微软Teams因其协作功能和全球采用成为高价值目标,攻击者滥用其消息、通话及屏幕共享等功能实施攻击。文章分析了攻击链各阶段(如侦察、初始访问等)及常用工具,并提出加强身份保护、端点安全及外部访问控制等防护建议。 2025-10-7 17:0:0 Author: www.microsoft.com(查看原文) 阅读量:3 收藏
The extensive collaboration features and global adoption of Microsoft Teams make it a high-value target for both cybercriminals and state-sponsored actors. Threat actors abuse its core capabilities – messaging (chat), calls and meetings, and video-based screen-sharing – at different points along the attack chain. This raises the stakes for defenders to proactively monitor, detect, and respond.
While under Microsoft’s Secure Future Initiative (SFI), default security has been strengthened by design, defenders still need to make the most out of customer-facing security capabilities. Therefore, this blog recommends countermeasures and controls across identity, endpoints, data apps, and network layers to help harden enterprise Teams environments. To frame these defenses, we first examine relevant stages of the attack chain. This guidance complements, but doesn’t repeat, the guidance built into the Microsoft Security Development Lifecycle (SDL) as outlined in the Teams Security Guide; we will instead focus on guidance for disrupting adversarial objectives based on the relatively recently observed attempts to exploit Teams infrastructure and capabilities.
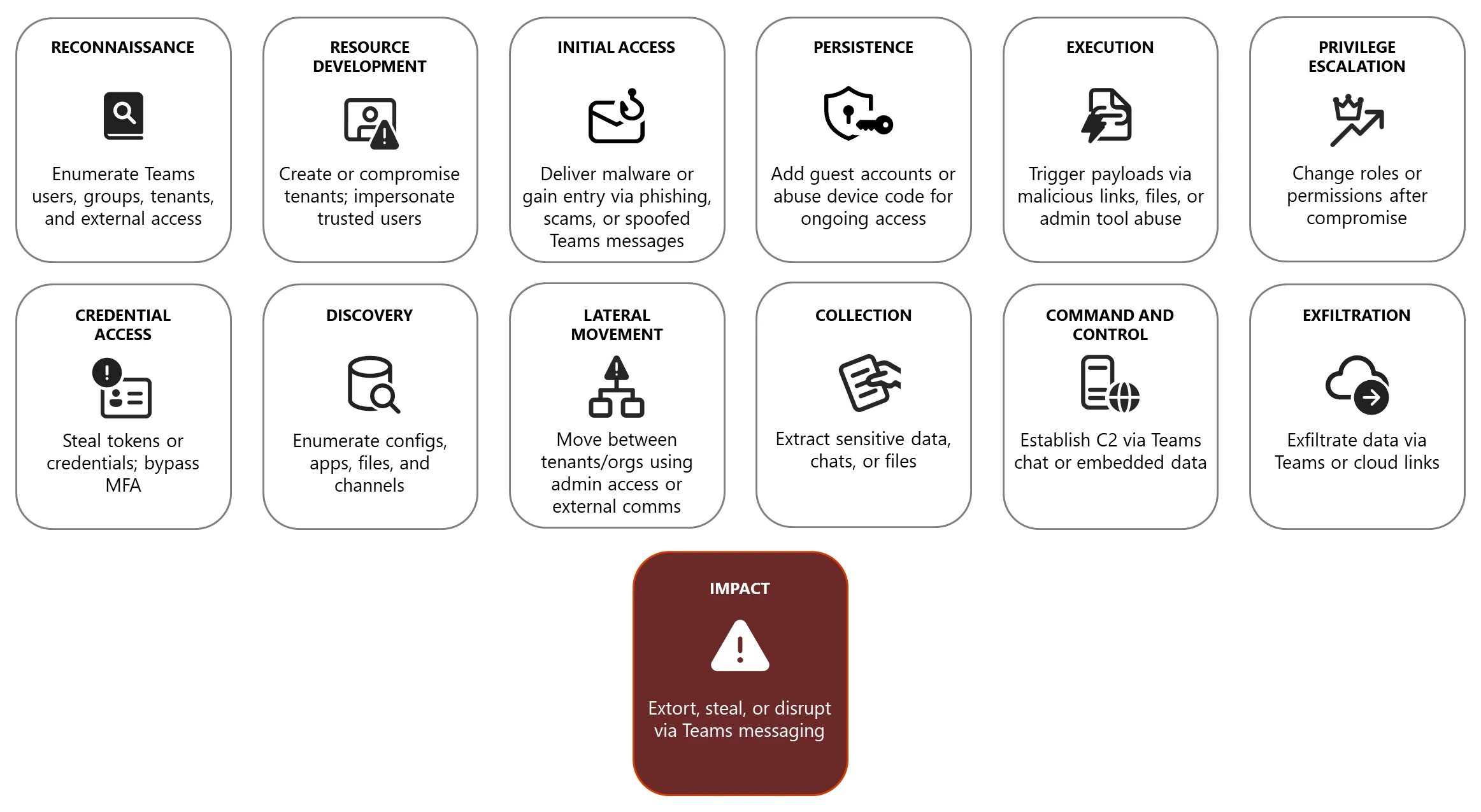
Attack chain

Reconnaissance
Every Teams user account is backed by a Microsoft Entra ID identity. Each team member is an Entra ID object, and a team is a collection of channel objects. Teams may be configured for the cloud or a hybrid environment and supports multi-tenant organizations (MTO) and cross-tenant communication and collaboration. There are anonymous participants, guests, and external access users. From an API perspective, Teams is an object type that can be queried and stored in a local database for reconnaissance by enumerating directory objects, and mapping relationships and privileges. For example, federation tenant configuration indicates whether the tenant allows external communication and can be inferred from the API response queries reflecting the effective tenant federation policy.
While not unique to Teams, there are open-source frameworks that can specifically be leveraged to enumerate less secure users, groups, and tenants in Teams (mostly by repurposing the Microsoft Graph API or gathering DNS), including ROADtools, TeamFiltration, TeamsEnum, and MSFT-Recon-RS. These tools facilitate enumerating teams, members of teams and channels, tenant IDs and enabled domains, as well as permissiveness for communicating with external organizations and other properties, like presence. Presence indicates a user’s current availability and status outside the organization if Privacy mode is not enabled, which could then be exploited if the admin has not disabled external meetings and chat with people and organizations outside the organization (or at least limited it to specified external domains).
Many open-source tools are modular Python packages including reusable libraries and classes that can be directly imported or extended to support custom classes, meaning they are also interoperable with other custom open-source reconnaissance and discovery frameworks designed to identify potential misconfigurations.
Resource development
Microsoft continuously enhances protections against fraudulent Microsoft Entra ID Workforce tenants and the abuse of free tenants and trial subscriptions. As these defenses grow stronger, threat actors are forced to invest significantly more resources in their attempts to impersonate trusted users, demonstrating the effectiveness of our layered security approach. . This includes threat actors trying to compromise weakly configured legitimate tenants, or even actually purchasing legitimate ones if they have confidence they could ultimately profit. It should come as no surprise that if they can build a persona for social engineering, they will take advantage of the same resources as legitimate organizations, including custom domains and branding, especially if it can lend credibility to impersonating internal help desk, admin, or IT support, which could then be used as a convincing pretext to compromise targets through chat messaging and phone calls. Sophisticated threat actors try to use the very same resources used by trustworthy organizations, such as acquiring multiple tenants for staging development or running separate operations across regions, and using everyday Teams features like scheduling private meetings through chat, and audio, video and screen-sharing capabilities for productivity.
Initial access
Tech support scams remain a generally popular pretext for delivery of malicious remote monitoring and management (RMM) tools and information-stealing malware, leading to credential theft, extortion, and ransomware. There are always new variants to bypass security awareness defenses, such as the rise in email bombing to create a sense of stress and urgency to restore normalcy. In 2024, for instance, Storm-1811 impersonated tech support, claiming to be addressing junk email issues that it had initiated. They used RMM tools to deliver the ReedBed malware loader of ransomware payloads and remote command execution. Meanwhile, Midnight Blizard has successfully impersonated security and technical support teams to get targets to verify their identities under the pretext of protecting their accounts by entering authentication codes that complete the authentication flow for breaking into the accounts.
Similarly in May, Sophos identified a 3AM ransomware (believed to be a rebranding of BlackSuit) affiliate adopting techniques from Storm-1811, including flooding employees with unwanted emails followed by voice and video calls on Teams impersonating help desk personnel, claiming they needed remote access to stop the flood of junk emails. The threat actor reportedly spoofed the IT organization’s phone number.
With threat actors leveraging deepfakes, perceived authority helps make this kind of social engineering even more effective. Threat actors seeking to spoof automated workflow notifications and interactions can naturally extend to spoofing legitimate bots and agents as they gain more traction, as threat actors are turning to language models to facilitate their objectives.
Prevalent threat actors associated with ransomware campaigns, including the access broker tracked as Storm-1674 have used sophisticated red teaming tools, like TeamsPhisher, to distribute DarkGate malware and other malicious payloads over Teams. In December 2024, for example, Trend Micro reported an incident in which a threat actor impersonated a client during a Teams call to persuade a target to install AnyDesk. Remote access was reportedly then used also to deploy DarkGate. Threat actors may also just use Teams to gain initial access through drive-by-compromise activity to direct users to malicious websites.
Widely available admin tools, including AADInternals, could be leveraged to deliver malicious links and payloads directly into Teams. Teams branding (like any communications brand asset) makes for effective bait, and has been used by adversary-in-the-middle (AiTM) actors like Storm-00485. Threat actors could place malicious advertisements in search results for a spoofed app like Teams to misdirect users to a download site hosting credential-stealing malware. In July 2025, for instance, Malwarebytes reported observing a malvertising campaign delivering credential-stealing malware through a fake Microsoft Teams for Mac installer.
Whether it is a core app that is part of Teams, an app created by Microsoft, a partner app validated by Microsoft, or a custom app created by your own organization—no matter how secure an app—they could still be spoofed to gain a foothold in a network. And similar to leveraging a trusted brand like Teams, threat actors will also continue to try and take advantage of trusted relationships as well to gain Teams access, whether leveraging an account with access or abusing delegated administrator relationships to reach a target environment.
Persistence
Threat actors employ a variety of persistence techniques to maintain access to target systems—even after defenders attempt to regain control. These methods include abusing shortcuts in the Startup folder to execute malicious tools, or exploiting accessibility features like Sticky Keys (as seen in this ransomware case study). Threat actors could try to create guest users in target tenants or add their own credentials to a Teams account to maintain access.
Part of the reason device code phishing has been used to access target accounts is that it could enable persistent access for as long as the tokens remain valid. In February, Microsoft reported that Storm-2372 had been capturing authentication tokens by exploiting device code authentication flows, partially by masquerading as Microsoft Teams meeting invitations and initiating Teams chats to build rapport, so that when the targets were prompted to authenticate, they would use Storm-2372-generated device codes, enabling Storm-2372 to steal the authenticated sessions from the valid access tokens.
Teams phishing lures themselves can sometimes be a disguised attempt to help threat actors maintain persistence. For example, in July 2025, the financially motivated Storm-0324 most likely relied on TeamsPhisher to send Teams phishing lures to deliver a custom malware JSSloader for the ransomware operator Sangria Tempest to use as an access vector to maintain a foothold.
Execution
Apart from admin accounts, which are an attractive target because they come with elevated privileges, threat actors try and trick everyday Teams users into clicking links or opening files that lead to malicious code execution, just like through email.
Privilege escalation
If threat actors successfully compromise accounts or register actor-controlled devices, they often times try to change permission groups to escalate privileges. If a threat actor successfully compromises a Teams admin role, this could lead to abuse of the permissions to use the admin tools that belong to that role.
Credential access
With a valid refresh token, actors can impersonate users through Teams APIs. There is no shortage of administrator tools that can be maliciously repurposed, such as AADInternals, to intercept access to tokens with custom phishing flows. Tools like TeamFiltration could be leveraged just like for any other Microsoft 365 service for targeting Teams. If credentials are compromised through password spraying, threat actors use tools like this to request OAuth tokens for Teams and other services. Threat actors continue to try and bypass multifactor authentication (MFA) by repeatedly generating authentication prompts until someone accepts by mistake, and try to compromise MFA by adding alternate phone numbers or intercepting SMS-based codes.
For instance, the financially motivated threat actor Octo Tempest uses aggressive social engineering, including over Teams, to take control of MFA for privileged accounts. They consistently socially engineer help desk personnel, targeting federated identity providers using tools like AADInternals to federate existing domains, or spoof legitimate domains by adding and then federating new domains to forge tokens.
Discovery
To refine targeting, threat actors analyze Teams configuration data from API responses, enumerate Teams apps if they obtain unauthorized access, and search for valuable files and directories by leveraging toolkits for contextualizing potential attack paths. For instance, Void Blizzard has used AzureHound to enumerate a compromised organization’s Microsoft Entra ID configuration and gather details on users, roles, groups, applications, and devices. In a small number of compromises, the threat actor accessed Teams conversations and messages through the web client. AADInternals can also be used to discover Teams group structures and permissions.
The state-sponsored actor Peach Sandstorm has delivered malicious ZIP files through Teams, then used AD Explorer to take snapshots of on-premises Active Directory database and related files.
Lateral movement
A threat actor that manages to obtain Teams admin access (whether directly or indirectly by purchasing an admin account through a rogue online marketplace) could potentially leverage external communication settings and enable trust relationships between organizations to move laterally. In late 2024, in a campaign dubbed VEILdrive by Hunters’ Team AXON, the financially motivated cybercriminal threat actors Sangria Tempest and Storm-1674 used previously compromised accounts to impersonate IT personnel and convince a user in another organization through Teams to accept a chat request and grant access through a remote connection.
Collection
Threat actors often target Teams to try and collect information from it that could help them to accomplish their objectives, such as to discover collaboration channels or high-privileged accounts. They could try to mine Teams for any information perceived as useful in furtherance of their objectives, including pivoting from a compromised account to data accessible to that user from OneDrive or SharePoint. AADInternals can be used to collect sensitive chat data and user profiles. Post-compromise, GraphRunner can leverage the Microsoft Graph API to search all chats and channels and export Teams conversations.
Command and control
Threat actors attempt to deliver malware through file attachments in Teams chats or channels. A cracked version of Brute Ratel C4 (BRc4) includes features to establish C2 channels with platforms like Microsoft Teams by using their communications protocols to send and receive commands and data.
Post-compromise, threat actors can use red teaming tool ConvoC2 to send commands through Microsoft Teams messages using the Adaptive Card framework to embed data in hidden span tags and then exfiltrate using webhooks. But threat actors can also use legitimate remote access tools to try and establish interactive C2 through Teams.
Exfiltration
Threat actors may use Teams messages or shared links to direct data exfiltration to cloud storage under their control. Tools like TeamFiltration include an exfiltration module that rely on a valid access token to then extract recent contacts and download chats and files through OneDrive or SharePoint.
Impact
Threat actors try to use Teams messages to support financial theft through extortion, social engineering, or technical means.
Octo Tempest has used communication apps, including Teams to send taunting and threatening messages to organizations, defenders, and incident response teams as part of extortion and ransomware payment pressure tactics. After gaining control of MFA through social engineering password resets, they sign in to Teams to identify sensitive information supporting their financially motivated operations.
Mitigation and protection guidance
Strengthen identity protection
- Enable sign-in and user risk policies in Microsoft Entra ID Protection. Enforce access controls based on sign-in risk. Users must be registered for Microsoft Entra multifactor authentication before sign-in risk policies can be triggered.
- Configure just-in-time access to privileged roles. Use Microsoft Entra Privileged Identity Management (PIM) (preview) to provide as-needed and just-in-time access to Microsoft 365 roles to reduce standing privileges and limit exposure.
Harden endpoint security
- Use configuration analyzer to strengthen security posture. Identify and remediate security policies that are less secure than the Standard or Strict protection profiles in preset security policies.
- Keep Teams clients, browsers, OS, and dependencies updated.
- Enable network protection and web protection capability in Defender for Endpoint.
- Enable cloud-delivered protection in Defender Antivirus. Cloud-delivered protection enables sharing detection status between Microsoft 365 and Defender for Endpoint. Real-time protection blocking, including on-access scanning, is not availablewhen Defender Antivirus is running only in passive mode. You can turn on endpoint detection and response (EDR) in block mode even if Defender Antivirus isn’t your primary antivirus solution. EDR in block mode detects and remediates malicious items on the device post-breach.
- Protect security settings from being disabled or changed with tamper protection.
- Require device compliance policies with Conditional Access. Enhance conditional access, to the extent available, with real-time enforcement through Continuous Access Evaluation (CAE), so that user session revocation is enforced in near-real time. Teams is supported as a cloud app in Microsoft Entra, so that conditional access policies apply when a user signs in. The Teams desktop application supports AppLocker, but we recommend using App Control, if feasible. Use Defender for Endpoint to enforce device compliance with Microsoft Intune.
- If your organization utilizes another remote support tool such as Remote Help, disable or remove Quick Assist as a best practice, if it isn’t used within your environment.
- Understand and use attack surface reduction capabilities in your environment to prevent common techniques used in combination with Teams threat activity as part of your first line of defense.
Secure Teams clients and apps
Implementing some of these recommendations will require Teams Administrator permissions.
- Follow the Microsoft Teams recommendations on Microsoft Secure Score.
- Manage Teams for iOS and Android with Microsoft Intune.
- Configure Teams protection in Defender for Office 365.
- Use SharePoint Online PowerShell to prevent users from downloading malicious files.
- Use the Defender portal (or PowerShell) to create an alert policy for detected files.
- Configure Zero-hour auto purge (ZAP). ZAP can retroactively detect existing malicious chat messages in Teams. Set the quarantine policy that is used for detections.
- Secure external access to Teams with Microsoft Entra ID.
- Manage guest access in Teams.
- Manage call settings in Teams. Inbound calls originating from the Public Switched Telephone Network (PSTN) on a tenant global level can be blocked.
- Use meeting and event policies to control the features that are available to organizers and participants.
- Use the Teams admin center or PowerShell to require anonymous users and people from untrusted organizations to complete a verification check before joining the meeting.
- Control access to meetings with lobby policies (who can bypass it and eligibility for admitting participants).
- Manage who can present and request control to generally prevent external users by default without business justification from being able to automatically request control over a shared window or screen.
- Manage Teams recording policies for meetings and events (as well as for town halls).
- Manage external meetings and chat.
- Specify which types of external meetings and chat to allow and which users should have access to these features. You can change the default setting to limit external access to only allowed domains or block specific domains and subdomains. By blocking external communication with trial-only tenants, users that do not have any purchased seats are not able to search and contact your users via chat, Teams calls, and meetings.
- You can prevent users that are not managed by an organization from starting conversations or prevent chat with them. If you choose to allow anonymous users in your environment, you can verify their identities by email code to join meetings (Premium).
- Monitor Teams activities using activity policies in Defender for Cloud Apps. If external users are enabled, you can monitor their presence. Defender for Cloud Apps integrates directly with Microsoft 365 audit logs. Office 365 Cloud Apps Security has access to the features of Defender for Cloud Apps to support the Office 365 app connector.
- Specify which users and groups can use Microsoft Teams apps or a copilot agent and control it on a per-app basis. You can change the default setting letting users install apps by default. Evaluate the compliance, security, and data handling information of an app and also understand the permissions requested by the app before you allow an app to be used.
Protect sensitive data
- Use meeting templates, sensitivity labels, and admin policies together for sensitive meetings.
- Teams data is encrypted in transit and at rest in Microsoft services, between services, and between clients and services. For heightened confidentiality, you can also use end-to-end encryption in advanced meeting protection that is available with the Teams Premium add-on license. This encrypts audio, video, and video-based screen sharing at its origin and decrypts it at its destination.
- You can use end-to-end encryption for up to 200 meeting participants and turn off the ability to copy and paste from meeting chats. The Premium add-on license may be required to prevent users from sharing sensitive information when attending external meetings and restrict recording to organizers in meetings with sensitive information.
- Block chats and channel messages that contain sensitive information with Microsoft Purview Data Loss Prevention (DLP) for Teams.
- Manage sharing settings for SharePoint and OneDrive.
Raise awareness
- Get started using attack simulation training. The Teams attack simulation training is currently in private preview. Build organizational resilience by raising awareness of QR code phishing, deepfakes including voice, and about protecting your organization from tech support and ClickFix scams.
- Train developers to follow best practices when working with the Microsoft Graph API. Apply these practices when detecting, defending against, and responding to malicious techniques targeting Teams.
- Using server-side code to make Graph API calls that require access tokens helps protect against token interception or leakage. We recommend using the most secure authentication flow available. For more information, see Microsoft identity platform and OAuth 2.0 Resource Owner Password Credentials.
- Learn more about some of the frequent initial access threats impacting SharePoint servers. SharePoint is a front end for Microsoft Teams and an attractive target.
Configure detection and response
- Verify the auditing status of your organization in Microsoft Purview to make sure you can investigate incidents. In Threat Explorer, Content malware includes files detected by Safe Attachments for Teams, and URL clicks include all user clicks in Teams.
- Customize how users report malicious messages, and then view and triage them.
- Security Operations (SecOps) should be enabled to proactively manage false negatives and false positives, and to hunt for threats and detections. They should triage and investigate from the Defender XDR incidents queue in the Defender portal.
- If user reporting of messages is turned on in the Teams admin center, it also needs to be turned on in the Defender portal. We encourage you to submit user reported Teams messages to Microsoft here.
- Search the audit log for events in Teams.
- Refer to the table listing the Microsoft Teams activities logged in the Microsoft 365 audit log. With the Office 365 Management Activity API, you can retrieve information about user, admin, system, and policy actions and events including from Entra activity logs.
- Familiarize yourself with relevant advanced hunting schema and available tables.
- Advanced hunting supports guided and advanced modes. You can use the advanced hunting queries in the advanced hunting section to hunt with these tables for Teams-related threats.
- Several tables covering Teams-related threats are available in preview and populated by Defender for Office 365, including MessageEvents, MessagePostDeliveryEvents, MessageUrlInfo, and UrlClickEvents. These tables provide visibility into ZAP events and URLs in Teams messages, including allowed or blocked URL clicks in Teams clients. You can join these tables with others to gain more comprehensive insight into the progression of the attack chain and end-to-end threat activity.
- Connect Microsoft 365 to Microsoft Defender for Cloud Apps.
- To hunt for Teams messages without URLs, use the CloudAppEvents table, populated by Defender for Cloud Apps. This table also includes chat monitoring events, meeting and Teams call tracking, and behavioral analytics. To make sure advanced hunting tables are populated by Defender for Cloud Apps data, go to the Defender portal and select Settings > Cloud apps > App connectors. Then, in the Select Microsoft 365 components page, select the Microsoft 365 activities checkbox. Control Microsoft 365 with built-in policies and policy templates to detect and notify you about potential threats.
- Create Defender for Cloud Apps threat detection policies.
- Many of the detection types enabled by default apply to Teams and do not require custom policy creation, including sign-ins from geographically distant locations in a short time, access from a country not previously associated with a user, unexpected admin actions, mass downloads, activity from anonymous IP addresses, or from a device flagged as malware-infected by Defender for Endpoint, as well as Oauth app abuse (when app governance is turned on).
- Defender for Cloud Apps enables you to identify high-risk use and cloud security issues, detect abnormal user behavior, and prevent threats in your sanctioned cloud apps. You can integrate Defender for Cloud Apps with Microsoft Sentinel (preview) or use the supported APIs.
- Detect and remediate illicit consent grants in Microsoft 365.
- Refer to the compromised and malicious applications incident response playbook. This playbook includes relevant guidance for identifying and investigating malicious activity on third-party apps installed in Teams, custom apps using the Graph API for Teams, or OAuth abuse involving Teams permissions.
- Discover and enable the Microsoft Sentinel data lake in Defender XDR. Sentinel data lake brings together security logs from data sources like Microsoft Defender and Microsoft Sentinel, Microsoft 365, Microsoft Entra ID, Purview, Intune, Microsoft Resource Graph, firewall and network logs, identity and access logs, DNS, plus sources from hundreds of connectors and solutions, including Microsoft Defender Threat Intelligence. Advanced hunting KQL queries can be run directly on the data lake. You can analyze the data using Jupyter notebooks.
Microsoft Defender detections
Microsoft Defender XDR customers can refer to the list of applicable detections below. Microsoft Defender XDR coordinates detection, prevention, investigation, and response across endpoints, identities, email, apps to provide integrated protection against attacks like the threat discussed in this blog.
Customers with provisioned access can also use Microsoft Security Copilot in Microsoft Defender to investigate and respond to incidents, hunt for threats, and protect their organization with relevant threat intelligence.
Microsoft Defender XDR
The following alerts might indicate threat activity associated with this threat.
- Malicious sign in from a risky IP address
- Malicious sign in from an unusual user agent
- Account compromised following a password-spray attack
- Compromised user account identified in Password Spray activity
- Successful authentication after password spray attack
- Password Spray detected via suspicious Teams client (TeamFiltration)
Microsoft Entra ID Protection
Any type of sign-in and user risk detection might also indicate threat activity associated with this threat. An example is listed below. These alerts, however, can be triggered by unrelated threat activity.
- Impossible travel
- Anomalous Microsoft Teams login from web client
Microsoft Defender for Endpoint
The following alerts might indicate threat activity associated with this threat.
- Suspicious module loaded using Microsoft Teams
The following alerts might also indicate threat activity associated with this threat. These alerts, however, can be triggered by unrelated threat activity and are not monitored in the status cards provided with this report.
- Suspicious usage of remote management software
Microsoft Defender for Office 365
The following alerts might indicate threat activity associated with this threat.
- Malicious link shared in Teams chat
- User clicked a malicious link in Teams chat
When Microsoft Defender for Cloud Apps is enabled, the following alert might indicate threat activity associated with this threat.
- Potentially Malicious IT Support Teams impersonation post mail bombing
The following alerts might also indicate threat activity associated with this threat. These alerts, however, can be triggered by unrelated threat activity and are not monitored in the status cards provided with this report.
- A potentially malicious URL click was detected
- Possible AiTM phishing attempt
Microsoft Defender for Identity
The following Microsoft Defender for Identity alerts can indicate associated threat activity:
- Account enumeration reconnaissance
- Suspicious additions to sensitive groups
- Account Enumeration reconnaissance (LDAP)
Microsoft Defender for Cloud Apps
The following alerts might indicate threat activity associated with this threat.
- Consent granted to application with Microsoft Teams permissions
- Risky user installed a suspicious application in Microsoft Teams
- Compromised account signed in to Microsoft Teams
- Microsoft Teams chat initiated by a suspicious external user
- Suspicious Teams access via Graph API
The following alerts might also indicate threat activity associated with this threat. These alerts, however, can be triggered by unrelated threat activity and are not monitored in the status cards provided with this report.
- Possible mail exfiltration by app
Microsoft Security Copilot
Microsoft Security Copilot customers can use the Copilot in Defender embedded experience to check the impact of this report and get insights based on their environment’s highest exposure level in Threat analytics, Intel profiles, Intel Explorer and Intel projects pages of the Defender portal.
You can also use Copilot in Defender to speed up analysis of suspicious scripts and command lines by inspecting them below the incident graph on an incident page and in the timeline on the Device entity page without using external tools.
Threat intelligence reports
Microsoft customers can use the following reports in Microsoft products to get the most up-to-date information about the threat actor, malicious activity, and techniques discussed in this blog. These reports provide the intelligence, protection information, and recommended actions to prevent, mitigate, or respond to associated threats found in customer environments.
Microsoft Defender XDR threat analytics
Microsoft Security Copilot customers can also use the Microsoft Security Copilot integration in Microsoft Defender Threat Intelligence, either in the Security Copilot standalone portal or in the embedded experience in the Microsoft Defender portal to get more information about this threat actor.
Hunting queries
Microsoft Defender XDR
Advanced hunting allows you to view and query all the data sources available within the unified Microsoft Defender portal, which include Microsoft Defender XDR and various Microsoft security services.
After onboarding to the Microsoft Sentinel data lake, auxiliary log tables are no longer available in Microsoft Defender advanced hunting. Instead, you can access them through data lake exploration Kusto Query Language (KQL) queries in the Defender portal. For more information, see KQL queries in the Microsoft Sentinel data lake.
You can design and tweak custom detection rules using the advanced hunting queries and set them to run at regular intervals, generating alerts and taking response actions whenever there are matches. You can also link the generated alert to this report so that it appears in the Related incidents tab in threat analytics. Custom detection rule can automatically take actions on devices, files, users, or emails that are returned by the query. To make sure you’re creating detections that trigger true alerts, take time to review your existing custom detections by following the steps in Manage existing custom detection rules.
Detect potential data exfiltration from Teams
let timeWindow = 1h;
let messageThreshold = 20;
let trustedDomains = dynamic(["trustedpartner.com", "anothertrusted.com"]);
CloudAppEvents
| where Timestamp > ago(1d)
| where ActionType == "MessageSent"
| where Application == "Microsoft Teams"
| where isnotempty(AccountObjectId)
| where tostring(parse_json(RawEventData).ParticipantInfo.HasForeignTenantUsers) == "true"
| where tostring(parse_json(RawEventData).CommunicationType) in ("OneOnOne", "GroupChat")
| extend RecipientDomain = tostring(parse_json(RawEventData).ParticipantInfo.ParticipatingDomains[1])
| where RecipientDomain !in (trustedDomains)
| extend SenderUPN = tostring(parse_json(RawEventData).UserId)
| summarize MessageCount = count() by bin(Timestamp, timeWindow), SenderUPN, RecipientDomain
| where MessageCount > messageThreshold
| project Timestamp, MessageCount, SenderUPN, RecipientDomain
| sort by MessageCount desc
Detect mail bombing that sometimes precedes technical support scams on Microsoft Teams
EmailEvents | where Timestamp > ago(1d) | where DetectionMethods contains "Mail bombing" | project Timestamp, NetworkMessageId, SenderFromAddress, Subject, ReportId
Detect malicious Teams content from MessageEvents
MessageEvents | where Timestamp > ago(1d) | where ThreatTypes has "Phish" or ThreatTypes has "Malware" or ThreatTypes has "Spam" | project Timestamp, SenderDisplayName, SenderEmailAddress, RecipientDetails, IsOwnedThread, ThreadType, IsExternalThread, ReportId
Detect communication with external help desk/support representatives
MessageEvents | where Timestamp > ago(5d) | where IsExternalThread == true | where (RecipientDetails contains "help" and RecipientDetails contains "desk") or (RecipientDetails contains "it" and RecipientDetails contains "support") or (RecipientDetails contains "working" and RecipientDetails contains "home") or (SenderDisplayName contains "help" and SenderDisplayName contains "desk") or (SenderDisplayName contains "it" and SenderDisplayName contains "support") or (SenderDisplayName contains "working" and SenderDisplayName contains "home") | project Timestamp, SenderDisplayName, SenderEmailAddress, RecipientDetails, IsOwnedThread, ThreadType
Expand detection of communication with external help desk/support representatives by searching for linked process executions
let portableExecutable = pack_array("binary.exe", "portable.exe");
let timeAgo = ago(30d);
MessageEvents
| where Timestamp > timeAgo
| where IsExternalThread == true
| where (RecipientDetails contains "help" and RecipientDetails contains "desk")
or (RecipientDetails contains "it" and RecipientDetails contains "support")
or (RecipientDetails contains "working" and RecipientDetails contains "home")
| summarize spamEvent = min(Timestamp) by SenderEmailAddress
| join kind=inner (
DeviceProcessEvents
| where Timestamp > timeAgo
| where FileName in (portableExecutable)
) on $left.SenderEmailAddress == $right.InitiatingProcessAccountUpn
| where spamEvent < Timestamp
Surface Teams threat activity using Microsoft Security Copilot
Microsoft Security Copilot in Microsoft Defender comes with a query assistant capability in advanced hunting. You can also run the following prompt in Microsoft Security Copilot pane in the Advanced hunting page or by reopening Copilot from the top of the query editor:
Show me recent activity in the last 7 days that matches attack techniques described in the Microsoft Teams technique profile. Include relevant alerts, affected users and devices, and generate advanced hunting queries to investigate further.
Microsoft Sentinel
Possible Teams phishing activity
This query specifically monitors Microsoft Teams for one-on-one chats involving impersonated users (e.g., 'Help Desk', 'Microsoft Security').
let suspiciousUpns = DeviceProcessEvents
| where DeviceId == "alertedMachine"
| where isnotempty(InitiatingProcessAccountUpn)
| project InitiatingProcessAccountUpn;
CloudAppEvents
| where Application == "Microsoft Teams"
| where ActionType == "ChatCreated"
| where isempty(AccountObjectId)
| where RawEventData.ParticipantInfo.HasForeignTenantUsers == true
| where RawEventData.CommunicationType == "OneonOne"
| where RawEventData.ParticipantInfo.HasGuestUsers == false
| where RawEventData.ParticipantInfo.HasOtherGuestUsers == false
| where RawEventData.Members[0].DisplayName in ("Microsoft Security", "Help Desk", "Help Desk Team", "Help Desk IT", "Microsoft Security", "office")
| where AccountId has "@"
| extend TargetUPN = tolower(tostring(RawEventData.Members[1].UPN))
| where TargetUPN in (suspiciousUpns)
Files uploaded to Teams and access summary
This query identifies files uploaded to Microsoft Teams chat files and their access history, specifically mentioning operations from SharePoint. It allows tracking of potential file collection activity through Teams-related storage.
OfficeActivity
| where RecordType =~ "SharePointFileOperation"
| where Operation =~ "FileUploaded"
| where UserId != "app@sharepoint"
| where SourceRelativeUrl has "Microsoft Teams Chat Files"
| join kind= leftouter (
OfficeActivity
| where RecordType =~ "SharePointFileOperation"
| where Operation =~ "FileDownloaded" or Operation =~ "FileAccessed"
| where UserId != "app@sharepoint"
| where SourceRelativeUrl has "Microsoft Teams Chat Files"
) on OfficeObjectId
| extend userBag = bag_pack(UserId1, ClientIP1)
| summarize make_set(UserId1, 10000), make_bag(userBag, 10000) by TimeGenerated, UserId, OfficeObjectId, SourceFileName
| extend NumberUsers = array_length(bag_keys(bag_userBag))
| project timestamp=TimeGenerated, UserId, FileLocation=OfficeObjectId, FileName=SourceFileName, AccessedBy=bag_userBag, NumberOfUsersAccessed=NumberUsers
| extend AccountName = tostring(split(UserId, "@")[0]), AccountUPNSuffix = tostring(split(UserId, "@")[1])
| extend Account_0_Name = AccountName
| extend Account_0_UPNSuffix = AccountUPNSuffix
References
- A familiar playbook with a twist: 3AM ransomware actors dropped virtual machine with vishing and Quick Assist (Sophos)
- convoC2 (Cxnuri0n)
- EvilSlackbot (Drew-Sec)
- Fake Microsoft Teams Emails Phish for Credentials (Dark Reading)
- Fake Microsoft Teams for Mac delivers Atomic Stealer (Malwarebytes)
- GraphRunner (Dafthack)
- Inside the Microsoft Teams attack matrix: unpacking the frontier in collaboration threats (Cyberdom)
- Microsoft 365 Attack Surfaces: Elevation of Privilege Vulnerabilities (CoreView)
- Microsoft 365 secure configuration baselines (CISA)
- MSFT-Recon-RS (Copyleftdev)
- Ongoing Email Bombing Campaigns leading to Remote Access and Post-Exploitation (eSentire)
- Playing for the wrong team: dangerous functionalities in Microsoft Teams enable phishing and malware delivery by attackers (Proofpoint)
- Signed. Sideloaded. Compromised! (Ontinue)
- Sophos MDR tracks two ransomware campaigns using “email bombing,” Microsoft Teams “vishing” (Sophos)
- TeamsEnum (Secure Systems Engineering)
- TeamsPhisher (Octoberfest7)
- Thinking Outside the Mailbox: Modernized Phishing Techniques (Praetorian)
- Unmasking VEILDrive: Threat Actors Exploit Microsoft Services for C2 (Hunters)
- Vishing via Microsoft Teams Facilitates DarkGate Malware Intrusion (Trend Micro)
Learn more
For the latest security research from the Microsoft Threat Intelligence community, check out ff
To get notified about new publications and to join discussions on social media, follow us on LinkedIn, X (formerly Twitter), and Bluesky.
To hear stories and insights from the Microsoft Threat Intelligence community about the ever-evolving threat landscape, listen to the Microsoft Threat Intelligence podcast.
如有侵权请联系:admin#unsafe.sh