
好的,我现在需要帮用户总结一篇文章,控制在100字以内。用户的要求是直接写文章描述,不需要特定的开头。首先,我得通读整篇文章,抓住主要内容。 文章讲的是一个威胁行为者Zestix通过入侵企业使用的ShareFile、Nextcloud和OwnCloud平台,窃取了大量公司数据,并在地下论坛上出售。他利用恶意软件收集员工的凭证,这些恶意软件通常通过网络钓鱼或广告传播。此外,由于缺乏多因素认证,攻击者更容易进入这些云服务。Hudson Rock指出,很多公司的凭证在犯罪数据库中存在多年,说明他们没有及时更换密码或处理活跃会话。 总结的时候要包括Zestix的行为、使用的工具、影响的行业以及问题根源。还要注意字数限制,确保信息准确且简洁。 </think> 威胁行为者Zestix通过入侵企业使用的ShareFile、Nextcloud和OwnCloud平台窃取数据,并在地下论坛上出售。他利用恶意软件收集员工凭证,并利用多因素认证缺失获取非法访问。涉及行业包括航空、国防、医疗等。问题源于企业安全措施不足和凭证管理不善。 2026-1-5 23:0:20 Author: www.bleepingcomputer.com(查看原文) 阅读量:3 收藏

A threat actor known as Zestix has been offering to sell corporate data stolen from dozens of companies likely after breaching their ShareFile, Nextcloud, and OwnCloud instances.
According to cybercrime intelligence company Hudson Rock, initial access may have been obtained through credentials collected by info-stealing malware such as RedLine, Lumma, and Vidar deployed on employee devices.
The three infostealers are usually distributed through malvertising campaigns or ClickFix attacks. This type of malware commonly targets data stored by web browsers (credentials, credit cards, personal info), messaging apps, and cryptocurrency wallets.
A threat actor with valid credentials can gain unauthorized access to a service, such as a file-sharing platforms, when multi-factor authentication (MFA) protection is missing.
In a report today, Hudson Rock notes that some of the analyzed stolen credentials have been present in criminal databases for years, indicating failure to rotate them or to invalidate active sessions even after extended periods.
Multiple breaches advertised
Hudson Rock says that Zestix operates as an initial access broker (IAB) on underground forums, selling access to high-value corporate cloud platforms.
The cybersecurity company suggest that attackers breached ShareFile, Nextcloud, and ownCloud environments used by organizations across multiple sectors, including aviation, defense, healthcare, utilities, mass transit, telecommunications, legal, real estate, and government.
Source: Hudson Rock
After parsing infostealer logs "specifically looking for corporate cloud URLs (ShareFile, Nextcloud)," the threat actor logs into the file-sharing services using a valid username and password where MFA is not active.
Hudson Rock says it pinpointed the likely breach points by correlating infostealer data from its platform with publicly available images, metadata, and open-source information.
In at least 15 of the analyzed cases, the cybersecurity company found that employee credentials for the cloud file-sharing services had been collected by infostealers.
It is important to note that this verification is unilateral, and there’s no public confirmation of a security breach from the listed companies. One exception could be Iberia, although its recent disclosure isn't necessarily linked to Hudson Rock's findings.
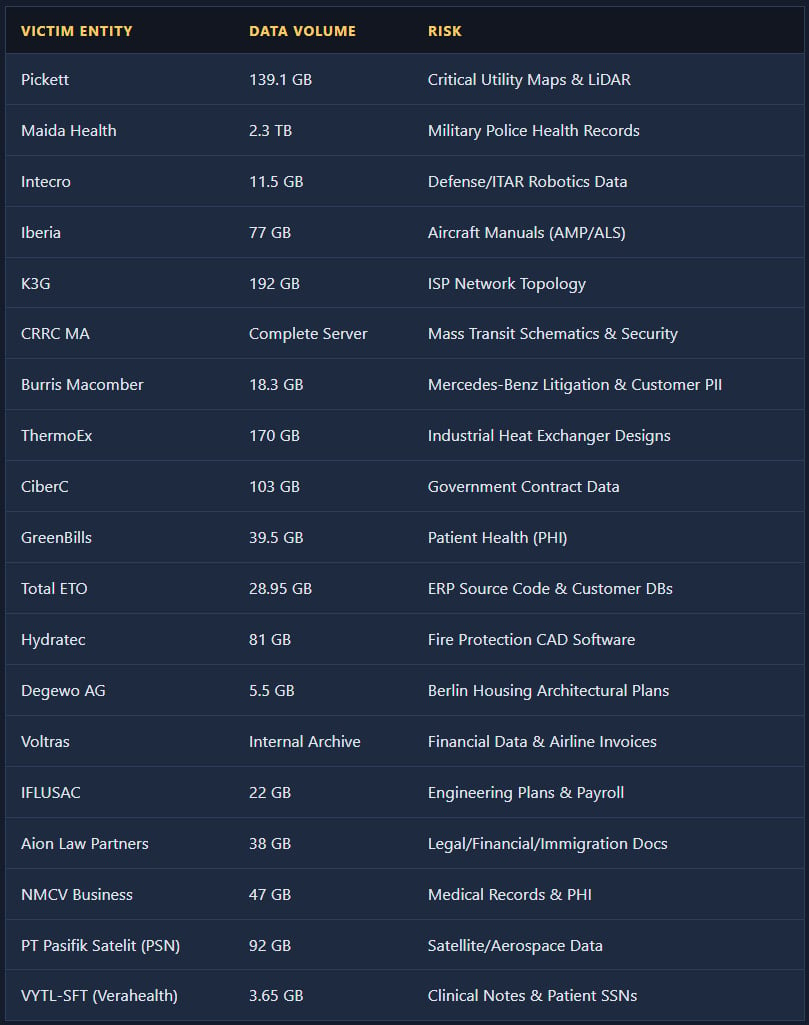
Zestix offered to sell stolen data volumes that range from tens of gigabytes to several terabytes, claiming to include aircraft maintenance manuals and fleet data, defense and engineering files, customer databases, health records, mass-transit schematics, utility LiDAR maps, ISP network configs, satellite project data, ERP source code, government contracts, and legal documents.
Many of the allegedly stolen files could expose organizations to security, privacy, and industrial espionage risks, while exposed government contracts may raise national security concerns.
Source: Hudson Rock
Hudson Rock has found an additional set of 30 victims that Zestix sells under the alias “Sentap,” but the researchers did not validate it in the same way.
The researchers report that, in addition to the listed victims, their threat intelligence data indicates that cloud exposure is a broader, systemic problem stemming from organizations’ failure to follow good security practices.
They report having identified thousands of infected computers, including some at Deloitte, KPMG, Samsung, Honeywell, and Walmart.
Hudson Rock told BleepingComputer that it has notified ShareFile and will also alert Nextcloud and OwnCloud about the verified exposures so they can take the appropriate action.
The 2026 CISO Budget Benchmark
It's budget season! Over 300 CISOs and security leaders have shared how they're planning, spending, and prioritizing for the year ahead. This report compiles their insights, allowing readers to benchmark strategies, identify emerging trends, and compare their priorities as they head into 2026.
Learn how top leaders are turning investment into measurable impact.
如有侵权请联系:admin#unsafe.sh

