
嗯,用户让我总结一下这篇文章的内容,控制在100字以内,而且不需要用“文章内容总结”之类的开头。好的,我先看看文章讲的是什么。 文章主要讲的是一个网络攻击活动,目标是Palo Alto的GlobalProtect VPN和SonicWall的SonicOS API。攻击者使用了来自德国公司3xK GmbH的7000多个IP地址,时间从12月2日开始。GreyNoise的报告提到,攻击者先是尝试暴力破解GlobalProtect的登录,然后转向扫描SonicWall的API端点。Palo Alto回应说这是基于凭证的攻击,不是软件漏洞利用,并建议启用多因素认证。 好的,我需要把这些关键点浓缩到100字以内。包括攻击目标、IP来源、时间、GreyNoise的发现、攻击手法变化、Palo Alto的回应和建议。 可能这样写:描述了一个针对Palo Alto GlobalProtect VPN和SonicWall SonicOS API的大规模网络攻击活动,涉及7,000多个IP地址,起始于12月2日。GreyNoise报告指出攻击者最初尝试暴力破解VPN登录,随后转向扫描API端点。Palo Alto确认此为基于凭证的攻击,并建议启用多因素认证。 检查一下字数是否在限制内,并且是否涵盖了所有关键点。 </think> 描述了一个针对Palo Alto GlobalProtect VPN和SonicWall SonicOS API的大规模网络攻击活动,涉及7,000多个IP地址,起始于12月2日。GreyNoise报告指出攻击者最初尝试暴力破解VPN登录,随后转向扫描API端点。Palo Alto确认此为基于凭证的攻击,并建议启用多因素认证。 2025-12-6 18:45:21 Author: www.bleepingcomputer.com(查看原文) 阅读量:13 收藏

A campaign has been observed targeting Palo Alto GlobalProtect portals with login attempts and launching scanning activity against SonicWall SonicOS API endpoints.
The activity started on December 2nd and originated from more than 7,000 IP addresses from infrastructure operated by the German IT company 3xK GmbH, which runs its own BGP network (AS200373) and operates as a hosting provider.
Initially, the actor targeted GlobalProtect portals with bruteforce and login attempts, then pivoted to scanning SonicWall API endpoints, threat intelligence company GreyNoise says in a report this week.
GlobalProtect is the VPN and remote access component of Palo Alto Networks’ firewall platform, used by large enterprises, government agencies, and service providers.
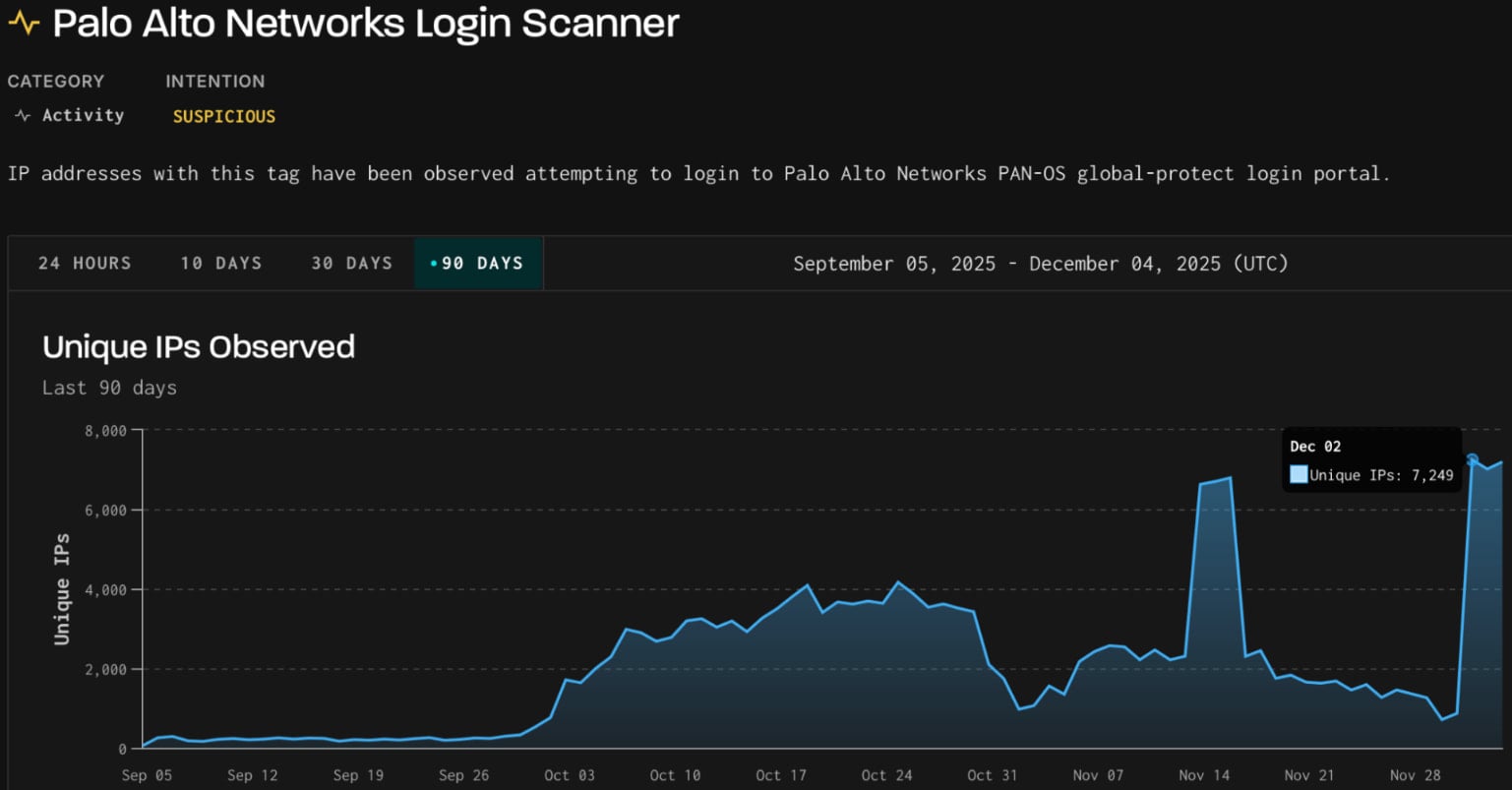
Source: GreyNoise
According to GreyNoise, the GlobalProtect login attempts targeted two profiles in the company's sensor network for passive capture of scanning and exploitation activity.
The researchers say that the surge used three client fingerprints previously observed in scanning attempts recorded between late September and mid-October.
This past activity originated from four ASNs with no history of malicious activity, generating over 9 million non-spoofable HTTP sessions, mostly targeting GlobalProtect portals.
In mid-November, GreyNoise also observed activity from 3xK Tech GmbH's infrastructure probing GlobalProtect VPN portals with 2.3 million scan sessions. Most of the attacking IPs (62%) were located in Germany, and used the same TCP/JA4t fingerprints.
Based on the analyzed indicators, the company confidently attributes both activities to the same actor.
On December 3, the same three fingerprints were seen in scanning activity targeting SonicWall SonicOS API.
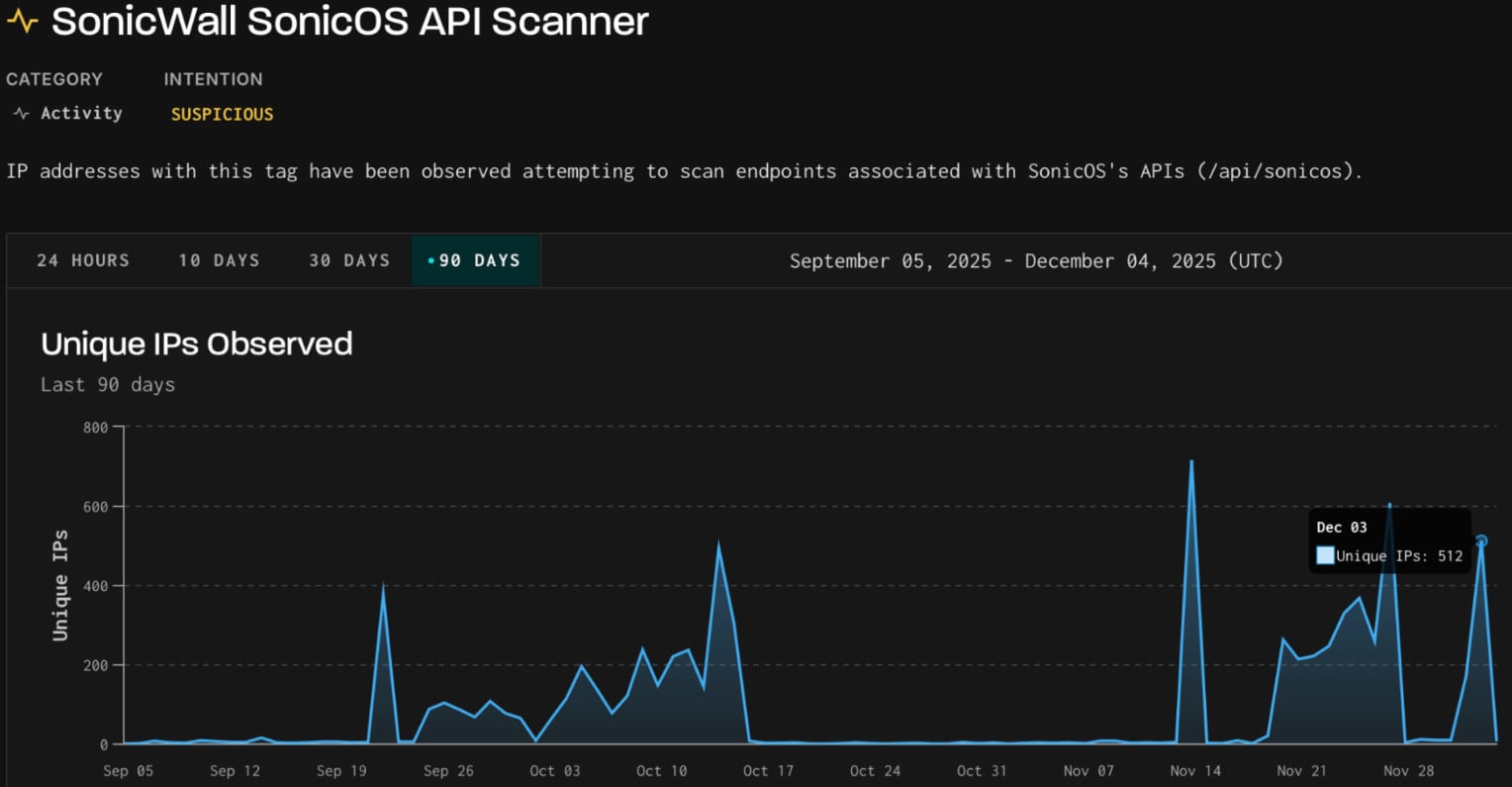
Source: GreyNoise
SonicOS is the operating system running on SonicWall firewalls, exposing API endpoints for configuration, remote management, and monitoring.
Malicious scanning targeting these endpoints is typically done to identify vulnerabilities and misconfigurations. GreyNoise has previously noted that these scans may also help discover exposed infrastructure in preparation for potential exploitation of upcoming flaws.
For this reason, defenders are advised to monitor for IPs associated with this type of activity and block them.
It is also recommended to monitor authentication surfaces for abnormal velocity/repeated failures, track recurring client fingerprints, and use dynamic, context-aware blocking instead of static reputation lists.
BleepingComputer has contacted Palo Alto Networks and SonicWall about this activity.
Palo Alto Networks said that it detected increased scanning aimed at GlobalProtect interfaces, and confirmed that it "represents credential-based attacks, not an exploit of a software vulnerability."
"Furthermore, our internal telemetry and Cortex XSIAM protection confirm this activity does not constitute a compromise of our products or services," the company told BleepingComputer.
Palo Alto Networks recommends customers enforce Multi-Factor Authentication (MFA) to protect against credential abuse.
Break down IAM silos like Bitpanda, KnowBe4, and PathAI
Broken IAM isn't just an IT problem - the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what "good" IAM looks like, and a simple checklist for building a scalable strategy.
如有侵权请联系:admin#unsafe.sh
