好的,用户让我总结一篇关于VVS Stealer的文章,控制在100字以内,不需要特定的开头。首先,我需要通读文章,抓住关键点。 文章提到VVS Stealer是一种基于Python的恶意软件,用于窃取Discord的凭证和令牌。它从2025年4月起在Telegram上销售。使用Pyarmor混淆代码,研究人员去混淆后分析了其功能。 主要功能包括窃取Discord数据、劫持会话、提取浏览器凭证和截图。它通过启动项安装维持持久性,并使用假错误信息隐藏自己。数据被压缩成ZIP并通过HTTP POST发送到预定义的 webhook。 此外,它还针对Chromium和Firefox浏览器提取密码等信息,并注入JavaScript劫持Discord会话。研究人员分析了Pyarmor的加密机制,成功去混淆代码。 总结时需要涵盖恶意软件的功能、传播方式、技术手段以及影响。控制在100字以内,所以要简洁明了。 </think> VVS Stealer是一种基于Python的恶意软件,用于窃取Discord凭证和令牌,并通过Telegram销售。它利用Pyarmor混淆代码以隐藏功能,并可窃取浏览器凭证、截图及维持会话劫持。数据通过HTTP POST发送至预定义 webhook,研究人员成功去混淆并分析其行为。 2026-1-5 08:45:43 Author: securityaffairs.com(查看原文) 阅读量:5 收藏
VVS Stealer, a new python malware steals Discord credentials

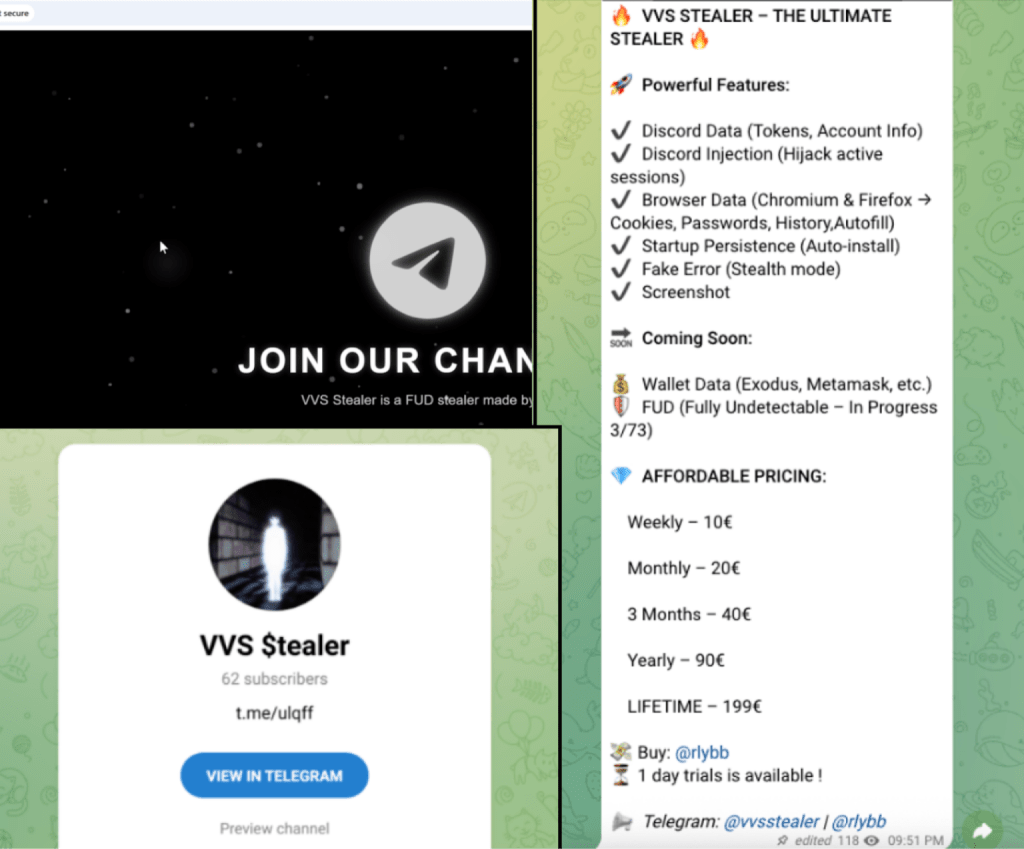
VVS Stealer is a Python-based malware that steals Discord credentials and tokens and has been sold on Telegram since at least April 2025.
Palo Alto Networks researchers uncovered VVS Stealer, a Python-based malware that steals Discord credentials and tokens and has been sold on Telegram since at least April 2025.
VVS Stealer uses the source code obfuscator Pyarmor to heavily obfuscate its Python code, hindering analysis and detection. Researchers deobfuscated samples to analyze the malicious code.
Marketed on Telegram as the “ultimate stealer,” the malware is sold via subscriptions or licenses, starting at €10 per week up to €199 for lifetime access.
VVS Stealer can steal Discord data, hijack sessions, extract browser credentials, and capture screenshots. It maintains persistence via startup installation, while operating stealthily using fake error messages.
“Once these data are extracted, the malware sample prepares it for exfiltration by compressing it into a single ZIP archive file named <USERNAME>_vault.zip. It then exfiltrates this file via HTTP POST requests to the predefined webhook endpoints, similar to the Discord data exfiltration process.” reads the report published by Palo Alto Networks.
Researchers analyzed a VVS Stealer sample packaged with PyInstaller and obfuscated using Pyarmor. They extracted and restored raw Python bytecode, identified Python 3.11.5 and Pyarmor details, and reconstructed the .pyc header to successfully decompile the malware and recover its source code.
Researchers analyzed Pyarmor headers, AES-128-CTR encryption, and BCC mode, which compiles Python functions into C code stored in ELF files. By reconstructing encrypted bytecode, constants, and strings using keys and nonces tied to the Pyarmor license, they recovered core functions such as browser key extraction. Disarming these layers enabled full analysis of the malware’s capabilities.
After removing Pyarmor obfuscation, researchers revealed VVS Stealer as a sophisticated malware focused on data theft and session hijacking. The malware is time-limited, expiring after October 31, 2026, and uses a fixed Chrome User-Agent for all HTTP traffic. It targets Discord by locating and decrypting encrypted tokens, then queries Discord APIs to collect extensive user data, including account details, billing info, MFA status, IP address, and system metadata.
“The malware sample first searches for potential encrypted Discord tokens. Encrypted Discord tokens are strings beginning with the prefix dQw4w9WgXcQ:. The malware sample uses regular expressions to form a pattern from this string prefix. It then uses this pattern to search inside the contents of files with the .ldb or .log file extensions, stored within the LevelDB directory.” continues the report. “After gathering all this information, the malware sample proceeds to exfiltrate it in JavaScript Object Notation (JSON) format. The exfiltration takes place via HTTP POST requests to the predefined webhook endpoints (%WEBHOOK% environment variable and hard-coded fall back URLs).
Webhooks are “a low-effort way to post messages to channels in Discord. They do not require a bot user or authentication to use.” (Source: Discord Developer Portal.)”
The collected data are exfiltrated via Discord webhooks. The malware also injects obfuscated JavaScript into the Discord client to hijack active sessions, monitor user actions, and maintain persistence. Additionally, VVS Stealer targets numerous Chromium- and Firefox-based browsers, extracting passwords, cookies, browsing history, and autofill data, packaging them into ZIP archives for exfiltration through the same webhook channels.
The malware shows a fake fatal error message using the Windows MessageBoxW API to trick users into thinking a system restart is required.
“VVS stealer demonstrates how tools like Pyarmor, which can be used for legitimate purposes, can also be leveraged to build stealthy malware aimed at hijacking credentials for popular platforms such as Discord. Its emergence signals a need for defenders to strengthen monitoring around credential theft and account abuse.” concludes the report.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, VVS Stealer)
如有侵权请联系:admin#unsafe.sh
