
嗯,用户让我总结这篇文章的内容,控制在100字以内,而且不需要用“文章内容总结”之类的开头。首先,我需要快速浏览文章,抓住主要信息。 文章讲的是WebRAT恶意软件通过GitHub仓库传播,这些仓库声称提供漏洞的POC利用。之前WebRAT是通过盗版软件和游戏外挂传播的,现在转向GitHub。它能窃取Steam、Discord等账号信息,还能监控摄像头和截图。Kaspersky发现15个这样的仓库,内容结构像是AI生成的。恶意软件通过密码保护的ZIP文件分发,包含各种文件和主加载器。虽然这个方法不算新,但提醒开发者要注意来源。 接下来,我需要把这些要点浓缩到100字以内。确保涵盖传播方式、功能、发现情况以及安全建议。避免使用复杂的术语,保持简洁明了。 最后检查字数是否符合要求,并确保没有使用禁止的开头语句。 </think> WebRAT恶意软件通过伪装成漏洞利用的GitHub仓库传播,窃取用户凭证并监控设备。研究人员发现15个相关恶意仓库,内容疑似AI生成。该恶意软件以密码保护的ZIP文件分发,并通过批处理文件和加载器执行。此方法虽非首创,但提醒开发者需谨慎对待第三方代码来源。 2025-12-23 19:45:29 Author: www.bleepingcomputer.com(查看原文) 阅读量:7 收藏

The WebRAT malware is now being distributed through GitHub repositories that claim to host proof-of-concept exploits for recently disclosed vulnerabilities.
Previously spread through pirated software and cheats for games like Roblox, Counter Strike, and Rust, WebRAT is a backdoor with info-stealing capabilities that emerged at the beginning of the year.
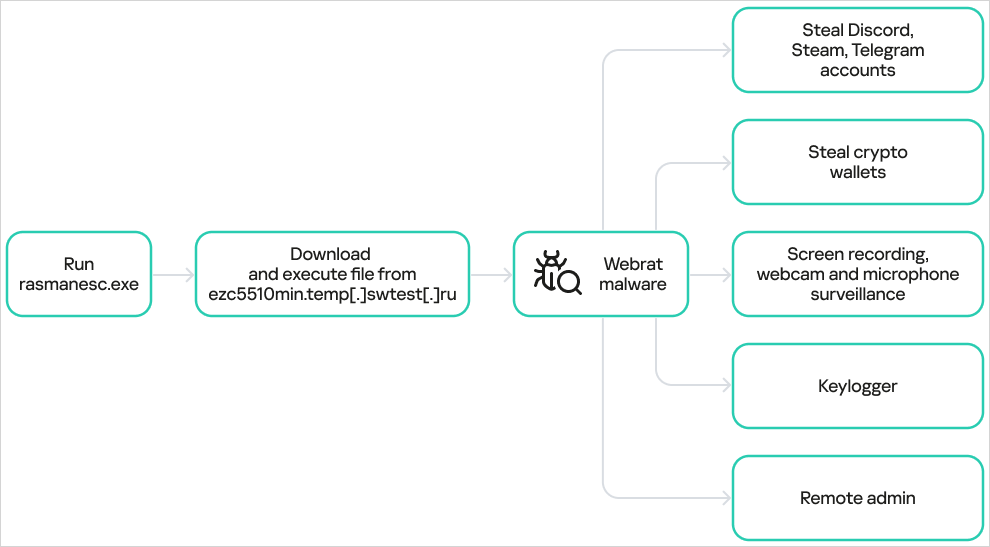
According to a report from Solar 4RAYS in May, WebRAT can steal credentials for Steam, Discord, and Telegram accounts, as well as cryptocurrency wallet data. It can also spy on victims through webcams and capture screenshots.
Since at least September, the operators started to deliver the malware through carefully crafted repositories claiming to provide an exploit for several vulnerabilities that had been covered in media reports. Among them were:
- CVE-2025-59295 – A heap-based buffer overflow in the Windows MSHTML/Internet Explorer component, enabling arbitrary code execution via specially crafted data sent over the network.
- CVE-2025-10294 – A critical authentication bypass in the OwnID Passwordless Login plugin for WordPress. Due to improper validation of a shared secret, unauthenticated attackers could log in as arbitrary users, including administrators, without credentials.
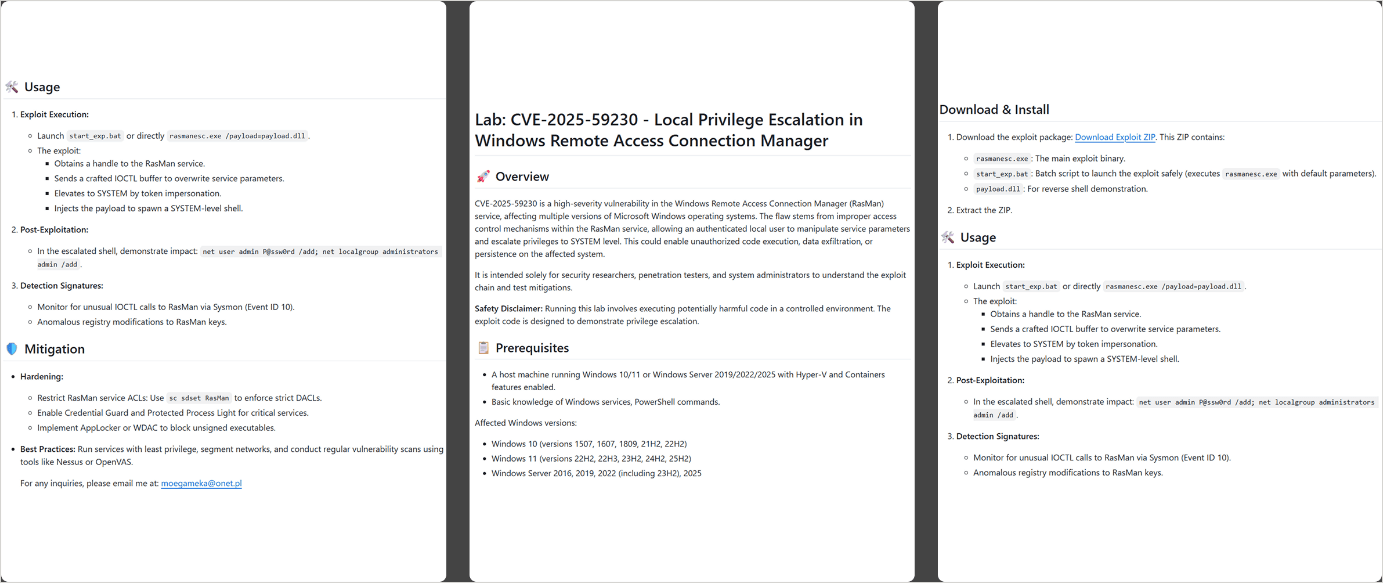
- CVE-2025-59230 – An elevation-of-privilege (EoP) vulnerability in Windows’ Remote Access Connection Manager (RasMan) service. A locally authenticated attacker could exploit improper access control to escalate their privileges to SYSTEM level on affected Windows installations.
Security researchers at Kaspersky discovered 15 repositories distributing WebRAT, all of them providing information about the issue, what the alleged exploit does, and the available mitigations.
Due to the way the information is structured, Kaspersky believes that the text was generated using an artificial intelligence model.
Source: Kaspersky
The malware has multiple methods to establish persistence, including Windows Registry modifications, the Task Scheduler, and injecting itself into random system directories.
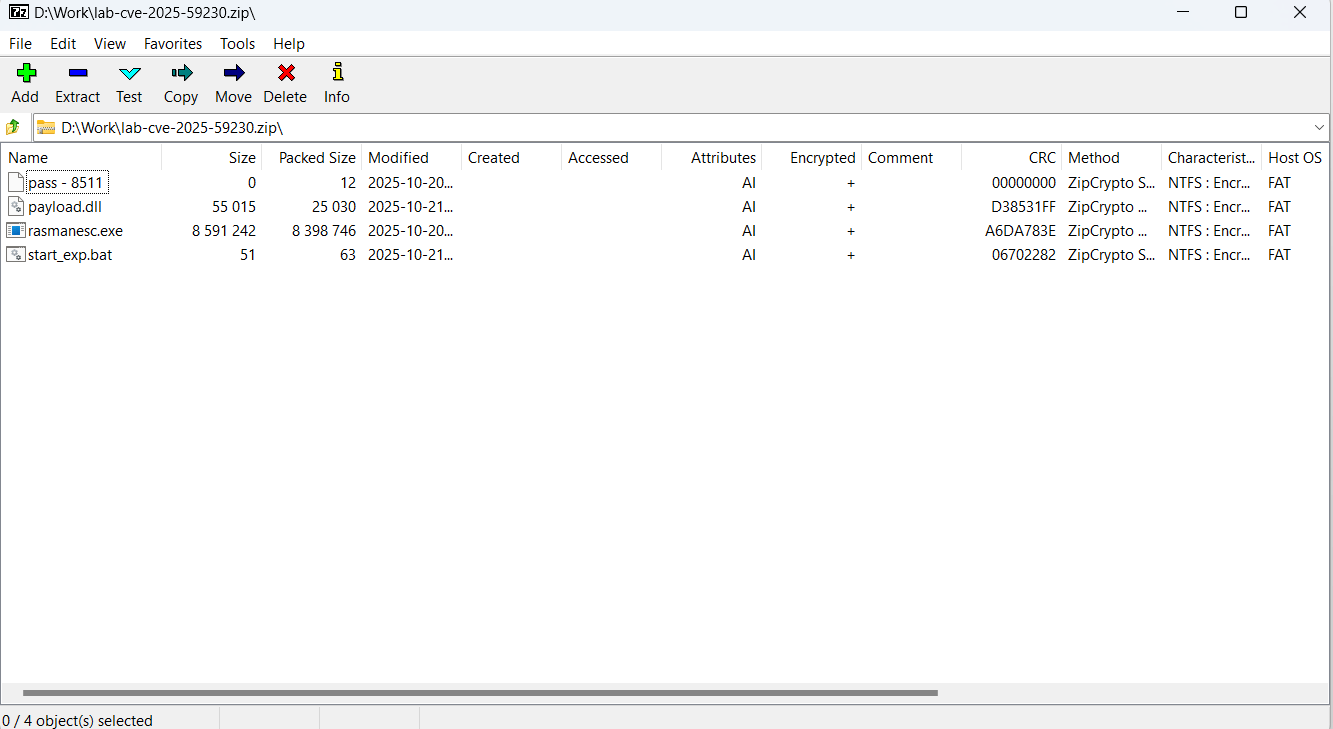
Kaspersky researchers say that the fake exploits are delivered in the form of a password-protected ZIP file containing an empty file with the password as its name, a corrupted decoy DLL file acting as a decoy, a batch file used in the execution chain, and the main dropper named rasmanesc.exe.
Source: Kaspersky
According to the analysts, the dropper elevates privileges, disables Windows Defender, and then downloads and executes WebRAT from a hardcoded URL.
Kaspersky notes that the WebRAT variant used in this campaign is no different from previously documented samples and lists the same capabilities described in past reports.
Source: Kaspersky
Using fake exploits on GitHub to lure unsuspecting users into installing malware is not a new tactic, as it has been extensively documented in the past [1, 2, 3, 4]. More recently, threat actors promoted a fake “LDAPNightmare” exploit on GitHub to spread infostealing malware.
All malicious GitHub repositories related to the WebRAT campaign that Kaspersky uncovered have been removed. However, developers and infosec enthusiasts should be careful about the sources they use, as threat actors can submit new lures under different publisher names.
The general rule when testing exploits or code that comes from a potentially untrusted source is to run them in a controlled, isolated environment.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.
如有侵权请联系:admin#unsafe.sh

