嗯,用户让我用中文帮他总结一下这篇文章的内容,控制在一百个字以内,而且不需要用“文章内容总结”或者“这篇文章”这样的开头,直接写描述。好的,我先看看文章讲的是什么。 文章主要讲的是网络攻击者利用配置错误的电子邮件路由和伪造保护措施,发送看似来自内部的钓鱼邮件。他们使用PhaaS平台,比如Tycoon2FA,来窃取凭证。微软报告提到这种情况自2025年5月以来有所增加,影响多个行业。 我需要把重点提炼出来:攻击者如何利用配置错误、使用哪些平台、带来的威胁以及微软的建议。还要注意字数限制在100字以内。 可能的结构是:攻击者利用配置错误的邮件路由和伪造保护发送看似内部的钓鱼邮件,使用PhaaS平台窃取凭证。微软指出正确配置MX记录和加强DMARC/SPF策略可以防范此类攻击。 这样应该能涵盖主要信息,并且符合用户的格式要求。 </think> 网络攻击者利用配置错误的电子邮件路由和伪造保护措施,发送看似来自组织内部的钓鱼邮件,使用PhaaS平台如Tycoon2FA窃取凭证。微软指出,正确配置MX记录和加强DMARC/SPF策略可防范此类攻击。 2026-1-7 14:57:52 Author: securityaffairs.com(查看原文) 阅读量:1 收藏
Misconfigured email routing enables internal-spoofed phishing

Attackers exploit misconfigured email routing to spoof internal emails, using PhaaS platforms like Tycoon2FA to steal credentials.
Attackers exploit misconfigured email routing and spoof protections to send phishing emails appearing internal, using PhaaS platforms like Tycoon2FA to steal credentials.
“Phishing actors are exploiting complex routing scenarios and misconfigured spoof protections to effectively spoof organizations’ domains and deliver phishing emails that appear, superficially, to have been sent internally. Threat actors have leveraged this vector to deliver a wide variety of phishing messages related to various phishing-as-a-service (PhaaS) platforms such as Tycoon2FA.” reads the report published by Microsoft. “These include messages with lures themed around voicemails, shared documents, communications from human resources (HR) departments, password resets or expirations, and others, leading to credential phishing.”
Since May 2025, phishing attacks exploiting misconfigured email routing and spoof protections have increased. Microsoft reported opportunistic campaigns targeting multiple industries, sometimes for financial scams. Messages appear internal, boosting success. Office 365 tenants with correct MX records are protected, but others risk credential theft, BEC, or fund loss. Microsoft advises proper spoof protection and connector configuration to block these attacks.
Phishing attacks exploiting misconfigured email routing and spoof protections allow threat actors to send emails appearing from an organization’s own domain. Tenants with complex routing and MX records not pointed to Office 365, or lacking strict DMARC/SPF policies, are vulnerable.
“Setting strict Domain-based Message Authentication, Reporting, and Conformance (DMARC) reject and SPF hard fail (rather than soft fail) policies and properly configuring any third-party connectors will prevent phishing attacks spoofing organizations’ domains.” continues the report.
Attackers often use PhaaS platforms like Tycoon2FA, enabling credential theft, AiTM bypass of MFA, and financial scams. Office 365 tenants with properly configured MX records are protected.
Attackers exploit complex email routing and weak spoofing protections to send phishing emails that look like internal messages. These emails often use common themes such as HR notices, password resets, voicemails, or shared documents. A typical trick is using the same email address in both the “To” and “From” fields to appear legitimate.

Although the emails look internal, email headers show they come from external servers. Signs include SPF or DMARC failures, missing DKIM signatures, and headers indicating anonymous external delivery. In poorly configured environments, these failures may not block delivery, especially when third-party mail connectors are misconfigured.
Many campaigns redirect users through legitimate-looking links, such as Google Maps URLs, to attacker-controlled sites. Victims are shown fake CAPTCHA pages that lead to Tycoon2FA phishing pages designed to steal credentials, sometimes bypassing MFA. Proper DMARC, SPF hard fail, DKIM, and correct connector setup can prevent these attacks.
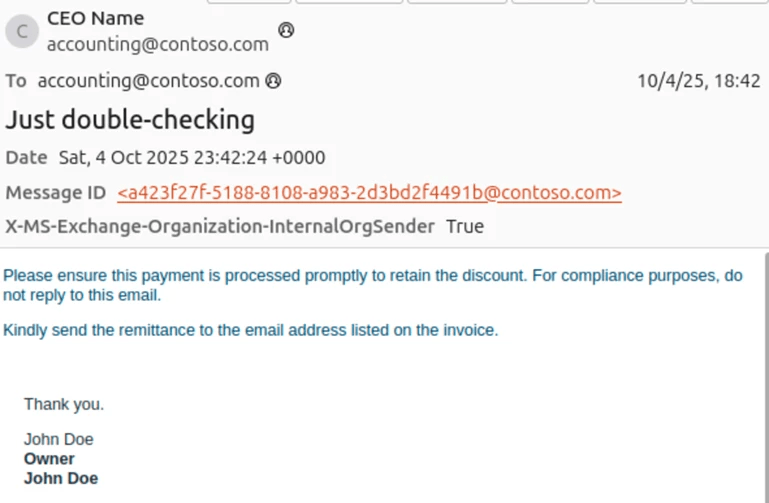
Microsoft Threat Intelligence has also observed financial scams delivered through spoofed emails that appear to come from inside an organization. These messages are designed to look like ongoing email threads involving senior staff, often impersonating the CEO, the accounting department, or a supplier requesting payment.

In the observed cases, weak email authentication settings allowed the scams to succeed. DMARC was set to “none,” meaning authentication failures were not enforced. As a result, spoofed emails sent from external IP addresses were delivered to inboxes, especially in environments where MX records do not point to Office 365.
The scam emails often use urgency to pressure victims, such as requesting quick payment to secure a discount. They typically use the same email address in both the “To” and “From” fields, with the CEO’s name shown as the display name to appear legitimate.
Attachments commonly include a fake invoice requesting payment to a fraudulent bank account, an IRS W-9 form using stolen personal data, and a fake bank letter to add credibility. Victims who pay may suffer significant and unrecoverable financial losses, as funds are quickly moved by attackers.
Organizations should enforce strict DMARC reject and SPF hard-fail policies and properly configure third-party mail connectors. Microsoft pointed out that tenants with MX records pointing directly to Office 365 are protected.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, phishing)
如有侵权请联系:admin#unsafe.sh