CISA发布指南强调运营技术资产清点与分类的重要性,并提供六步方法以确保安全 posture。Tenable OT Security 提供自动化资产发现、分类及生命周期管理功能,助力组织实现高效安全运营。 2025-9-15 15:0:0 Author: www.tenable.com(查看原文) 阅读量:3 收藏
A complete and detailed operational technology (OT) asset inventory and taxonomy are not only the foundation of a defensible security posture, they’re also essential for resilient operations. Here’s a breakdown of CISA's latest OT guidance with details on how Tenable can help you turn it into action.
Key takeaways
- CISA’s recently published “Foundations for OT Cybersecurity: Asset Inventory Guidance for Owners and Operators” offers a systematic process you can use to develop and maintain an accurate, up-to-date record of your organization’s OT assets.
- Taking the time to build a well-structured OT taxonomy offers numerous benefits, including better decision making and improved data analytics and insights.
- By providing unmatched visibility into complex and converged IT/OT environments, Tenable OT Security helps organizations meet the foundational requirements outlined in CISA's latest guidance.
A fundamental challenge in securing operational technology (OT) environments is a pervasive lack of visibility, security and control. Without these, it’s difficult to know exactly which assets you have, their configurations and their related activities. Recognizing this critical need, the U.S. Cybersecurity and Infrastructure Security Agency (CISA), along with various U.S. government agencies and international partner agencies, recently published a detailed guide on "Foundations for OT Cybersecurity: Asset Inventory Guidance for Owners and Operators." This directive emphasizes that creating an OT asset inventory, supplemented by an OT taxonomy, is essential for building a modern defensible architecture.

CISA's blueprint for OT asset inventory and taxonomy
CISA’s guidance offers a systematic process you can use to develop and maintain an accurate, up-to-date record of your organization’s OT assets. It outlines six key steps to get you started: defining scope and governance, identifying assets, collecting key attributes, creating a taxonomy, managing the data and implementing lifecycle management.
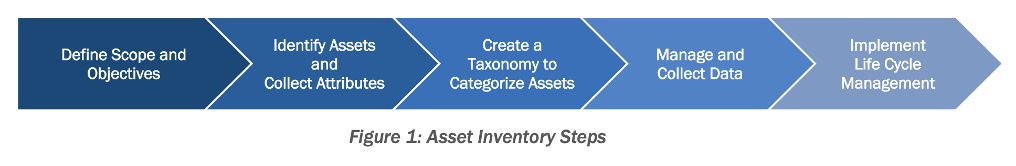
CISA defines each step as follows:
Defining scope and objectives: Identify governance, assign roles and set boundaries for the inventory program.
Identifying assets and collecting attributes: Conducting physical inspections and logical surveys to compile a comprehensive list of assets and their network dependencies. High-priority attributes to collect include active/supported communication protocols, asset criticality, IP/MAC addresses, manufacturer, model, OS and physical location.
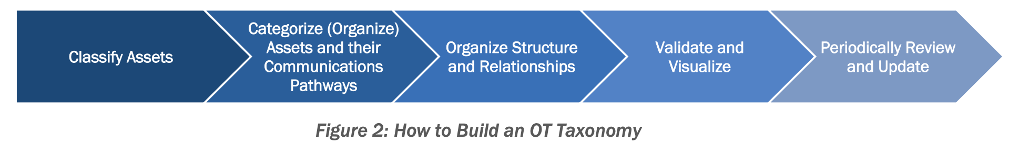
Creating a taxonomy to categorize assets: Building a classification system to organize and prioritize OT assets based on criticality or function. As shown in the process flow below, this process should involve classifying assets and categorizing them into "Zones" and "Conduits" to manage security requirements and communication pathways.
Managing and collecting data: Establish centralized databases and security controls for asset data.
Implementing lifecycle management: Define stages for the lifecycle of each of your assets and develop policies for managing them.
The guide also emphasizes that security teams should leverage inventory data generated for risk management, maintenance planning, performance monitoring, training and continuous improvement. CISA provides sector-specific taxonomy examples for oil and gas, electricity and water/wastewater verticals to help organizations adopt the approach to the unique needs of their environment.
Benefits of implementing an OT taxonomy
Taking the time to build a well-structured OT taxonomy offers numerous benefits, including the following outlined by CISA:
- Improved organization and management: Enables effective categorization of assets, processes and data, leading to more efficient operations and information retrieval.
- Enhanced communication: Standardizes terminology and classifications, reduces misunderstandings and improves collaboration between teams and departments.
- Better decision making: Provides a clear understanding of asset relationships, which enables security teams to make more informed decisions regarding resource allocation, planning maintenance downtime intervals and implementing software/OS upgrades.
- Cost savings: Optimizes asset management and reduces inefficiencies, which can lead to significant cost savings and helps minimize downtime.
- Data analytics and insights: Offers a clear framework for organizing and analyzing data, leading to valuable insights that drive continuous improvement.
How Tenable can help
Tenable OT Security, a key part of our Tenable One Exposure Management Platform, provides a complete solution for managing your OT risk exposure and securing your most critical assets. The Tenable One platform unifies data from more than 300 third-party integrations and Tenable’s own sensors, giving security teams a single, AI-powered view of exposures across the IT and OT ecosystem. By normalizing and correlating this data, Tenable One pinpoints what matters most so you can act faster and stay ahead of threats. Purpose-built to provide complete visibility for even the most complex OT/IT environments, Tenable OT Security helps you assess, prioritize and mitigate risk with OT asset inventory capabilities that are fully aligned with CISA's latest inventory and taxonomy guidance.
Intelligent asset discovery and inventory
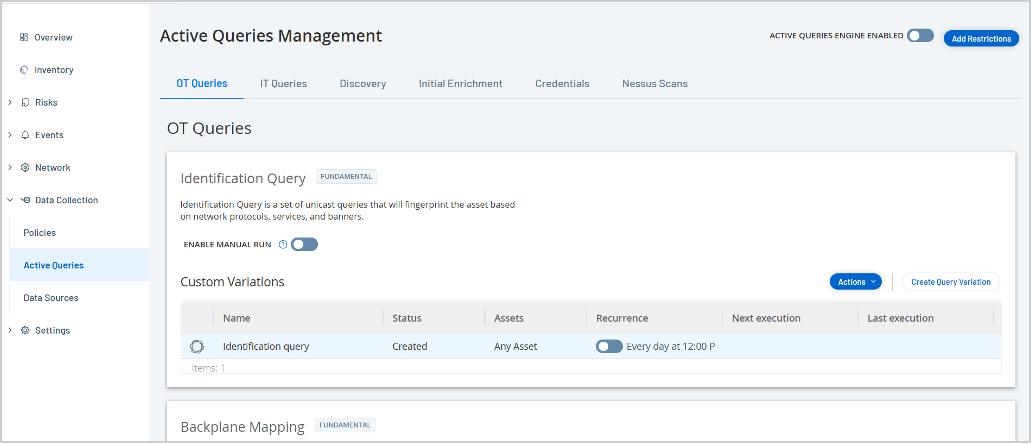
Tenable OT Security automatically discovers all devices in your network — with greater specificity than what is discernible directly from the device — resulting in a complete asset inventory that includes controllers (PLCs, RTUs, DCS), human-machine interfaces (HMIs), workstations, servers and IoT devices. This directly supports CISA's crucial step of "identifying assets." We also gather deep insights into device state, including firmware version, patch levels and ladder logic details, which align with CISA's recommendation to "collect asset attributes" such as manufacturer, model and OS.
Our proprietary Hybrid Discovery Engine detects and classifies assets using a combination of passive monitoring and active scanning techniques. We perform deep packet inspection on network traffic that occurs naturally, with the ability to interpret the proprietary responses from devices via Active Query. For example, if it's a simpler device, our solutions search for headers or banners on HTTP/SNMP/FTP protocols. For more complex devices such as programmable logic controllers (PLCs) and remote terminal units (RTUs), we search for and decode the bytes that tell us what the family or model is in order to fingerprint the device.
To support evolving requirements, Tenable Research publishes new device detection profiles through a live feed to customers on a regular basis.
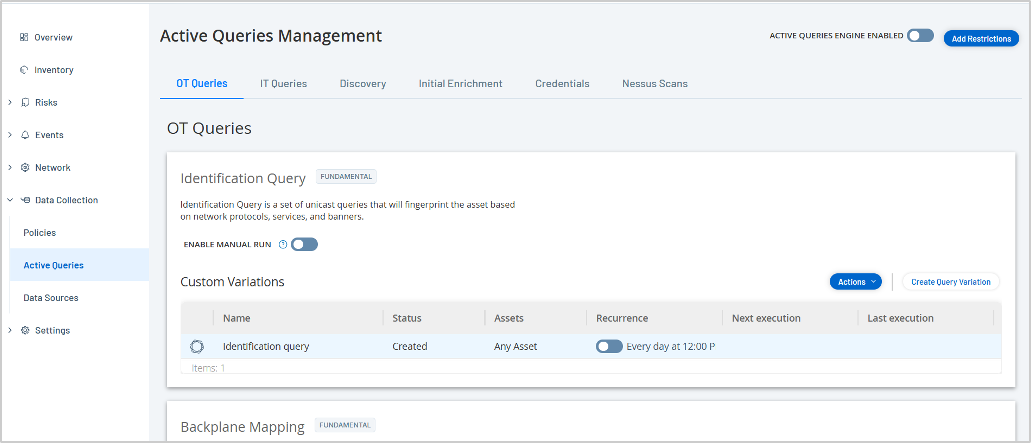
These capabilities provide a foundation for security teams to implement a classification system to effectively build and maintain a complete asset inventory and prioritize risk remediation efforts all while uncovering crucial enterprise-wide context.
Enterprise data enrichment with support for offline file imports
Tenable OT Security helps streamline visibility and asset management across disparate data sources with the ability to import multiple file types. Supported file formats include CSV files, SCD files (electrical power substations), PLC project files (e.g., Rockwell Automation RSLogix 5000 Program Files) and packet capture (PCAP) files. Support for API-driven automation enables security teams to enrich assets from internal inventory data sources.
Additionally, you can export a CSV file for your entire inventory, facilitating periodic audits and taxonomy updates. You can modify exported data offline via familiar tools, such as Microsoft Excel, and then easily import files back into Tenable OT Security to update asset values.
Asset management with custom tags and groups
Tenable OT Security enables security analysts to apply custom fields to assets, such as "asset owner" or "building name," allowing organizations to add specific business context to their inventory and mirror real-world environments. Dynamic tagging capabilities enable you to categorize assets based on important properties, including OT vendor, device or product family, IP address and system type. This helps in organizing and prioritizing OT and IoT assets based on criticality and function, as recommended by CISA.
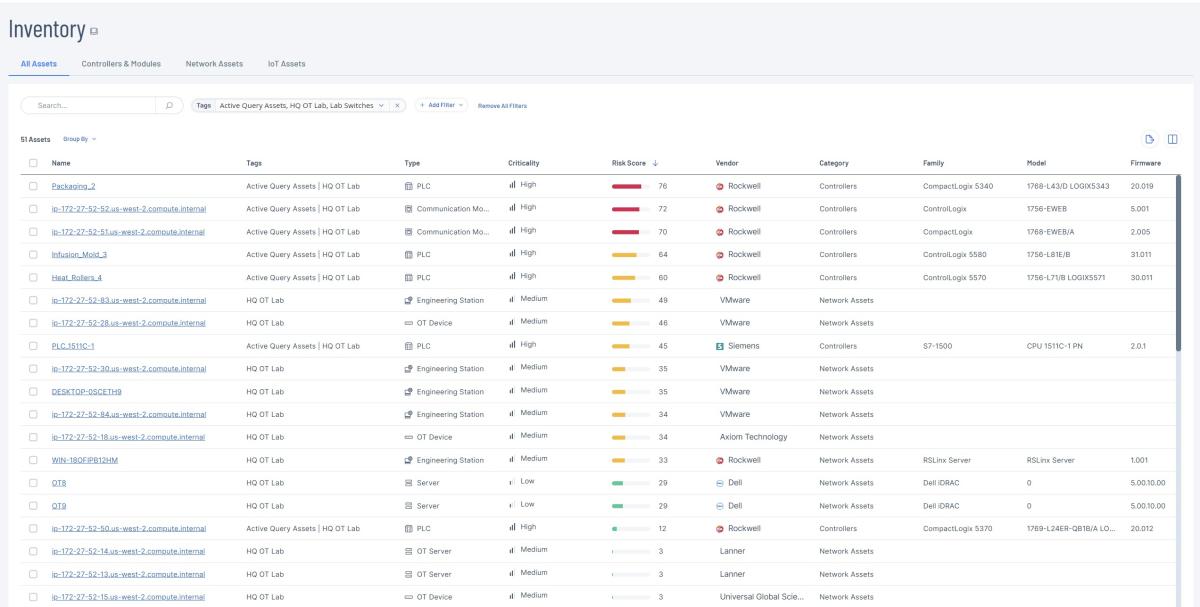
360-degree visibility and situational awareness
Tenable OT Security simplifies OT network complexity and hones situational awareness, offering unparalleled visibility into assets, their state and their communications. This addresses core challenges identified by CISA regarding the lack of visibility security teams have into their OT environment. Interactive and customizable views help security teams quickly access relevant asset details for mitigation and remediation without the need for operational downtime.
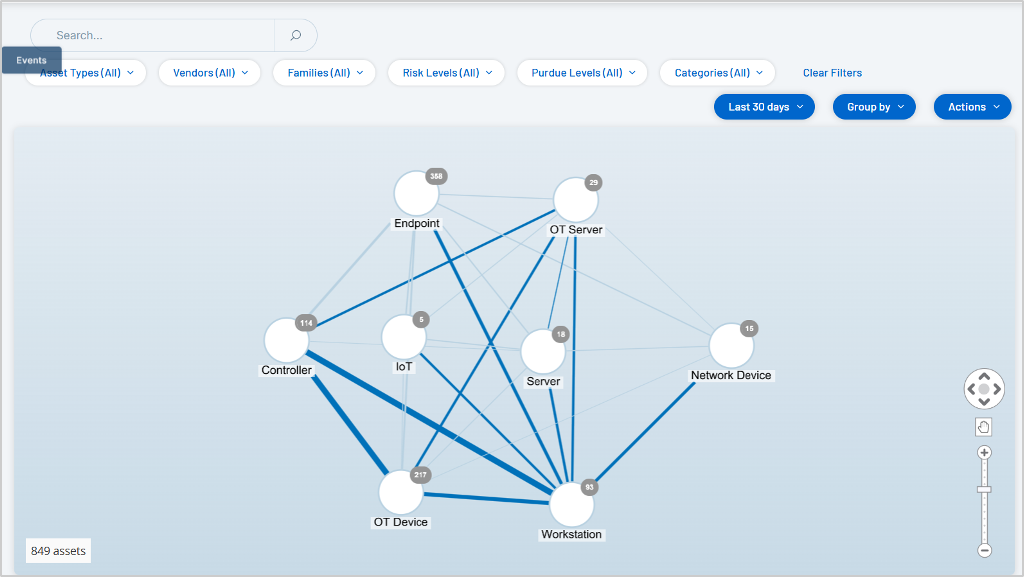
Interactive asset mapping and visualization
Network maps in Tenable OT Security reveal how OT/IT networks operate by visualizing asset hierarchies, dependencies and communication patterns. This capability supports CISA's "validate and visualize" step for building an effective taxonomy. You can view the whole network or zoom in on specific assets and drill down into protocol information or other details. Network maps also automatically group assets into logical clusters aligned with your environment.
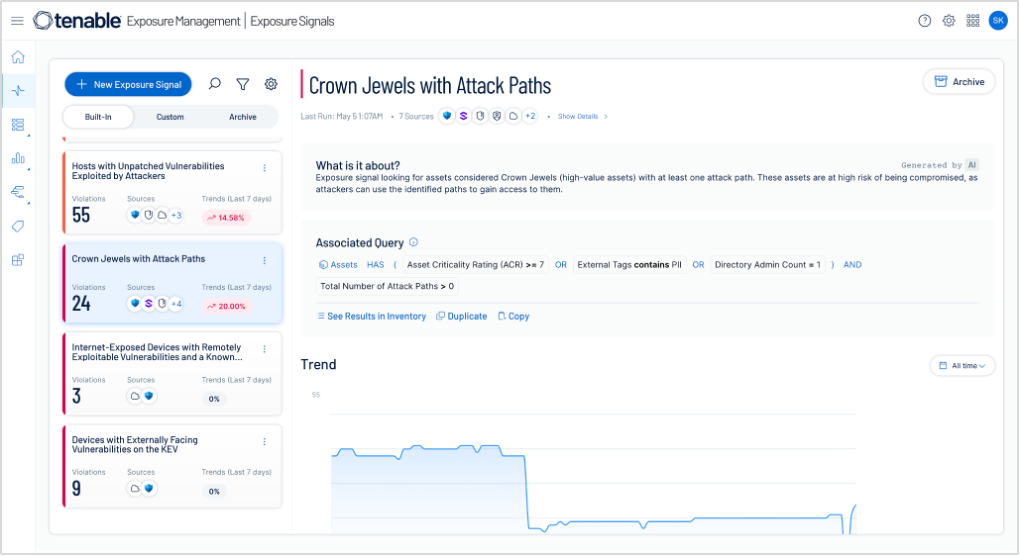
Proactive threat detection and risk management
Exposure Signals — a key capability in Tenable One — allows you to connect the dots between vulnerabilities, misconfigurations, exposed assets and other risks across your environment to reveal entire attack paths. If you can understand not just what is vulnerable, but how those vulnerabilities connect, you can clearly see how a "medium-risk" vulnerability on a web server isn't just a single issue; it's the first step in a chain that leads directly to your most critical OT assets and data, allowing you to prioritize and dismantle the threats that truly matter. It helps you identify which of your “crown jewels” are most at risk. Tenable One acts as a detective, ingesting signals from every corner of your attack surface (IT, cloud, identity systems, OT, etc.) and correlating them.
And your OT asset inventory becomes even more powerful when connected to your broader security and enterprise IT ecosystem. Tenable excels at breaking down these silos, transforming OT data from a static list into an actionable component of your security operations program. This allows your teams to leverage their existing tools for a holistic view of risk.
By enriching your ServiceNow CMDB with detailed OT asset data, you create a single source of truth that accelerates incident response and streamlines change management. Forwarding security events (including vulnerabilities and asset details) to Splunk allows your SOC to use their existing SIEM workflows and playbooks to monitor threats across the entire converged environment. This holistic approach extends to risk management, as OT data is leveraged by Tenable One for a unified view of exposure across your entire attack surface. This same data can also be fed into Risk-Based Vulnerability Management (RBVM) platforms such as Tenable Lumin, Brinqa and Kenna, ensuring you can apply consistent, data-driven prioritization for both IT and OT vulnerabilities and focus remediation on the highest-risk issues.
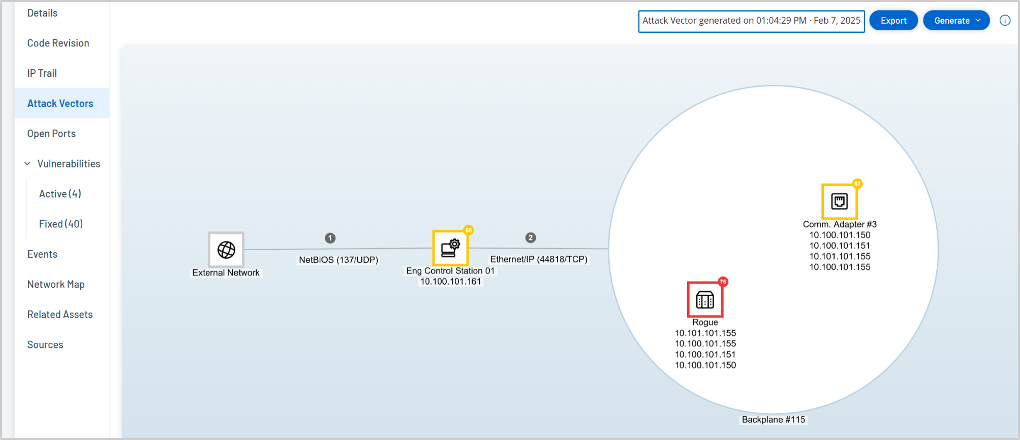
Additionally, embedded Attack Path Analysis tools help security teams identify risky configurations and/or device states, alerting administrators to potential threats before an incident occurs. Attack Path Analysis helps identify unknown devices and connections, highlighting problematic communications (e.g., between environments that should be firewalled or unauthorized remote access). This is critical for early warning of unfolding threats and directly aligns with CISA's objective of implementing real-time monitoring to detect emerging threats and vulnerabilities.
Hardware and software product lifecycle management
Tenable OT Security provides security teams with valuable insight into the current level of support for particular software applications or hardware devices, based on publicly available data published by the vendor or OEM (made available via custom API).
Built-in OT asset lifecycle management capabilities help detect outdated firmware and end-of-life software, with comprehensive alerts and extensive plug-in support for commonly used OT device vendors such as Siemens, Schneider Electric and Rockwell, as well as a vast library of IoT applications.
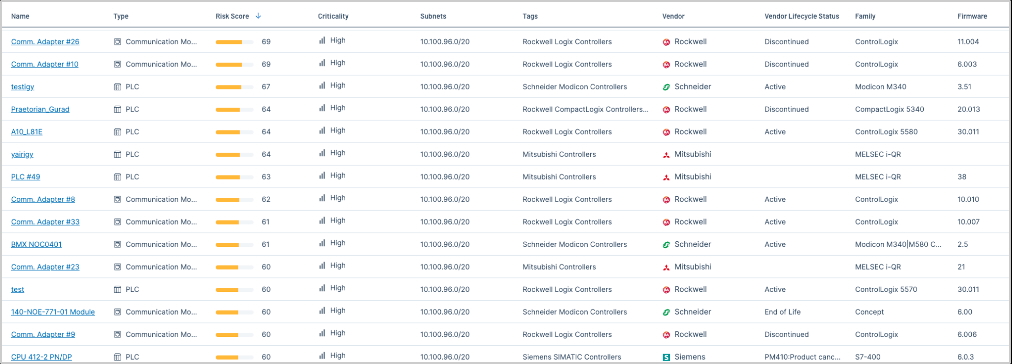
By providing unmatched visibility into complex and converged IT/OT environments, Tenable helps organizations meet the foundational requirements outlined in CISA's latest guidance. We’re committed to helping organizations simplify asset management, strengthen their security posture and proactively defend against advanced cyber threats to critical national infrastructure.
Learn more
- Download the CISA Asset Inventory Guidance for Owners and Operators
- Learn more about Tenable OT Security
- Learn more about the Tenable One Exposure Management Platform
- Request a demo to see Tenable solutions in action
如有侵权请联系:admin#unsafe.sh