TG Soft的CRAM报告称,在2025年9月15日至21日期间,意大利及全球的恶意软件活动增加,监测到31起活动,其中10起使用意大利语。主要涉及AgentTesla、BluStealer等密码窃取家族。样本以脚本文件为主(35.49%),其次是MSIL和WIN32可执行文件。活动通过邮件主题如订单、报价等进行传播。 2025-9-15 14:33:19 Author: www.tgsoft.it(查看原文) 阅读量:0 收藏
Weekly report by TG Soft's CRAM, concerning Italian malspam campaigns.
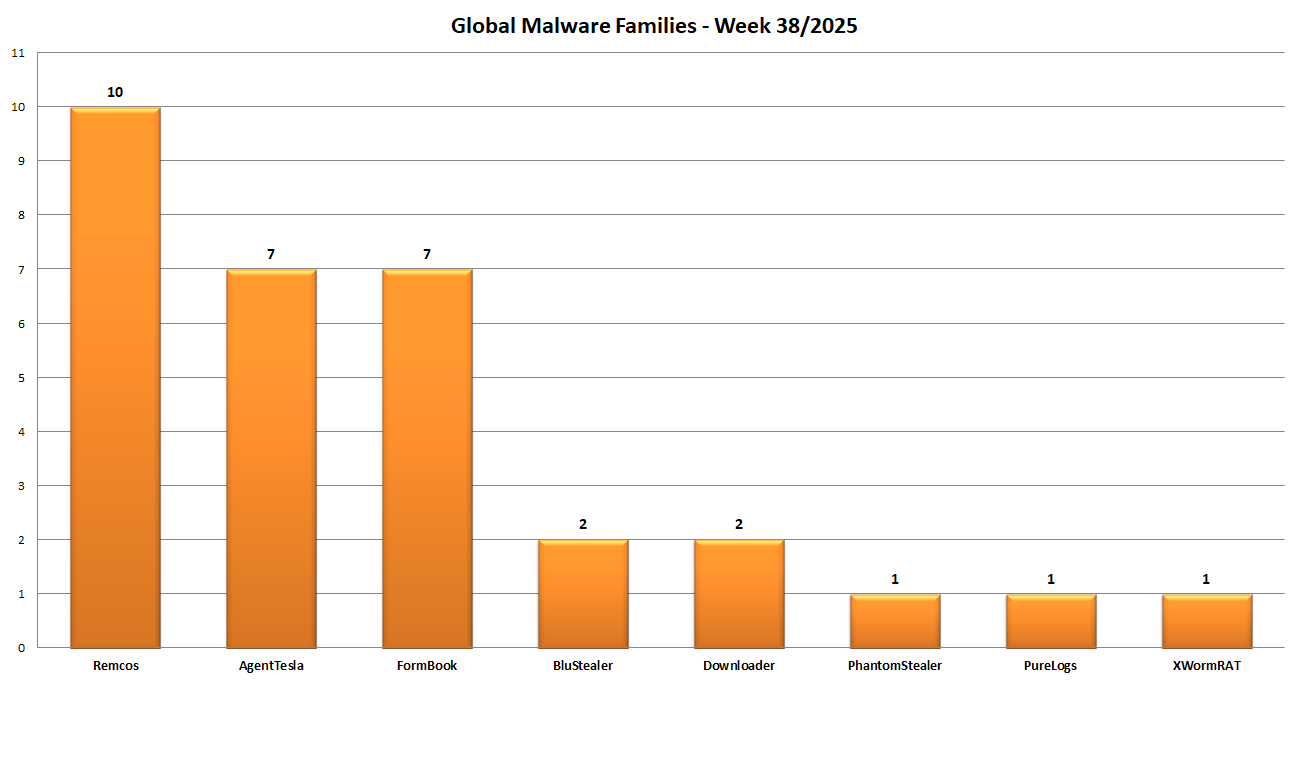
The week was characterized by Password Stealer of the Familiies:
Below are the details of the campaigns released during from 15 September to 21 September 2025.
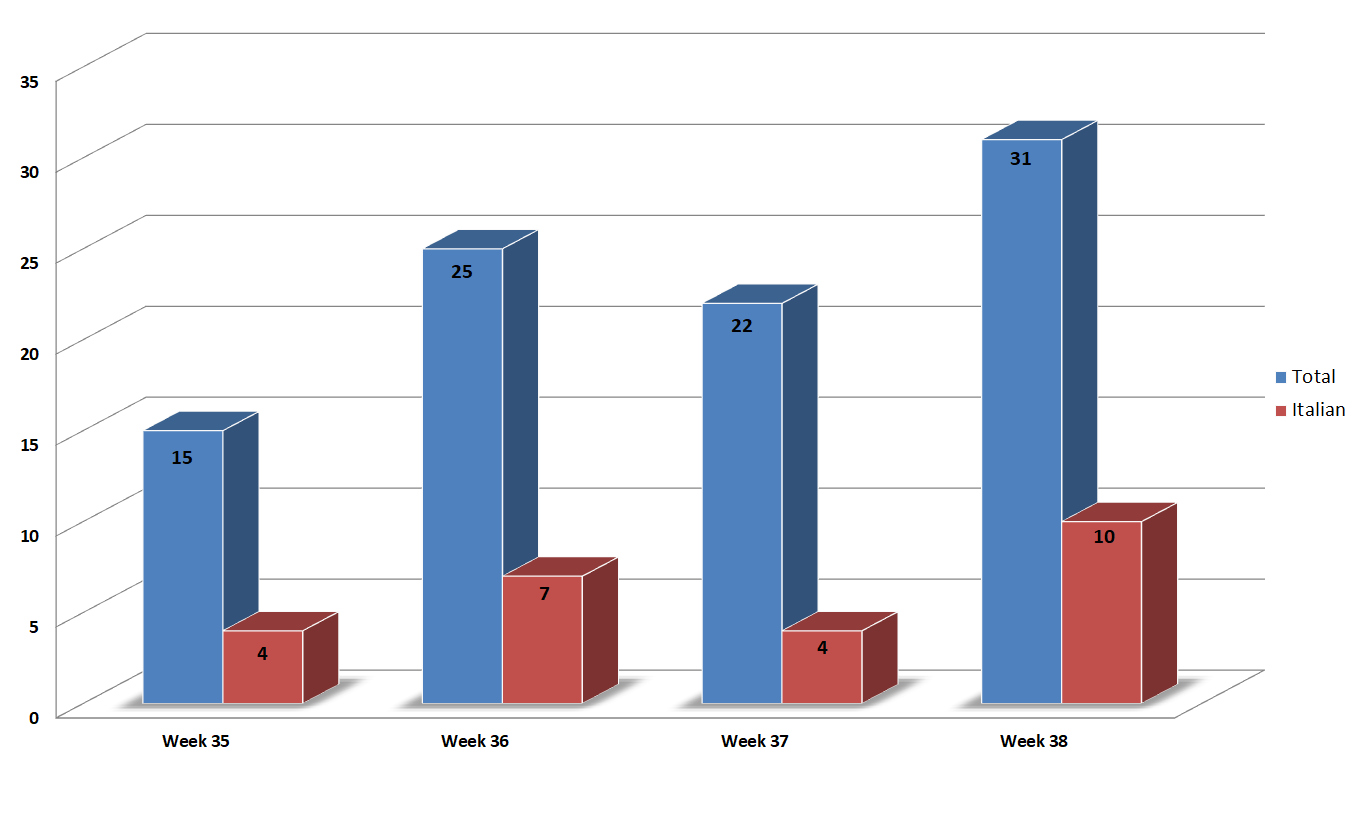
During the monitored week, global campaigns increased compared to the previous week, with Italian campaigns also on the rise.
The blue bar shows the total number of campaigns monitored in Italy in each week, while the red bar concerns campaigns in Italian (and targeting Italy).
We monitored 31 campaigns during the week, 10 of which used Italian as their language.
In order to understand how the various weeks are divided, below is a small table showing the breakdown of the considered period:
| Week |
from | to |
| Week_35 | 25/08 | 31/08 |
| Week_36 | 01/09 | 07/09 |
| Week_37 | 08/09 | 14/09 |
| Week_38 | 15/09 | 21/09 |
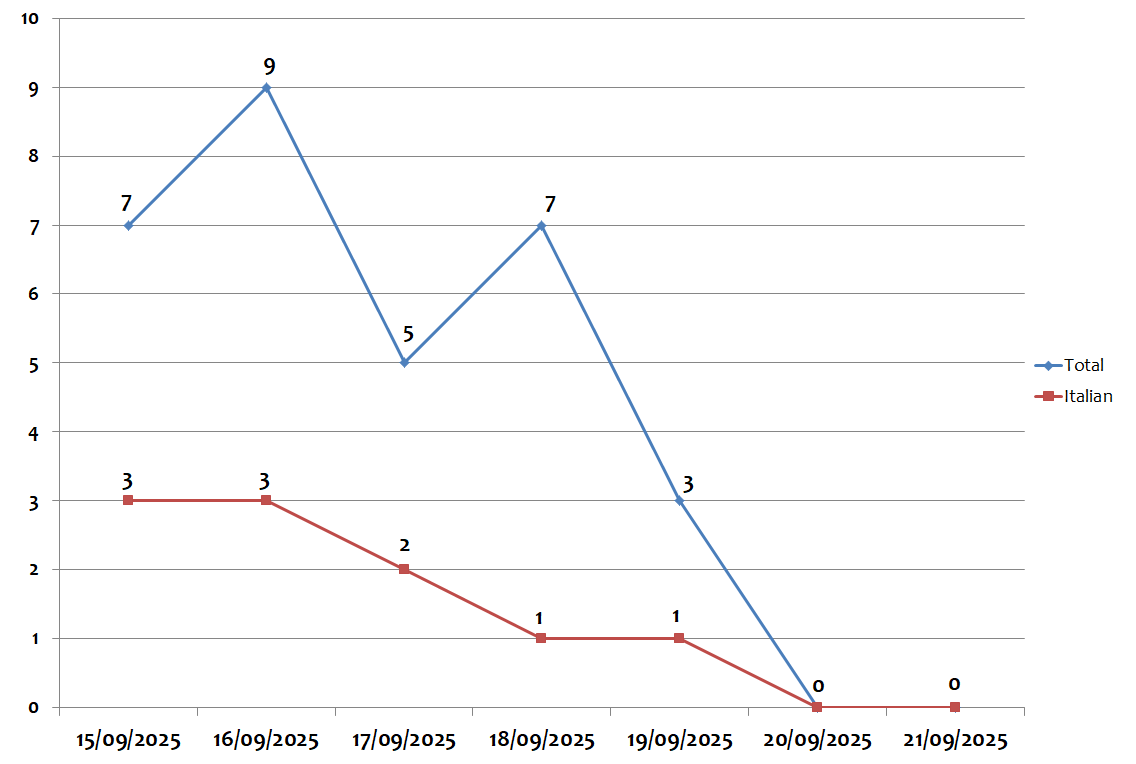
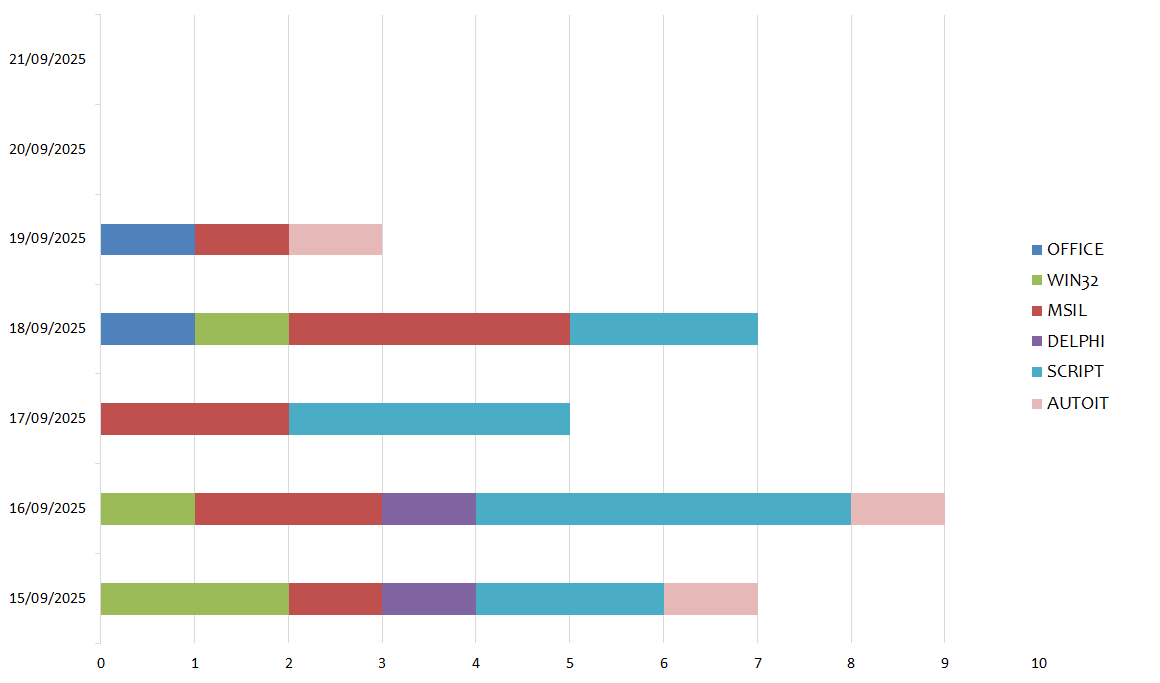
During the week, the peak in global campaigns was recorded on Tuesday 16 September, with 9 different campaigns per day. The peak in campaigns in Italian was recorded on Monday 15 and Tuesday 16 September, with 3 campaigns per day, as shown in the graph below:
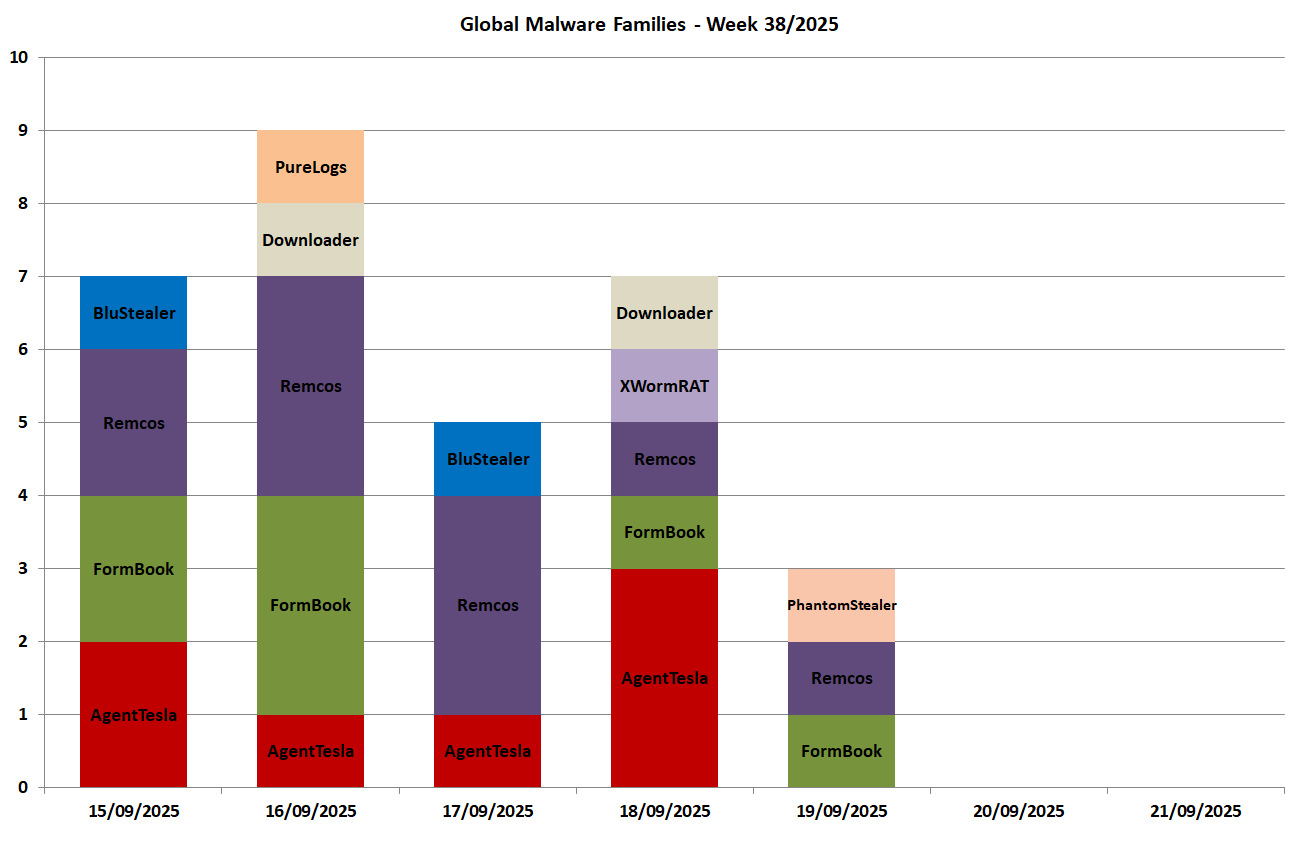
In the following chart we see the malware families spread globally for each day of the week:
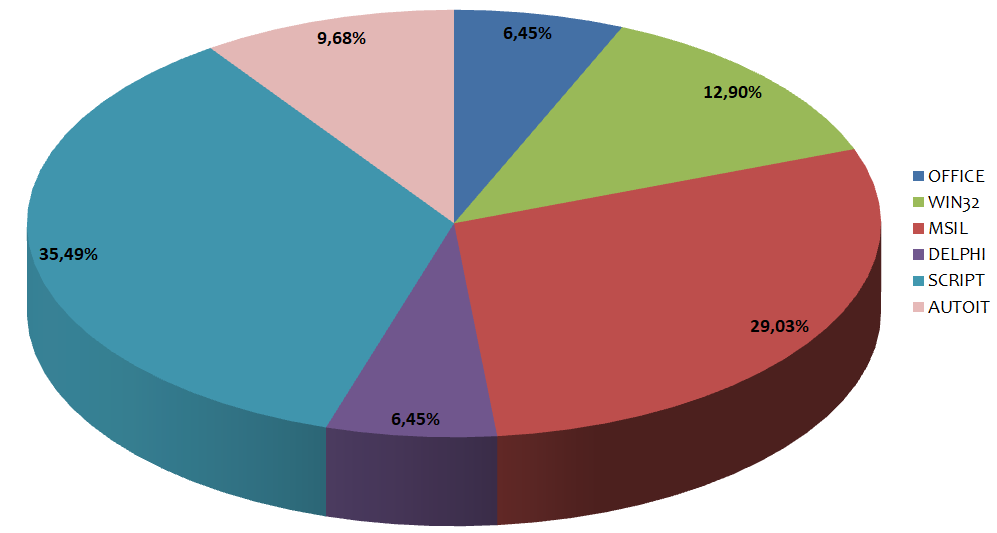
Instead in this graph we see the distribution based on malware family. In the past week 8 different families were detected:
The samples that ranked first this week were Script files with 35.49%.
In second place were MSIL executable files with 29.03%.
In third place were WIN32 executable files with 12.90%.
In the chart below we can see the various types of language used to develop malware:
In the following graph we see the distribution of the various types of languages divided by day:
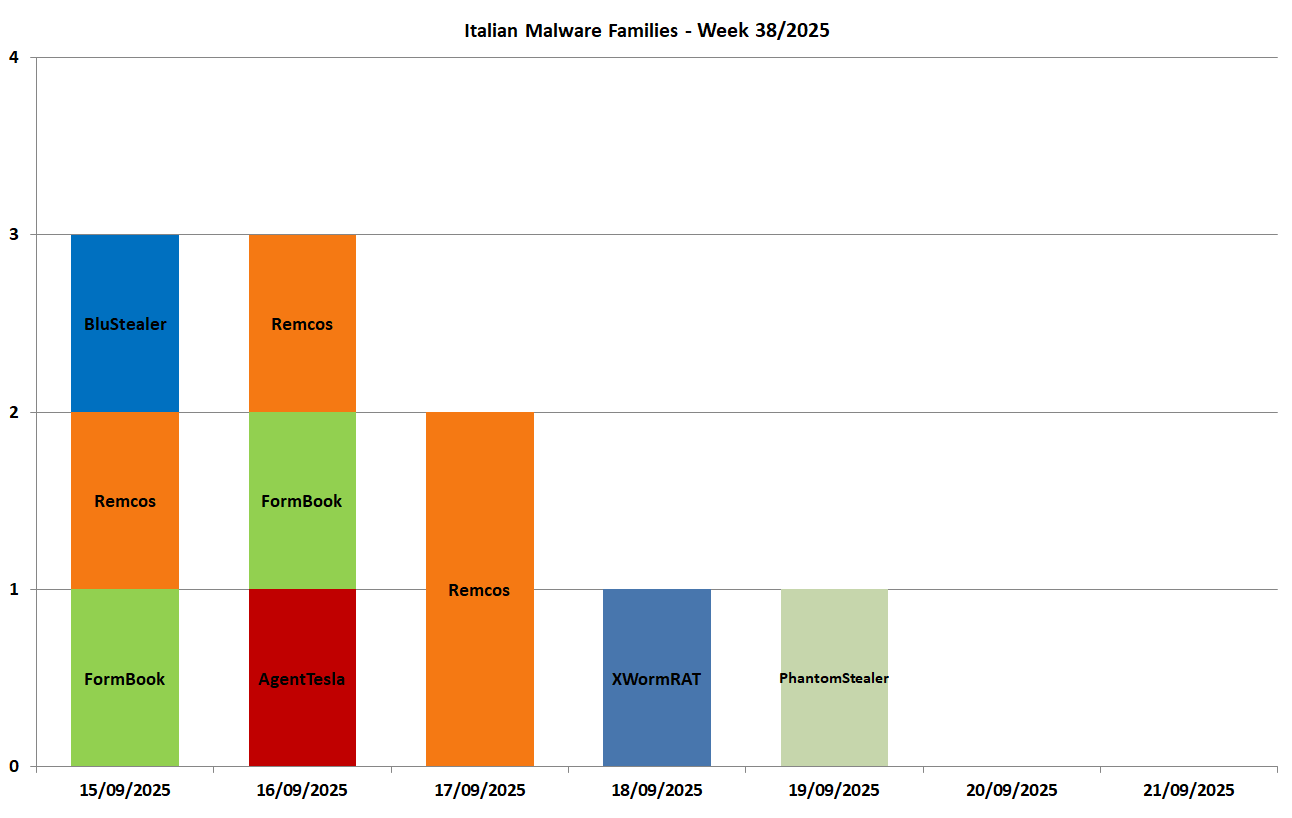
In this graph we can see the malware families spread during the week with target Italy (in Italian) and composed of 6 families:
The Italian campaigns analyzed by TG Soft's C.R.A.M. were grouped according to macro categories, obtained from the subject of the email message used for malware distribution (malspam). Below we see the subjects used in the various campaigns divided by day and type of malware.
15/09/2025
BluStealer - spread through a campaign themed "Orders".
FormBook - spread through a campaign themed "Quotations".
Remcos - spread through a campaign themed "Invoices".
16/09/2025
AgentTesla - spread through a campaign themed "Orders".
FormBook - spread through a campaign themed "Offers".
Remcos - spread through a campaign themed "Offers".
17/09/2025
Remcos - spread through two campaigns, the first themed "Orders" and the second themed "Payments".18/09/2025
XWormRAT - spread through a campaign themed "Quotations".19/09/2025
PhantomStealer - spread through a campaign themed "Various".
Check out the August/September campaigns
We invite you to check out the August/September 2025 reports, to stay up-to-date on the malspam campaigns circulating in Italy:
Any information published on our site may be used and published on other websites, blogs, forums, facebook and/or in any other form both in paper and electronic form as long as the source is always and in any case cited explicitly “Source: CRAM by TG Soft www.tgsoft.it” with a clickable link to the original information and / or web page from which textual content, ideas and / or images have been extrapolated.
It will be appreciated in case of use of the information of C.R.A.M. by TG Soft www.tgsoft.it in the report of summary articles the following acknowledgment/thanks “Thanks to Anti-Malware Research Center C.R.A.M. by TG Soft of which we point out the direct link to the original information: [direct clickable link]”
如有侵权请联系:admin#unsafe.sh