攻击者通过钓鱼邮件入侵npm包维护者账户,在高下载量包中注入恶意软件,劫持加密货币交易并转移至攻击者钱包。 2025-9-8 17:0:19 Author: www.bleepingcomputer.com(查看原文) 阅读量:1 收藏

In a supply chain attack, attackers have injected malware into NPM packages with over 2.6 billion weekly downloads after compromising a maintainer's account in a phishing attack.
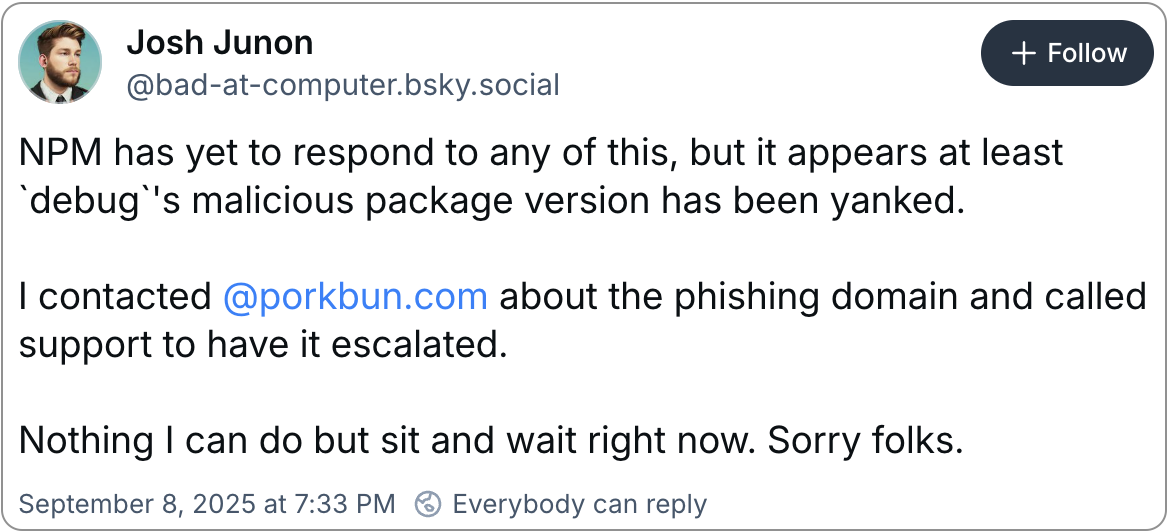
Josh Junon (qix), the package maintainer whose accounts were hijacked in this supply-chain attack, confirmed the incident earlier today, stating that he was aware of the compromise and adding that the phishing email came from support [at] npmjs [dot] help, a domain that hosts a website impersonating the legitimate npmjs.com domain.
In the emails, the attackers threatened that the targeted maintainers' accounts would be locked on September 10th, 2025, as a scare tactic to get them to click on the link redirecting them to the phishing sites.
"As part of our ongoing commitment to account security, we are requesting that all users update their Two-Factor Authentication (2FA) credentials. Our records indicate that it has been over 12 months since your last 2FA update," the phishing email reads.
"To maintain the security and integrity of your account, we kindly ask that you complete this update at your earliest convenience. Please note that accounts with outdated 2FA credentials will be temporarily locked starting September 10, 2025, to prevent unauthorized access."
The attackers targeted other package maintainers and developers using the same email, according to reports from those who received the phishing message.
BleepingComputer found that the npmjs[.]help page also includes a login form that will exfiltrate inputted credentials to the following URL:
https://websocket-api2[.]publicvm.com/images/jpg-to-png.php?name=[name]&pass=[password]Since the incident was detected, the NPM team has removed some of the malicious versions published by the attackers, including the one for the debug package, which is downloaded 357.6 million times per week.
The supply chain attack
According to Aikido Security, which analyzed the supply-chain attack, the threat actors updated the packages after taking over control, injecting malicious code that acts as a browser-based interceptor into the index.js files, capable of hijacking network traffic and application APIs.
The malicious code only impacts individuals accessing the compromised applications over the web, monitoring for cryptocurrency addresses and transactions that are then redirected to attacker-controlled wallet addresses. This causes the transaction to be hijacked by the attackers rather than being sent to the intended address.
The malware operates by injecting itself into the web browser, monitoring Ethereum, Bitcoin, Solana, Tron, Litecoin, and Bitcoin Cash wallet addresses or transfers. On network responses with crypto transactions, it replaces the destinations with attacker-controlled addresses and hijacks transactions before they're signed.
Aikido says the malicious code does this by hooking JavaScript functions like fetch, XMLHttpRequest, and wallet APIs (window.ethereum, Solana, etc.).
The packages hijacked so far collectively have over 2.6 billion downloads every week:
- backslash (0.26m downloads per week)
- chalk-template (3.9m downloads per week)
- supports-hyperlinks (19.2m downloads per week)
- has-ansi (12.1m downloads per week)
- simple-swizzle (26.26m downloads per week)
- color-string (27.48m downloads per week)
- error-ex (47.17m downloads per week)
- color-name (191.71m downloads per week)
- is-arrayish (73.8m downloads per week)
- slice-ansi (59.8m downloads per week)
- color-convert (193.5m downloads per week)
- wrap-ansi (197.99m downloads per week)
- ansi-regex (243.64m downloads per week)
- supports-color (287.1m downloads per week)
- strip-ansi (261.17m downloads per week)
- chalk (299.99m downloads per week)
- debug (357.6m downloads per week)
- ansi-styles (371.41m downloads per week)
"The packages were updated to contain a piece of code that would be executed on the client of a website, which silently intercepts crypto and web3 activity in the browser, manipulates wallet interactions, and rewrites payment destinations so that funds and approvals are redirected to attacker-controlled accounts without any obvious signs to the user," Aikido Security researcher Charlie Eriksen said.
"What makes it dangerous is that it operates at multiple layers: altering content shown on websites, tampering with API calls, and manipulating what users' apps believe they are signing."
While this is a supply chain attack, Andrew MacPherson, Principal Security Engineer at Privy, told BleepingComputer that there are specific criteria that must be met for an app to have been affected, which significantly decreases the impact. This includes:
- A fresh install between ~9 AM and ~11.30 AM ET, when the packages were compromised
- Package-lock.json was created during that time
- Vulnerable packages in direct or transient dependencies
This supply-chain attack follows a series of similar attacks targeting developers of various well-known JavaScript libraries over the past few months.
For instance, in July, attackers compromised eslint-config-prettier, a package with over 30 million weekly downloads, while in March, ten other widely used npm libraries were hijacked and turned into info-stealers.
Both the phishing attack and the injected malware illustrate how the web browser has become a massive attack surface for stealing credentials, modifying traffic, and breaching networks.
BleepingComputer has a webinar later this month titled "Your Browser Is the Breach: Securing the Modern Web Edge" that focuses on recent browser attacks and how to defend this attack surface.
Update: Revised the lede as the attack is not as impactful as initially thought.
如有侵权请联系:admin#unsafe.sh