
嗯,用户让我帮忙总结一篇文章,控制在100字以内,而且不需要用“文章内容总结”这样的开头。我得先仔细阅读文章内容,抓住关键点。 文章讲的是一个叫做“Ni8mare”的漏洞,属于最高级别的安全风险。这个漏洞允许攻击者远程控制N8N平台的实例。N8N是一个工作流自动化工具,用户很多,下载量和使用量都很大。 漏洞的细节方面,攻击者可以通过特定的工作流访问服务器上的文件,导致敏感信息泄露甚至进一步入侵。研究人员发现这个问题,并报告给了N8N团队。漏洞的核心是解析数据时的内容类型混淆问题。 解决方法是升级到1.121.0或更高版本,或者限制公开的webhook和表单端点。 现在我需要把这些信息浓缩到100字以内。要包括漏洞名称、影响、攻击方式、受影响的用户数量、漏洞原因以及解决方案。 可能的结构是:介绍漏洞名称和影响,说明攻击者如何利用它,提到受影响的用户数量,然后简要说明原因和解决办法。 比如:“Ni8mare漏洞(CVE-2026-21858)允许远程攻击者控制N8N实例。该漏洞利用内容类型混淆,使攻击者可读取服务器文件并获取敏感信息。受影响用户超过10万。建议升级至最新版本或限制公开端点。” 这样应该在100字以内,并且涵盖了主要信息。 </think> Ni8mare漏洞(CVE-2026-21858)允许远程攻击者通过特定工作流控制N8N实例,读取服务器文件并获取敏感信息。该漏洞利用内容类型混淆机制,影响超10万用户。建议升级至n8n 1.121.0或更高版本以修复问题。 2026-1-7 17:45:15 Author: www.bleepingcomputer.com(查看原文) 阅读量:4 收藏
A maximum severity vulnerability dubbed "Ni8mare" allows remote, unauthenticated attackers to take control over locally deployed instances of the N8N workflow automation platform.
The security issue is identified as CVE-2026-21858 and has a 10 out of 10 severity score. According to researchers at data security company Cyera, there are more than 100,000 vulnerable n8n servers.
n8n is an open-source workflow automation tool that allows users to connect applications, APIs, and services into complex workflows via a visual editor. It is primarily used to automate tasks and supports integrations with AI and large language model (LLM) services.
It has over 50,000 weekly downloads on npm and more than 100 million pulls on Docker Hub. It is a popular tool in the AI space, where it is used to orchestrate LLM calls, build AI agents and RAG pipelines, and automate data ingestion and retrieval.
Ni8mare details
The Ni8mare vulnerability gives an attacker access to files on the underlying server by executing certain form-based workflows.
"A vulnerable workflow could grant access to an unauthenticated remote attacker. This could result in exposure of sensitive information stored on the system and may enable further compromise depending on deployment configuration and workflow usage," n8n developers say.
Cyera researchers discovered the Ni8mare vulnerability (CVE-2026-21858) and reported it to n8n on November 9, 2025. They say that the security issue is a content-type confusion in the way n8n parses data.
n8n uses two functions to process incoming data based on the 'content-type' header configured in a webhook, the component that triggers events in a workflow by listening for specific messages.
When the webhook request is marked as multipart/form-data, n8n treats it as a file upload and uses a special upload parser that saves files in randomly generated temporary locations.
"This means users can’t control where files end up, which protects against path traversal attacks."
However, for all other content types, n8n uses its standard parser instead.
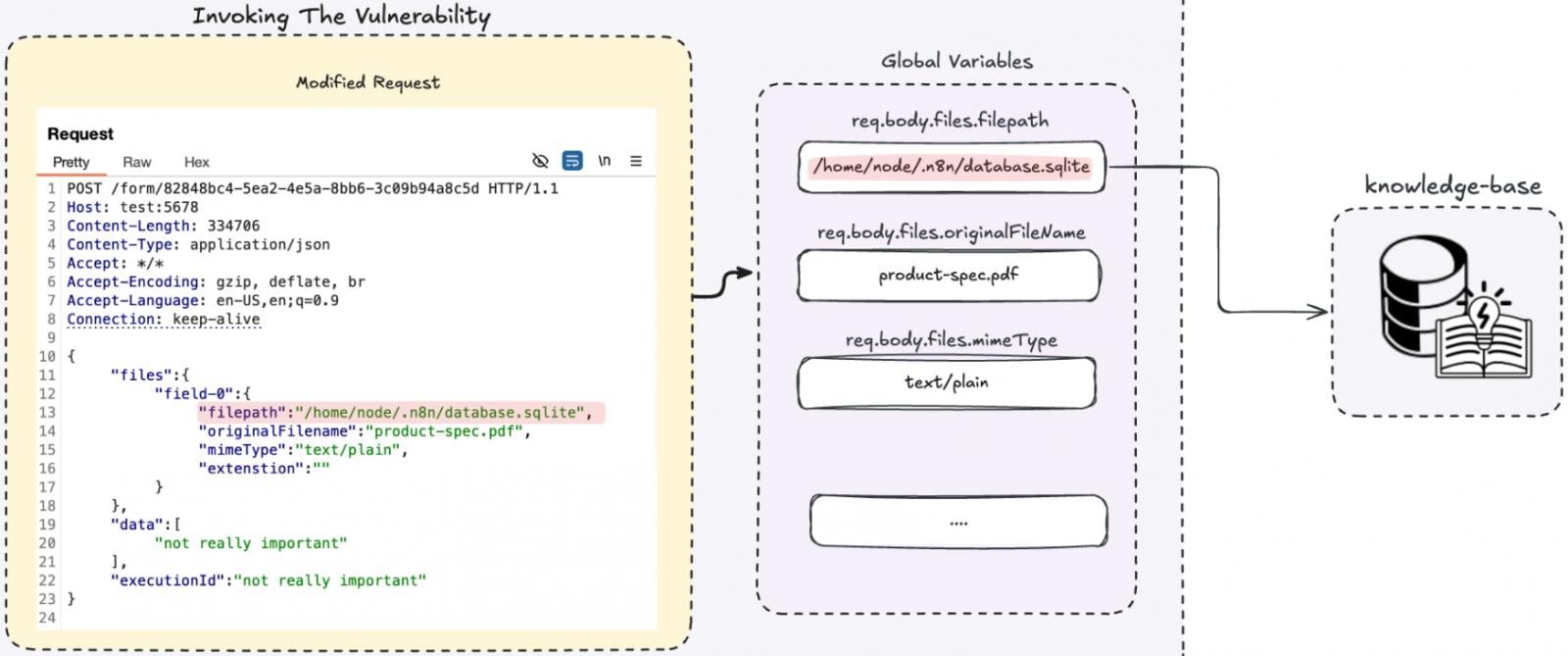
Cyera found that by setting a different content type, such as application/json, an attacker can bypass the upload parser.
In this situation, n8n still processes file-related fields but does so without verifying that the request actually contains a valid file upload. This allows the attacker to fully control the file metadata, including the file path.
.jpg)
Source: Cyera
"Since this function is called without verifying the content type is multipart/form-data, we control the entire req.body.files object. That means we control the filepath parameter – so instead of copying an uploaded file, we can copy any local file from the system," explains Cyera.
This allows reading arbitrary files from an n8n instance, which can expose secrets by adding internal files into the workflow's knowledge base.
Cyera says this can be abused to expose secrets stored on the instance, inject sensitive files into workflows, forge session cookies to bypass authentication, or even execute arbitrary commands.
Source: Cyera
Cyera emphasizes that n8n often stores API keys, OAuth tokens, database credentials, cloud storage access, CI/CD secrets, and business data, making it a central automation hub.
n8n developers say that there is no official workaround available for Ni8mare, but one mitigation is to restrict or disable publicly accessible webhook and form endpoints.
The recommended action is to update to n8n version 1.121.0 or a more recent one.
Secrets Security Cheat Sheet: From Sprawl to Control
Whether you're cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.
如有侵权请联系:admin#unsafe.sh

