九月上半月微软钓鱼攻击创纪录,采用加密载荷、设备指纹识别等高级技术,并滥用Backblaze等知名主机。攻击者利用Telegram API实时窃取凭证,并通过地理位置追踪和会话令牌窃取进一步 targeting。同时针对企业及个人账户(如American Express),采用品牌模仿和深度指纹识别技术。 2025-9-15 16:31:18 Author: pixmsecurity.com(查看原文) 阅读量:3 收藏
The first half of September witnessed yet new records of Microsoft spearphish volume, with threat actors employing advanced evasion techniques, including payload encryption, device fingerprinting, and infrastructure abuse of reputable hosts like Backblaze, Hostinger, and Telegram’s Bot API. The same period saw sustained phishing targeting of personal accounts on work devices like American Express and AOL. Here are some examples and highlights.
stab[.]ru[.]com
e0ba4b4c729c46bda371ea8244d7a314[.]hanbookupdatecompliance[.]online
ameuricnapesires[.]com
slateblue-fox-104423[.]hostingersite[.]com
f005[.]backblazeb2[.]com
login[.]stawment[.]icu
apis-f7c[.]novabrightlab[.]ru[.]com
harbor-6eb[.]groovix[.]sa[.]com
cityofmorehead[.]blessing[.]com[.]de
vtkrdwha[.]hootouloo[.]sa[.]com
baylineliving[.]it[.]com
Microsoft and OneDrive on Backblaze
Standing out during this period was a widespread campaign targeting users at Minnesota and Kentucky organizations. The below Microsoft spearphish was first clicked on Sep 10 by an administrator at a Minnesota organization with a lure about a document share via OneDrive.
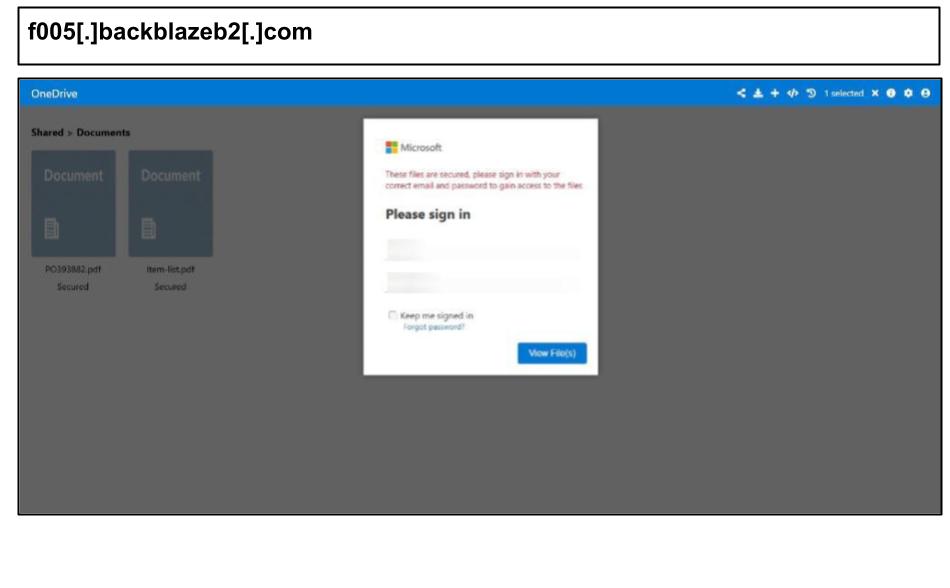
The attack references multiple PDFs–PO393882.pdf and Item-list.pdf–suggesting the lure was regarding a purchase order and targeting procurement personnel. The page was hosted on Backblaze B2 for free TLS/CDN and reputation cover, similar to prior attacks leveraging the same with CloudFlare.
The site notably uses Telegram’s Bot API to exfiltrate credentials and sends them to multiple recipients for redundancy.
https://api.telegram.org/bot…/sendMessage?chat_id=…&text=…
This removes the need for costly attacker infrastructure like domains and TLS certificates needed to exfiltrate credentials. Instead, attackers get real time alerts on their phones or desktops, while the traffic leaving the victim’s network moves through an otherwise reputable api.telegram.org channel.
The page further grabs geographic information of the user to send along with compromised credentials for additional targeting efforts. The same attack was clicked by 6 other staff members at the same organization on the same day, as well as employees at a Kentucky organization on September 11.
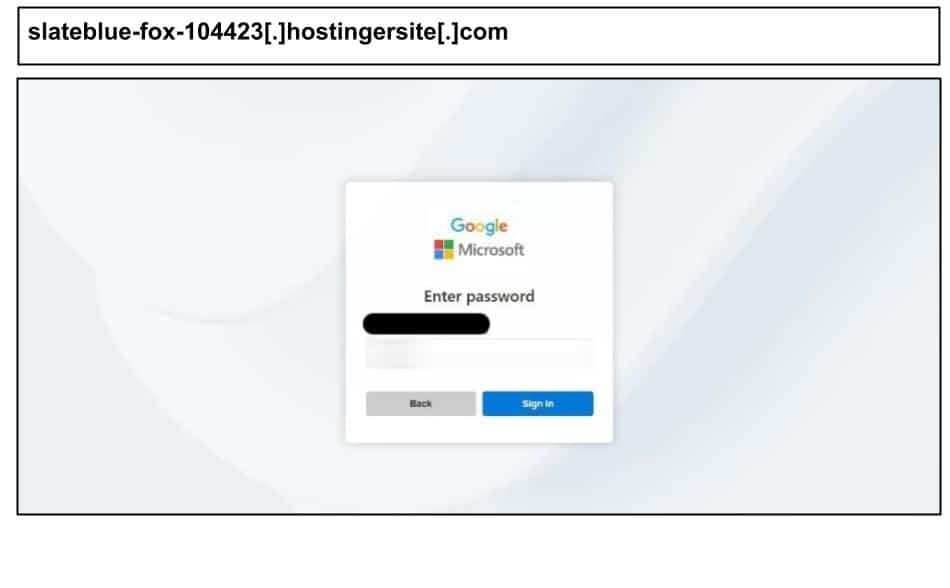
Also leveraging legitimate infrastructure was an attack targeting a staff member at another Minnesota organization, who clicked the below Microsoft spear phish on September 9 that used Hostinger’s official *.hostingersite.com builder domain—-a legitimate third-party hosting service.
The period saw a number of Microsoft spearphish using evasive techniques. On Sep 4th, a staff member at a Kentucky organization clicked the below Microsoft spearphish.
The page included a couple of evasive techniques, like keeping its code in a completely encrypted state until loaded inside the browser to avoid web scanners. It also checks what kind of device or browser it’s on (e.g., signs of a test/virtual environment) and will go blank or stop running if it thinks it’s being analyzed. On September 10th, an administrator at the same Kentucky organization clicked the below phishing page.
It uses similar encryption techniques to the prior example to evade detection. It also steals session tokens and device details from the browser as well as regular credentials in order to login elsewhere without triggering a multi-factor event.
We also saw a number of campaigns hosting phishing attacks across a large number of servers in order to quickly redirect and switch upon detection. On September 10, a staff member at a Colorado organization clicked the below Microsoft spear phish.
The phishing attack is part of a large cluster of subdomains of *.statwment[.]icu, so that the page can quietly switch to a different server if one gets blocked.
newnewdomnewdefijbfjhi[.]stawment[.]icu
newnewdomnewbjbfcjfidd[.]stawment[.]icu
newnewdomnewcaiaibhdji[.]stawment[.]icu
newnewdomnewbdechaigda[.]stawment[.]icu
The page is built to run inside other pages or in-app browsers via iframes, and it rewrites cookie settings so its login data still works across their look-alike sites—even as browsers phase out third-party cookies.
In addition to stealing passwords, a concerning tactic we saw during the period involved stealthily obtaining consent from users for full access to their mailboxes. On September 4, a director at a Kentucky organization clicked the below Microsoft spearphish.
Upon harvesting a victim’s credentials, the page will redirect the user to the legitimate office.com page. In addition to stealing credentials, the page also asks for permissions to read and send messages from the user’s email, including the ability to do so when the user is offline. This effectively gives the attacker multiple keys to the victim’s mail.
The same period saw threat actors harvesting credentials on Russian servers, using aggressive device fingerprinting for enhanced targeting, and soliciting 6 digit MFA codes. On September 8, an administrator at a Kentucky organization clicked the below Microsoft spearphish.
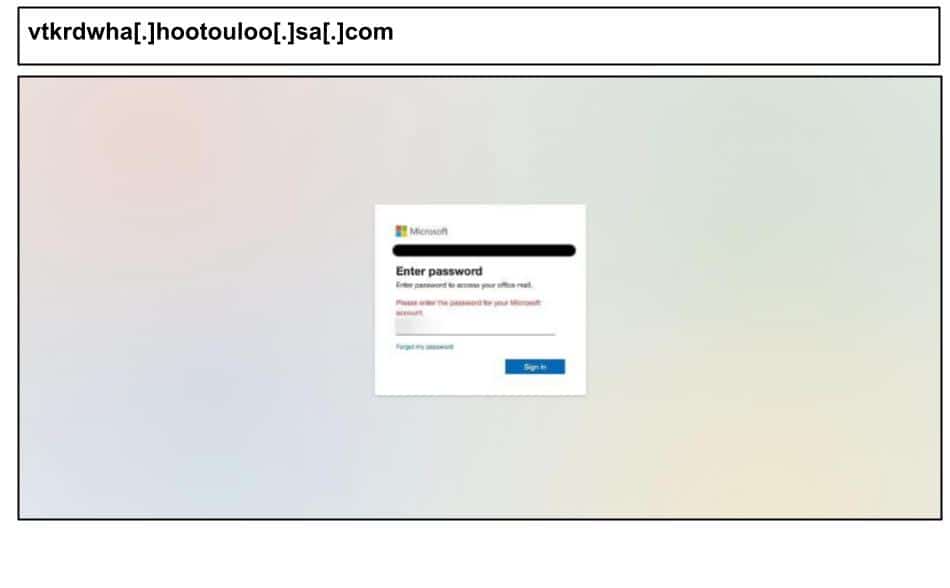
The page includes payload encryption and prompts users for multiple types of 6 digit MFA codes, eg. SMS, authenticator app etc. On September 10, a staff member at a Kentucky organization clicked the below Microsoft spearphish.
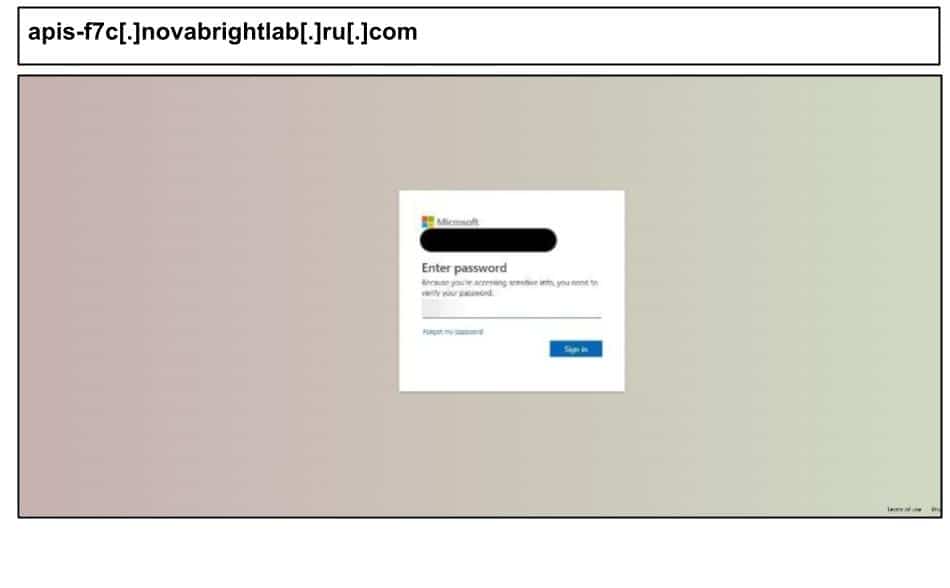
The page exfiltrates credentials to a Russian domain: alchemypromoh[.]ru. The page cleverly conceals plaintext like “Enter password,” “Approve a request,” etc, by splitting characters with invisible HTML span elements, so they would not be detected by various scanning tools. On September 11, a staff member at a Kentucky organization clicked the below Microsoft spearphish.
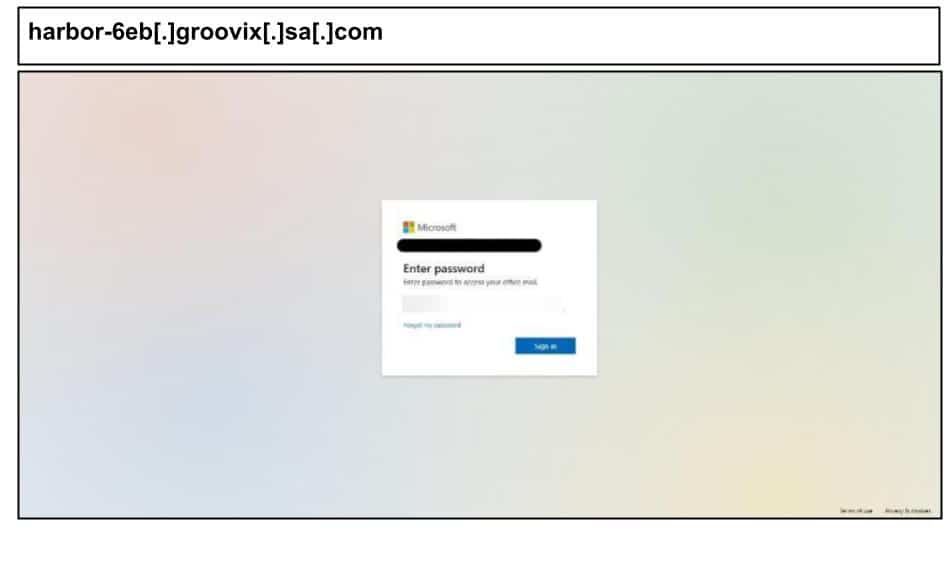
Like other Microsoft impersonations seen during this period, the attack conceals its code in an encrypted format until loaded into the browser and features aggressive browser fingerprinting.
Personal Accounts Targeted on Work Devices
The period saw personal accounts targeted on work devices like American Express and AOL that included some similar TTPs seen in above cases targeting corporate accounts. On August 31, a staff member at a Georgia organization clicked the below American Express phishing attack.
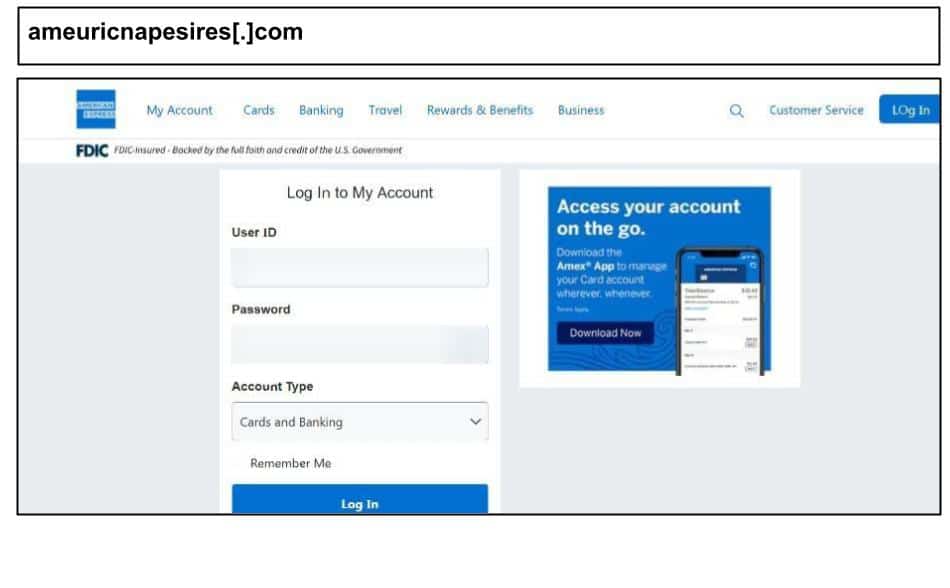
The HTML content swaps in look-alike letters from other alphabets (e.g., Cyrillic “е” or Greek “ο”) so words like “American Express” or “Account” look right to the user but do not trigger web scanners for brand impersonation.
On September 11, multiple staff members at a Florida organization clicked the below AOL phishing attack on their work devices.
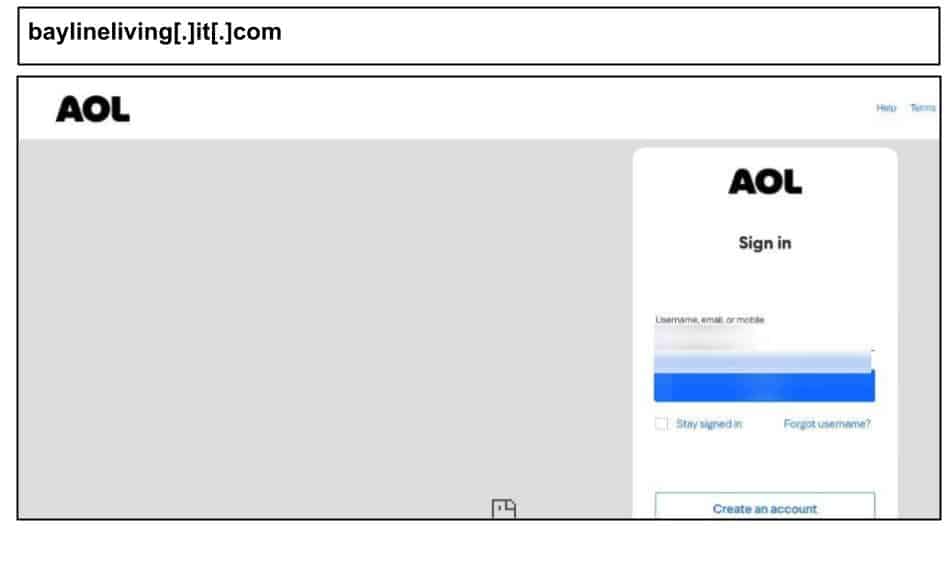
The page uses in depth device fingerprinting, including WebGL vendor/renderer, canvas/audio entropy, ad-block detection, TZ, CPU cores, and RAM among others. This allows the attacker to evade sandboxing, correlate repeat visits, and prioritize high value victims if there are clues of an enterprise environment. The page references other domains like palmvistarealty[.]it[.]com, likely to redirect and rotate if the initial one gets blocked.
Mitigations
- Block the specified domains on corporate firewalls and endpoint security solutions.
- Educate users about phishing risks even on pages that purport to use MFA
- Remind users of phishing risks for their personal accounts they access even if they are on corporate devices
- Enforce multi-factor authentication (MFA) on all corporate logins to reduce the risk of credential compromise.
If you are interested in seeing how PIXM can help prevent attacks like these for your organization, book a demo here.
如有侵权请联系:admin#unsafe.sh