嗯,用户让我用中文总结一篇文章,控制在一百个字以内,而且不需要特定的开头。看起来这篇文章分为三个部分:英国政府的网络安全计划、中国关联的网络间谍活动,以及n8n平台的漏洞。 首先,我需要抓住每个部分的核心信息。英国政府投入了2.1亿英镑来加强公共部门的网络安全,这是一个主要点。然后是中国的网络威胁扩展到了欧洲,这显示了威胁范围的扩大。最后是n8n平台存在严重漏洞,可能导致远程代码执行,影响很大。 接下来,我要把这些信息浓缩到100字以内。可能需要合并一些内容,比如把三个部分分别简要概括。确保每个部分的关键点都涵盖进去:资金数额、威胁扩展、漏洞严重性。 还要注意用词简洁,避免冗长。比如“投入2.1亿英镑”比详细描述更直接。“网络间谍活动扩展”可以简明扼要地表达。最后提到漏洞可能导致系统被接管。 检查一下字数是否符合要求,确保没有超过限制。可能需要调整句子结构或删减不必要的细节。 最终总结应该涵盖三个主要点:英国的资金投入、中国的威胁扩展、n8n的漏洞问题,并且保持简洁明了。 </think> 英国政府投入2.1亿英镑加强公共部门网络安全;中国关联网络间谍活动扩展至欧洲;开源平台n8n曝出严重漏洞或致系统被接管。 2026-1-9 14:0:33 Author: www.sentinelone.com(查看原文) 阅读量:2 收藏
The Good | U.K. Government Resets Public-Sector Cybersecurity With £210M Action Plan
The United Kingdom has unveiled a sweeping reset of its public-sector cybersecurity strategy, committing more than £210 million ($283 million) to shore up defenses across government departments and essential services. This investment is part of the new Government Cyber Action Plan, which marks a clear departure from years of fragmented oversight and outdated, legacy technology.
The new Government Cyber Action Plan sets a clear path to strengthen cyber security and boost resilience across the public sector.
Read more below⬇️ https://t.co/HCswSOGuhP
— NCSC UK (@NCSC) January 6, 2026
The core of the plan is a centralized Government Cyber Unit, tasked with coordinating risk management, setting mandatory security standards, and leading incident response. Digital Government Minister Ian Murray framed the shift as urgent, warning that cyberattacks can take critical public services offline within minutes. Recent incidents like ransomware-driven NHS disruptions and the compromise of Ministry of Defence payroll systems all show that these risks are recurring realities rather than theoretical threats.
The action plan introduces stricter accountability for senior leaders, enhanced visibility into cyber risks, and more robust, centrally coordinated incident response exercises. Strategic government suppliers will also face tougher contractual cybersecurity requirements as concerns over supply chain vulnerabilities grow.
In tandem with the plan, the government is advancing the Cyber Security and Resilience Bill, which builds on the 2018 Network and Information System (NIS) Regulations. Separately, public bodies and critical infrastructure operators are set to be banned from paying ransomware demands, while telecom providers have pledged to curb phone-number spoofing.
While challenges still remain, this new strategy signals a long-overdue cultural and structural shift. If matched with sustained investment and accountability, it could finally place the U.K. public sector on a more resilient and security-first footing in the face of accelerating cyber threats.
The Bad | China-Linked UAT-7290 Expands Linux-Based Espionage Beyond South Asian Telcos
UAT-7290, a China-linked threat actor, has expanded its cyber espionage operations beyond its focus on South Asian telecommunications firms to include organizations across Southeastern Europe. Active since at least 2022, the group is known for its extensive reconnaissance, network penetration techniques, and heavy reliance on Linux-based malware to compromise public-facing infrastructure.
Cyber researchers assess that UAT-7290 conducts extensive technical profiling of targets before exploiting exposed edge network devices. The actor primarily leverages one-day exploits and targeted SSH brute force attacks, often relying on publicly available proof of concept (PoC) exploit code rather than developing their own. Once initial access is achieved, the group escalates privileges and deploys a modular malware ecosystem tailored for persistence and lateral movement.
UAT-7290’s core tooling centers on Linux implants, beginning with the RushDrop (ChronosRAT) initial dropper, which initiates the infection chain and deploys additional components such as DriveSwitch and the SilentRaid (MystRodX) backdoor. SilentRaid enables long-term access through a plugin-based architecture that supports remote shell access, port forwarding, file operations, and credential-related data collection. While Linux remains the primary focus, the group has occasionally deployed Windows malware – tools commonly shared among China-aligned threat actors.
UAT-7290 is also known for playing a secondary role as an initial access provider. It converts compromised devices into Operational Relay Boxes (ORBs), infrastructure that can later be reused by other Chinese espionage groups, using the Bulbature backdoor.
The tooling and infrastructure overlaps with clusters such as APT10 and Moshen Dragon, reinforcing assessments that UAT-7290 is both an espionage operator and a strategic enabler within the broader Chinese cyber ecosystem.
The Ugly | Researchers Reveal Critical n8n Vulnerabilities Enabling Remote Code Execution
A series of critical vulnerabilities were recently disclosed in the open-source workflow automation platform n8n, allowing unauthenticated attackers to achieve remote code execution (RCE), perform arbitrary commands, and execute untrusted code leading to full compromise.
Beginning with CVE-2025-68668 dubbed ‘N8scape’, this critical flaw (CVSS 9.9) involves a sandbox bypass in the Python Code Node using Pyodide. It works by affecting n8n versions prior to 2.0.0 and allows users with workflow permissions to execute arbitrary OS commands with the same privileges as the n8n service. With version 2.0.0, a task runner-based native Python implementation that improves security isolation was made default thus addressing the issue.
Shortly afterward, n8n disclosed an even more severe issue tracked as CVE-2026-21877, a CVSS 10.0 vulnerability enabling authenticated remote code execution under certain conditions. Affecting both self-hosted and n8n cloud deployments, the flaw could allow untrusted code execution, eventually leading to compromise of the entire instance. Although the critical flaw is patched in version 1.121.3, administrators are advised to apply the updates quickly, especially given a growing pattern of critical RCE-class vulnerabilities in the platform.
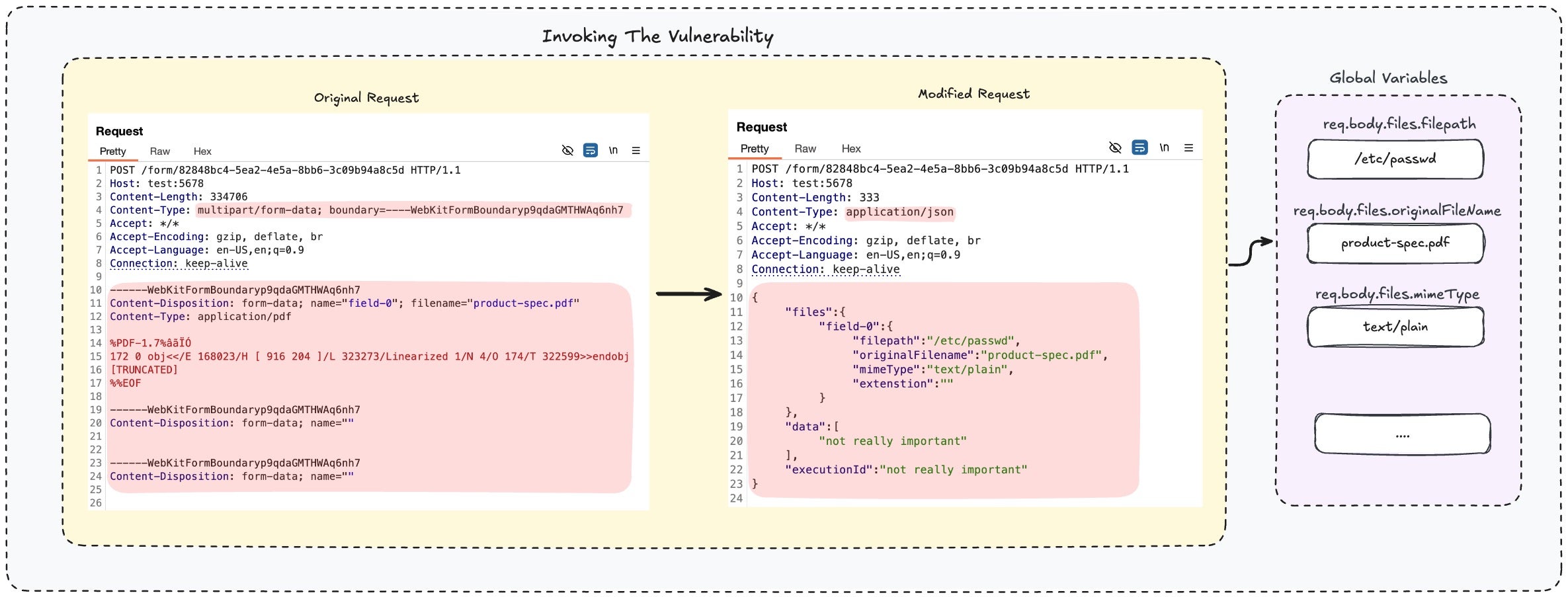
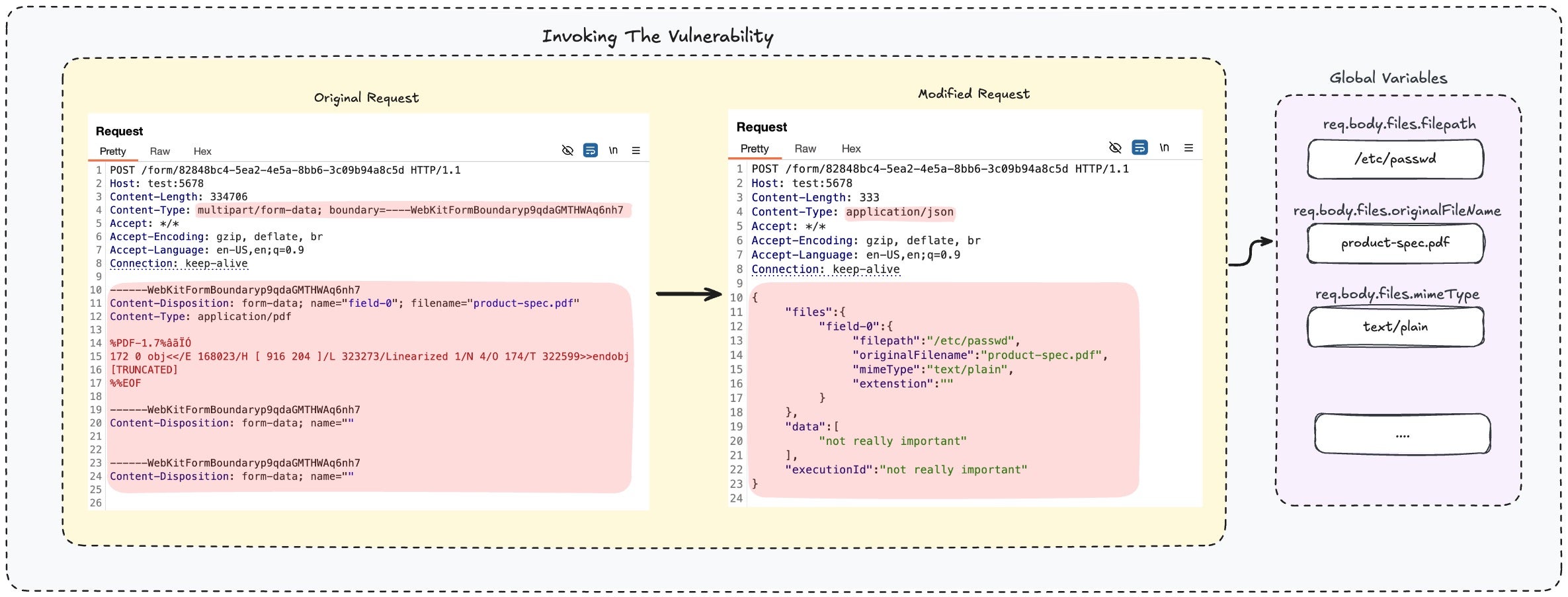
The third and latest disclosure this week, codenamed ‘Ni8mare’ and tracked as CVE-2026-21858 (CVSS 10.0), is a critical flaw that allows complete takeover of affected instances. Exploiting a content-type confusion issue in n8n’s webhook and form handling, attackers can read arbitrary files, extract credentials and encryption keys, forge admin sessions, and ultimately achieve RCE. Researchers noted that a compromised n8n instance becomes a single point of failure due to centralized storage of API keys, OAuth tokens, and infrastructure credentials, making it a veritable data trove for threat actors.
At the time of writing, reports from attack surface management vendors are observing over 26,000 exposed n8n instances online, emphasizing the need for timely patching, controlled exposure, and strict access management.
如有侵权请联系:admin#unsafe.sh
