
LockBit、Qilin和DragonForce宣布结盟后,分析显示LockBit自2025年6月起几乎无活动,Qilin活动增加但未显著改变趋势。勒索软件生态系统呈现碎片化,赎金支付下降,数据泄露勒索模式兴起。 2025-12-18 17:31:24 Author: labs.yarix.com(查看原文) 阅读量:5 收藏
Reading Time: 15 minutes
Disclaimer: On December 5, 2025, LockBit resurfaced with a newly branded Data Leak Site named after the latest version of its encryption tool. Although this report relies on data collected between January 1 and November 30, 2025, the CTI Team reviewed all posts published on the new LockBit DLS up to December 11, 2025.
Findings indicate that approximately 55% of the victims listed after the relaunch were previously disclosed on older LockBit DLS versions, suggesting that, at this stage, the group’s return does not materially affect the trends, assessments, or conclusions presented in this analysis.
Key Takeaways
Based on the data analyzed in this report, the following observations are drawn in relation to the alliance announcement published on September 15, 2025:
- Ransomware claim distribution observed after the alliance post indicates a continued fragmentation of the ransomware ecosystem, with activity spread across a growing number of groups rather than consolidation around a single dominant actor.
- The increase in Qilin’s activity recorded in the weeks following the alliance announcement aligns temporally with increased underground visibility generated by the post.
- In the broader context highlighted by the alliance post, sustained pressure on traditional Ransomware as a Service groups and declining ransom payments might favor data only extortion models as a lower risk and more resilient approach.
- Time based analysis of Data Leak Site activity does not show evidence of an operational recovery for LockBit following the alliance announcement, despite renewed branding efforts and the public release of a new malware version.
On the occasion of the announcement made by the ransomware group DragonForce regarding the creation of an alliance between DragonForce, Qilin, and LockBit, identified on September 15, 2025, the Cyber Intelligence Team conducted an analysis based on internally collected data to assess the potential risk and the credibility of the claim. This activity was carried out as part of ongoing ransomware claims monitoring operations aimed at identifying emerging risks and issuing customer alerts.
The analysis leveraged ransomware claim data attributed to criminal gangs observed throughout 2025, with the objective of identifying trends that could indicate a potential shift in strategy among the groups involved in the alleged alliance, also considering the broader context of heightened pressure and possible fragmentation of the ransomware landscape during 2025.
Subsequently, a possible interpretative framework is provided, examining the situation preceding the publication of the thread and building upon previous analyses conducted on the LockBit collective, particularly in relation to the incident involving the dump of its management panel.
The post published on September 15, identified on a Russian underground forum and posted by the user “dragonforce”, announced the creation of the Qilin/LockBit/DragonForce ransomware cartel.
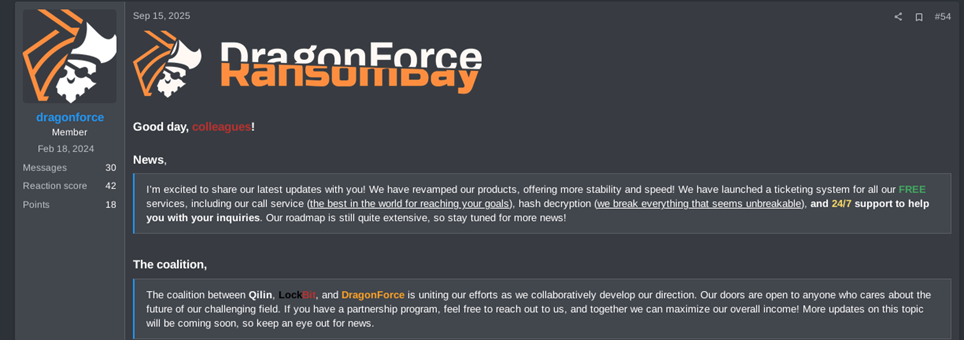
Figure 1. Post identified within a Russian underground forum
As stated in the message, the coalition is presented as necessary to face a “challenging” future (referred to as “challenge” in the original post) within the ransomware criminal ecosystem. The post presumably refers to multiple law enforcement actions carried out by international authorities, which have already led to the disruption of well-known ransomware groups such as HIVE (January 2023),[1] AlphV/BlackCat (December 2023),[2] and LockBit (February 2024),[3],[4] the latter being considered one of the most prolific ransomware collectives of all time.
In this context, the ransomware landscape has become a high-risk environment, as national and international law enforcement operations have not been limited to dismantling group infrastructures, but have also identified collective administrators and the identities of several Ransomware-as-a-Service (RaaS) operators, resulting in the issuance of international arrest warrants and the arrest of key members.[5]
This situation has contributed to a more fragmented and less cohesive ransomware ecosystem, increasing the perceived risk for individuals seeking to engage in such criminal activities. This effect is particularly evident given that takedown operations have led to the dismantling of prominent groups of presumed or confirmed Russian origin, such as HIVE, AlphV/BlackCat, and LockBit, ultimately reducing the attractiveness of ransomware gangs from a recruitment perspective.
In support of this trend, an analysis conducted in May 2025 by the Yarix Intelligence Team on leaked data from the LockBit group[6] revealed that the majority of affiliated operators were likely inexperienced, while only a small subset of skilled operators accounted for most of the attacks. The fact that most affiliates were “newbies” and that only a few meaningfully contributed to operations consequently reduced the group’s ability to attract new members. This applies not only to inexperienced affiliates, but also to seasoned operators, who increasingly perceive LockBit as a “dead man walking” a weakened organization trapped in the past and, above all, compromised by the impact of Operation Cronos.[7]
Fragmentation rather than recovery
Although overall figures suggest an increase in ransomware claims compared to 2024 with claims up approximately 61% year over year when comparing the January-November 2025 period to the same timeframe in 2024, analysts have observed a structural crisis within the ransomware ecosystem. As previously discussed, this crisis does not primarily concern the volume of operations, but rather the perception of a loss of “central” power following the dismantling of historically dominant groups such as HIVE, AlphV/BlackCat, and LockBit.
A further element supporting the fragmentation of the ransomware landscape emerges from the analysis of the percentage distribution of claims among the leading groups. In the January–November 2024 period, despite a lower overall number of claims (4,170), the top 10 ransomware groups accounted for approximately 54.8% of total claims, with a strong concentration around LockBit (10.36%) and RansomHub (9.66%). In the January–November 2025 period, despite an increase in total claims (5,998), the share attributed to the top 10 groups declines to approximately 53.1%, indicating a more even distribution of activity and the absence of a dominant actor, consistent with a more fragmented landscape.
This has led to the identification of several structural phenomena, including:
- Fragmentation: the fragmentation of ransomware groups, evidenced by the growth in the number of active groups and by the alliance discussed in this report (as of November, 2025, the ransomware groups tracked by the CTI Team already exceeded by more than 30% the total number monitored throughout the entirety of 2024);
- Payments: a decline in ransom payments made by victims.
With regard to the fragmented landscape, the case of Hunters International is particularly illustrative, as it suggests a more cautious approach to ransomware group management in the current operational environment, as also highlighted by external analyses. Hunters International, a criminal group that emerged in October 2023 and is likely a rebrand of the HIVE ransomware group, accounted for 4.30% of total victims in 2024, reaching the Top 5 most active ransomware groups by number of claims published on its Data Leak Site (DLS) by the end of the year. This figure is noteworthy given that the group was established only in late 2023 and achieved results comparable to groups such as RansomHub, LockBit, Play Ransomware, and Akira within just over a year.
Despite this ill-gotten “success,” the group progressively decided to shut down operations and re-emerge in 2025 under the “World Leaks” brand, abandoning system encryption and focusing exclusively on data exfiltration followed by extortion.[8]
This shift appears to reflect an intentional effort to reduce the group’s exposure surface and suggests a deliberate reduction in operational risk, mirroring a broader trend of caution and adaptation in a ransomware ecosystem under sustained pressure from international investigations and takedown operations following Operation Cronos. This fragmentation may also have been facilitated by the lowering of technical barriers to entry within the ransomware landscape. The widespread availability of automation tools and artificial intelligence has made it easier for less experienced operators to develop or customize encryption and exfiltration components, contributing to the proliferation of smaller groups capable of operating with greater autonomy than in the past.
With regard to the decline in victim payments, based on recent external analyses, the median ransom payment made to ransomware groups during Q3 2025 is estimated at approximately USD 140,000, representing a 65% decrease compared to the previous quarter. At the same time, the proportion of victims that actually paid whether in cases involving data exfiltration only or full system encryption dropped sharply to 23%, down from Q2 2025. Overall, these figures reflect a slow but steady trend of organizations opting not to pay ransoms, a trend that is clearly illustrated in the Coveware’s chart below.
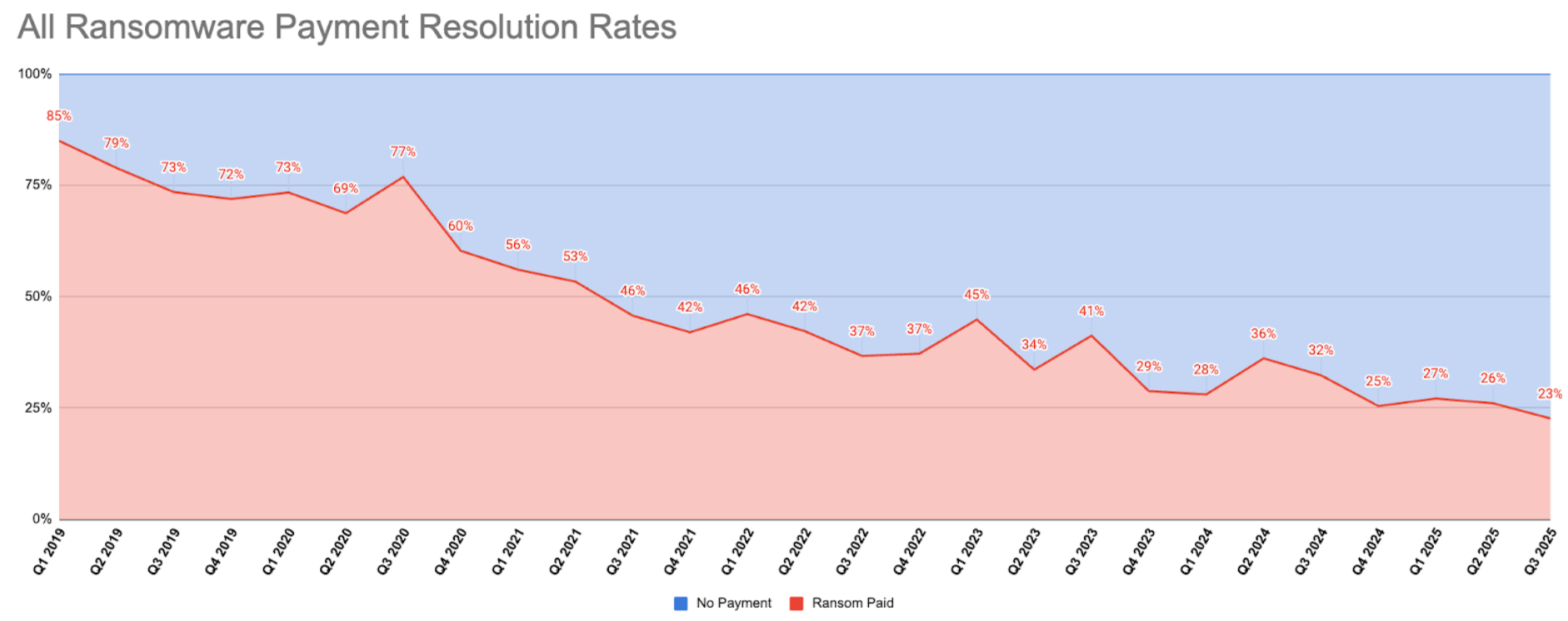
Figure 2. Source: Coveware https://www.coveware.com/blog/2025/10/24/insider-threats-loom-while-ransom-payment-rates-plummet
This phenomenon may be linked, to varying degrees, to the fragmentation of the ransomware ecosystem, the growing difficulty in attracting both inexperienced and seasoned ransomware operators capable of carrying out attacks and conducting extortion negotiations, as well as to declining confidence in ransomware as a stable criminal business model. Additionally, the reduction in payments may also be attributed to improved preparedness among organizations, which in cases of encryption no longer consider ransom payment necessary due to the availability of effective backup strategies.
As previously discussed, takedown operations often accompanied by naming and shaming campaigns targeting administrators,[9] defacement of public-facing sites,[10] and increasing organizational maturity in terms of security awareness and incident response have collectively created conditions that make the ransomware landscape both less attractive and significantly riskier for criminal actors.
Why volume no longer translates into leverage
In this context, it is important to highlight the presence of ransomware actors that do not operate exclusively within a traditional Ransomware-as-a-Service (RaaS) model, but instead focus on identifying specific vulnerabilities in widely used applications to exfiltrate as much data as possible before proceeding with the “ransom” phase, demanding payment to prevent publication on their Data Leak Sites (DLS). One of the most illustrative examples is Cl0p, which over the years has become well known for exploiting vulnerabilities in applications primarily used for enterprise data transfer, including Accellion FTA, GoAnywhere MFT, and vulnerabilities related to MOVEit Transfer.[11]
Note: Cl0p-related claims connected to the Cleo exploitation campaign were released gradually in 2025. This publication pattern may lead to an underestimation of Cl0p’s activity in the time-based analyses presented below, and the group’s actual impact could therefore be higher than reflected in this report, as a portion of these disclosures were not yet fully incorporated into the CTI Team’s dataset at the time of analysis.
Given the near annual recurrence of this pattern, Cl0p represents a successful example of single extortion, deliberately avoiding data encryption, which would require riskful presence within victim infrastructures typically achieved through the abuse of privileged credentials on exposed and theoretically more protected endpoints such as firewalls. Instead, the group relies on exploiting CVEs in widely deployed and comparatively less monitored applications to exfiltrate large volumes of data and subsequently demand ransom payments to prevent disclosure.
More recently, threat actors, including the ShinyHunters group appear to have adopted a similar approach, focusing on vulnerabilities or weak configurations in widely used services, likely not only for financial gain but also for visibility. This has resulted in the acquisition of significant volumes of data, reportedly through the exploitation of applications such as Snowflake, Salesforce and the abuse of the recently disclosed CVE-2025-61882 affecting Oracle E-Business Suite.[12]
The increasing reliance on data-only exfiltration campaigns highlights a pragmatic evolution of the ransomware model in a context of sustained pressure. Single extortion significantly reduces the time spent within victim environments and allows threat actors to avoid high-risk activities, thereby decreasing the number of detectable indicators and anomalies within monitoring systems. Furthermore, the absence of an encryption phase entails lower operational risk and a more limited exposure profile, while still preserving a strong extortion potential.
Supporting data
In order to assess the actual credibility of the post announcing the Qilin/DragonForce/LockBit alliance, the following section analyzes the trends of the main ransomware groups observed between January 1 and November 30, 2025, with the aim of identifying a potential correlation between the alliance announcement and the ransomware claims attributed to the groups involved.
Ransomware figures for the January–November 2025 period show that Qilin is the group with the highest number of claims (13.07%), followed by Akira (10.85%), INC Ransom (5.45%), Play Ransomware (4.92%), and SafePay (4.60%). Overall, the top five ransomware groups accounted for just under 39% of total ransomware claims recorded in 2025 (38.89%).
Focusing the analysis on the groups involved in the alliance, Qilin and DragonForce both show an upward trend throughout the year in terms of claims published on their respective Data Leak Sites (DLS). LockBit, by contrast, has not published any claims since May 2025, despite the announcement of the launch of the “new” LockBit 5.0 malware version.
Qilin Claims (Jan-Nov 2025)
| Month | % |
|---|---|
| Jan | 0.33% |
| Feb | 0.48% |
| Mar | 0.67% |
| Apr | 0.78% |
| May | 0.92% |
| Jun | 1.38% |
| Jul | 0.95% |
| Aug | 1.27% |
| Sep | 1.33% |
| Oct | 3.25% |
| Nov | 1.70% |
| Total | 13.06% |
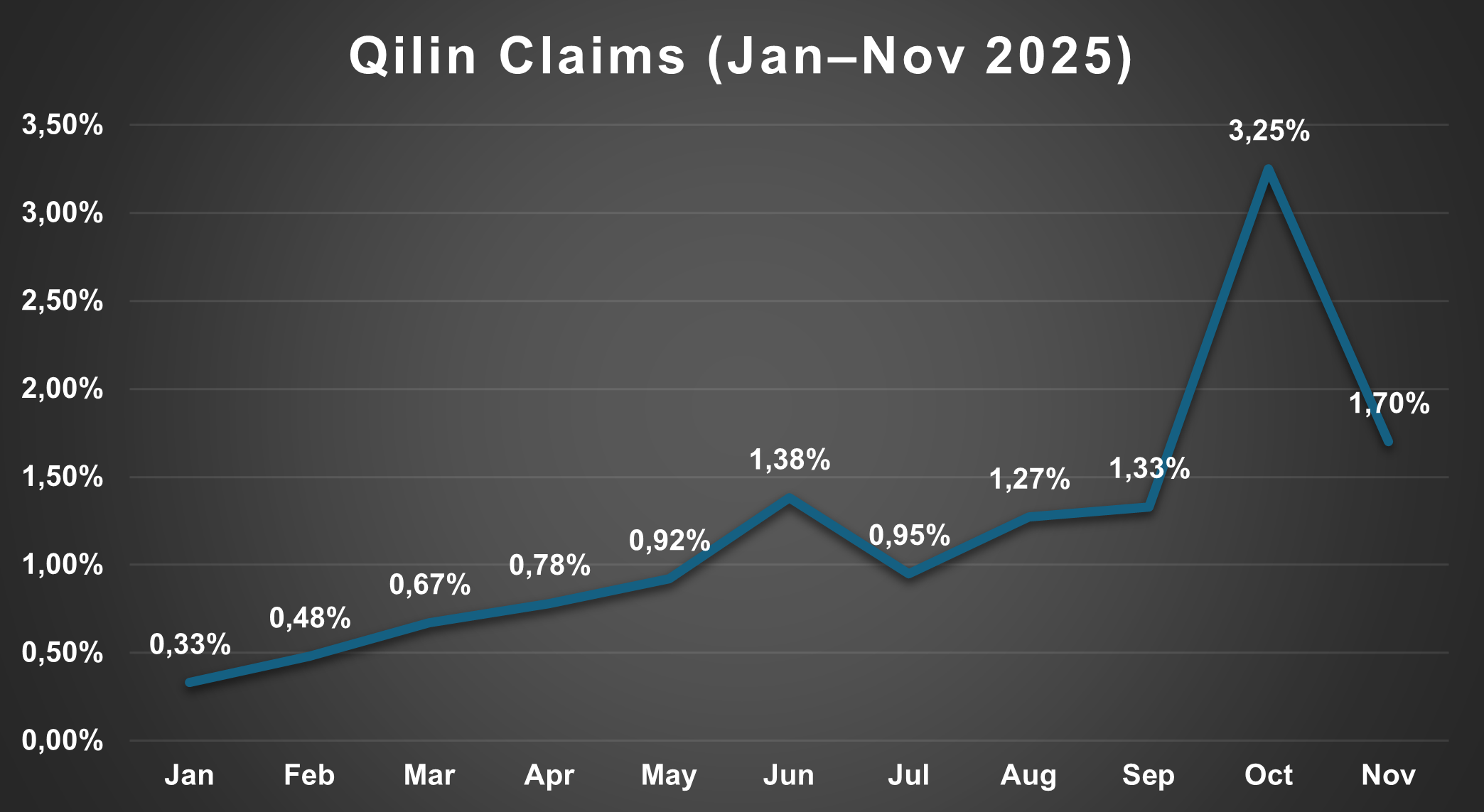
Figure 3. Qilin Claims (Jan–Nov 2025)
DragonForce Claims (Jan-Nov 2025)
| Month | % |
|---|---|
| Jan | 0.10% |
| Feb | 0.08% |
| Mar | 0.22% |
| Apr | 0.22% |
| May | 0.00% |
| Jun | 0.40% |
| Jul | 0.38% |
| Aug | 0.45% |
| Sep | 0.15% |
| Oct | 0.32% |
| Nov | 0.38% |
| Total | 2.70% |

Figure 4. DragonForce Claims (Jan-Nov 2025)
LockBit Claims (Jan-Nov 2025)
| Month | % |
|---|---|
| Jan | 0.17% |
| Feb | 0.08% |
| Mar | 0.03% |
| Apr | 0.10% |
| May | 0.07% |
| Jun | 0.00% |
| Jul | 0.00% |
| Aug | 0.00% |
| Sep | 0.00% |
| Oct | 0.00% |
| Nov | 0.00% |
| Total | 0.45% |
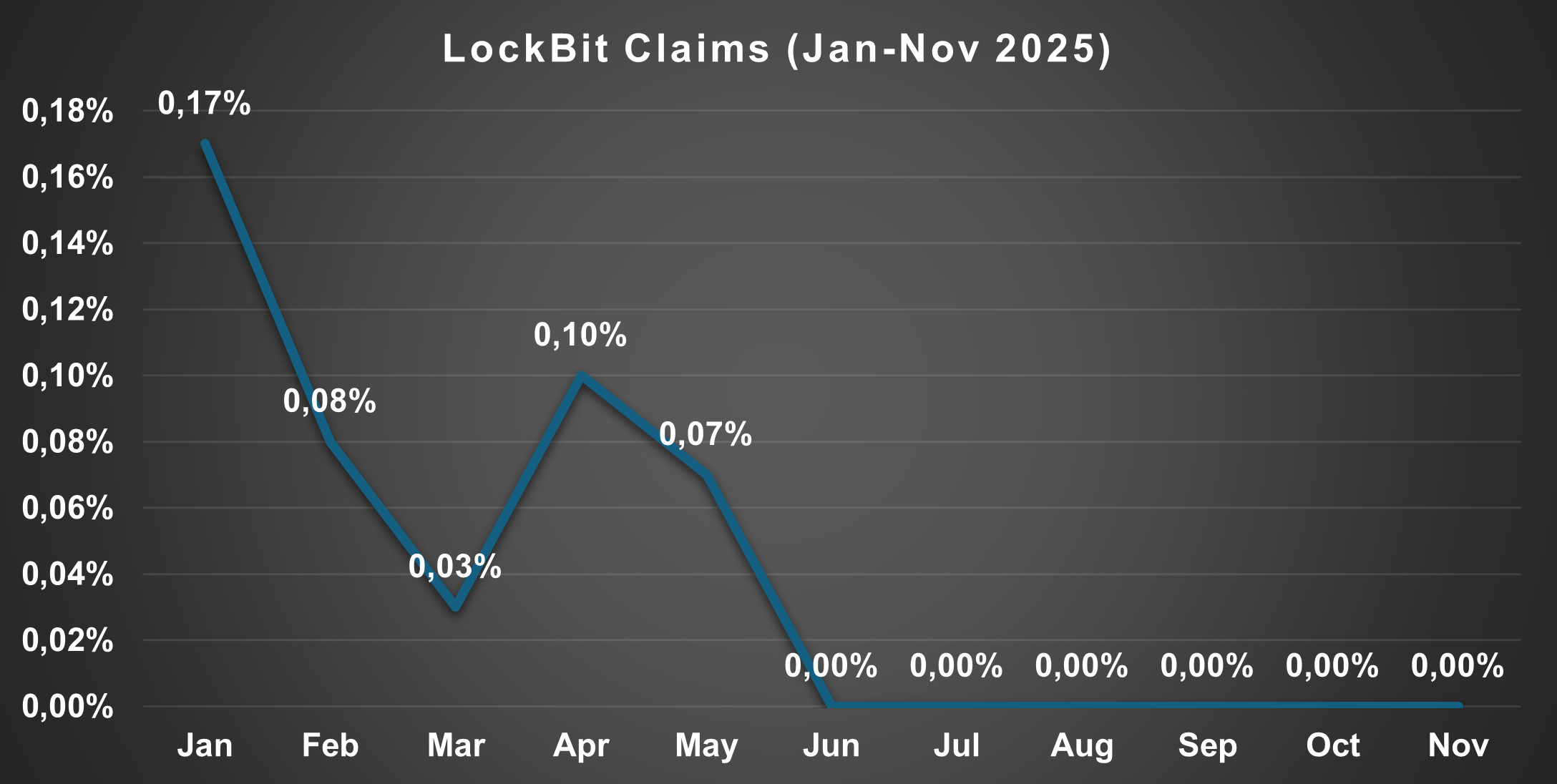
Figure 5. LockBit Claims (Jan-Nov 2025)

Figure 6. Trend Qilin-DragonForce-LockBit Claims (Jan-Nov 2025)
As already analyzed in the CTI Team’s May 2025 report,[13] following the defacement operation and the database dump of the internal panel used by RaaS operators, LockBit does not appear to have recovered full operational capability after Operation Cronos.
Despite an initially encouraging start, the period from June to November shows no public claims on the group’s DLS. This behavior is consistent with the previously analyzed panel dump incident, which revealed that the majority of LockBit affiliates were inexperienced operators, while only a small subset of skilled members contributed significantly to attack activity.
With specific reference to the alliance, the observed trend does not appear to be slowing down, supporting the hypothesis of a possible correlation between DragonForce’s collaboration announcement and an effective increase in workforce across the analyzed groups.
Notably, the activity peak recorded by Qilin in October coincides temporally with the September 15, 2025 alliance announcement, suggesting a potential internal organizational adjustment driven by a redistribution of operators that may have begun in the preceding months.
Although Qilin’s number of claims decreases in November, it remains higher than in August, prior to the alliance announcement, maintaining a very high level of activity even after the October peak. DragonForce, meanwhile, shows stable and consistent operational continuity in line with its year-long profile. LockBit, by contrast, remains completely inactive since June, reinforcing the hypothesis that the alliance announced in September may also represent a brand survival strategy or an attempt to capitalize on operators migrating toward more active collectives such as Qilin and DragonForce.
A further significant indicator for assessing a potential multiplier effect of the announcement concerns Qilin’s positioning within the Top 5 most active ransomware groups. Considering the number of claims prior to the alliance announcement, namely from January to August 2025, Qilin ranked second, behind only Akira. Analyzing claims recorded in the subsequent months, Qilin overtook Akira as early as September, securing first place and maintaining that position through October and November.
Claims Jan–Aug 2025
| TOP | Ransomware | % |
|---|---|---|
| 1 | Akira | 10.31% |
| 2 | Qilin | 9.90% |
| 3 | SafePay | 5.47% |
| 4 | INC Ransom | 5.01% |
| 5 | Play Ransomware | 4.96% |
Claims Jan–Sep 2025
| TOP | Ransomware | % |
|---|---|---|
| 1 | Qilin | 10.57% |
| 2 | Akira | 10.39% |
| 3 | SafePay | 5.34% |
| 4 | INC Ransom | 5.27% |
| 5 | Play Ransomware | 5.23% |
With regard to DragonForce,[14] growth appears more gradual but nonetheless significant. In August, the group ranked ninth in terms of total claims, maintaining steady growth and reaching eighth place by October 31, 2025.
Claims Jan–Aug 2025
| TOP | Ransomware | % |
|---|---|---|
| 1 | Akira | 10.31% |
| 2 | Qilin | 9.90% |
| 3 | SafePay | 5.47% |
| 4 | INC Ransom | 5.01% |
| 5 | Play Ransomware | 4.96% |
| 6 | Lynx | 4.55% |
| 7 | RansomHub | 4.40% |
| 8 | babuk | 3.26% |
| 9 | DragonForce | 2.70% |
| 10 | Clop | 2.31% |
Claims Jan–Oct 2025
| TOP | Ransomware | % |
|---|---|---|
| 1 | Qilin | 12.76% |
| 2 | Akira | 10.33% |
| 3 | INC Ransom | 5.18% |
| 4 | Play Ransomware | 5.00% |
| 5 | SafePay | 4.88% |
| 6 | Lynx | 4.21% |
| 7 | RansomHub | 3.39% |
| 8 | DragonForce | 2.60% |
| 9 | babuk | 2.51% |
| 10 | Clop | 2.02% |
It is important to consider that the Qilin/DragonForce/LockBit alliance may not reflect genuine operational integration, but rather a communication-driven maneuver aimed at reinforcing brand perception, particularly for LockBit. In light of the group’s loss of credibility following the panel dump, the absence of claims since mid-2025, and its ban from underground forums (discussed in the following section), LockBit may have leveraged the announcement as a reputational survival strategy.
At the same time, Qilin and DragonForce, both of which displayed consistent and sustained growth throughout 2025, do not show concrete signs of strategic dependency on LockBit, making it plausible that the coalition is largely symbolic rather than indicative of structured operational coordination. Nevertheless, the spike in Qilin’s claims in October 2025 may also be partially attributed to the marketing effect of the ransomware trio’s announcement, which, even without a direct transfer of operators from LockBit, likely generated significant visibility and attracted ransomware operators who subsequently affiliated with Qilin and DragonForce following the alliance post.
In the context of LockBit’s apparent and progressive loss of public and operational relevance, it is worth noting that on September 2, 2025, approximately two weeks prior to the alliance announcement, the administrator of the XSS forum launched a poll directed at the criminal community to gather feedback on the possible removal of the ban imposed on the LockBitSupp account.[15]. The vote, which remained open until September 9, 2025, resulted in a decision against reinstating the profile.
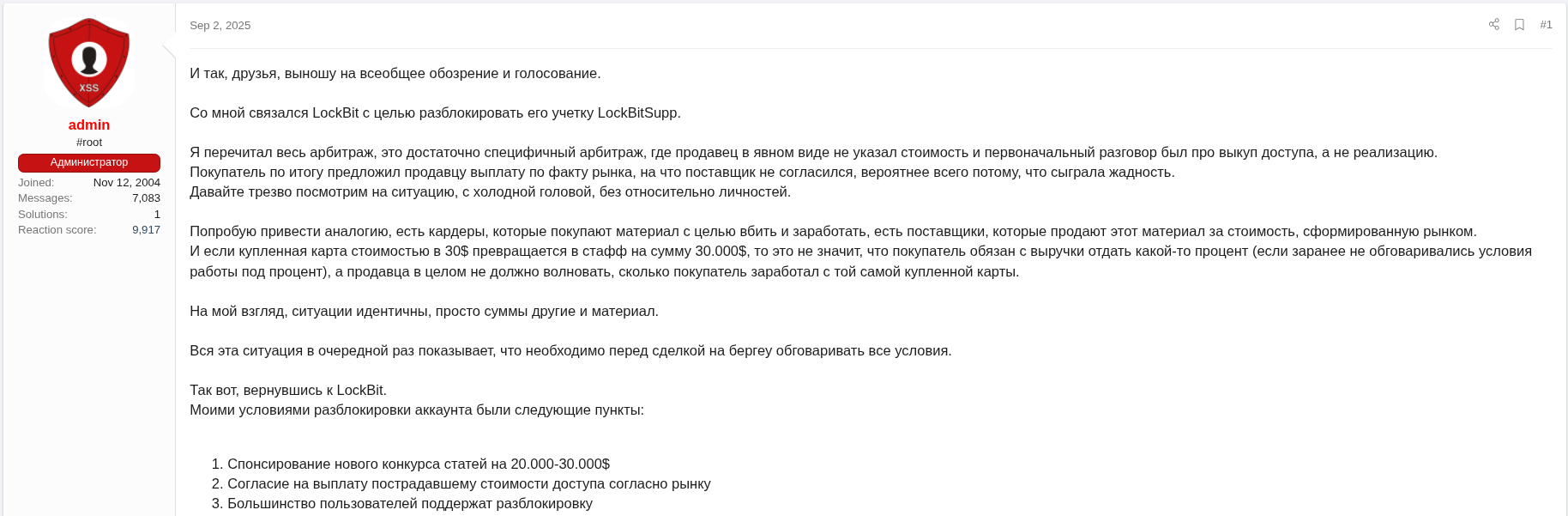
Figure 7. Original post in Russian – September 2, 2025
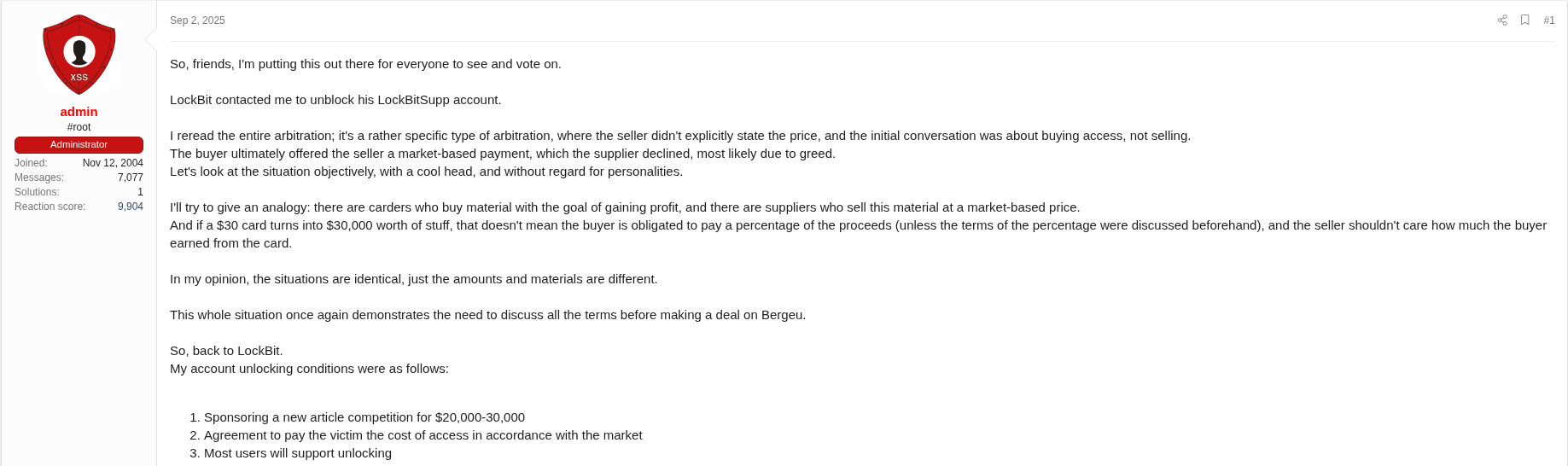

Figure 8. Post translated using automated translation tools – September 2, 2025
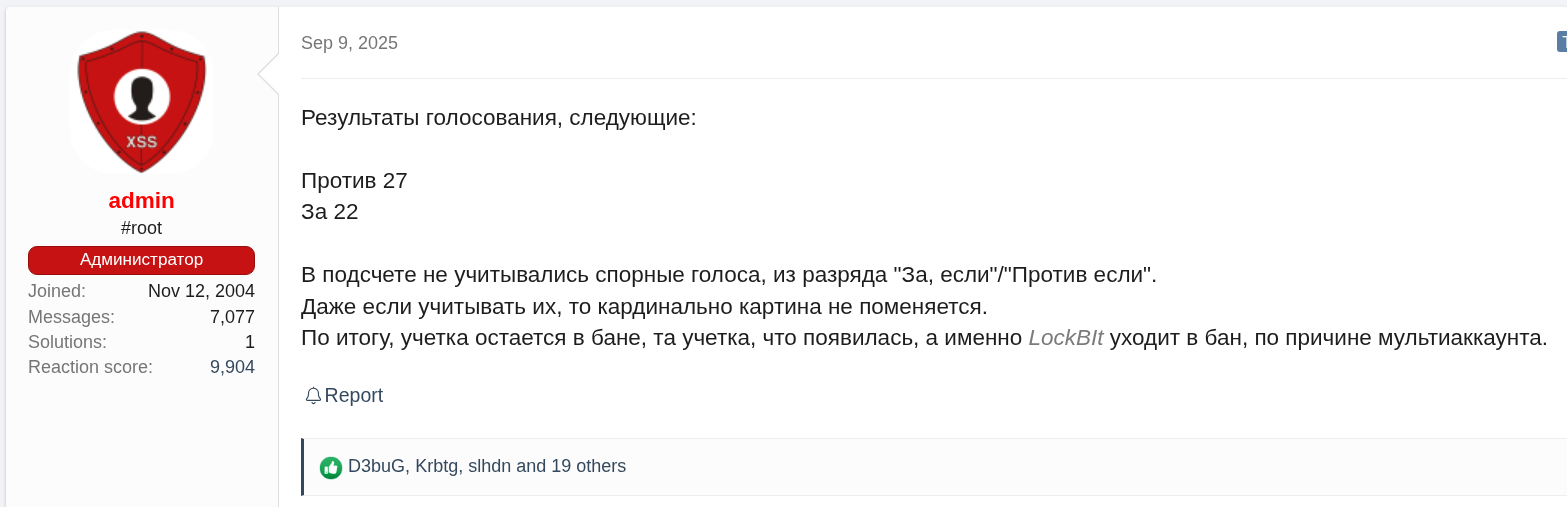
Figure 9. Voting results – September 9, 2025
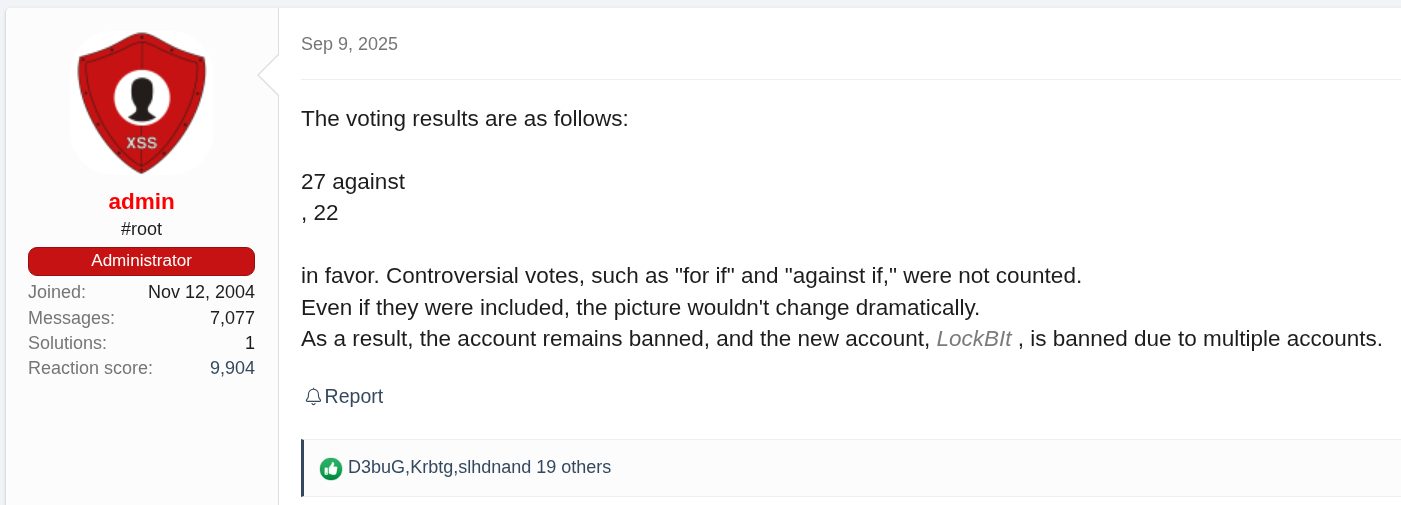
Figure 10. Post translated using automated translation tools – September 9, 2025
In this context, it is useful to analyze the timeline of events involving LockBit. In early September, the group appears to have attempted to rehabilitate its reputation within underground circles, in parallel with the announcement of the new LockBit 5.0 version.[16] These developments preceded and converged with the Qilin/DragonForce/LockBit alliance announcement of September 15, 2025.
At present, it is not possible to determine whether the alliance was planned independently of the outcome of the poll conducted on XSS. However, the temporal correlation between these events represents a potentially relevant element in the overall analysis.
The Qilin, DragonForce and LockBit alliance appears to emerge within a context of significant operational pressure, particularly following international takedown operations and Operation Cronos. While the alliance may represent an attempt to consolidate forces among active collectives, the absence of concrete operational signals from LockBit and its complete inactivity since June 2025 suggest that the alliance may reflect a reputational survival strategy aimed not only at preserving brand relevance, but also at attracting new affiliates and talent, rather than genuine operational integration.
At the same time, the autonomous growth of Qilin and DragonForce, as evidenced by the increase in claims and the operational continuity of both groups, suggests that the coalition may have been driven more by image and visibility dynamics than by an actual transfer of capabilities or operators.
Despite these considerations, trend analysis indicates that the alliance announcement coincides temporally with an increase in Qilin’s activity in October,[17] a signal that may reflect an attraction effect toward operators migrating from declining collectives or encouraged by the visibility generated by the September 15 post. In this sense, even if partially symbolic, the alliance could still have a tangible impact on the reallocation of criminal workforce and on the perceived vitality of the groups involved.
In parallel, the evolution of the ransomware operating model, marked by the rise of data only exfiltration campaigns and the broader adoption of single extortion techniques, suggests that threat actors operating under heightened pressure may increasingly favor lower risk approaches compared to traditional Ransomware as a Service models, prioritizing data exfiltration and extortion over system encryption.
In conclusion, the alliance involving Qilin, DragonForce and LockBit can be interpreted both as a signal of adaptation and rapid growth among certain criminal groups operating under intense pressure, and as an attempt by LockBit to regain relevance within an ecosystem in which its reputational and operational weight has visibly declined. Regardless of the actual solidity of the coalition, the observed developments highlight the need for continuous monitoring of ransomware claim trends, internal movements within Ransomware as a Service ecosystems, and emerging tactics focused on data exfiltration, which may redefine the scale and impact of future ransomware campaigns.
References
-
- U.S. Department of Justice, U.S. Department of Justice Disrupts Hive Ransomware Variant, available at:
hxxps://www.justice.gov/archives/opa/pr/us-department-justice-disrupts-hive-ransomware-variant
Back to the text - U.S. Department of Justice, Justice Department Disrupts Prolific ALPHV/BlackCat Ransomware Variant, available at:
hxxps://www.justice.gov/archives/opa/pr/justice-department-disrupts-prolific-alphvblackcat-ransomware-variant
Back to the text - Europol, Law enforcement disrupts world’s biggest ransomware operation, available at:
hxxps://www.europol.europa.eu/media-press/newsroom/news/law-enforcement-disrupt-worlds-biggest-ransomware-operation
Back to the text - Trend Micro, Unveiling the Fallout: Operation Cronos’ Impact on LockBit Following Landmark Disruption, available at:
hxxps://www.trendmicro.com/en_gb/research/24/d/operation-cronos-aftermath.html
Back to the text - Europol, LockBit power cut: four new arrests and financial sanctions against affiliates, available at:
hxxps://www.europol.europa.eu/media-press/newsroom/news/lockbit-power-cut-four-new-arrests-and-financial-sanctions-against-affiliates
Back to the text - Yarix Labs, Exploring the LockBit panel breach: what logs and chats reveal about Ransomware-as-a-Service, May 2025, available at:
hxxps://labs.yarix.com/2025/05/exploring-the-lockbit-panel-breach-what-logs-and-chats-reveal-about-ransomware-as-a-service/
Back to the text - Trend Micro, Operation Cronos: Aftermath, available at:
hxxps://www.trendmicro.com/en_gb/research/24/d/operation-cronos-aftermath.html
Back to the text - Group-IB, The beginning of the end: the story of Hunters International, available at:
hxxps://www.group-ib.com/it/blog/hunters-international-ransomware-group/
Back to the text - U.S. Department of Justice, U.S. Charges Russian National for Developing and Operating LockBit Ransomware, available at:
hxxps://www.justice.gov/archives/opa/pr/us-charges-russian-national-developing-and-operating-lockbit-ransomware
Back to the text - Krebs on Security (Brian Krebs), U.S. Charges Russian Man as Boss of LockBit Ransomware Group, May 2024, available at:
hxxps://krebsonsecurity.com/2024/05/u-s-charges-russian-man-as-boss-of-lockbit-ransomware-group/
Back to the text - Google Cloud Threat Intelligence, Oracle E-Business Suite Zero-Day Exploited in Widespread Extortion Campaign, available at:
hxxps://cloud.google.com/blog/topics/threat-intelligence/oracle-ebusiness-suite-zero-day-exploitation
Back to the text - Krebs on Security (Brian Krebs), ShinyHunters Wage Broad Corporate Extortion Spree, October 2025, available at:
hxxps://krebsonsecurity.com/2025/10/shinyhunters-wage-broad-corporate-extortion-spree/
Back to the text - Yarix Labs, Exploring the LockBit panel breach: what logs and chats reveal about Ransomware-as-a-Service, May 2025, available at:
hxxps://labs.yarix.com/2025/05/exploring-the-lockbit-panel-breach-what-logs-and-chats-reveal-about-ransomware-as-a-service/
Back to the text - Signs of the establishment of a “ransomware cartel” were already visible in March 2025, as announced by the ransomware collective itself. For further details: Trend Micro, Ransomware Spotlight: DragonForce, available at:
hxxps://www.trendmicro.com/vinfo/us/security/news/ransomware-spotlight/ransomware-spotlight-dragonforce
Back to the text - In January 2024, accounts associated with LockBit were banned from the forum following accusations that they had scammed an Initial Access Broker by failing to pay after the broker had provided initial access to LockBit. For further details: Flare, LockBit’s conversation on XSS forum with an Initial Access Broker, March 2024, available at:
hxxps://flare.io/fr/en-apprendre/num%C3%A9riques/blog/lockbits-conversation-on-xss-forum-with-an-initial-access-broker/
Back to the text - DailyDarkWeb, LockBit Ransomware Group Unveils Version 5.0 on Its Sixth Anniversary, available at:
hxxps://dailydarkweb.net/lockbit-ransomware-group-unveils-version-5-0-on-its-sixth-anniversary/
Back to the text - Author’s note: Within the timeframe considered in this report and in line with the limitations outlined in the initial disclaimer, variations in publicly reported victim counts, including the increase observed for Qilin, should be interpreted with caution, as Data Leak Site activity may reflect delayed or batch publication of previously compromised organizations rather than real-time changes in operational activity.
Back to the text
- U.S. Department of Justice, U.S. Department of Justice Disrupts Hive Ransomware Variant, available at:
Author
Samuele De Tomas Colatin serves as the Cyber Intelligence Team Leader within the Yarix’s Cyber Threat Intelligence division (YCTI). Previously, he worked as a researcher at the NATO Cooperative Cyber Defence Centre of Excellence in Tallinn, Estonia. He is currently trying to find a balance between updating MISP and living his private life. Spoiler: he has not succeeded yet.
如有侵权请联系:admin#unsafe.sh