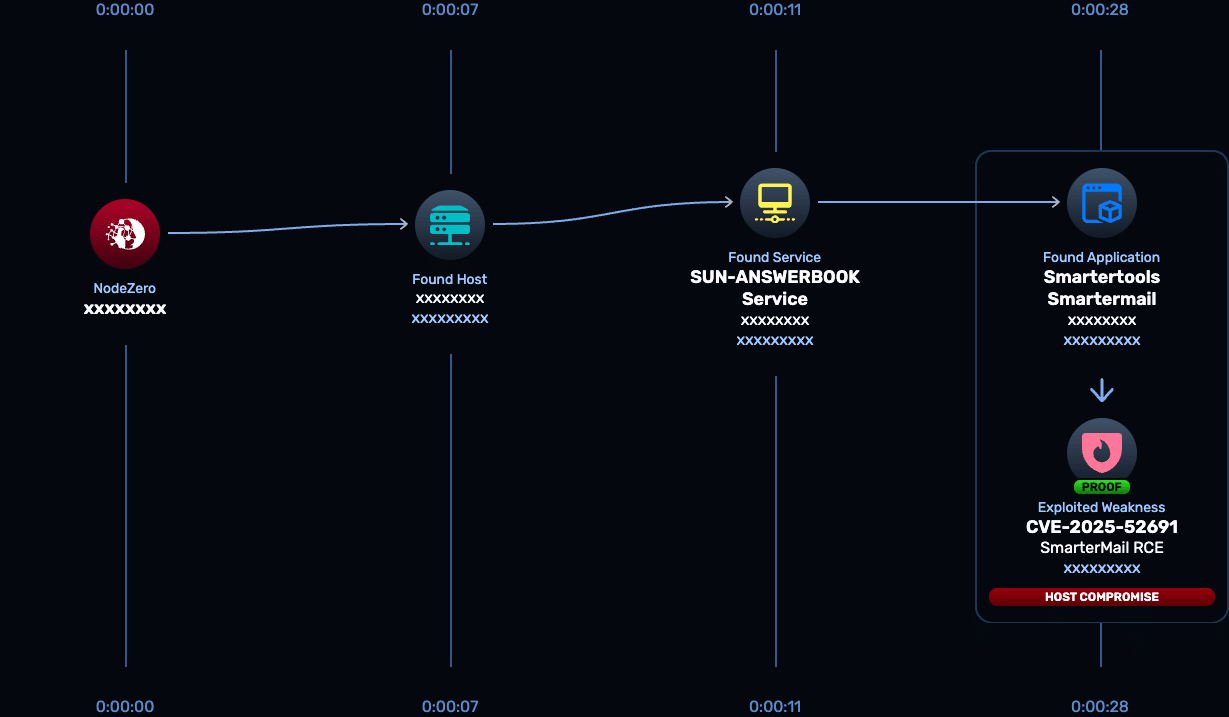
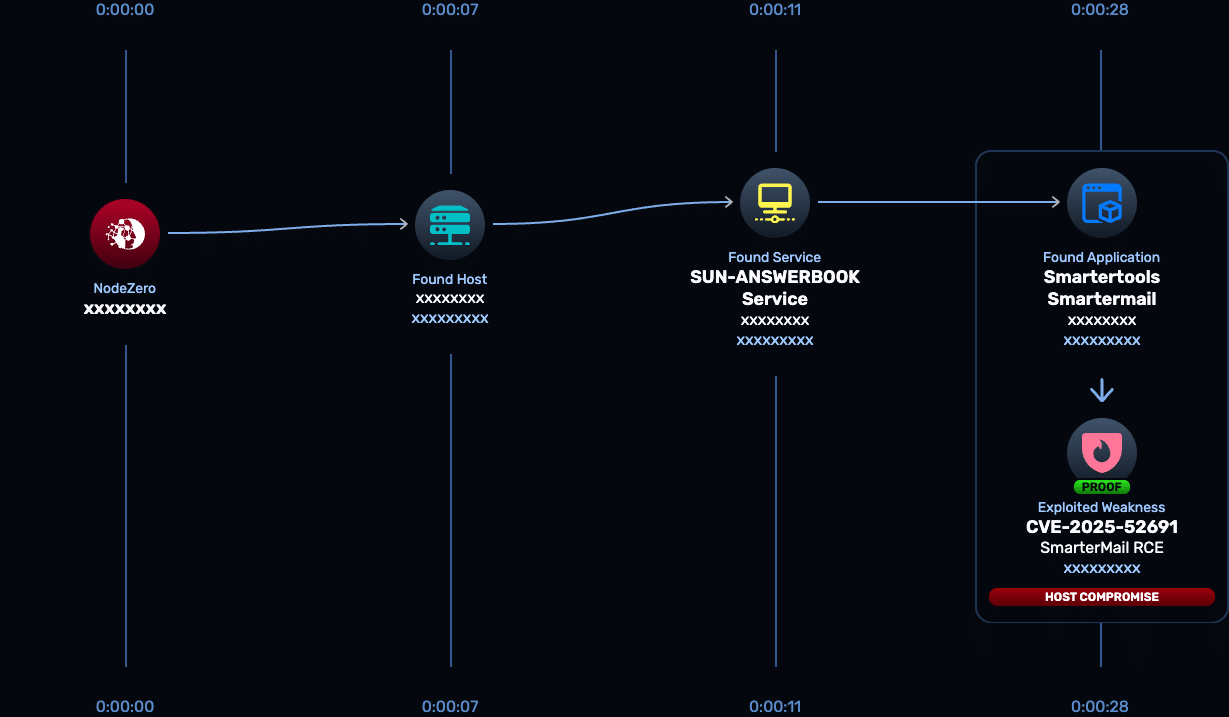
CVE-2025-52691 is a critical vulnerability in SmarterTools SmarterMail that allows an unauthenticated attacker to upload arbitrary files to arbitrary locations on the mail server, potentially enabling remote code execution. While there hasn’t been reports of active exploitation, the ease of exploit, prevalence of internet-exposed instances, and seriousness and likelihood of full compromise upon an attack make finding and addressing risk highly urgent for organizations leveraging this tool.
SmarterMail builds 9406 and earlier are affected, and SmarterTools released a fix in Build 9413; more recent builds will also include the patch.
Stop Guessing, Start Proving
Technical Details
- The root issue is an unauthenticated arbitrary file upload that allows attackers to write files outside intended upload paths.
- If an attacker can place a server-interpreted file in an executable context, this can result in remote code execution with the privileges of the SmarterMail service.
- Severity is maximum: CVSS 3.1 score 10.0.
NodeZero® Offensive Security Platform — Rapid Response
The SmarterTools SmarterMail Rapid Response test (CVE-2025-52691) released Jan. 12, 2026 enables customers to safely verify whether SmarterMail instances are exploitable to this unauthenticated file upload flaw (and therefore susceptible to full compromise) and to confirm remediation.
- Run the Rapid Response test – run the SmarterTools SmarterMail – CVE-2025-52691 Rapid Response test from the customer portal to identify vulnerable, reachable SmarterMail instances.
- Patch immediately – upgrade SmarterMail to Build 9413 or later. If you can, upgrade to the latest available build per vendor guidance.
- Re-run the Rapid Response test – after upgrading, re-run the Rapid Response test to confirm the vulnerability is no longer exploitable.
If the Rapid Response test confirms exploitability, treat the host as potentially compromised, preserve relevant logs, isolate the system, and engage incident response.
Indicators of Compromise (IOCs) — hunting guidance
| Indicator | Type | Description / detection tips |
| Unusual HTTP(S) requests to SmarterMail web interface | Network / Web | Look for spikes in requests, suspicious multipart/form-data uploads, or anomalous user agents from unknown sources near the time of suspected activity. |
| Unexpected file creation under SmarterMail install paths or web-accessible directories | Host / File | Alert on new or modified files in directories served by the SmarterMail web app and on unexpected writes by the SmarterMail service account. |
| Web process spawning unusual child processes | Host / Behavior | Watch for unexpected child processes from the SmarterMail web worker / service processes (for example shells, scripting engines, or binary execution). |
| New scheduled tasks, services, or persistence artifacts shortly after suspicious web activity | Host / Persistence | Correlate persistence creation with prior anomalous web requests and file write events. |
| Anomalous outbound connections from the mail server | Network | Look for new egress destinations, beaconing patterns, or outbound data transfers following suspicious web activity. |
Affected Versions & Patch
- CVE-2025-52691: SmarterMail Build 9406 and earlier are affected.
- Patch: upgrade to SmarterMail Build 9413 or later. CSA explicitly advises updating to Build 9413.
Recommended actions (summary)
- Inventory & scope – identify all SmarterMail instances, especially internet-exposed deployments.
- Run validation – use the Rapid Response test to confirm whether each instance is exploitable.
- Patch – upgrade to Build 9413 or later, then verify the deployed build across all nodes.
- Reduce exposure until patched – restrict administrative and web access to trusted networks, and consider temporarily limiting external reachability where feasible.
- Hunt for compromise – review web logs, file creation events, process telemetry, and outbound connections around the patch window; patching does not remediate historical compromise.
References
🔗 Censys advisory (Dec 30, 2025)
🔗 CSA Alert AL-2025-124 (Vulnerability in SmarterTools Software)
🔗 The Hacker News coverage (Dec 30, 2025)
🔗 CCB Belgium advisory (Dec 29, 2025)
Read about other CVEs
NodeZero® Platform
Implement a continuous find, fix, and verify loop with NodeZero
The NodeZero® platform empowers your organization to reduce your security risks by autonomously finding exploitable weaknesses in your network, giving you detailed guidance around how to priortize and fix them, and having you immediately verify that your fixes are effective.
Recognized By
如有侵权请联系:admin#unsafe.sh
