
文章探讨了CISO整合网络安全工具、AI开发助手的安全风险、Ivanti漏洞分析、EASM购买指南以及Qilin勒索软件对地方政府的威胁。 2025-9-19 13:0:0 Author: www.tenable.com(查看原文) 阅读量:3 收藏
Check out why CISOs are embracing security platforms to reduce tool sprawl. Plus, learn how to prompt AI developer assistants into generating secure code. Further, dig into CISA’s analysis of malware tied to Ivanti EPMM vulnerabilities. And get the latest on external attack surface management and the Qilin ransomware threat to local governments.
Key takeaways
- Facing tight budgets, CISOs are all in on integrated cybersecurity platforms that let them consolidate cyber functions.
- That AI coding assistant saving you hours of work? It might also be injecting vulnerabilities into your code. The solution? Better prompts.
- If you use Ivanti EPMM, CISA wants you to stop what you're doing and make sure it's patched.
Here are five things you need to know for the week ending September 19.
1 - Study: CISOs heart cybersecurity platforms, MSSPs
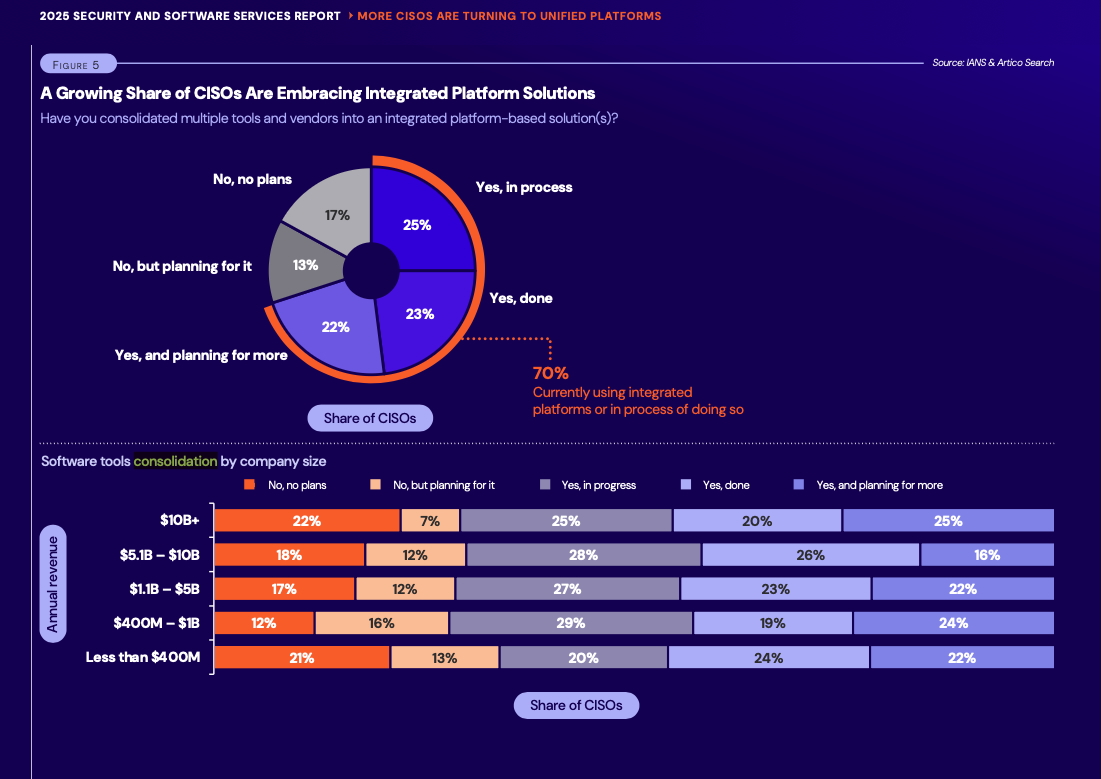
As they deal with budget pressures, technical complexity and scalability needs, CISOs are increasingly turning to integrated security platforms and to managed security services providers (MSSPs).
That’s a key takeaway from the “Security Software and Services 2025 Benchmark Report” published by IANS Research and Artico Search and based on a survey of 628 CISOs.
“The findings of this survey research show that tools consolidation and MSSPs can deliver value to CISOs where they need it most,” reads an IANS Research blog posted this week.
Specifically, 70% of CISOs said they either have consolidated or are in the process of consolidating standalone security tools with integrated platforms. Another 13% have plans to do so.
(Source: “Security Software and Services 2025 Benchmark Report” from IANS Research and Artico Search, September 2025)
Drivers for platform adoption include:
- Less tool sprawl, more clarity: Fewer tools mean less chaos and a clearer view of what's happening.
- Smarter security: Platforms integrate data, making it easier to spot and stop threats.
- Easier on the wallet: Bundled pricing beats buying dozens of individual products.
CISOs’ preferred areas for tool consolidation are endpoint security, cloud security and security operations. Network security, identity and access management (IAM) and data security are also seeing consolidation.
Meanwhile, almost 70% of CISOs have used at least one MSSP to manage security functions, including threat detection and response (84%), endpoint protection (57%), network security monitoring (43%) and incident response (33%).
“Success with these strategies will depend on striking the right balance – using integrated platforms to simplify security operations and MSSPs to scale, without sacrificing control or resilience,” the blog reads.
For more information about the benefits of an exposure management platform, check out these Tenable resources:
- “Exposure Management: 7 Benefits of a Platform Approach” (blog)
- “What Is Exposure Management?” (cybersecurity guide)
- “Breaking Down Silos: Why You Need an Ecosystem View of Cloud Risk” (blog)
- “How Exposure Management Has Helped Tenable Reduce Risk and Align with the Business” (blog)
- “Exposure Management Is the Future of Proactive Security” (blog)
2 - Is your AI coding assistant a security liability?
The productivity boost that developers get from using AI assistants for coding can come at a high price if they don’t use the tools securely.
To assist developers with this issue, the Open Source Security Foundation (OpenSSF) this week published the guide “Security-Focused Guide for AI Code Assistant Instructions.”
“AI code assistants are powerful tools. They can speed up development, suggest solutions, and help explore alternatives,” reads the OpenSSF blog “New OpenSSF Guidance on AI Code Assistant Instructions.”
“But they also create security risks, because the results you get depend heavily on what you ask,” it adds.

The guide offers developers tips and best practices on how to prompt these AI coding helpers to reduce the risk that they’ll generate unsafe code.
Specifically, the guide’s advice seeks to ensure that the AI coding assistants take into account:
- Application code security, such as validating inputs and managing secrets
- Supply chain safety, such as selecting safe dependencies and using package managers
- Platform or language-specific considerations, such as applying security best practices to containers
- Security standards and frameworks, such as those from OWASP and the SANS Institute
“In practice, this means fewer vulnerabilities making it into your codebase,” reads the guide.
For more information about the cyber risks of AI coding assistants:
- “Hackers setting traps for vibe coders: AI assistants can deliver malware” (Cybernews)
- “Cybersecurity Risks of AI-Generated Code” (Georgetown University)
- “Security risks of AI-generated code and how to manage them” (TechTarget)
- “AI-generated code risks: What CISOs need to know” (ITPro)
- “GitLab's AI Assistant Opened Devs to Code Theft” (Dark Reading)
3 - CISA slices and dices Ivanti EPMM vulnerability malware
If you use the Ivanti Endpoint Manager Mobile (EPMM) product, CISA has a message for you: Make sure you’re running its latest version. If you’re not, upgrade ASAP.
In a malware analysis report published this week, CISA unpacks a sophisticated malware campaign targeting this endpoint mobile management tool. Specifically, the report details the functionality of "malicious listener" malware used by threat actors to compromise the systems of an unnamed organization.
The attackers gained initial access by exploiting two critical vulnerabilities, CVE-2025-4427 and CVE-2025-4428, in Ivanti EPMM, and for which Ivanti provided patches in mid-May.
By chaining these vulnerabilities, the actors were able to execute remote commands, collect system information, download malicious files, map the network and exfiltrate sensitive data, including LDAP credentials.

CISA's analysis focused on two distinct sets of malware discovered in the compromised environment, according to CISA’s report, titled “Malicious Listener for Ivanti Endpoint Mobile Management Systems.”
Both sets were designed to establish persistence, allowing the threat actors to inject and execute arbitrary code on the affected server.
This malware acts as a listener, intercepting HTTP requests which could enable the attackers to exfiltrate data and maintain long-term access. The delivery method was stealthy, involving the malware being sent in multiple Base64-encoded segments via separate HTTP GET requests, a technique used to evade detection.
To combat this threat, CISA's report provides specific indicators of compromise (IOCs) along with YARA and SIGMA rules to help network defenders detect the malicious activity.
Mitigation recommendations include:
- Immediately upgrade Ivanti EPMM systems to the latest patched version.
- Treat all mobile device management (MDM) systems as high-value assets that warrant beefed-up security monitoring, restricted access, and heightened vigilance.
- Require phishing-resistant multifactor authentication (MFA) for all staff and services.
For more information about Ivanti EPMM vulnerabilities:
- “CVE-2025-4427, CVE-2025-4428: Ivanti Endpoint Manager Mobile (EPMM) Remote Code Execution” (Tenable)
- “Security Advisory Ivanti Endpoint Manager Mobile (EPMM) May 2025 (CVE-2025-4427 and CVE-2025-4428)” (Ivanti)
- “Chinese cyber spies are using Ivanti EPMM flaws to breach EU, US organizations” (Help Net Security)
- “Questions mount as Ivanti tackles another round of zero-days” (Cyberscoop)
- “Ivanti EPMM Zero-Day Flaws Exploited in Chained Attack” (Dark Reading)
4 - U.K.’s cyber agency offers EASM buying advice
If you’re in the market for an external attack surface management (EASM) system, you might be interested in a set of recommendations for how to pick the right one for your organization.
The “External Attack Surface Management (EASM) Buyer's Guide,” published this week by the U.K. National Cyber Security Centre (NCSC), seeks to demystify EASM and offer a structured approach for selecting the most appropriate product.
The NCSC defines EASM as the process of identifying, monitoring and remediating security issues in an organization's internet-accessible assets. EASM systems continuously scan for digital assets – such as websites, servers and cloud services – that may not be in the radar of the organization’s IT and security teams, and flag vulnerabilities, misconfigurations and other exposures.

EASM tools provide a comprehensive and up-to-date view of the organization’s external attack surface, so that they can proactively identify and mitigate security gaps.
“EASM products contribute to maintaining the 'defender’s edge' by ensuring you have the same – or better – visibility of your online systems as potential attackers,” reads an NCSC blog.
The NCSC breaks down essential EASM features into three main categories:
- Visibility and Insight: This includes asset discovery, technology identification and asset relationship mapping.
- Security Analysis: This involves vulnerability scanning, misconfiguration detection and risk prioritization based on severity and exploitability.
- Supporting Functions: These features help integrate the EASM tool into existing workflows, such as ticketing systems, reporting dashboards and alerting mechanisms.
The guide provides a step-by-step process for choosing a product. It encourages organizations to first understand their specific needs by asking key questions, including:
- What are our primary security concerns?
- Who will be using this tool?
- How will we integrate the information into our existing security operations?
- Do we also need vulnerability assessment?
- How current does our data need to be?
By clearly defining their goals and operational requirements, organizations can more effectively evaluate and select an EASM solution that is best suited to their unique environment and security challenges.
For more information about EASM, check out these Tenable resources:
- “What is External Attack Surface Management?” (cybersecurity guide)
- “Attackers Don't Honor Silos: Five Steps to Prioritize True Business Exposure” (white paper)
- “Visibility of the Unknown: Understanding EASM and How It Can Help” (blog)
- “Understanding Your Attack Surface: The Key to Effective Exposure Management” (blog)
- “Attack Surface Management FAQ” (FAQ)
5 - Local governments: Beware of Qilin ransomware
The Qilin gang has emerged as the top ransomware attackers against U.S. state, local, tribal and territorial (SLTT) governments.
Qilin accounted for about 25% of ransomware attacks against these governments during 2025’s second quarter, up sharply from a 9% share in the first quarter, according to the Center for Internet Security (CIS).
The group operates on a double-extortion model, meaning it not only encrypts the victim's data and demands a ransom, but also steals sensitive information and threatens to make it public. Ransom demands from Qilin have been as high as $500,000.
“The ransomware group’s mature operation and high attack tempo present a near-term threat to U.S. SLTTs for significant disruptions due to network-wide encryption and associated recovery efforts,” reads the CIS blog “Qilin Top Ransomware Threat to SLTTs in Q2 2025.”

CIS attributes Qilin's rise partly to the recent inactivity of the previously dominant RansomHub group, with many of its affiliates believed to have moved over to Qilin's ransomware-as-a-service (RaaS) operation.
Qilin typically gains initial access through phishing campaigns, exploiting vulnerabilities in public-facing applications and using remote services. Following the initial breach, Qilin conducts further exploitation and data theft.
For more information about Qilin:
- “CISA reaffirms to safeguard US critical infrastructure against escalating threats from Qilin ransomware group” (Industrial Cyber)
- “Attackers exploit Fortinet flaws to deploy Qilin ransomware” (Security Affairs)
- “Hackers start leaking New Orleans sheriff ransomware data” (Axios)
- “Qilin ransomware steals credentials stored in Google Chrome” (Security Affairs)
- “Qilin Ransomware Ranked Highest in April 2025 with 72 Data Leak Disclosures” (The Hacker News)

Juan Perez
Senior Content Marketing Manager
Juan has been writing about IT since the mid-1990s, first as a reporter and editor, and now as a content marketer. He spent the bulk of his journalism career at International Data Group’s IDG News Service, a tech news wire service where he held various positions over the years, including Senior Editor and News Editor. His content marketing journey began at Qualys, with stops at Moogsoft and JFrog. As a content marketer, he's helped plan, write and edit the whole gamut of content assets, including blog posts, case studies, e-books, product briefs and white papers, while supporting a wide variety of teams, including product marketing, demand generation, corporate communications, and events.
如有侵权请联系:admin#unsafe.sh